System Security

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
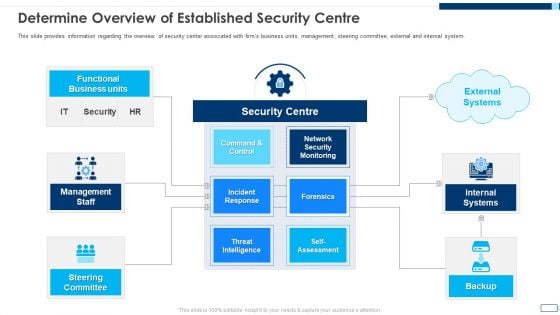
Evolving BI Infrastructure Determine Overview Of Established Security Centre Slides PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting evolving bi infrastructure determine overview of established security centre slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, internal systems, backup, functional business units. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
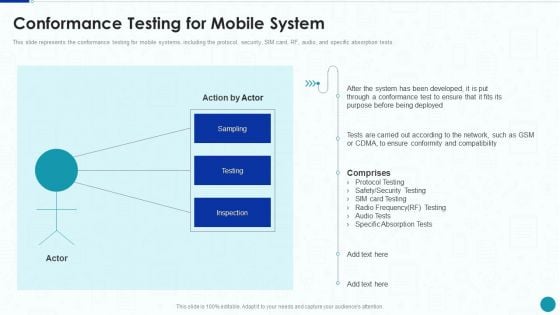
Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF
This slide represents the conformance testing for mobile systems, including the protocol, security, SIM card, RF, audio, and specific absorption tests. Deliver an awe inspiring pitch with this creative Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF bundle. Topics like Network, System, Security Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
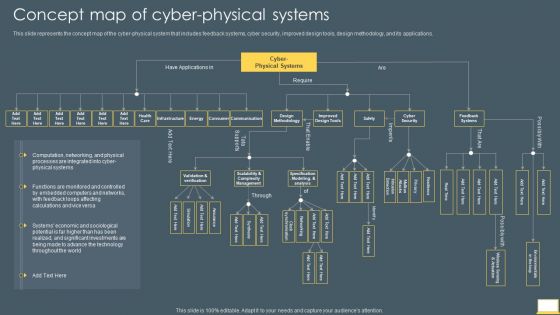
Cyber Intelligent Computing System Concept Map Of Cyber Physical Systems Formats PDF
This slide represents the concept map of the cyber physical system that includes feedback systems, cyber security, improved design tools, design methodology, and its applications. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Concept Map Of Cyber Physical Systems Formats PDF. Use them to share invaluable insights on Cyber Security, Feedback Systems, Improved Design Tools and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
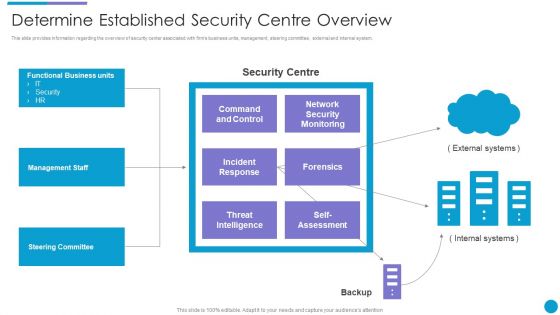
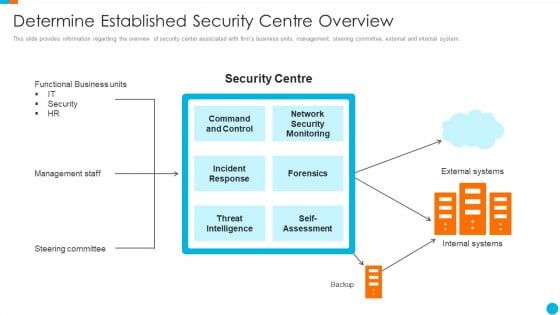
Major Techniques For Project Safety IT Determine Established Security Centre Overview Summary PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting major techniques for project safety it determine established security centre overview summary pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, functional business units, threat intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
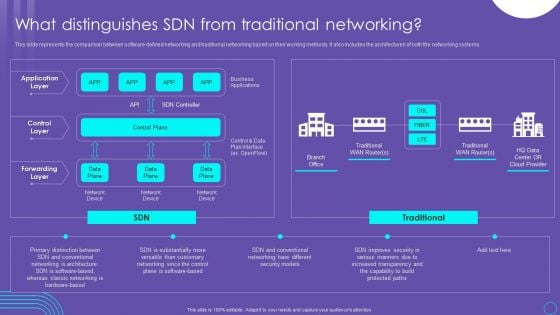
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.
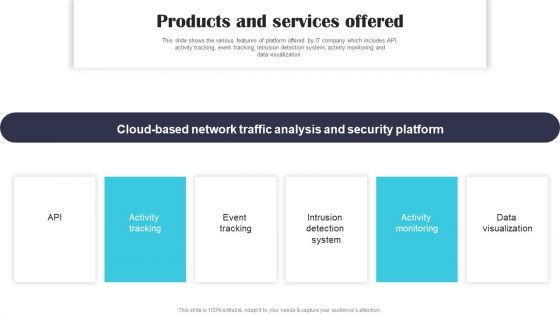
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Boost your pitch with our creative As A Service Deployment Approach Zero Trust Network Security Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
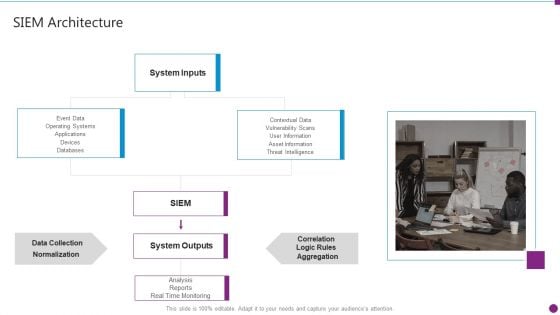
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Topics PDF
Presenting security information and event management strategies for financial audit and compliance siem architecture topics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like system inputs, system outputs, data collection, databases. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Analyzing The Impact Of Russia Ukraine Conflict On Gas Sector Russian Conflict Risk On Security Icons PDF
This slide showcases Russia invasion risk to security of Ukrainian gas transmission system GTS. It provides information about military intervention, instability zone, south stream project, etc. This is a analyzing the impact of russia ukraine conflict on gas sector russian conflict risk on security icons pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian conflict risk on security of ukrainian gas transportation system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
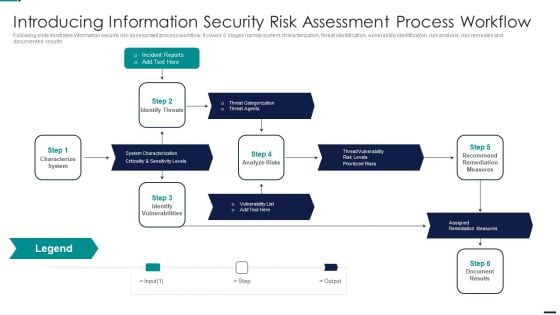
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
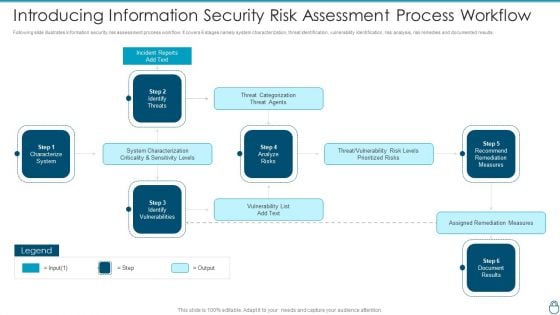
Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Recommender System Implementation Recommender System Implementation Challenges Download Pdf
This slide talks about the various difficulties faced while implementing recommendation systems. These challenges include significant investments needed, numerous choices available, complex onboarding procedures, privacy concerns, cold-start problem etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recommender System Implementation Recommender System Implementation Challenges Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Recommender System Implementation Recommender System Implementation Challenges Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the various difficulties faced while implementing recommendation systems. These challenges include significant investments needed, numerous choices available, complex onboarding procedures, privacy concerns, cold-start problem etc.
Fire Detection System And Protection System Icon Clipart PDF
Showcasing this set of slides titled Fire Detection System And Protection System Icon Clipart PDF. The topics addressed in these templates are Fire Detection, System Protection, System Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
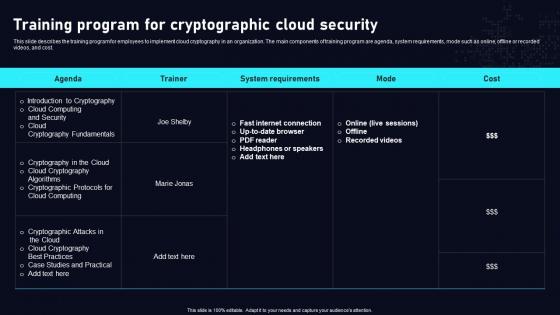
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Roles And Responsibilities Assigned In Quality Management Process Food Security Excellence Ppt Outline Design Templates PDF
This slide outlines roles and responsibilities such as project manager, quality manager, system integrator, etc. that are assigned to people who are involved in quality management process. Presenting roles and responsibilities assigned in quality management process food security excellence ppt outline design templates pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like project manager, technical manager, quality manager, system integrator, test team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
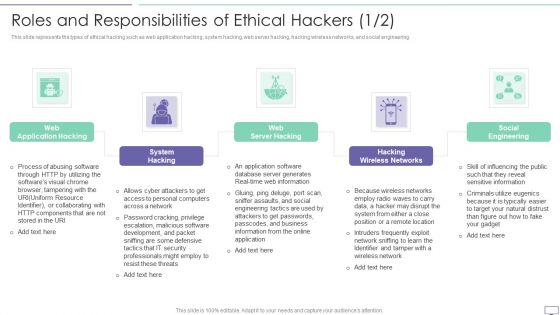
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF. Use them to share invaluable insights on Key Solutions Services, Intelligent Smart Devices, Operating System Integration, Service Delivery Model and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Implementation Framework Essential Contingency Plan Strategies Ppt Portfolio Introduction PDF
Presenting this set of slides with name cyber security implementation framework essential contingency plan strategies ppt portfolio introduction pdf. The topics discussed in these slides are contingency considerations, contingency solutions, vendors coordination, system backups. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Technology PowerPoint Templates because we provide the means to project your views. Download and present our Business PowerPoint Templates because this template can project the path to sucess that you have charted. Use our Security PowerPoint Templates because you can Explore the various hues and layers existing in your in your plans and processes using this slide. Use our Computer PowerPoint Templates because it demonstrates the seeds of many of our successes. Download and present our Shapes PowerPoint Templates because the Gear train is a basic element of living and daily business.Use these PowerPoint slides for presentations relating to Lock laptop keyboard safety security on the internet, technology, Security, business, shapes, computer. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. People tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Flirty. Presenters tell us our technology PowerPoint templates and PPT Slides are Pretty. PowerPoint presentation experts tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 provide great value for your money. Be assured of finding the best projection to highlight your words. Customers tell us our on PowerPoint templates and PPT Slides are Reminiscent. Customers tell us our Laptop With Lock Internet Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Fantastic. Customers tell us our security PowerPoint templates and PPT Slides are Stunning. Develop their craving for your creativity. Become a brand name with our Laptop With Lock Internet Security PowerPoint Templates Ppt Backgrounds For Slides 1112.
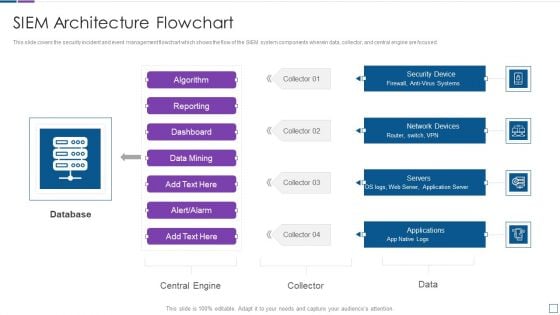
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Tachometer:- You have a good idea of the roadmap to your desired destination. Use our Internet PowerPoint Templates because, Display your ideas and highlight thei ability to accelerate the the growth of your company and you. Use our Communication PowerPoint Templates because,Explain the process by which you intend to right it. Use our Security PowerPoint Templates because, Build on your foundation or prepare for change ahead to enhance the future. Use our Symbol PowerPoint Templates because, You have the plans to increase the strength of your business relationships.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Orange Soak in the energy our Yellow Computer Folder With Golden Key Security PowerPoint Templates And PowerPoint Themes 1112 emit. Your thoughts will find them exhilirating.
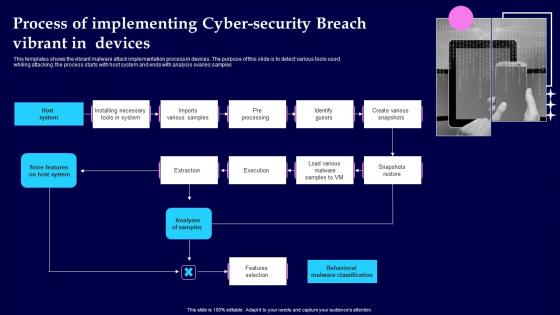
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cybersecurity What Is Electronic Information Security And How Does It Work Ppt Model Shapes PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting cybersecurity what is electronic information security and how does it work ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, devices, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Shield Icon With Lock And Tick Mark Ppt PowerPoint Presentation Pictures Sample
Presenting this set of slides with name security shield icon with lock and tick mark ppt powerpoint presentation pictures sample. This is a three stage process. The stages in this process are security shield icon with lock and tick mark. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Banknote Cash Currency Security Vector Icon Ppt PowerPoint Presentation Infographics Shapes
Presenting this set of slides with name banknote cash currency security vector icon ppt powerpoint presentation infographics shapes. This is a one stage process. The stage in this process is banknote cash currency security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enhanced Protection Corporate Event Administration Security And Operational Tasks Maintenance Checklist Slides PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security and operational tasks maintenance checklist slides pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key And Lock Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our Technology PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download our Shapes PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Present our Business PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime.Use these PowerPoint slides for presentations relating to Protect your computer, Security, Technology, Business, Shapes, Computer. The prominent colors used in the PowerPoint template are Yellow, Gray, Blue. Get fascinated by our Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213. They will keep attracting your attention.
Vector Illustration Of IT Security Measures For Strong Protection Ppt PowerPoint Presentation File Outline PDF
Persuade your audience using this vector illustration of it security measures for strong protection ppt powerpoint presentation file outline pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustration of it security measures for strong protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Corporate Security And Risk Management Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This corporate security and risk management ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

CASB 2 0 IT Training Program For Cloud Access Security Broker
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Training Program For Cloud Access Security Broker was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Training Program For Cloud Access Security Broker. This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training.

Global Cloud Based Email Security Market Industry Challenges Ppt Slides Structure PDF
Presenting this set of slides with name global cloud based email security market industry challenges ppt slides structure pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Image Of Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0713
Highlight your drive with our Image Of Internet Security PowerPoint Templates PPT Backgrounds For Slides. Prove the fact that you have control. Go the distance with our Security PowerPoint Templates. Maintain the pace till the end. Draw on the energy of our Technology PowerPoint Templates. Your thoughts will perk up. Our Image Of Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0713 will cause a celebration. Put your audience in a festive mood.
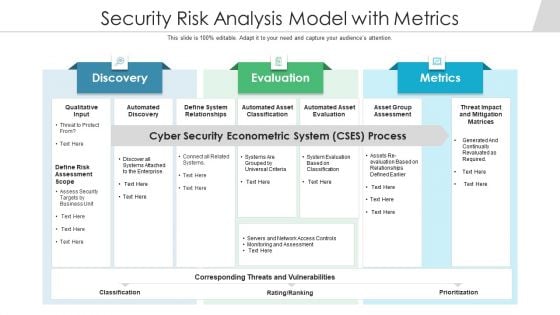
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Strategy Process 3d Render Of Round Chain Security Concept Icons Images
Your Grasp Of Economics Is Well Known. Help Your Audience Comprehend Issues With Our Business Strategy Process 3d Render Of Round Chain Security Concept Icons Images Powerpoint Templates.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Effective IT Risk Management Process Information Security Risk Assessment Formats PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this NAMEEEEEE. Use them to share invaluable insights on system failure, potential, vulnerability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
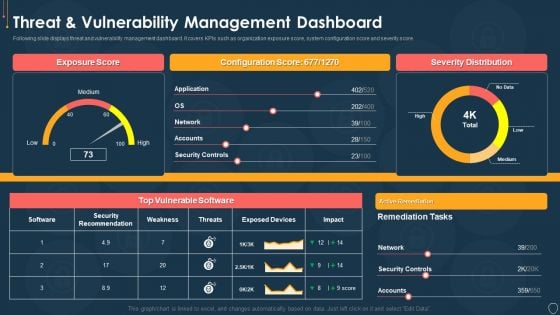
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
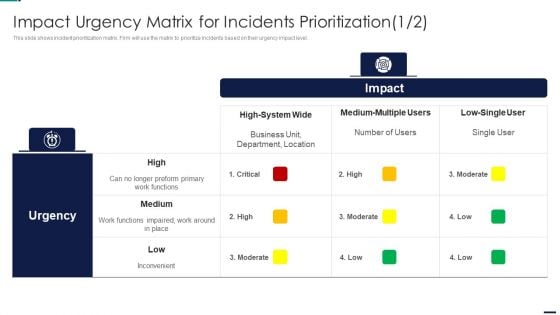
Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF bundle. Topics like High System Wide, Medium Multiple Users, Low Single User, Inconvenient can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
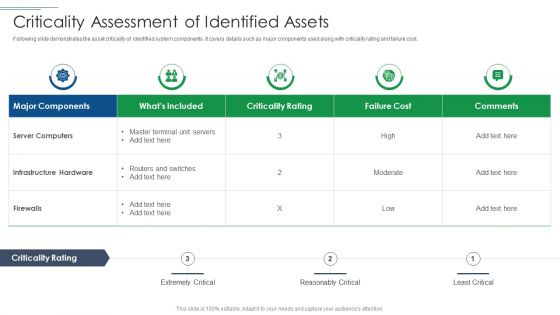
IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF bundle. Topics like Server Computers, Infrastructure Hardware, Failure Cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
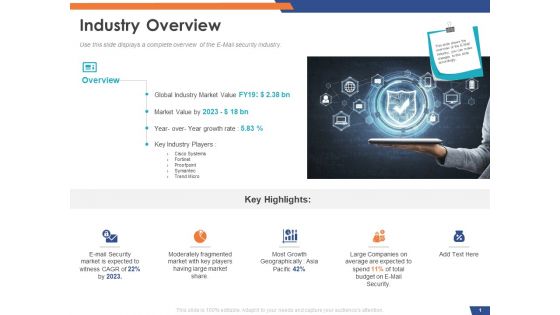
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Golden Key With Coins Investment Security PowerPoint Templates And PowerPoint Themes 0812
Golden Key With Coins Investment Security PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with golden key with coins Keep up the fight with our Golden Key With Coins Investment Security PowerPoint Templates And PowerPoint Themes 0812. Be assured of eventual achievement.
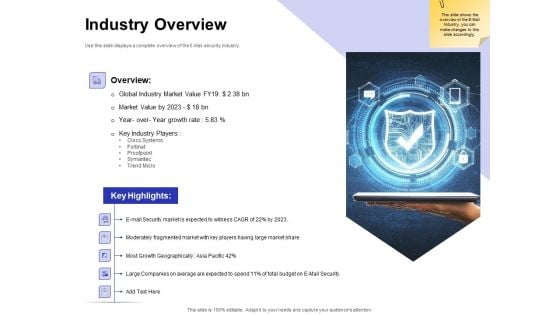
Global Cloud Based Email Security Market Industry Overview Ppt Slides Design Inspiration PDF
Presenting this set of slides with name global cloud based email security market industry overview ppt slides design inspiration pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Challenges Of Vpn Based Remote Access Zero Trust Network Security Ideas Pdf
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. There are so many reasons you need a Challenges Of Vpn Based Remote Access Zero Trust Network Security Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues.

Access Control Application Account Security Lock Ppt PowerPoint Presentation File Slide Portrait
This is a access control application account security lock ppt powerpoint presentation file slide portrait. This is a two stage process. The stages in this process are access rights, access management, business.


 Continue with Email
Continue with Email

 Home
Home


































