Threat Intelligence
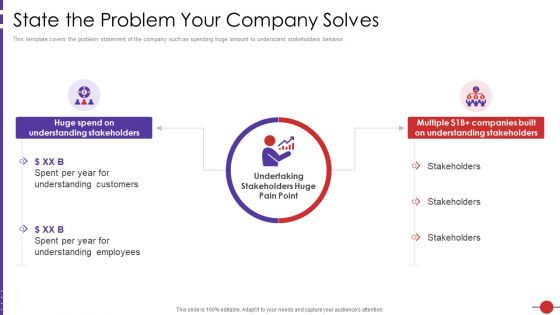
Artificial Intelligence Platform State The Problem Your Company Solves Ppt Pictures File Formats PDF
This template covers the problem statement of the company such as spending huge amount to understand stakeholders behavior. Presenting artificial intelligence platform state the problem your company solves ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like state the problem your company solves. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
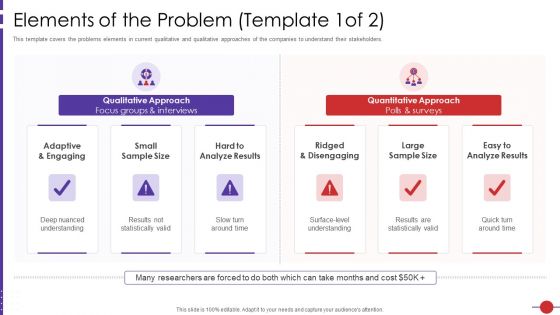
Artificial Intelligence Platform Elements Of The Problem Analyze Ppt Outline Graphics Template PDF
This template covers the problems elements in current qualitative and qualitative approaches of the companies to understand their stakeholders. Presenting artificial intelligence platform elements of the problem analyze ppt outline graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like elements of the problem. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Artificial Intelligence Investor State The Problem Your Company Solves Introduction PDF
This template covers the problem statement of the company such as spending huge amount to understand stakeholders behavior. Presenting artificial intelligence investor state the problem your company solves introduction pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like state the problem your company solves. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
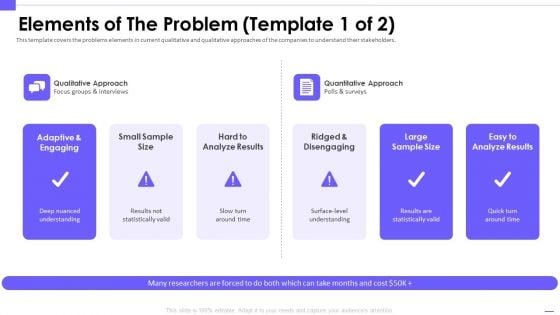
Artificial Intelligence Investor Elements Of The Problem Template 1 Of Approach Themes PDF
This template covers the problems elements in current qualitative and qualitative approaches of the companies to understand their stakeholders. Presenting artificial intelligence investor elements of the problem template 1 of approach themes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like analyze, surveys, qualitative approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

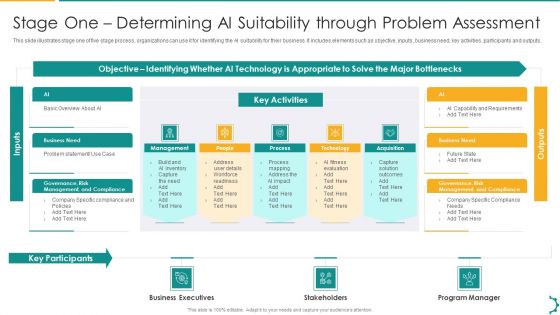
Artificial Intelligence Transformation Playbook Stage One Determining Ai Suitability Through Problem Assessment Introduction PDF
This slide illustrates stage one of five stage process, organizations can use it for identifying the AI suitability for their business. It includes elements such as objective, inputs, business need, key activities, participants and outputs. This is a artificial intelligence transformation playbook stage one determining ai suitability through problem assessment introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business executives, stakeholders, program manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Artificial Intelligence Playbook Stage One Determining AI Suitability Through Problem Assessment Rules PDF
This slide illustrates stage one of five stage process, organizations can use it for identifying the AI suitability for their business. It includes elements such as objective, inputs, business need, key activities, participants and outputs. Deliver and pitch your topic in the best possible manner with this artificial intelligence playbook stage one determining ai suitability through problem assessment rules pdf. Use them to share invaluable insights on ai technology, manageemnt, process, technology, acquisition and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
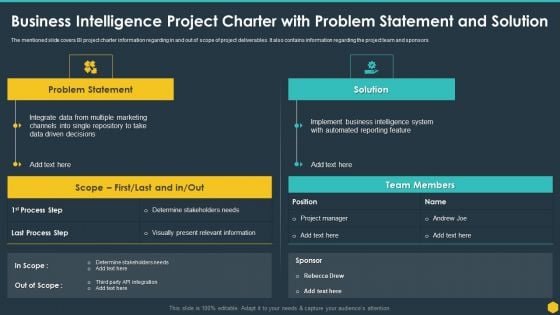
Business Intelligence Project Charter With Problem Statement And Solution BI Transformation Toolset Themes PDF
The mentioned slide covers BI project charter information regarding in and out of scope of project deliverables. It also contains information regarding the project team and sponsors Deliver and pitch your topic in the best possible manner with this Business Intelligence Project Charter With Problem Statement And Solution BI Transformation Toolset Themes PDF. Use them to share invaluable insights on Team Members, Marketing, Implement Business, Determine and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
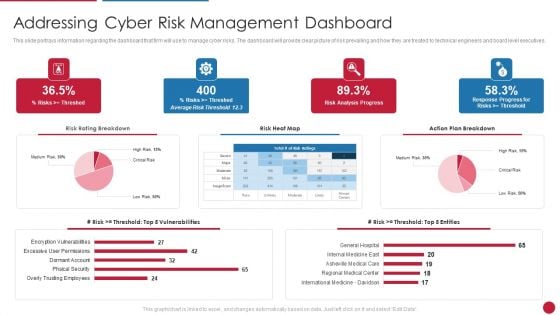
Facilitating IT Intelligence Architecture Addressing Cyber Risk Management Dashboard Professional PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber risks. The dashboard will provide clear picture of risk prevailing and how they are treated to technical engineers and board level executives.Deliver and pitch your topic in the best possible manner with this Facilitating IT Intelligence Architecture Addressing Cyber Risk Management Dashboard Professional PDF Use them to share invaluable insights on International Medicine Davidson, Regional Medical Center, Asheville Medical Care and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
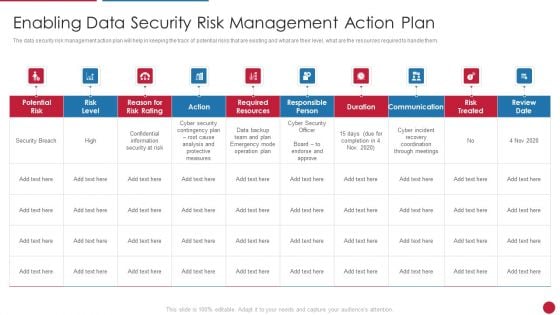
Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Intelligence And Big Data Analytics Business Case And Roadmap For Data Analytics Designs PDF
This slide shows the detailed document covering the problem statement, companys vision, key processes and outcomes for the data analytics project. Presenting business intelligence and big data analytics business case and roadmap for data analytics designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like problem statement, vision and objectives, process, analytical capabilities, key owners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
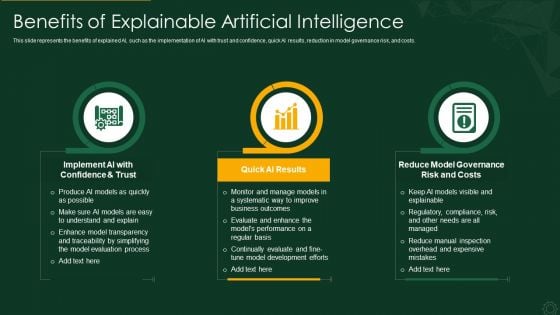
Explainable AI XAI Frameworks IT Benefits Of Explainable Artificial Intelligence Brochure PDF
This slide represents the benefits of explained AI, such as the implementation of AI with trust and confidence, quick AI results, reduction in model governance risk, and costs. This is a explainable ai xai frameworks it benefits of explainable artificial intelligence brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce model governance risk and costs, quick ai results, implement ai with confidence and trust. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
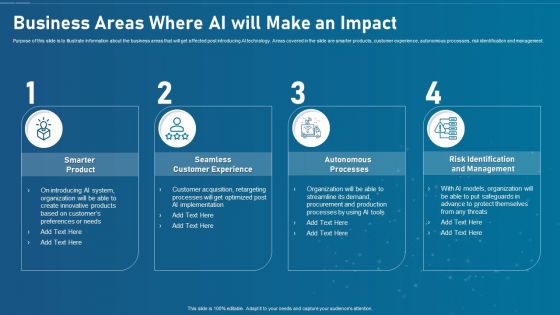
Artificial Intelligence Transformation Playbook Business Areas Where Ai Will Make An Impact Topics PDF
Purpose of this slide is to illustrate information about the business areas that will get affected post introducing AI technology. Areas covered in the slide are smarter products, customer experience, autonomous processes, risk identification and management. Presenting artificial intelligence transformation playbook business areas where ai will make an impact topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like smarter product, seamless customer experience, autonomous processes, risk identification and management . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Artificial Intelligence Transformation Playbook Kpi Dashboard For Tracking Business Performance Designs PDF
Mentioned slide portrays KPI dashboard that can be used by organizations to measure their business performance post AI introduction. KPIS covered here are progress, Before versus After AI Implementation, risks and issues. Deliver an awe inspiring pitch with this creative artificial intelligence transformation playbook kpi dashboard for tracking business performance designs pdf bundle. Topics like risk and issues, progress, performance kpis, before versus after all implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
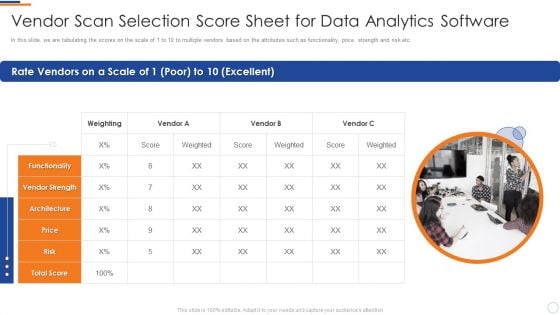
Business Intelligence And Big Vendor Scan Selection Score Sheet For Data Analytics Designs PDF
In this slide, we are tabulating the scores on the scale of 1 to 10 to multiple vendors based on the attributes such as functionality, price, strength and risk etc. Presenting business intelligence and big vendor scan selection score sheet for data analytics designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like rate vendors vendor strength, price, risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
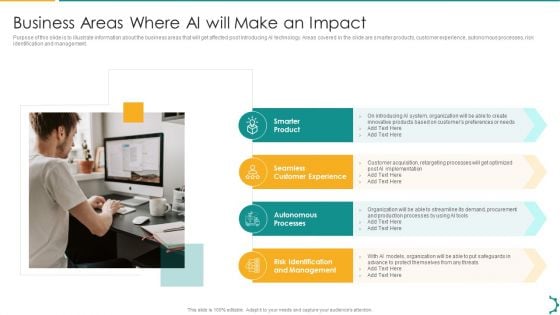
Artificial Intelligence Playbook Business Areas Where Ai Will Make An Impact Clipart PDF
Purpose of this slide is to illustrate information about the business areas that will get affected post introducing AI technology. Areas covered in the slide are smarter products, customer experience, autonomous processes, risk identification and management. Presenting artificial intelligence playbook business areas where ai will make an impact clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like smarter product, seamless customer experience, autonomous processes, risk identification and management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
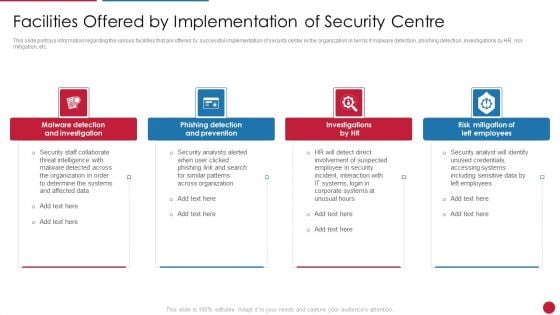
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Artificial Intelligence For IT Operations Playbook Stage Three Selection Of Right Solution Background PDF
This slide shows stage three of five stage process, businesses can use it to ensure that they are selecting the best fit technology. Elements covered are objective, inputs, business need, key activities, participants and outputs.Deliver an awe inspiring pitch with this creative Artificial Intelligence For IT Operations Playbook Stage Three Selection Of Right Solution Background PDF bundle. Topics like Risk Management, Governance Risk, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Analysis And BI Playbook Business Intelligence And Predictive Analytics Challenges Slides PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Want to ace your presentation in front of a live audience Our Information Analysis And BI Playbook Business Intelligence And Predictive Analytics Challenges Slides PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Data Interpretation And Analysis Playbook Business Intelligence And Predictive Analytics Challenges Template PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting data interpretation and analysis playbook business intelligence and predictive analytics challenges template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like security vulnerabilities, operationalizing, perform analysis, deployed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data And Analytics Playbook Business Intelligence And Predictive Analytics Challenges Template PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting Data And Analytics Playbook Business Intelligence And Predictive Analytics Challenges Template PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Challenges, Data Science, Operationalizing Data Science. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Administered Data And Analytic Quality Playbook Business Intelligence And Predictive Download PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Deliver and pitch your topic in the best possible manner with this Administered Data And Analytic Quality Playbook Business Intelligence And Predictive Download PDF Use them to share invaluable insights on Common Misconception, Operationalizing, Production Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
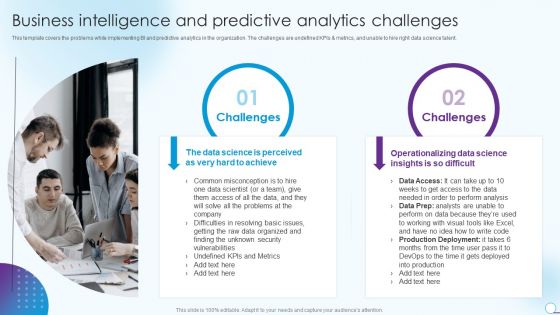
Information Analytics And Ml Strategy Playbook Business Intelligence And Predictive Analytics Challenges Structure PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. This is a Information Analytics And Ml Strategy Playbook Business Intelligence And Predictive Analytics Challenges Structure PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operationalizing Data Science, Unknown Security, Metrics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Raw Data Organized, Security Vulnerabilities, Perform Analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Transformation Toolkit Competitive Intelligence Information Analysis Business Case And Roadmap For Data Analytics Ideas PDF
This slide shows the detailed document covering the problem statement, companys vision, key processes and outcomes for the data analytics project Present like a pro with Transformation Toolkit Competitive Intelligence Information Analysis Business Case And Roadmap For Data Analytics Ideas PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Artificial Intelligence Machine Learning Deep Learning Where Is AI Used Ppt PowerPoint Presentation Slides Deck PDF
Presenting this set of slides with name artificial intelligence machine learning deep learning where is ai used ppt powerpoint presentation slides deck pdf. This is a twelve stage process. The stages in this process are customer experience, supply chain, human resources, fraud detection, knowledge creation, research and development, predictive analytics, real time operations management, customer services, risk management and analytics, customer insight, pricing and promotion. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Artificial Intelligence Gaming Industry Fund Raising Elevator What Is Our Exit Strategy Summary PDF
The following slide displays the exit strategy of the o rganization which can help in reducing the risk, these strategies are merger and acquisition, management buyout and initial public offering This is a artificial intelligence gaming industry fund raising elevator what is our exit strategy summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merger and acquisition, management buyout, initial public offering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Artificial Intelligence Transformation Playbook Stage One Questionnaire Results And Key Considerations Designs PDF
Mentioned slide displays the results of assessment questionnaire along with key considerations about the AI technology. It also showcases information about the capabilities of AI approach. Presenting artificial intelligence transformation playbook stage one questionnaire results and key considerations designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like incremental gains, cloud first and shared services, enhanced user experience, minimal risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
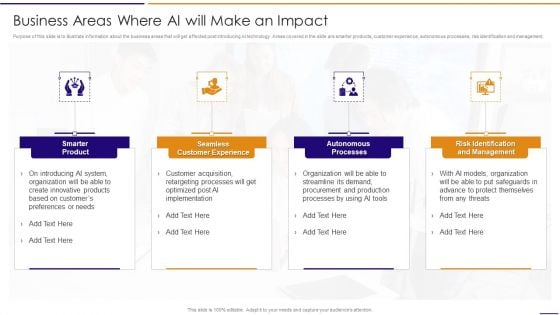
Artificial Intelligence For IT Operations Playbook Business Areas Where AI Will Make An Impact Demonstration PDF
Purpose of this slide is to illustrate information about the business areas that will get affected post introducing AI technology. Areas covered in the slide are smarter products, customer experience, autonomous processes, risk identification and management.This is a Artificial Intelligence For IT Operations Playbook Business Areas Where AI Will Make An Impact Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Smarter Product, Customer Experience, Autonomous Processes You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
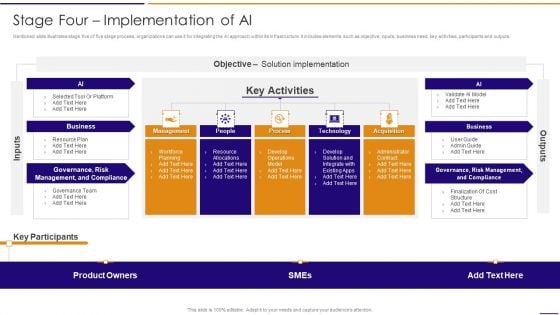
Artificial Intelligence For IT Operations Playbook Stage Four Implementation Of AI Introduction PDF
Mentioned slide illustrates stage five of five stage process, organizations can use it for integrating the AI approach within its infrastructure. It includes elements such as objective, inputs, business need, key activities, participants and outputs.Deliver and pitch your topic in the best possible manner with this Artificial Intelligence For IT Operations Playbook Stage Four Implementation Of AI Introduction PDF Use them to share invaluable insights on Management Compliance, Risk Management, Product Owners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
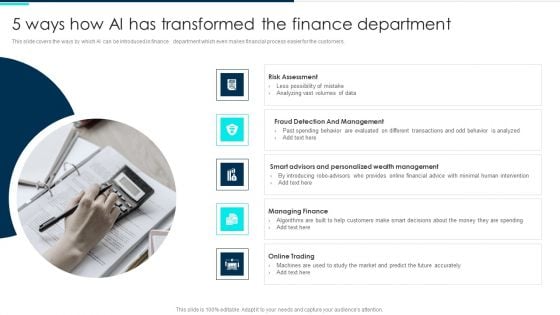
5 Ways How Ai Has Transformed The Finance Department Deploying Artificial Intelligence In Business Slides PDF
This slide covers the ways by which AI can be introduced in finance department which even makes financial process easier for the customers.This is a 5 Ways How Ai Has Transformed The Finance Department Deploying Artificial Intelligence In Business Slides PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Assessment, Detection Management, personalized management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
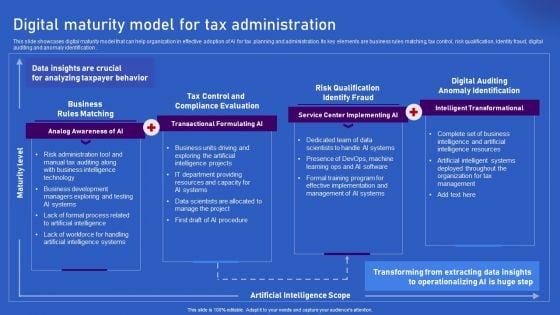
Ways Artificial Intelligence Is Transforming Finance Sector Digital Maturity Model For Tax Administration Portrait PDF
This slide showcases digital maturity model that can help organization in effective adoption of AI for tax planning and administration. Its key elements are business rules matching, tax control, risk qualification, Identity fraud, digital auditing and anomaly identification . There are so many reasons you need a Ways Artificial Intelligence Is Transforming Finance Sector Digital Maturity Model For Tax Administration Portrait PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Ways Artificial Intelligence Is Transforming Finance Sector Importance Of AI In Stock Market Projection Icons PDF
This slide showcases benefits of leveraging AI solutions for making stock market projections. Key benefits of using AI for market projections are increase accuracy, faster analysis, risk management and cost savings. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Ways Artificial Intelligence Is Transforming Finance Sector Importance Of AI In Stock Market Projection Icons PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
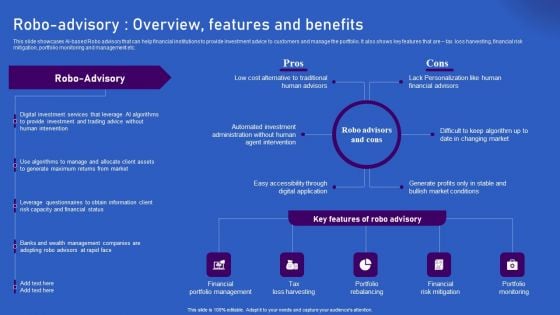
Ways Artificial Intelligence Is Transforming Finance Sector Robo Advisory Overview Features And Benefits Portrait PDF
This slide showcases AI-based Robo advisory that can help financial institutions to provide investment advice to customers and manage the portfolio. It also shows key features that are tax loss harvesting, financial risk mitigation, portfolio monitoring and management etc. Want to ace your presentation in front of a live audience Our Ways Artificial Intelligence Is Transforming Finance Sector Robo Advisory Overview Features And Benefits Portrait PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
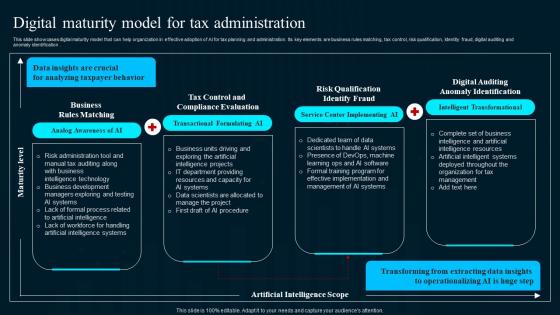
Digital Maturity Model For Tax Administration Artificial Intelligence Applications Structure Pdf
This slide showcases digital maturity model that can help organization in effective adoption of AI for tax planning and administration. Its key elements are business rules matching, tax control, risk qualification, Identity fraud, digital auditing and anomaly identification .Slidegeeks is here to make your presentations a breeze with Digital Maturity Model For Tax Administration Artificial Intelligence Applications Structure Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide showcases digital maturity model that can help organization in effective adoption of AI for tax planning and administration. Its key elements are business rules matching, tax control, risk qualification, Identity fraud, digital auditing and anomaly identification .
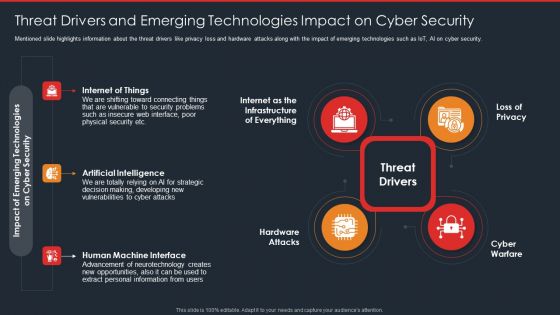
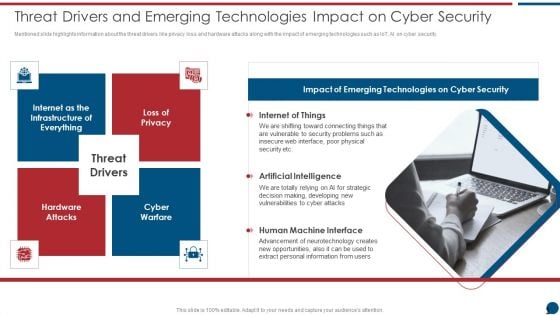
Data Safety Initiatives Threat Drivers And Emerging Technologies Impact On Cyber Security Brochure PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a data safety initiatives threat drivers and emerging technologies impact on cyber security brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat drivers, loss privacy, cyber warfare, hardware attacks, artificial intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
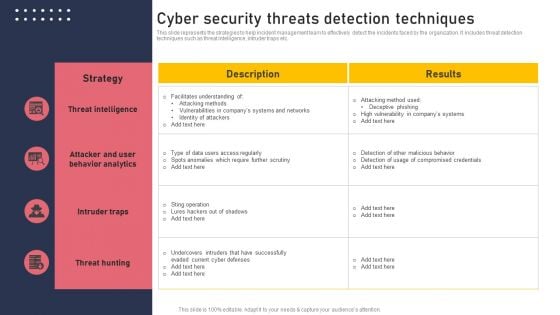
Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Data Interpretation And Analysis Playbook How To Fix The Business Intelligence Problem Data Analytics Playbook Sample PDF
This template covers the solution for BI problems such as analytics transformation and business intelligence program. It also depicts that switching to next-generation analytics platform that gives business users data-driven insights. Presenting data interpretation and analysis playbook how to fix the business intelligence problem data analytics playbook sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like analytics, business intelligence, predictive analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Analysis And BI Playbook How To Fix The Business Intelligence Problem Data Analytics Playbook Designs PDF
This template covers the solution for BI problems such as analytics transformation and business intelligence program. It also depicts that switching to next generation analytics platform that gives business users data-driven insights. Get a simple yet stunning designed Information Analysis And BI Playbook How To Fix The Business Intelligence Problem Data Analytics Playbook Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Analysis And BI Playbook How To Fix The Business Intelligence Problem Data Analytics Playbook Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
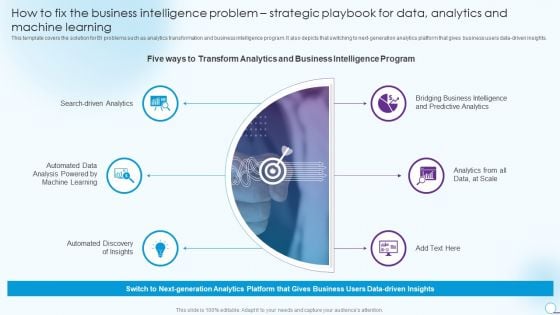
How To Fix The Business Intelligence Problem Strategic Playbook For Data Analytics And Machine Learning Designs PDF
This template covers the solution for BI problems such as analytics transformation and business intelligence program. It also depicts that switching to next generation analytics platform that gives business users data driven insights. This is a How To Fix The Business Intelligence Problem Strategic Playbook For Data Analytics And Machine Learning Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automated Data Analysis, Search Driven Analytics, Predictive Analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ml And Big Data In Information Technology Processes Need For Artificial Intelligence In IT Operations Structure PDF
The purpose of the following slide is to show the need of artificial intelligence in the organizations, these problems can be no real time analysis , poor monitoring From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Ml And Big Data In Information Technology Processes Need For Artificial Intelligence In IT Operations Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
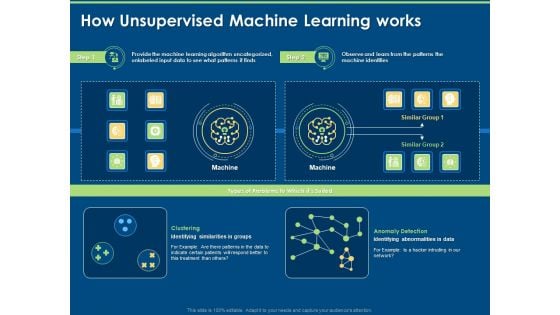
Artificial Intelligence Machine Learning Deep Learning How Unsupervised Machine Learning Works Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name artificial intelligence machine learning deep learning how unsupervised machine learning works ppt powerpoint presentation professional themes pdf. This is a two stage process. The stages in this process are machine, clustering, anomaly detection, problems. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enterprise Problem Solving And Intellect Business Intelligence KPI Metrics Profit Ppt PowerPoint Presentation Infographic Template Portrait PDF
Presenting this set of slides with name enterprise problem solving and intellect business intelligence kpi metrics profit ppt powerpoint presentation infographic template portrait pdf. This is a four stage process. The stages in this process are days since last accident, net profit margin, remaining inventory, response time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
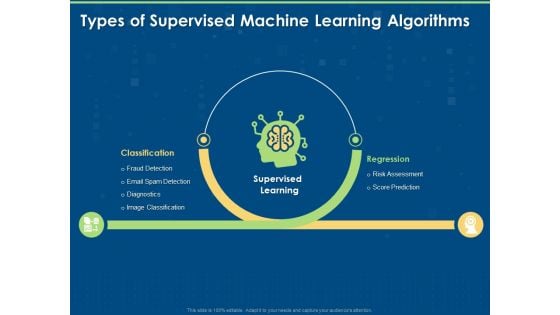
Artificial Intelligence Machine Learning Deep Learning Types Of Supervised Machine Learning Algorithms Ppt PowerPoint Presentation Outline Topics PDF
Presenting this set of slides with name artificial intelligence machine learning deep learning types of supervised machine learning algorithms ppt powerpoint presentation outline topics pdf. This is a two stage process. The stages in this process are classification, risk assessment, regression, supervised learning, risk assessment, score prediction, fraud detection, email spam detection, diagnostics, image classification. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
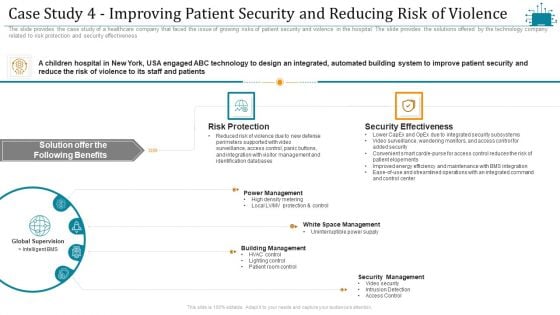
Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Threat And Caution Icon With Explanatory Mark Ppt PowerPoint Presentation Portfolio Objects PDF
Persuade your audience using this threat and caution icon with explanatory mark ppt powerpoint presentation portfolio objects pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including threat and caution icon with explanatory mark. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Financial Risk Indicator With Threat Symbol Vector Icon Ppt PowerPoint Presentation Summary PDF
Persuade your audience using this financial risk indicator with threat symbol vector icon ppt powerpoint presentation summary pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including financial risk indicator with threat symbol vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Crime With Eye And Threat Symbol Ppt PowerPoint Presentation File Background PDF
Persuade your audience using this online crime with eye and threat symbol ppt powerpoint presentation file background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including online crime with eye and threat symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
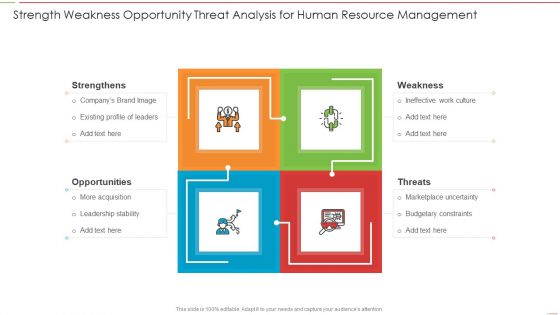
Strength Weakness Opportunity Threat Analysis For Human Resource Management Slides PDF
Persuade your audience using this Strength Weakness Opportunity Threat Analysis For Human Resource Management Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strength, Weakness, Threats, Opportunity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
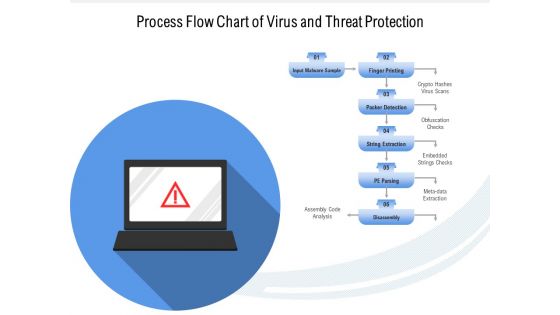
Process Flow Chart Of Virus And Threat Protection Ppt PowerPoint Presentation File Layout PDF
Persuade your audience using this process flow chart of virus and threat protection ppt powerpoint presentation file layout pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including analysis, extraction, obfuscation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
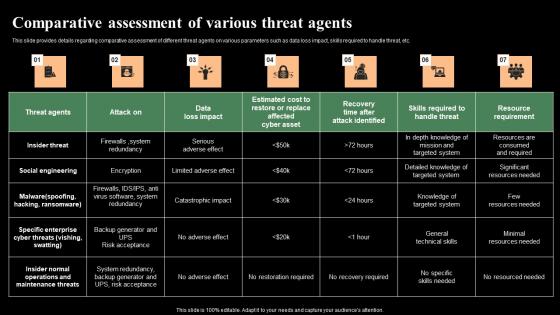
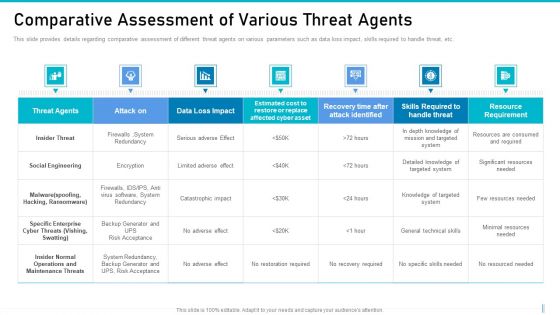
Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Find a pre-designed and impeccable Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc.
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
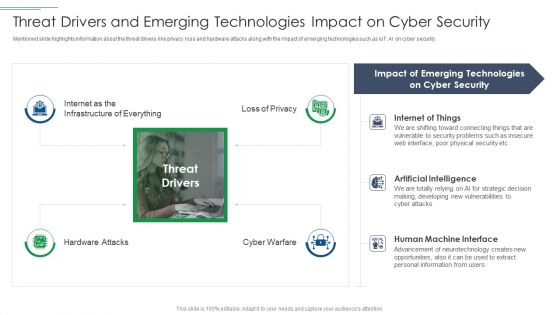
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
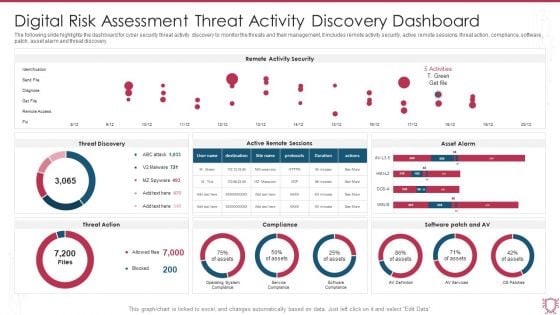
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Management For Organization Essential Assets Comparative Assessment Of Various Threat Professional PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets comparative assessment of various threat professional pdf bundle. Topics like threat agents, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
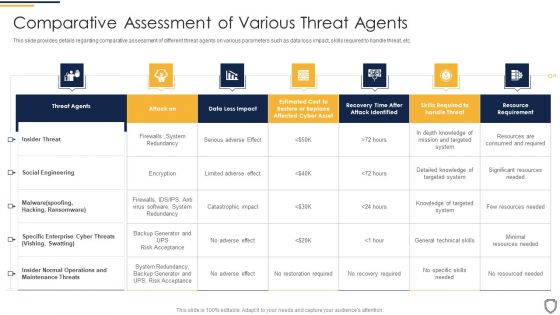
Corporate Security And Risk Management Comparative Assessment Of Various Threat Agents Slides PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management comparative assessment of various threat agents slides pdf. Use them to share invaluable insights on comparative assessment of various threat agents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
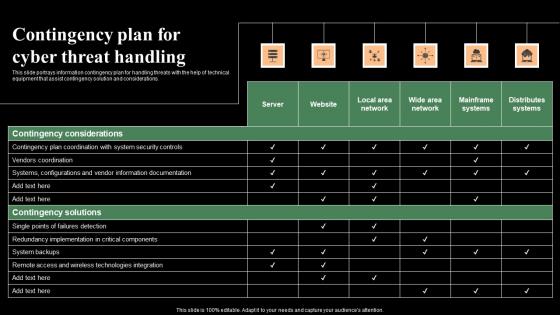
Contingency Plan For Cyber Threat Handling Monitoring Digital Assets Formats Pdf
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Boost your pitch with our creative Contingency Plan For Cyber Threat Handling Monitoring Digital Assets Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations.
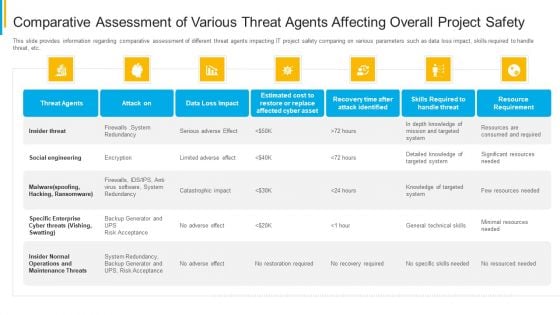
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
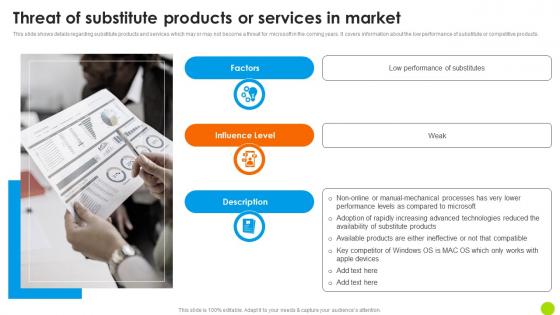
Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF
This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF can be your best option for delivering a presentation. Represent everything in detail using Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products.
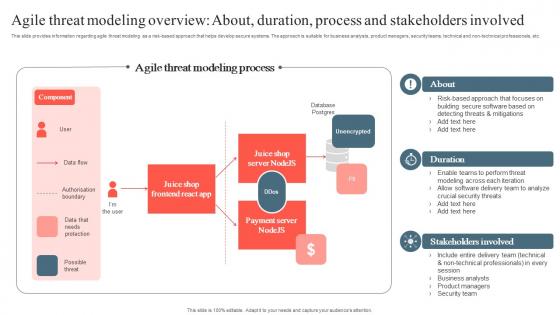
Playbook To Remediate False Agile Threat Modeling Overview About Download Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Want to ace your presentation in front of a live audience Our Playbook To Remediate False Agile Threat Modeling Overview About Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.


 Continue with Email
Continue with Email

 Home
Home


































