Threat Intelligence
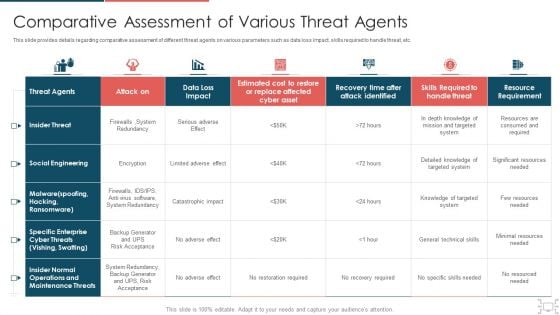
Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
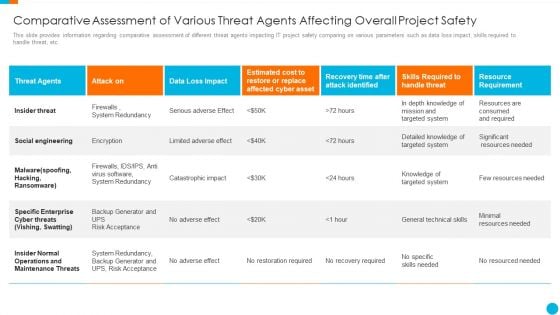
Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Clipart PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative comparative assessment of various threat agents affecting overall project safety clipart pdf bundle. Topics like threat agents, attack on, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
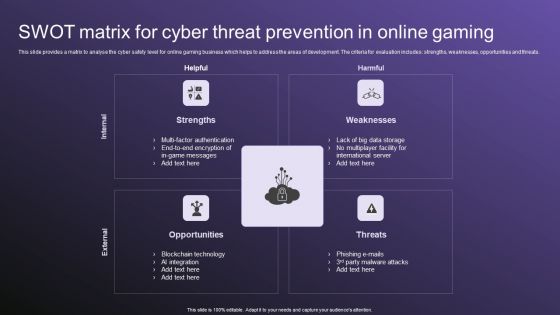
SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF
This slide provides a matrix to analyse the cyber safety level for online gaming business which helps to address the areas of development. The criteria for evaluation includes strengths, weaknesses, opportunities and threats. Persuade your audience using this SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
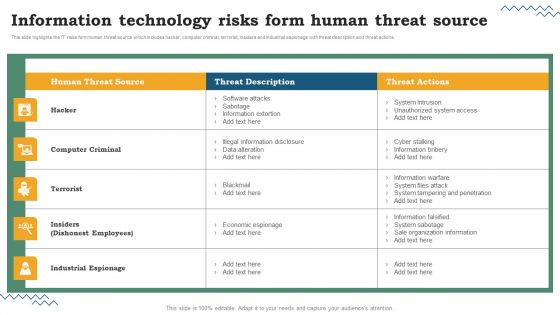
Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
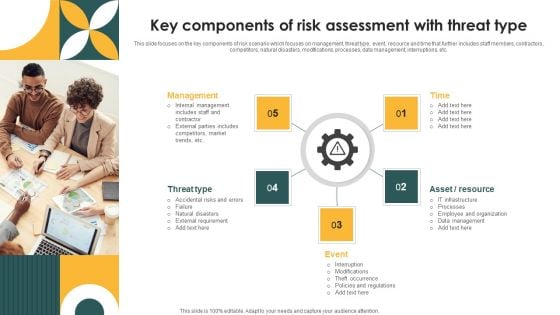
Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF
This slide focuses on the key components of risk scenario which focuses on management, threat type, event, resource and time that further includes staff members, contractors, competitors, natural disasters, modifications, processes, data management, interruptions, etc. Persuade your audience using this Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Management, Threat Type, Event, Time. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
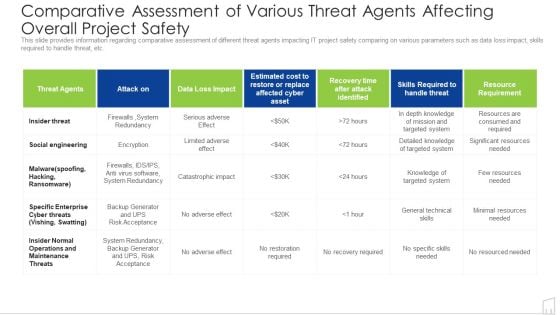
Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Ppt Ideas Outfit PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this comparative assessment of various threat agents affecting overall project safety ppt ideas outfit pdf. Use them to share invaluable insights on system, required, resources, social and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.
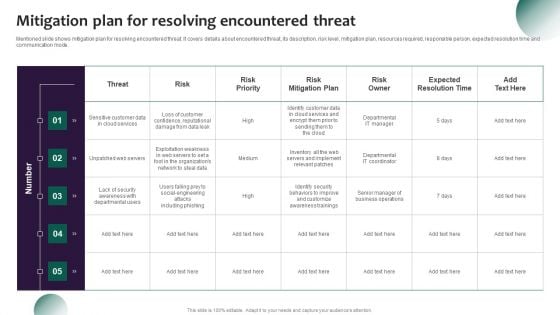
Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
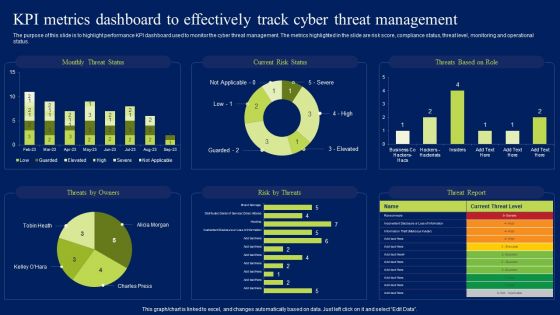
Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF.
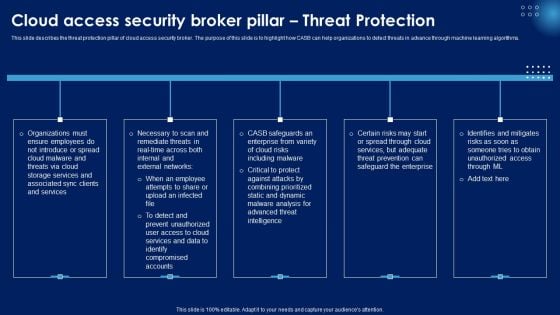
Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Online Data Protection Icon For Threat Management Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this online data protection icon for threat management ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online data protection icon for threat management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Database Server Safety From IT Threat Vector Icon Ppt PowerPoint Presentation Gallery Structure PDF
Persuade your audience using this database server safety from it threat vector icon ppt powerpoint presentation gallery structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including database server safety from it threat vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Threat With Hacker Icon On The Screen Ppt PowerPoint Presentation Infographic Template PDF
Persuade your audience using this cyber security threat with hacker icon on the screen ppt powerpoint presentation infographic template pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security threat with hacker icon on the screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Security Ransomware Hacking And Data Loss Threat Ppt PowerPoint Presentation File Formats PDF
Persuade your audience using this internet security ransomware hacking and data loss threat ppt powerpoint presentation file formats pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including internet security ransomware hacking and data loss threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Password Protection For Cyber Security Threat Ppt PowerPoint Presentation Icon Show PDF
Persuade your audience using this password protection for cyber security threat ppt powerpoint presentation icon show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including password protection for cyber security threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Potential Threat Assessment Model Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this business potential threat assessment model ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including identify, threat management plan, review plan design. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills
Network And Information Threat Safety Vector Icon Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Functional Process Icon With Threat Sign Ppt PowerPoint Presentation Icon Files PDF
Persuade your audience using this functional process icon with threat sign ppt powerpoint presentation icon files pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including functional process icon with threat sign. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Project Management Threat List Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Persuade your audience using this project management threat list vector icon ppt powerpoint presentation file microsoft pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including project management threat list vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
System Failure With Threat Symbol On Screen Icon Ppt PowerPoint Presentation Gallery Templates PDF
Persuade your audience using this system failure with threat symbol on screen icon ppt powerpoint presentation gallery templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including system failure with threat symbol on screen icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Circle Procedure Infographic To Manage Threat Detection And Response Ppt Styles Sample PDF
Persuade your audience using this circle procedure infographic to manage threat detection and response ppt styles sample pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure infographic to manage threat detection and response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
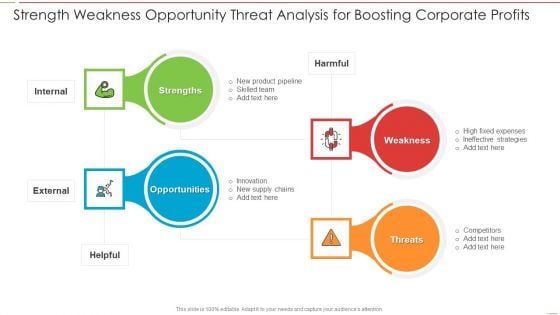
Strength Weakness Opportunity Threat Analysis For Boosting Corporate Profits Download PDF
Persuade your audience using this Strength Weakness Opportunity Threat Analysis For Boosting Corporate Profits Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strength, Weakness, Threats, Opportunity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Before Vs After Implementing Secure Web Gateway Web Threat Protection System
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Secure Web Gateway Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.

Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Welcome to our selection of the Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Find highly impressive Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Risk Assessment Matrix With Vulnerability And Threat Level Cybersecurity Risk Assessment Themes PDF for your upcoming presentation. All the presentation templates are 100 parcent editable and you can change the color and personalize the content accordingly. Download now.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
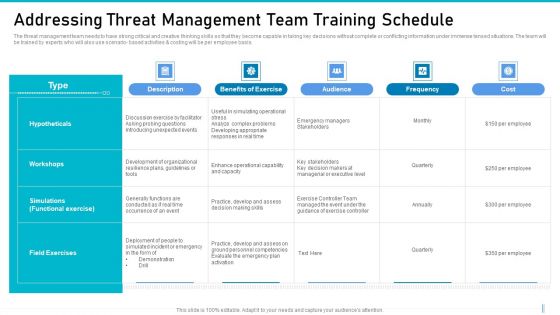
Risk Management For Organization Essential Assets Addressing Threat Management Team Portrait PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative risk management for organization essential assets addressing threat management team portrait pdf bundle. Topics like description, benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
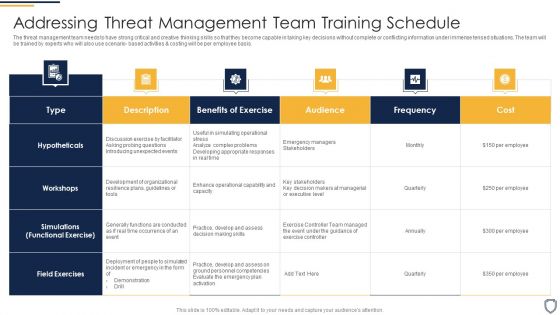
Corporate Security And Risk Management Addressing Threat Management Team Training Schedule Clipart PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing threat management team training schedule clipart pdf bundle. Topics like benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
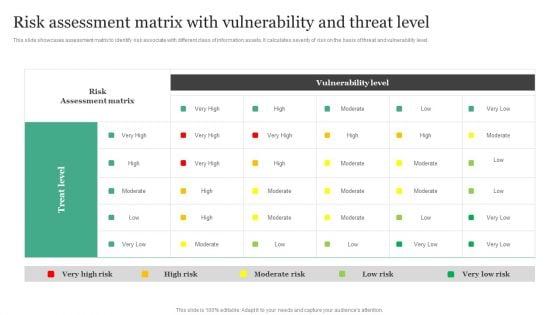
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
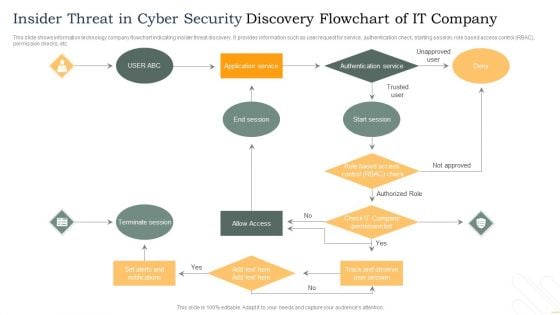
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
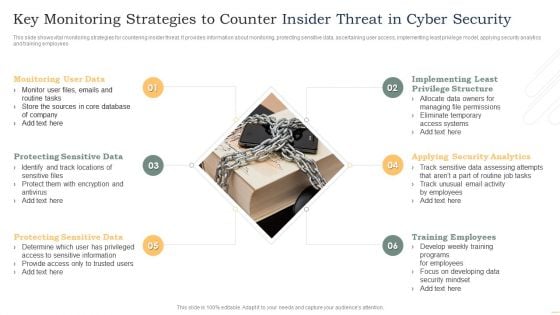
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
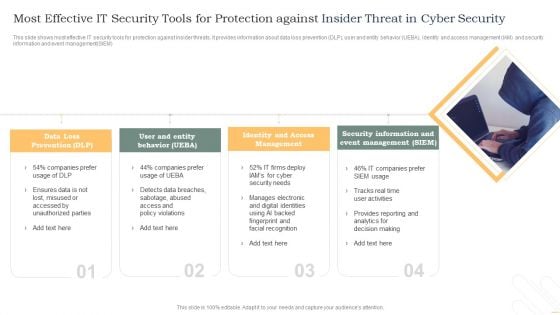
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
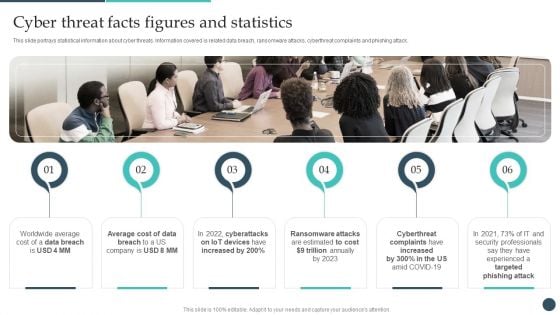
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF
Find highly impressive Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.
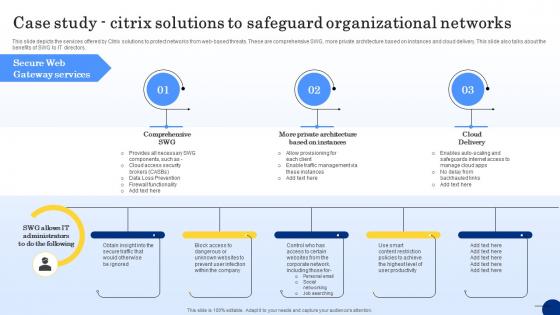
Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System
This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Citrix Solutions To Safeguard Organizational Networks Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors.
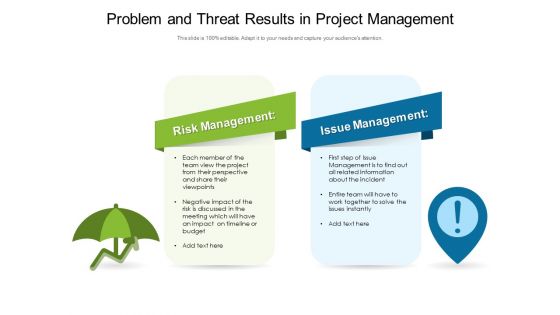
Problem And Threat Results In Project Management Ppt PowerPoint Presentation Styles Topics PDF
Persuade your audience using this problem and threat results in project management ppt powerpoint presentation styles topics pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including risk management, issue management, information, perspective, project, timeline, budget. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Internet Threat Risk Management Strategy Model Ppt PowerPoint Presentation Gallery Example Introduction PDF
Persuade your audience using this internet threat risk management strategy model ppt powerpoint presentation gallery example introduction pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, product, detect, respond. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
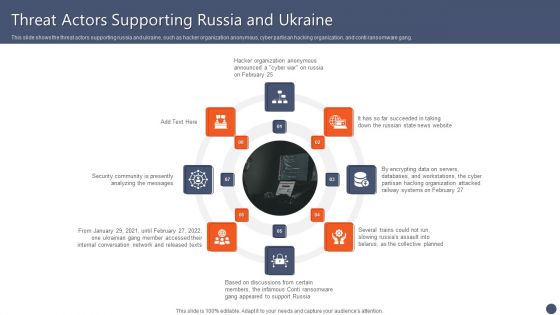
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
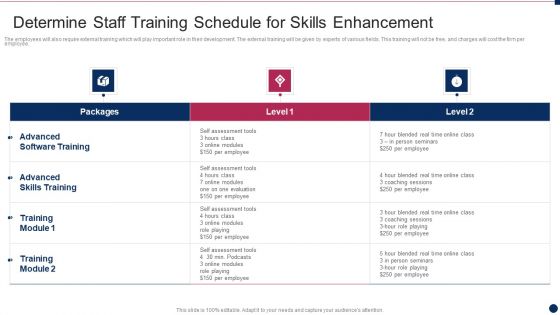
Threat Management At Workplace Determine Staff Training Schedule For Skills Enhancement Graphics Pdf
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver and pitch your topic in the best possible manner with this threat management at workplace determine staff training schedule for skills enhancement graphics pdf. Use them to share invaluable insights on advanced skills training, advanced software training, blended real time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Areas Professional PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. underlining competencies whose main purpose is to analyze behaviors, attributes, expertise and personal characteristics that supports the process of business analysis. This slide shows some competencies that are necessary to support business analysis and deliver the business solution effectively. This is a solution evaluation criteria assessment and threat impact matrix description of babok areas professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization knowledge, software applications, communication skills, behavioral characteristics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Step For Creating Event Threat Mitigation And Mitigation Plan Icons PDF
Persuade your audience using this Step For Creating Event Threat Mitigation And Mitigation Plan Icons PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics includingIdentify Event Risk, Perform Risk Assessment, Implement Mitigation Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills. This slide showcase steps in building event risk management plan to identify potential risk for optimize utilization of resources. It includes step like identify risk, perform risk mitigation, prioritize, track risk and implement mitigation strategies.
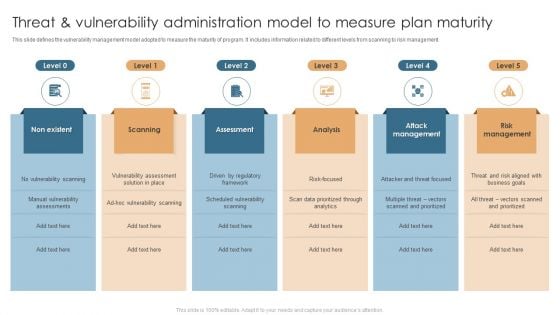
Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF
This slide defines the vulnerability management model adopted to measure the maturity of program. It includes information related to different levels from scanning to risk management. Persuade your audience using this Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Non Existent, Scanning, Assessment, Analysis, Attack Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
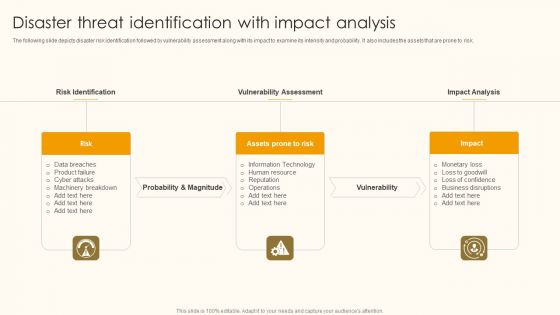
Disaster Threat Identification With Impact Analysis Ppt Styles Master Slide PDF
The following slide depicts disaster risk identification followed by vulnerability assessment along with its impact to examine its intensity and probability. It also includes the assets that are prone to risk. Persuade your audience using this Disaster Threat Identification With Impact Analysis Ppt Styles Master Slide PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Identification, Vulnerability Assessment, Impact Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
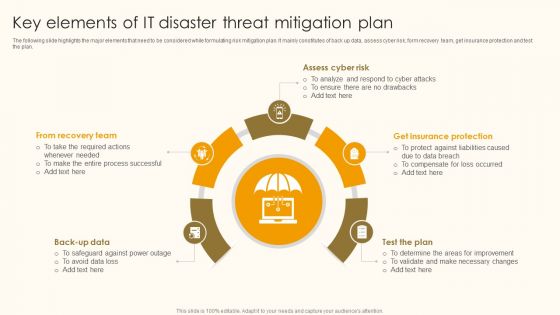
Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF
The following slide highlights the major elements that need to be considered while formulating risk mitigation plan. It mainly constitutes of back up data, assess cyber risk, form recovery team, get insurance protection and test the plan. Persuade your audience using this Key Elements Of IT Disaster Threat Mitigation Plan Ppt Show Files PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including From Recovery Team, Assess Cyber Risk, Get Insurance Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Continuity And Disaster Threat Reduction Methodology Ppt Portfolio Show PDF
The given below slide illustrates the steps for disaster risk reduction to reduce its impact on business. It begins with program initiation, stating requirements, strategy identification, plan documentation and ends with program management and testing. Persuade your audience using this Business Continuity And Disaster Threat Reduction Methodology Ppt Portfolio Show PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Program Initiation, State Requirements, Strategy Identification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Threat Status In Project Management Risk Plan Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured threat status in project management risk plan ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Fraud Threat Administration Guide Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourty five slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
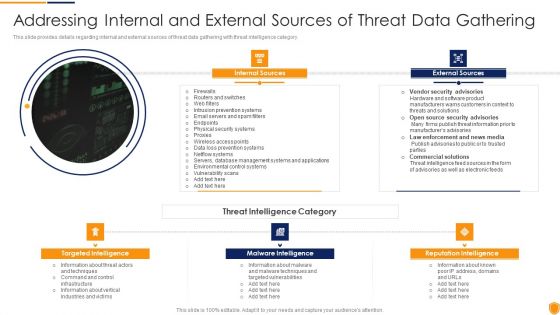
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Umbrella With Threat Symbol For Financial Risk Analysis Vector Icon Ppt PowerPoint Presentation Styles Background Image PDF
Persuade your audience using this umbrella with threat symbol for financial risk analysis vector icon ppt powerpoint presentation styles background image pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including umbrella with threat symbol for financial risk analysis vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
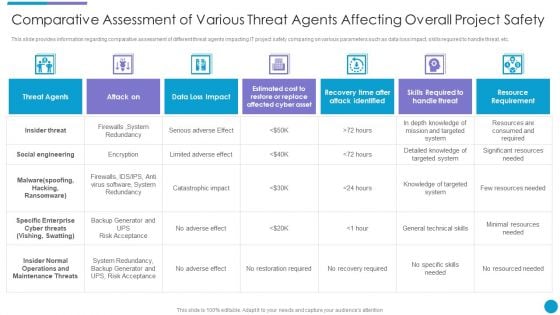
Major Techniques For Project Safety IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Portrait PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative major techniques for project safety it comparative assessment of various threat agents affecting overall project safety portrait pdf bundle. Topics like threat agents, attack on, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
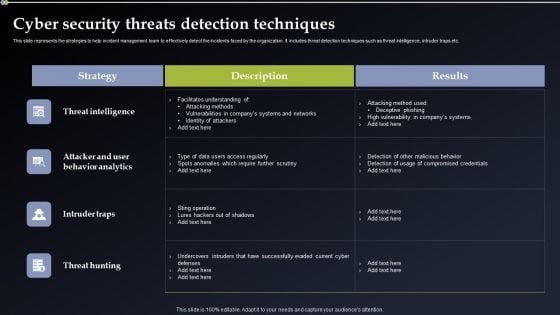
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.


 Continue with Email
Continue with Email

 Home
Home


































