Threat Intelligence

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
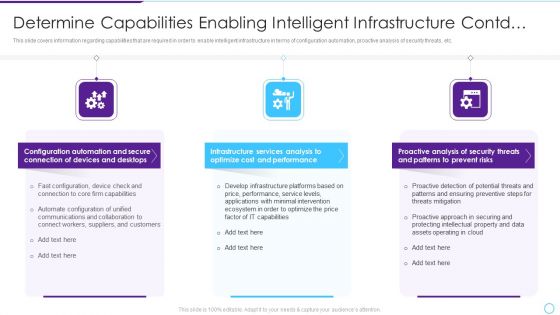
Intelligent Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Elements PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. This is a Intelligent Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Elements PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Configuration Automation, Devices And Desktops, Infrastructure Services Analysis, Proactive Analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why Switching To Next Generation Intelligent Intrusion Prevention System Ppt Presentation
This slide gives an overview of the reasons for organizations to switch to Next Generation firewall solutions. It highlights the features of the Next Generation firewall systems, such as packet inspection, threat intelligence, behavioral analytics, etc.Make sure to capture your audiences attention in your business displays with our gratis customizable Why Switching To Next Generation Intelligent Intrusion Prevention System Ppt Presentation. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide gives an overview of the reasons for organizations to switch to Next Generation firewall solutions. It highlights the features of the Next Generation firewall systems, such as packet inspection, threat intelligence, behavioral analytics, etc.
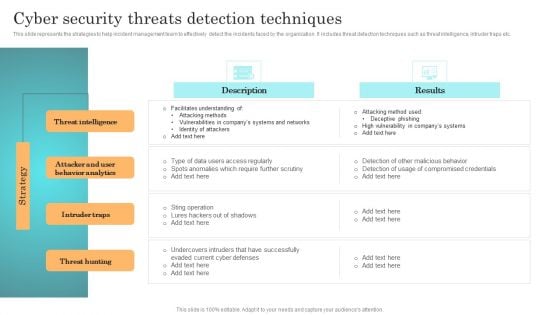
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.
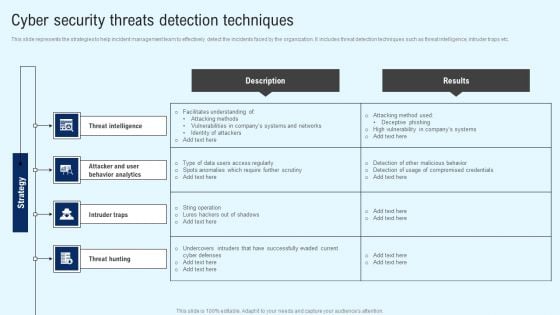
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.
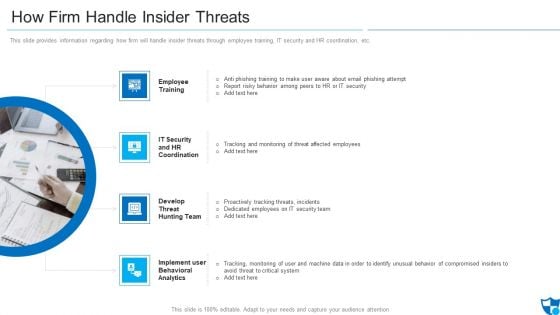
How Firm Handle Insider Threats Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc.Presenting how firm handle insider threats formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee training, it security and hr coordination, develop threat hunting team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
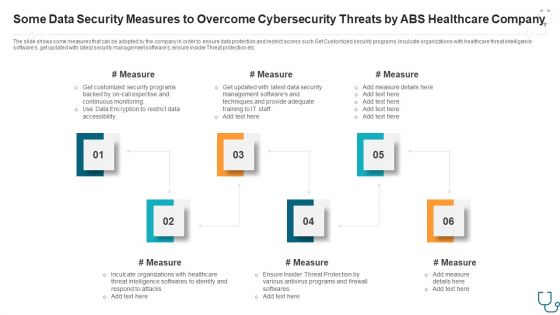
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
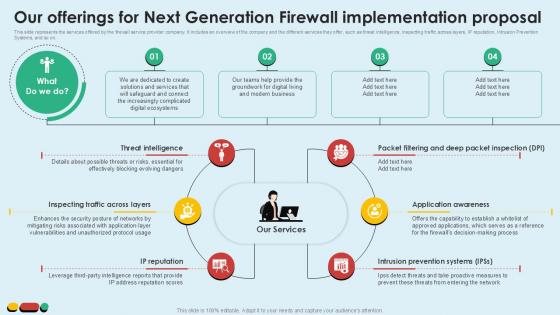
Our Offerings For Next Generation Intelligent Intrusion Prevention System Ppt Slide
This slide represents the services offered by the firewall service provider company. It includes an overview of the company and the different services they offer, such as threat intelligence, inspecting traffic across layers, IP reputation, Intrusion Prevention Systems, and so on.Present like a pro with Our Offerings For Next Generation Intelligent Intrusion Prevention System Ppt Slide. Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the services offered by the firewall service provider company. It includes an overview of the company and the different services they offer, such as threat intelligence, inspecting traffic across layers, IP reputation, Intrusion Prevention Systems, and so on.
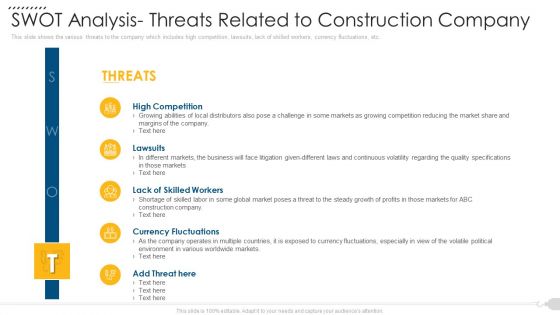
Swot Analysis Threats Related To Construction Company Professional PDF
This slide shows the various threats to the company which includes high competition, lawsuits, lack of skilled workers, currency fluctuations, etc. Presenting swot analysis threats related to construction company professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like competition, threats, skilled, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Swot Analysis Threats Related To Construction Company Infographics PDF
This slide shows the various threats to the company which includes high competition, lawsuits, lack of skilled workers, currency fluctuations, etc. Presenting swot analysis threats related to construction company infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high competition, lawsuits, skilled workers, currency fluctuations, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SWOT Analysis Of ABC Software Company Threats Pictures PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc.This is a swot analysis of abc software company threats pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability laws, shortage of skilled workforce, intense competition. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Swot Analysis Of Abc Software Company Threats Summary PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. This is a swot analysis of abc software company threats summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability, lawsuits, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SWOT Analysis Threats Related To Construction Company Introduction PDF
This slide shows the various threats to the company which includes high competition, lawsuits, lack of skilled workers, currency fluctuations, etc.This is a swot analysis threats related to construction company introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high competition, lack of skilled workers, currency fluctuations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Quality Auditing And Threats Reporting Process Ppt Icon Picture PDF
This slide covers auditing process of data quality and reporting risk detected. It includes framework depicting checkpoints needed to audit data quality for data warehouse and business intelligence projects. Presenting Data Quality Auditing And Threats Reporting Process Ppt Icon Picture PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including External Data, Customer Data, Legacy Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.
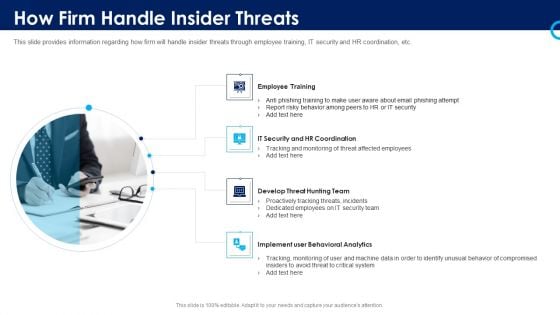
Organizational Security Solutions How Firm Handle Insider Threats Introduction PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a organizational security solutions how firm handle insider threats introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
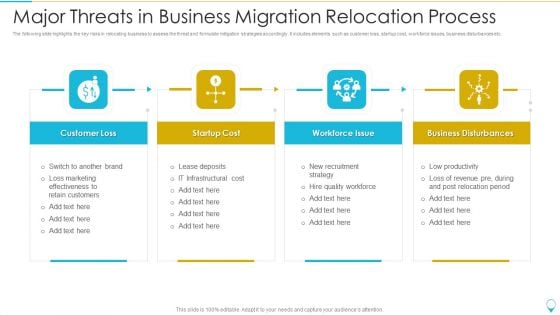
Major Threats In Business Migration Relocation Process Background PDF
The following slide highlights the key risks in relocating business to assess the threat and formulate mitigation strategies accordingly. It includes elements such as customer loss, startup cost, workforce issues, business disturbances etc. Presenting major threats in business migration relocation process background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including startup cost, workforce issue, business disturbances. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
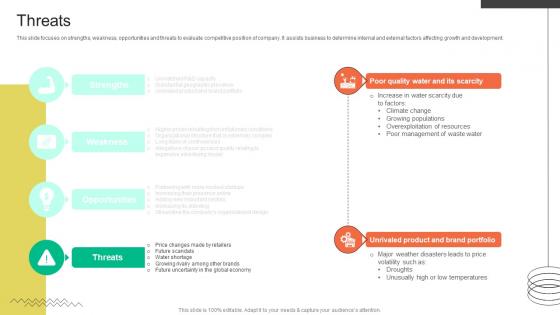
Threats FMCG Provider Company Profile CP SS V
This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Boost your pitch with our creative Threats FMCG Provider Company Profile CP SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.
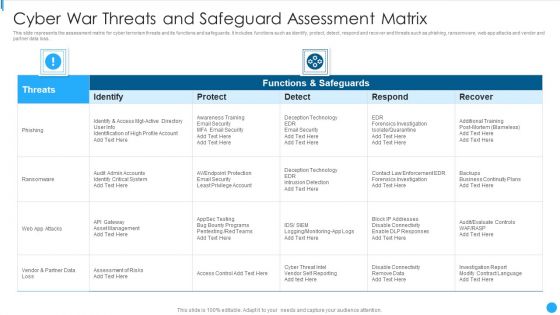
Cyber War Threats And Safeguard Assessment Matrix Summary PDF
This slide represents the assessment matrix for cyber terrorism threats and its functions and safeguards. It includes functions such as identify, protect, detect, respond and recover and threats such as phishing, ransomware, web app attacks and vendor and partner data loss.Showcasing this set of slides titled Cyber War Threats And Safeguard Assessment Matrix Summary PDF The topics addressed in these templates are Functions And Safeguards, Awareness Training, Forensics Investigation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
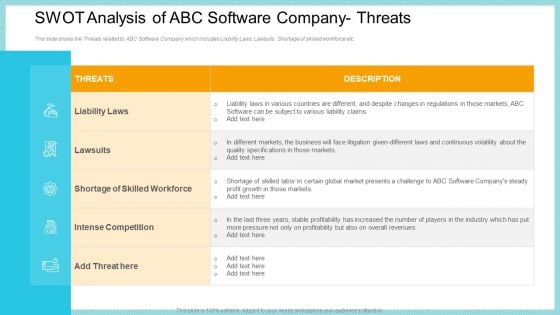
SWOT Analysis Of ABC Software Company Threats Structure PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like revenues, profitability, quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
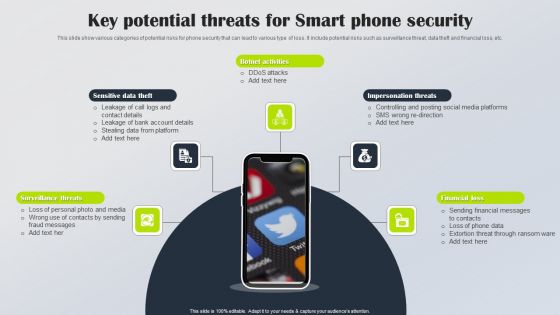
Key Potential Threats For Smart Phone Security Summary PDF
This slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Persuade your audience using this Key Potential Threats For Smart Phone Security Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Activities, Impersonation Threats, Financial Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
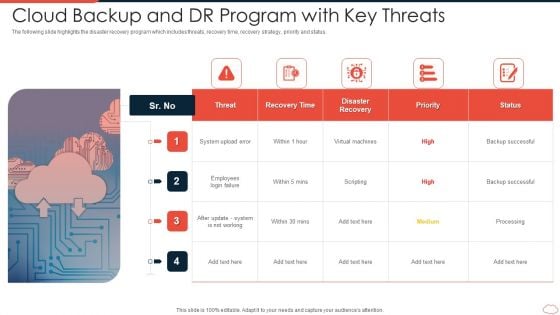
Cloud Backup And DR Program With Key Threats Topics PDF
The following slide highlights the disaster recovery program which includes threats, recovery time, recovery strategy, priority and status. Persuade your audience using this cloud backup and dr program with key threats topics pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including cloud backup and dr program with key threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
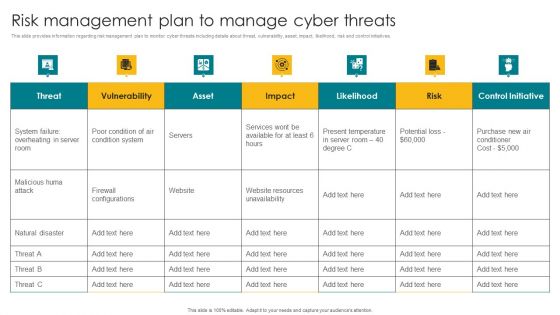
Risk Management Plan To Manage Cyber Threats Graphics PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Management Plan To Manage Cyber Threats Graphics PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Management Plan To Manage Cyber Threats Graphics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF
Persuade your audience using this Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threats And Vulnerability, Administration Plan, Requirement Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
SWOT Analysis Of ABC Software Company Threats Icons PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like liability laws, intense competition, shortage of skilled workforce. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
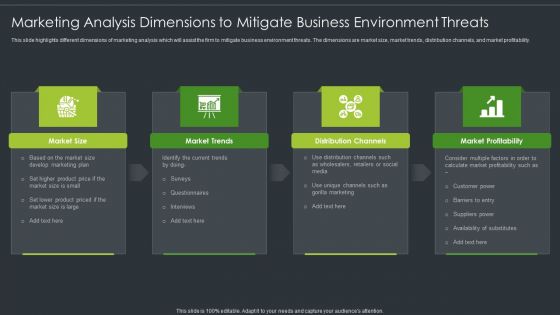
Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF
This slide highlights different dimensions of marketing analysis which will assist the firm to mitigate business environment threats. The dimensions are market size, market trends, distribution channels, and market profitability. Persuade your audience using this Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Market Size, Market Trends, Distribution Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
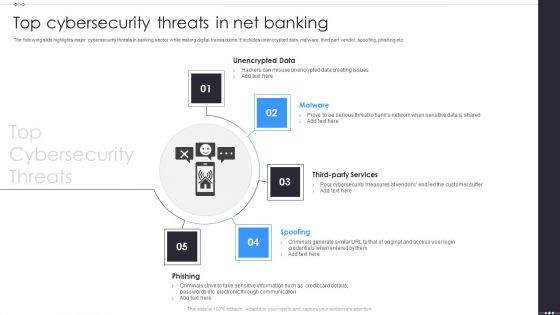
Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
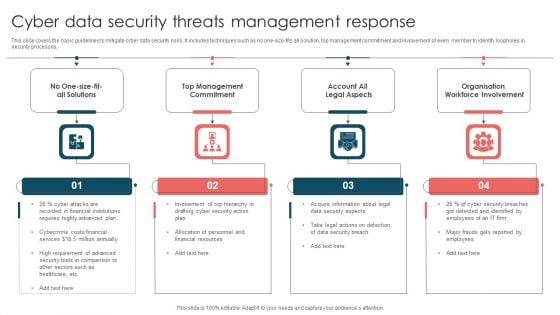
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
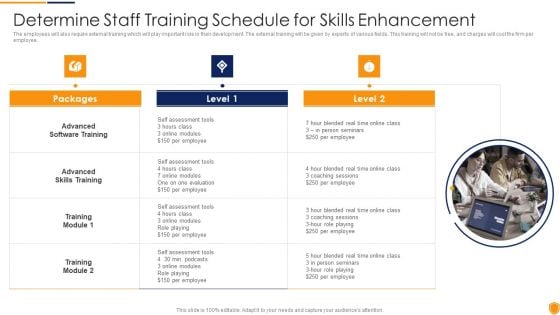
Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
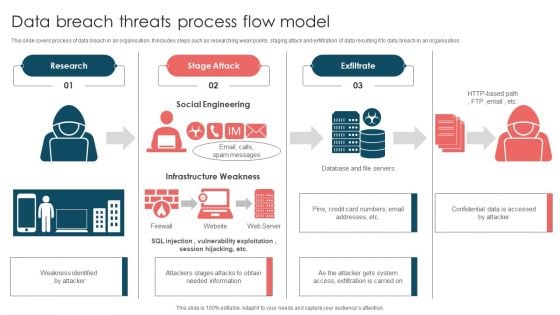
Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
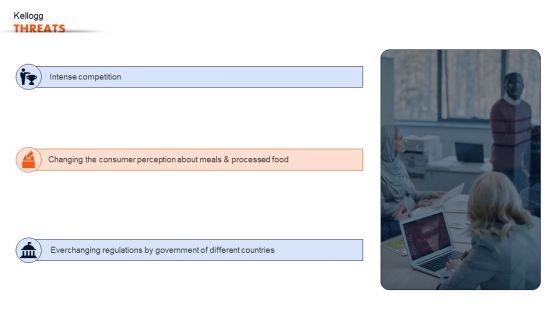
Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
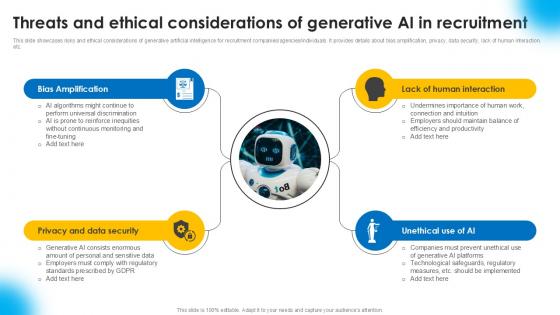
Threats And Ethical Considerations AI Powered Recruitment Enhancing Ppt PowerPoint AI SS V
This slide showcases risks and ethical considerations of generative artificial intelligence for recruitment companiesoragenciesorindividuals. It provides details about bias amplification, privacy, data security, lack of human interaction, etc.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats And Ethical Considerations AI Powered Recruitment Enhancing Ppt PowerPoint AI SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases risks and ethical considerations of generative artificial intelligence for recruitment companiesoragenciesorindividuals. It provides details about bias amplification, privacy, data security, lack of human interaction, etc.

Role Of Automation In Improving ESO System Ppt PowerPoint Presentation File Graphics Tutorials PDF
This slide covers role of automation in improving enterprise security operation. It involves AI powered threat detection, integrated threat intelligence and alert validation and noise reduction. Presenting Role Of Automation In Improving ESO System Ppt PowerPoint Presentation File Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including AI Powered, Threat Detection, Integrated Threat Intelligence, Alert Validation, Noise Reduction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
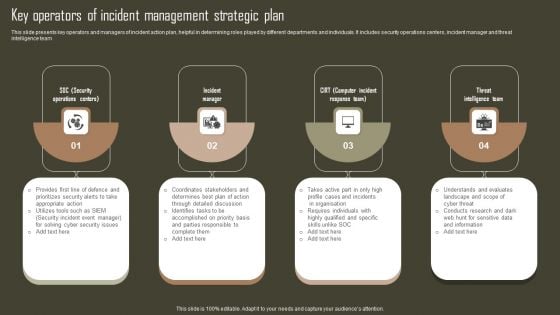
Key Operators Of Incident Management Strategic Plan Professional PDF
This slide presents key operators and managers of incident action plan, helpful in determining roles played by different departments and individuals. It includes security operations centers, incident manager and threat intelligence team. Presenting Key Operators Of Incident Management Strategic Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Manager, Threat Intelligence Team, Sensitive Data And Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Surge In Construction Faults Lawsuits Case Competition SWOT Analysis Threats Related To Construction Ideas PDF
This slide shows the various threats to the company which includes high competition, lawsuits, lack of skilled workers, currency fluctuations, etc. This is a surge in construction faults lawsuits case competition swot analysis threats related to construction ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high competition, lawsuits, lack of skilled workers, currency fluctuations, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Hacker Stealing Business Confidential Data Base Through Internet Threats Ppt PowerPoint Presentation File Pictures PDF
Persuade your audience using this hacker stealing business confidential data base through internet threats ppt powerpoint presentation file pictures pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hacker stealing business confidential data base through internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Threats For Credit Card Phishing Ppt PowerPoint Presentation File Layouts PDF
Persuade your audience using this internet threats for credit card phishing ppt powerpoint presentation file layouts pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including internet threats for credit card phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Online Network Security Against Hackers And Internet Threats Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this online network security against hackers and internet threats ppt powerpoint presentation file show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online network security against hackers and internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Software Deployed To Countermeasure Internet Threats Ppt PowerPoint Presentation Gallery Icon PDF
Persuade your audience using this security software deployed to countermeasure internet threats ppt powerpoint presentation gallery icon pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security software deployed to countermeasure internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Vector Illustrating Hacker Launching Internet Threats Through Malware Ppt PowerPoint Presentation Icon Backgrounds PDF
Persuade your audience using this vector illustrating hacker launching internet threats through malware ppt powerpoint presentation icon backgrounds pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustrating hacker launching internet threats through malware. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
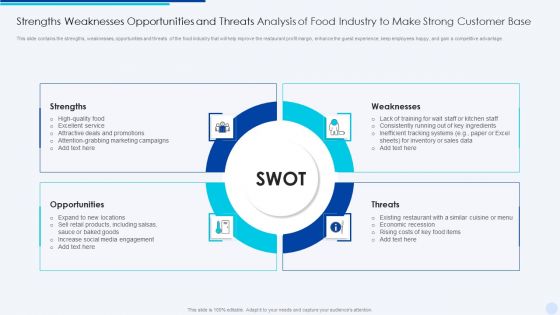
Strengths Weaknesses Opportunities And Threats Analysis Of Food Industry To Make Strong Customer Base Introduction PDF
This slide contains the strengths, weaknesses, opportunities and threats of the food industry that will help improve the restaurant profit margin, enhance the guest experience, keep employees happy, and gain a competitive advantage.Persuade your audience using this Strengths Weaknesses Opportunities And Threats Analysis Of Food Industry To Make Strong Customer Base Introduction PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SWOT Analysis Threats Related To Construction Company Ppt Gallery Example PDF
This slide shows the various threats to the company which includes high competition, lawsuits, lack of skilled workers, currency fluctuations, etc. This is a SWOT analysis strengths related to construction company ppt model show pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market share, quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Of Next Generation Intelligent Intrusion Prevention System Ppt Slide
This slide highlights the advantages of Next Generation Firewalls for network protection. The purpose of this slide is to showcase the different benefits of next generation firewall, such as robust threat prevention, flexible deployment, app, And identity based checking and control, etc.Boost your pitch with our creative Benefits Of Next Generation Intelligent Intrusion Prevention System Ppt Slide. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the advantages of Next Generation Firewalls for network protection. The purpose of this slide is to showcase the different benefits of next generation firewall, such as robust threat prevention, flexible deployment, app, and identity based checking and control, etc.

Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.
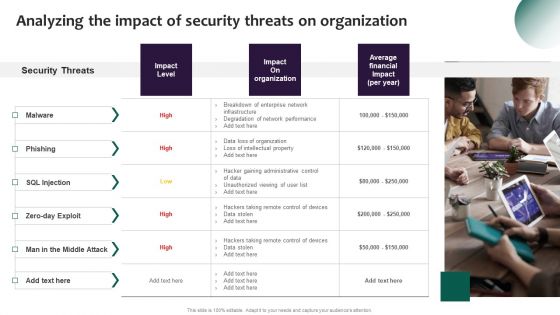
Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
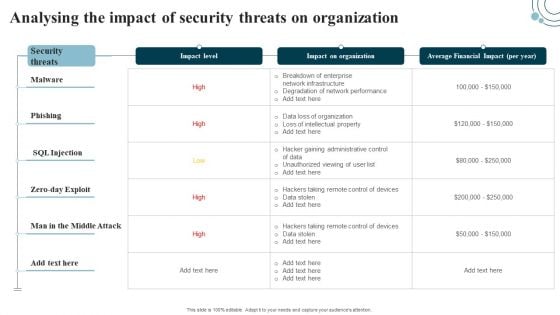
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Mitigating Cybersecurity Threats And Vulnerabilities Comparative Assessment Of Various Background PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities comparative assessment of various background pdf bundle. Topics like social engineering, insider threat, maintenance threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
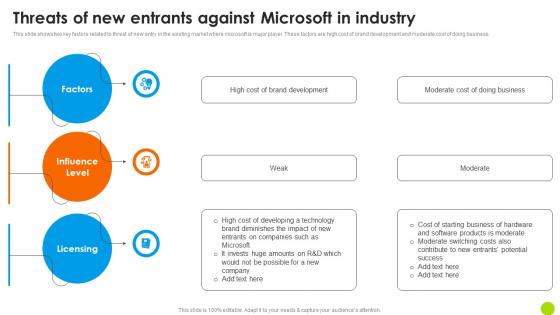
Threats Of New Entrants Against Microsoft In Industry Microsoft Long Term Business Formats PDF
This slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business. Find highly impressive Threats Of New Entrants Against Microsoft In Industry Microsoft Long Term Business Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Threats Of New Entrants Against Microsoft In Industry Microsoft Long Term Business Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business.
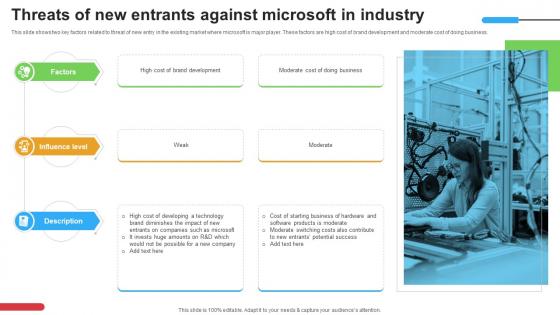
Micosoft Intensive Growth Threats Of New Entrants Against Microsoft In Industry Strategy SS V
This slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Micosoft Intensive Growth Threats Of New Entrants Against Microsoft In Industry Strategy SS V can be your best option for delivering a presentation. Represent everything in detail using Micosoft Intensive Growth Threats Of New Entrants Against Microsoft In Industry Strategy SS V make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Business Analytics Framework How Firm Handle Various Insider Threats At Workplace Infographics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Developing Business Analytics Framework How Firm Handle Various Insider Threats At Workplace Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Behavioral Analytics, Threat Hunting You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
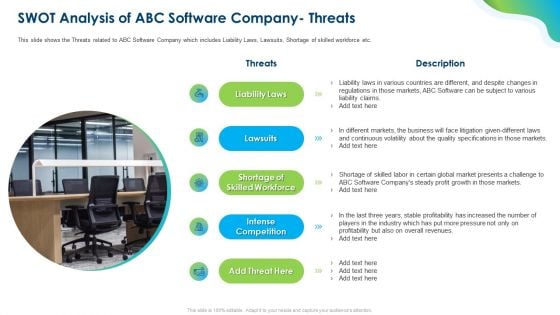
Growing Churn Rate In IT Organization Swot Analysis Of Abc Software Company Threats Mockup PDF
This is a Growing Churn Rate In IT Organization Swot Analysis Of Abc Software Company Threats Mockup PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability laws, lawsuits, shortage of skilled workforce, intense competition, add threat here. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations How Firm Handle Insider Threats Pictures PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a information and technology security operations how firm handle insider threats pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
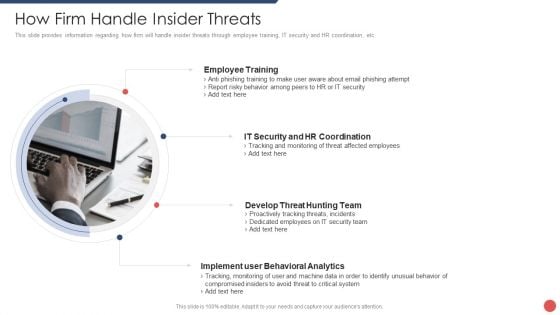
Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration How Firm Handle Insider Threats Structure PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a enhanced protection corporate event administration how firm handle insider threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration How Firm Handle Insider Threats Template PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security and process integration how firm handle insider threats template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































