Threat

Threat Of Email Virus In Computer System Shape Ppt PowerPoint Presentation Inspiration Files PDF
Presenting threat of email virus in computer system shape ppt powerpoint presentation inspiration files pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including threat of email virus in computer system shape. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Crisis Management Icon With Threat Sign Ppt PowerPoint Presentation Inspiration Background PDF
Presenting crisis management icon with threat sign ppt powerpoint presentation inspiration background pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including crisis management icon with threat sign. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Virus Threat Vector Icon Ppt PowerPoint Presentation Professional Graphics Pictures PDF
Presenting computer virus threat vector icon ppt powerpoint presentation professional graphics pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer virus threat vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Vector Showing IT Security Under Threat Ppt PowerPoint Presentation Gallery Deck PDF
Showcasing this set of slides titled vector showing it security under threat ppt powerpoint presentation gallery deck pdf. The topics addressed in these templates are vector showing it security under threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Online Security Threat And Computer Virus Vector Icon Ppt PowerPoint Presentation Styles Vector PDF
Presenting online security threat and computer virus vector icon ppt powerpoint presentation styles vector pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including online security threat and computer virus vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Software File Protection From Online Threat Vector Icon Ppt PowerPoint Presentation Show Visuals PDF
Showcasing this set of slides titled software file protection from online threat vector icon ppt powerpoint presentation show visuals pdf. The topics addressed in these templates are software file protection from online threat vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Clipboard With Threat Management Checklist Vector Icon Ppt PowerPoint Presentation Icon Outfit PDF
Presenting clipboard with threat management checklist vector icon ppt powerpoint presentation icon outfit pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including clipboard with threat management checklist vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Threat On Pc Monitor Vector Icon Ppt PowerPoint Presentation Layouts Information PDF
Presenting internet threat on pc monitor vector icon ppt powerpoint presentation layouts information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet threat on pc monitor vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Customer Getting Threat For The System Failure Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting customer getting threat for the system failure ppt powerpoint presentation gallery layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including customer getting threat for the system failure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Global Warming Threat Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Presenting global warming threat vector icon ppt powerpoint presentation file microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including global warming threat vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Plan With Key Trends Ppt PowerPoint Presentation Summary Mockup PDF
Showcasing this set of slides titled internet security threat analysis plan with key trends ppt powerpoint presentation summary mockup pdf. The topics addressed in these templates are internet security threat analysis plan with key trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
7 Petal Visual For Insider Threat Management Ppt PowerPoint Presentation File Brochure PDF
Presenting 7 petal visual for insider threat management ppt powerpoint presentation file brochure pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including 7 petal visual for insider threat management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
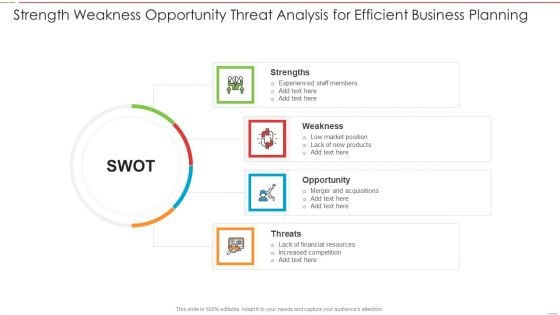
Strength Weakness Opportunity Threat Analysis For Efficient Business Planning Elements PDF
Presenting Strength Weakness Opportunity Threat Analysis For Efficient Business Planning Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strength, Weakness, Threats, Opportunity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strength Weakness Opportunity Threat Analysis Of Social Media Strategy Portrait PDF
Presenting Strength Weakness Opportunity Threat Analysis Of Social Media Strategy Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strength, Weakness, Threats, Opportunity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Disaster Threat Mitigation Strategy Icon Ppt Portfolio Design Templates PDF
Presenting Business Disaster Threat Mitigation Strategy Icon Ppt Portfolio Design Templates PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Business Disaster, Threat Mitigation, Strategy Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
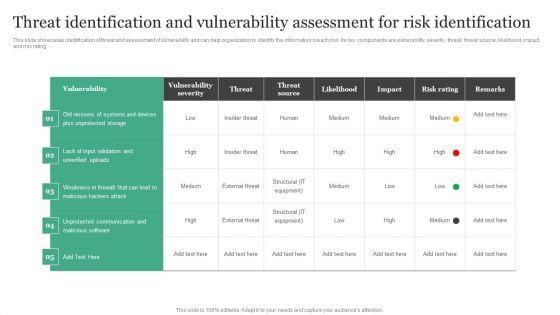
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

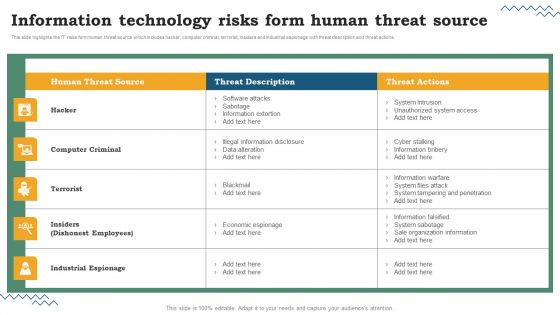
IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Whistleblowers Threats Presentation Backgrounds
This is a whistleblowers threats presentation backgrounds. This is a four stage process. The stages in this process are external content threats, active content threats, whistleblowers threats, unauthorized access threats.
Risk Management Dashboard Of IT Department With Threat Frequency Icons PDF
This slide shows dashboard of risk management of IT department representing net critical risks, threat and vulnerability frequency in last 60 days, open audit findings, open and vendor risks etc. Showcasing this set of slides titled Risk Management Dashboard Of IT Department With Threat Frequency Icons PDF. The topics addressed in these templates are Net Critical Risk, Organization, Threat Frequency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
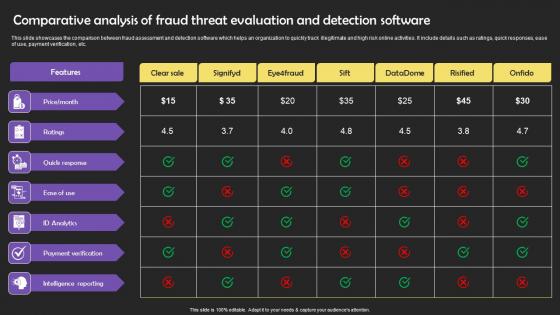
Comparative Analysis Of Fraud Threat Evaluation And Detection Software Ideas Pdf
This slide showcases the comparison between fraud assessment and detection software which helps an organization to quickly track illegitimate and high risk online activities. It include details such as ratings, quick responses, ease of use, payment verification, etc. Showcasing this set of slides titled Comparative Analysis Of Fraud Threat Evaluation And Detection Software Ideas Pdf The topics addressed in these templates are Ratings, Quick Response, Payment Verification, Analytics All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the comparison between fraud assessment and detection software which helps an organization to quickly track illegitimate and high risk online activities. It include details such as ratings, quick responses, ease of use, payment verification, etc.
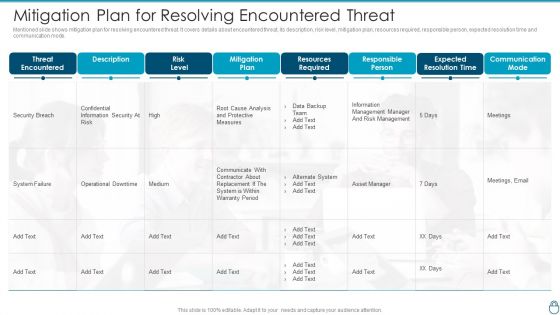
Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
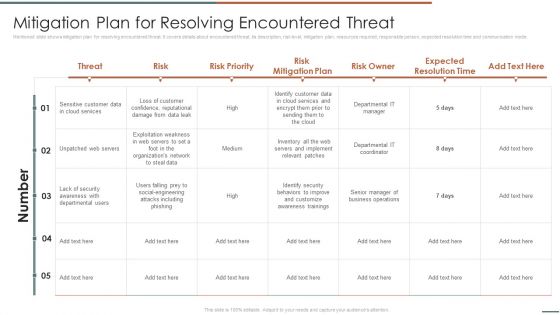
Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF. Use them to share invaluable insights on Unpatched Servers, Attacks Including, Awareness Trainings and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
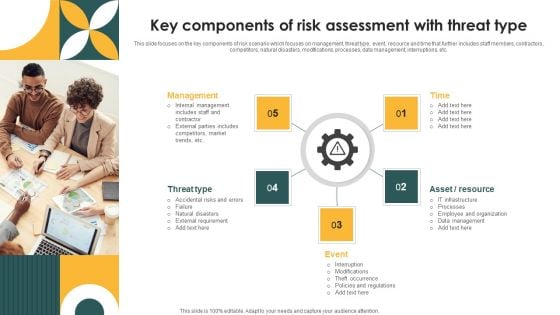
Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF
This slide focuses on the key components of risk scenario which focuses on management, threat type, event, resource and time that further includes staff members, contractors, competitors, natural disasters, modifications, processes, data management, interruptions, etc. Persuade your audience using this Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Management, Threat Type, Event, Time. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
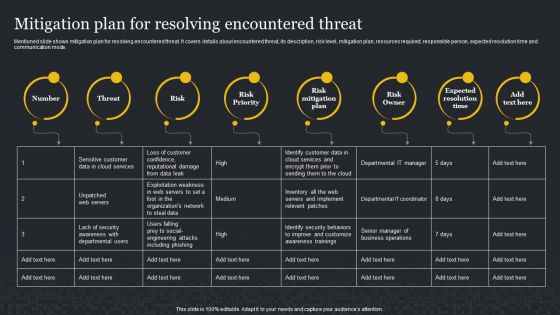
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Risk Management For Organization Essential Assets Selecting Secured Threat Management Software Background PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets selecting secured threat management software background pdf bundle. Topics like cost, information security prevention, api integration, access rights, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
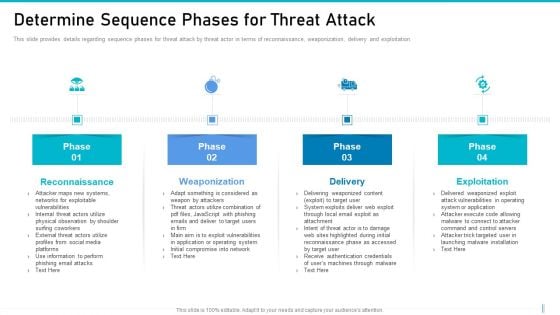
Risk Management For Organization Essential Assets Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a risk management for organization essential assets determine sequence phases for threat attack rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
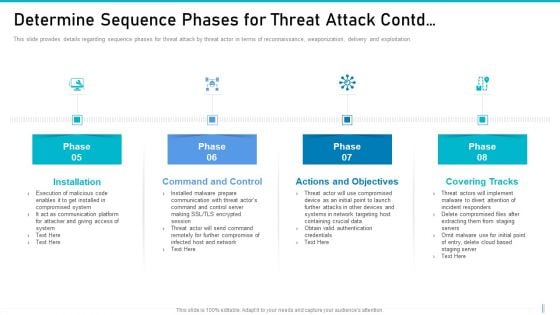
Risk Management For Organization Essential Assets Determine Sequence Phases For Threat Professional PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting risk management for organization essential assets determine sequence phases for threat professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
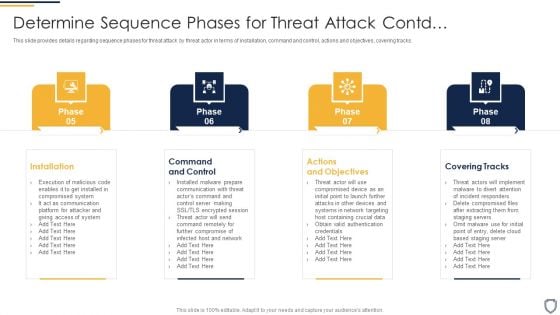
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
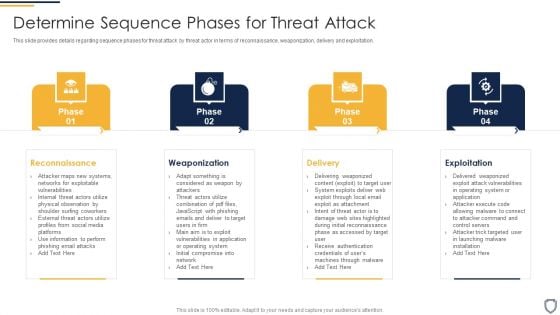
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Threat Management Team Structure Topics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a corporate security and risk management determine threat management team structure topics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
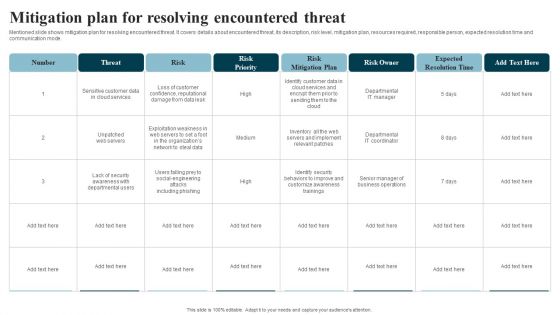
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
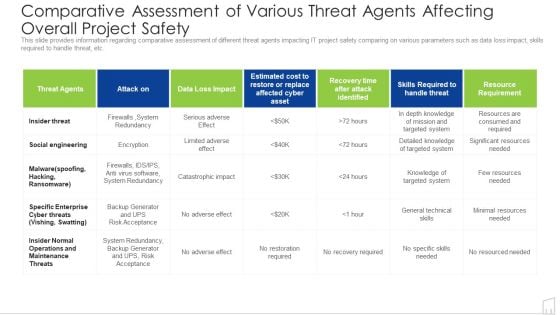
Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Ppt Ideas Outfit PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this comparative assessment of various threat agents affecting overall project safety ppt ideas outfit pdf. Use them to share invaluable insights on system, required, resources, social and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
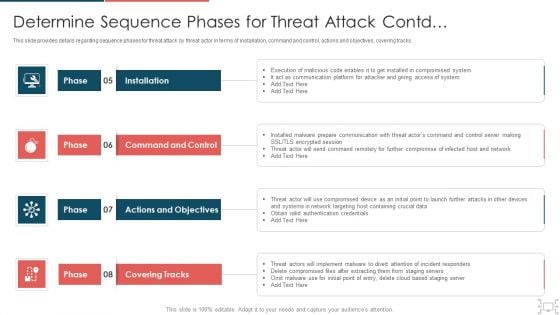
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Determine Several Threat Actors Profile Sample PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization determine several threat actors profile sample pdf. Use them to share invaluable insights on determine several threat actors profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
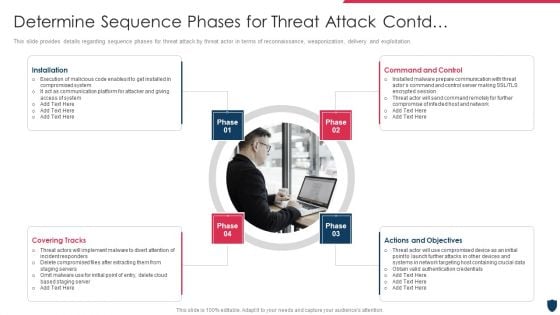
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
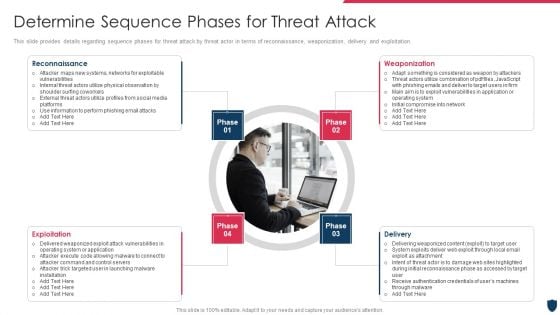
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
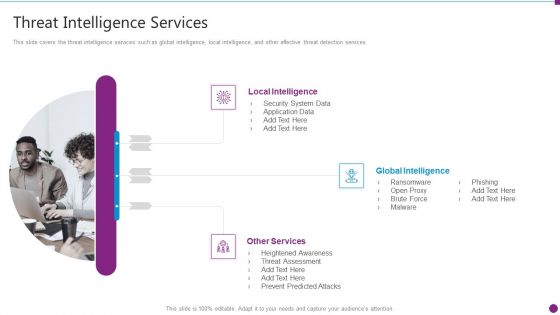
Security Information And Event Management Strategies For Financial Audit And Compliance Threat Intelligence Services Graphics PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting security information and event management strategies for financial audit and compliance threat intelligence services graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like local intelligence, global intelligence, other services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
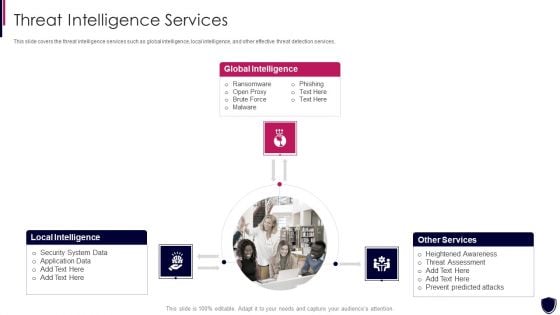
Enhancing Cyber Safety With Vulnerability Administration Threat Intelligence Services Information PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a enhancing cyber safety with vulnerability administration threat intelligence services information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
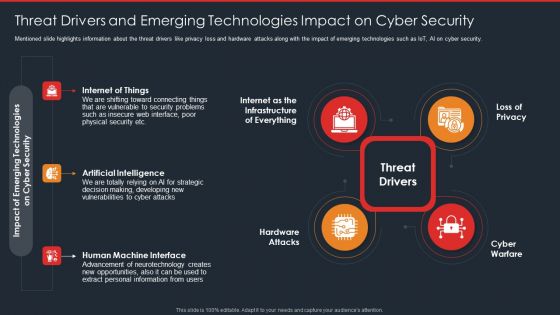
Data Safety Initiatives Threat Drivers And Emerging Technologies Impact On Cyber Security Brochure PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a data safety initiatives threat drivers and emerging technologies impact on cyber security brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat drivers, loss privacy, cyber warfare, hardware attacks, artificial intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
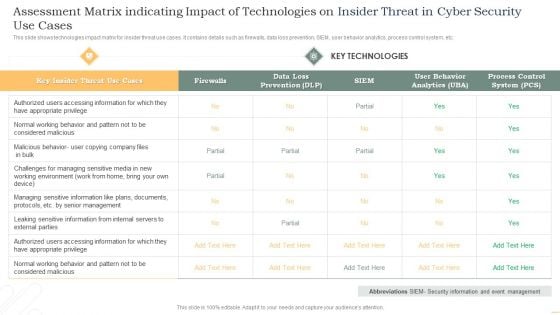
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
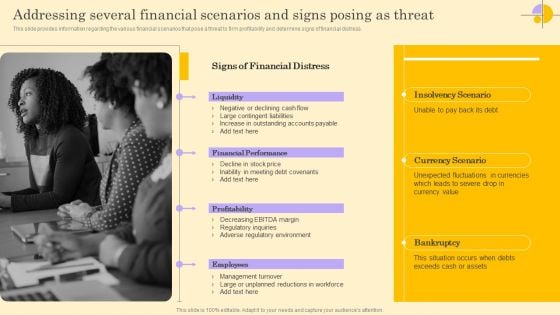
Addressing Several Financial Scenarios And Signs Posing As Threat Rules PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Create an editable Addressing Several Financial Scenarios And Signs Posing As Threat Rules PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing Several Financial Scenarios And Signs Posing As Threat Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
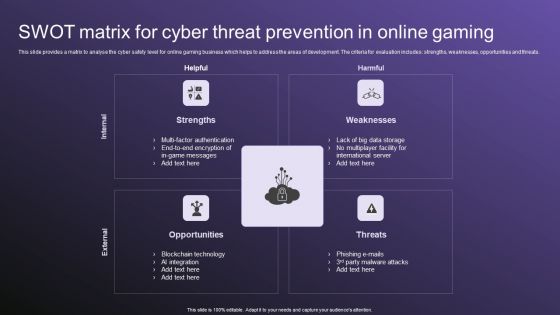
SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF
This slide provides a matrix to analyse the cyber safety level for online gaming business which helps to address the areas of development. The criteria for evaluation includes strengths, weaknesses, opportunities and threats. Persuade your audience using this SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
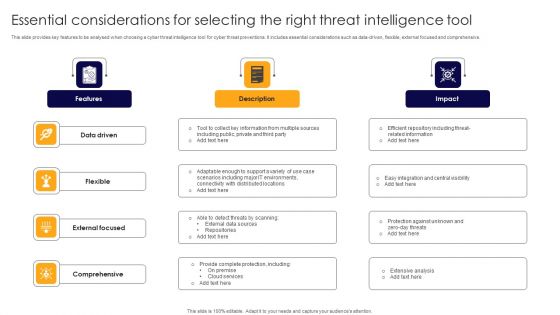
Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF
This slide provides key features to be analysed when choosing a cyber threat intelligence tool for cyber threat preventions. It includes essential considerations such as data-driven, flexible, external focused and comprehensive. Presenting Essential Considerations For Selecting The Right Threat Intelligence Tool Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Driven, Flexible, External Focused. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Risk Management Word Cloud With Threat Probability And Goals Ppt Powerpoint Presentation Show Designs Download
This is a risk management word cloud with threat probability and goals ppt powerpoint presentation show designs download. This is a four stage process. The stages in this process are success, business, motivation, management, always, objectives, item, organizational, money, taking.
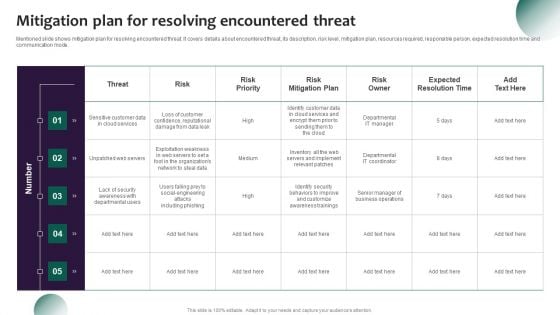
Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
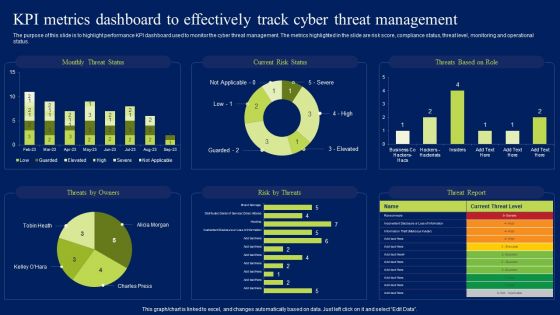
Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF.

Threat Of Substitute Product Or Service Slow Industry Growth PPT Slides
This is a rivalry among existing competitors numerous competitors ppt slides. This is a four stage process. The stages in this process are threat of substitute product or service, rivalry among existing competitors, numerous competitors, slow industry growth.
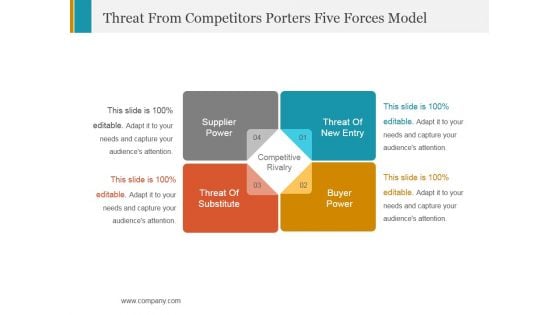
Threat From Competitors Porters Five Forces Model Ppt PowerPoint Presentation Template
This is a threat from competitors porters five forces model ppt powerpoint presentation template. This is a four stage process. The stages in this process are supplier power, competitive rivalry, buyer power.
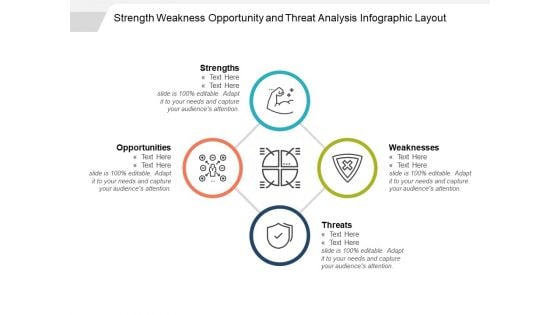
Strength Weakness Opportunity And Threat Analysis Infographic Layout Ppt PowerPoint Presentation Layouts
This is a strength weakness opportunity and threat analysis infographic layout ppt powerpoint presentation layouts. This is a four stage process. The stages in this process are due diligence, value gap analysis, value maximization process.

Responsible Technology Playbook Checklist To Manage Agile Threat Modelling Microsoft PDF
This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. This Responsible Technology Playbook Checklist To Manage Agile Threat Modelling Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Responsible Technology Playbook Checklist To Manage Agile Threat Modelling Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
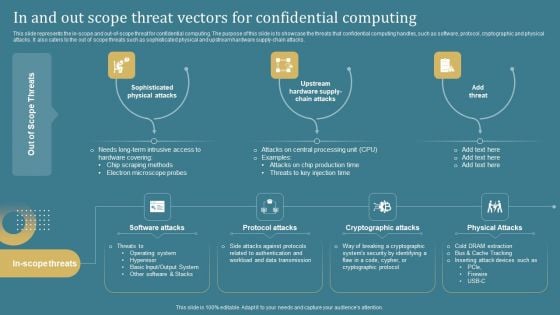
Confidential Computing System Technology In And Out Scope Threat Vectors For Confidential Professional PDF

 Home
Home