System Security
Security Wall Virtual Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security wall virtual ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
Road Traffic Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this road traffic security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
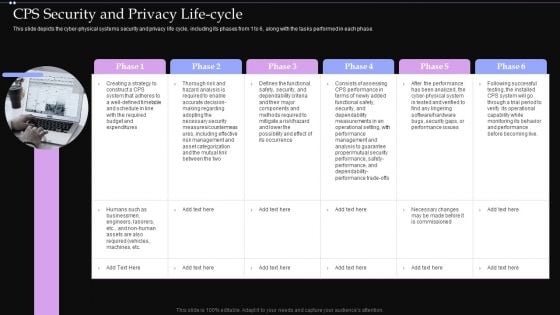
CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
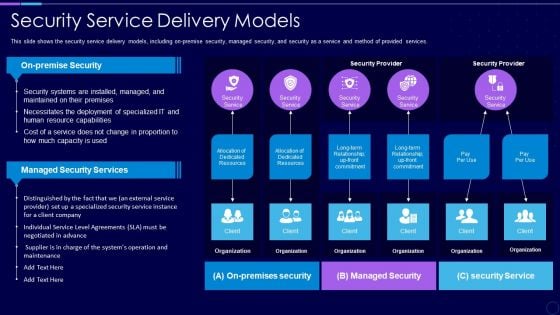
Everything As A Service Xaas For Cloud Computing IT Security Service Delivery Models Diagrams PDF
This slide shows the security service delivery models, including on-premise security, managed security, and security as a service and method of provided services. This is a everything as a service xaas for cloud computing it security service delivery models diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deployment, resource capabilities, security systems, security service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
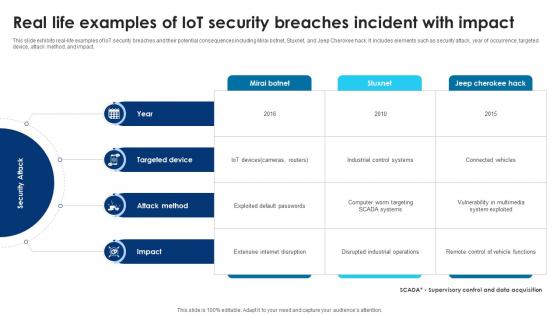
Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V
This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact. Get a simple yet stunning designed Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact.

Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V
This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V today and make your presentation stand out from the rest This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results.
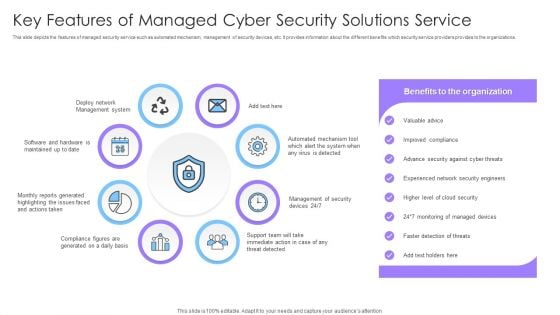
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
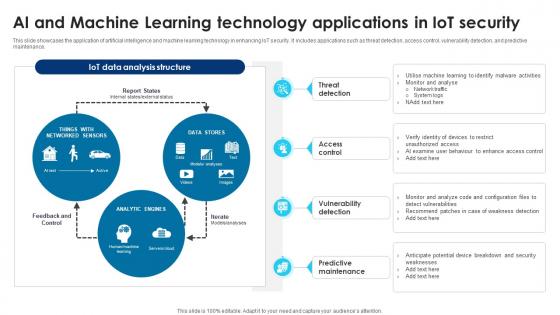
Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V
This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance. Boost your pitch with our creative Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
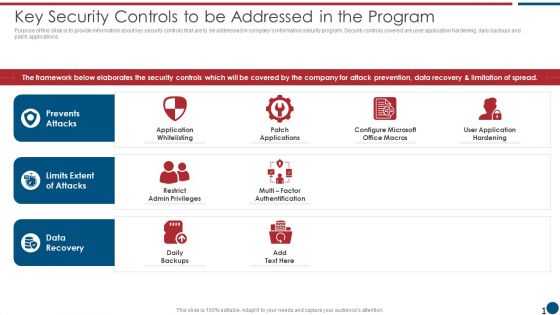
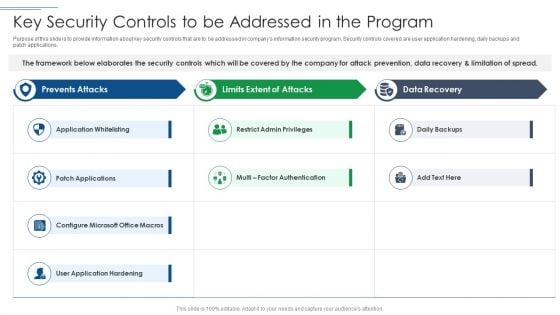
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
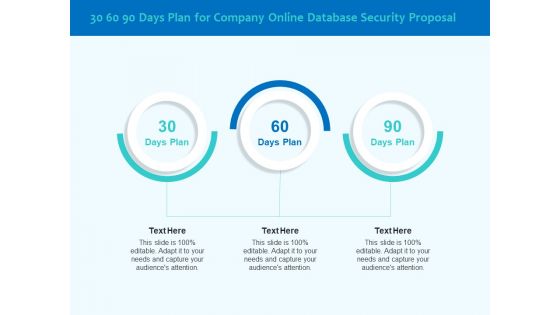
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
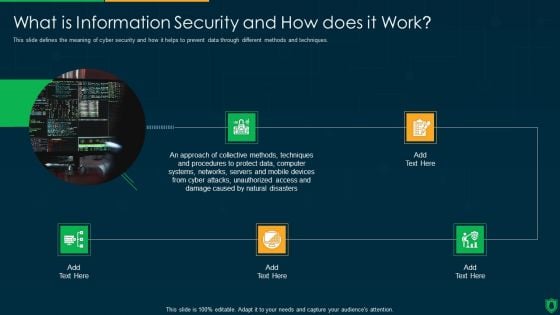
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
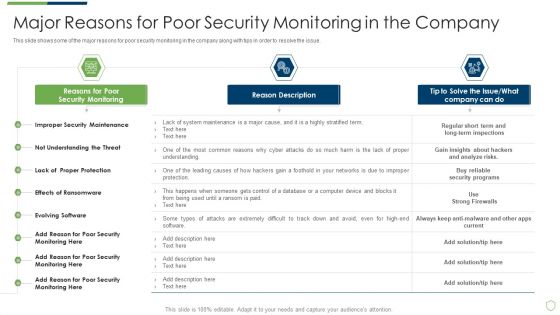
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Content Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Elements PDF
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
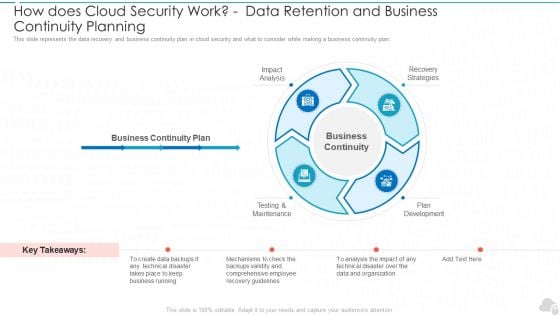
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
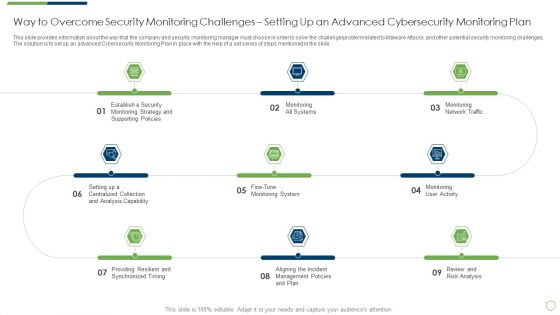
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
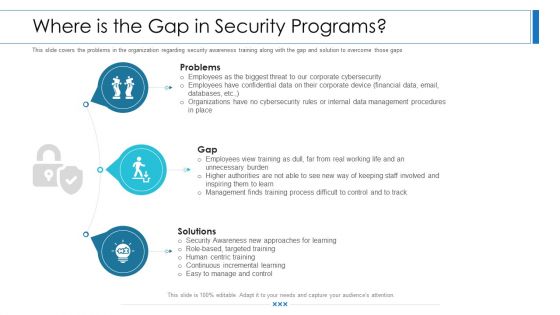
Workforce Security Realization Coaching Plan Where Is The Gap In Security Programs Ppt Show Master Slide PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a workforce security realization coaching plan where is the gap in security programs ppt show master slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Safety Initiatives Checklist For Effectively Managing Asset Security Themes PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this data safety initiatives checklist for effectively managing asset security themes pdf. Use them to share invaluable insights on system monitoring, data backup, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Shield Icon With Bitcoin Crypto Currency Symbol Ppt PowerPoint Presentation Pictures Skills PDF
Presenting this set of slides with name picture showing software security system ppt powerpoint presentation model slides pdf. This is a three stage process. The stages in this process are security shield icon with bitcoin crypto currency symbol. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
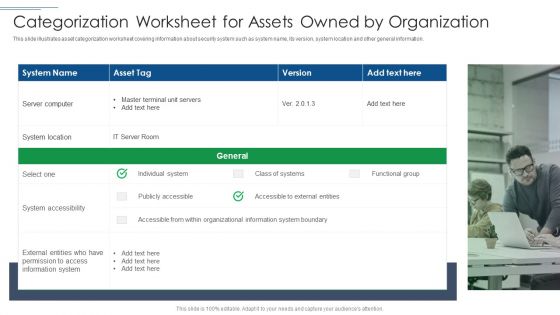
IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like System Location, System Accessibility, Information System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
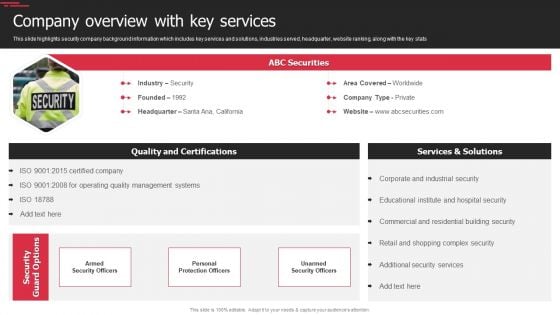
Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
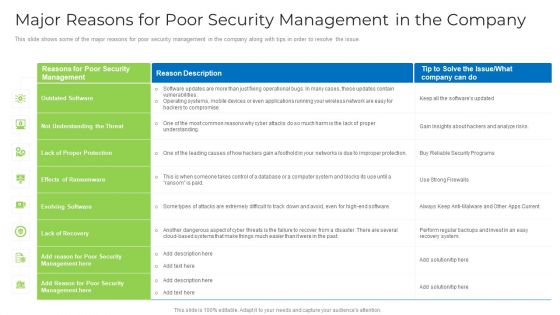
Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.

Optimization Of IoT Remote Monitoring Smart Locks Used To Increase Safety And Security IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. This Optimization Of IoT Remote Monitoring Smart Locks Used To Increase Safety And Security IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.
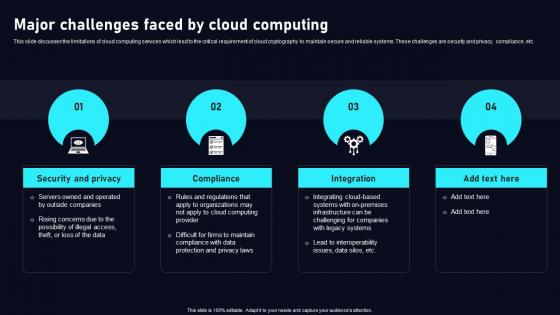
Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. QThere are so many reasons you need a Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
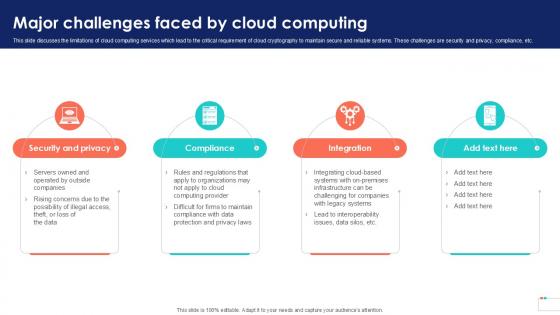
Major Challenges Faced By Data Security In Cloud Computing Ppt Sample
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. Do you know about Slidesgeeks Major Challenges Faced By Data Security In Cloud Computing Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
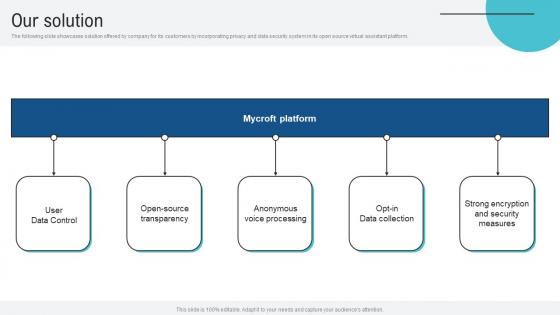
Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. This Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.
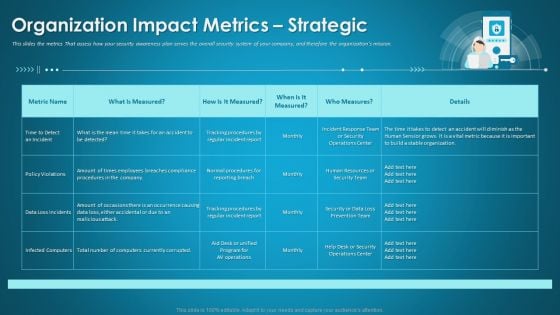
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
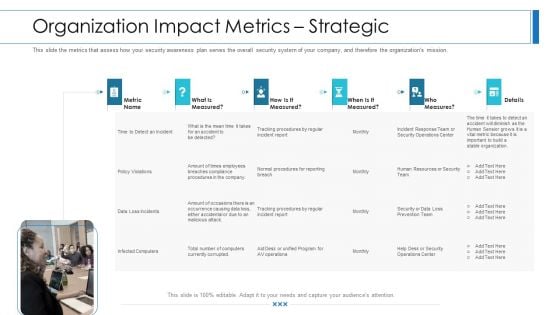
Workforce Security Realization Coaching Plan Organization Impact Metrics Strategic Infographics PDF
This slide the metrics that assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization impact metrics strategic infographics pdf. Use them to share invaluable insights on organization impact metrics strategicand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
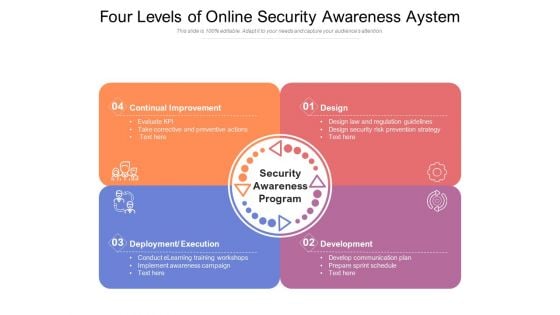
Four Levels Of Online Security Awareness Aystem Ppt PowerPoint Presentation Layouts Elements PDF
Presenting this set of slides with name four levels of online security awareness system ppt powerpoint presentation layouts elements pdf. This is a four stage process. The stages in this process are continual improvement, design, development, deployment, execution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
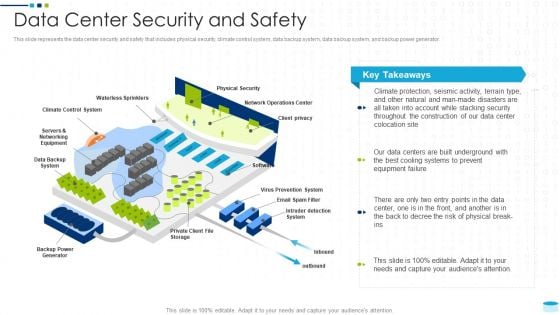
Data Center Infrastructure Management IT Data Center Security And Safety Demonstration PDF
This slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an awe inspiring pitch with this creative data center infrastructure management it data center security and safety demonstration pdf bundle. Topics like client privacy, physical security, waterless sprinklers, data backup system, virus prevention system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
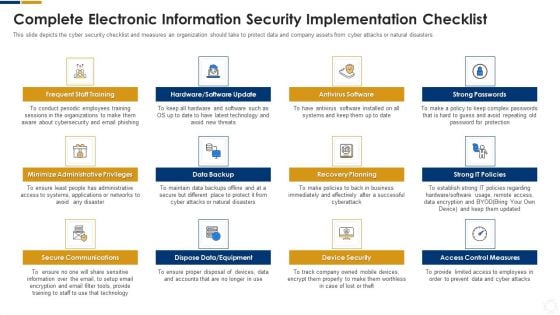
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V
This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols. Slidegeeks is here to make your presentations a breeze with Unlocking Potential IoTs Application Overview Of IoT Based Smart Home Security IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide briefly introduces IoT devices in smart home security with features. It also showcases the components of IoT security systems, such as hardware, software, and communication protocols.
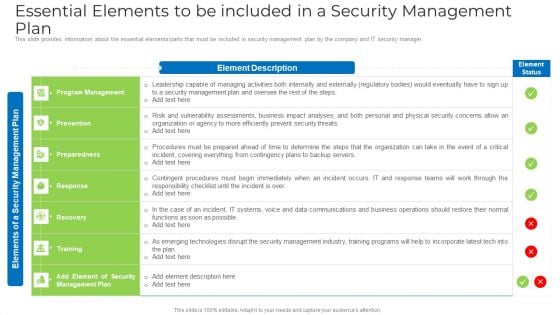
Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
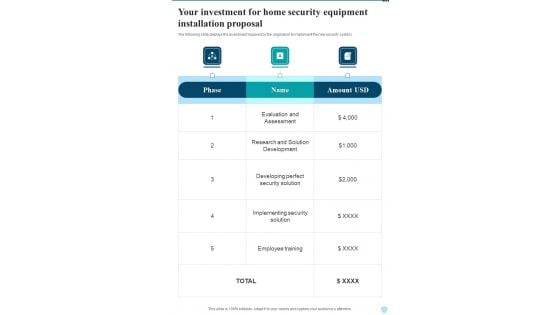
Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system. Presenting you an exemplary Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
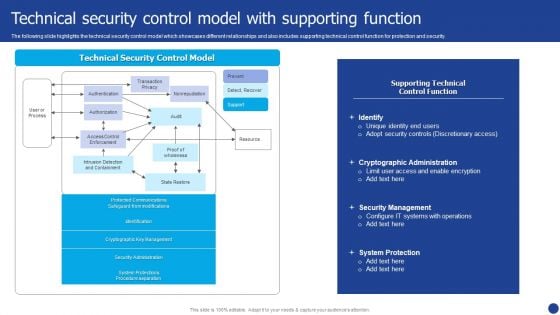
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Action Plan In Case Of Breaches Demonstration PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Action Plan In Case Of Breaches Demonstration PDF bundle. Topics like Security Breach, System Failure, Risk Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Activity Template PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration security operations implementation timeline activity template pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
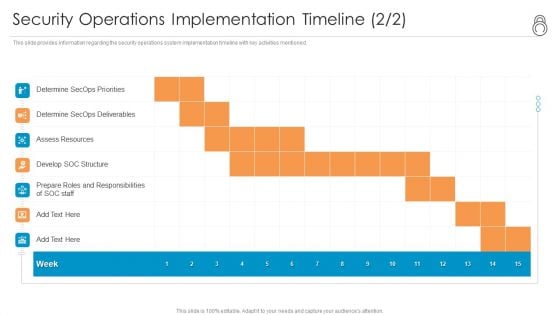
Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
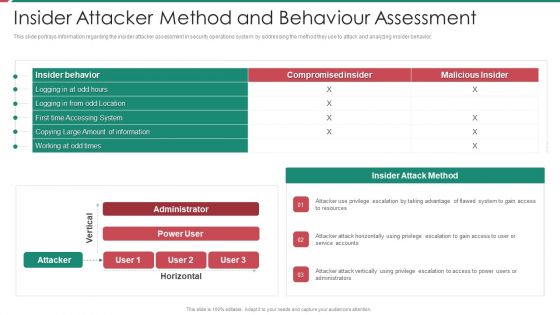
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
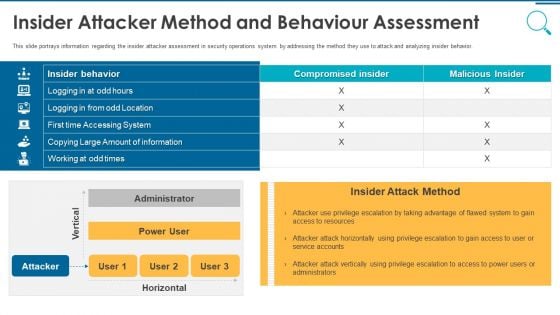
Information And Technology Security Operations Insider Attacker Method And Behaviour Assessment Inspiration PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this information and technology security operations insider attacker method and behaviour assessment inspiration pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
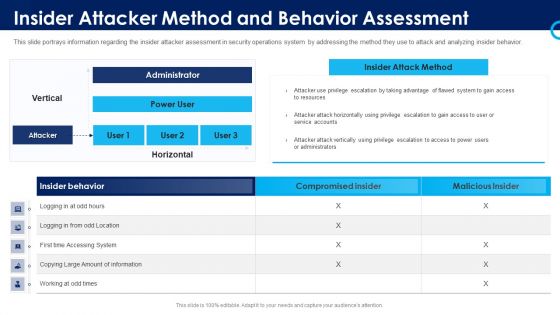
Organizational Security Solutions Insider Attacker Method And Behavior Assessment Introduction PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this organizational security solutions insider attacker method and behavior assessment introduction pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Internet PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Computer PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to The data is secure, security, business, technology, internet, computer. The prominent colors used in the PowerPoint template are Black, Gray, Yellow. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our internet PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Customers tell us our business PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. People tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. With our Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113 you will feel free. They drastically cut down the burden on you.
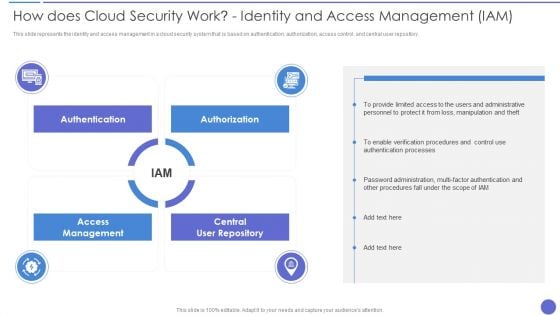
How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
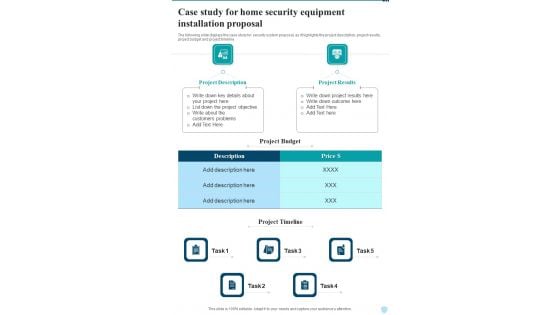
Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline Presenting you an exemplary Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
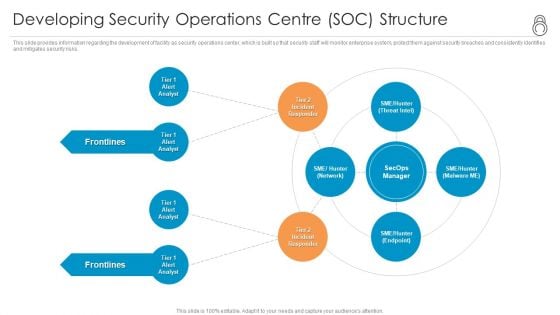
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
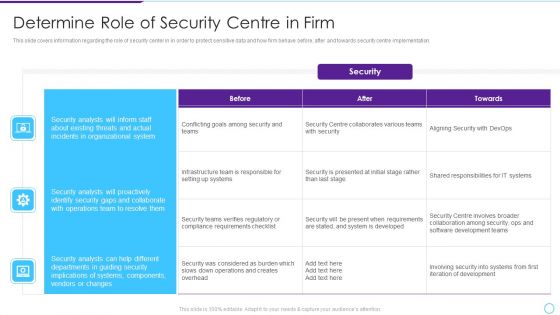
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































