Threat
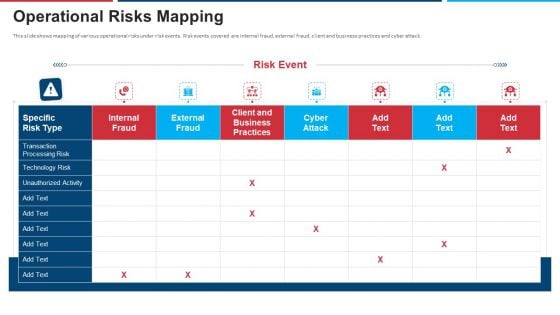
Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
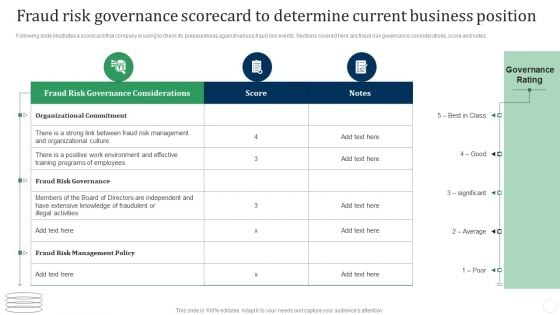
Fraud Risk Governance Scorecard To Determine Current Business Position Fraud Threat Administration Guide Sample PDF
Following slide illustrates a scorecard that company is using to check its preparedness against various fraud risk events. Sections covered here are fraud risk governance considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Fraud Risk Governance Scorecard To Determine Current Business Position Fraud Threat Administration Guide Sample PDF. Use them to share invaluable insights on Organizational Commitment, Risk Governance, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
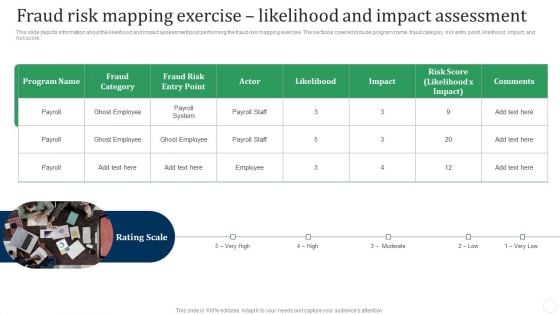
Fraud Risk Mapping Exercise Likelihood And Impact Assessment Fraud Threat Administration Guide Demonstration PDF
This slide depicts information about the likelihood and impact assessment post performing the fraud risk mapping exercise. The sections covered include program name, fraud category, risk entry point, likelihood, impact, and risk score.This is a Fraud Risk Mapping Exercise Likelihood And Impact Assessment Fraud Threat Administration Guide Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fraud Category, Ghost Employee, Fraud Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Use Case Fraud Risk Identified And Measures Taken Fraud Threat Administration Guide Icons PDF
Following slide depicts a use case for a fraud risk profile. It contains information about the identified risk as well as the organizations efforts to mitigate it.This is a Use Case Fraud Risk Identified And Measures Taken Fraud Threat Administration Guide Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Significance, Residual Risk, False Identity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Integration Of Risk Management Into Sdlc Infographics PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. This is a Information Technology Threat Mitigation Methods Integration Of Risk Management Into Sdlc Infographics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development, Implementation, Risk Management Activities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
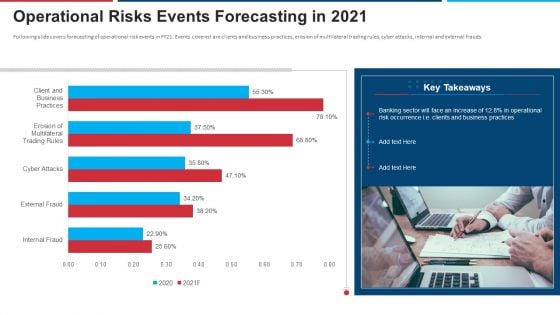
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigation Strategies For Operational Threat Budget For Operational Risk Management Ppt Infographics Slide Portrait PDF
Mentioned slide shows budget for operational risk management. It includes information such as functional department, training course, training duration, training cost, number of employees and total training cost. Presenting mitigation strategies for operational threat budget for operational risk management ppt infographics slide portrait pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risk management committee, training cost, implementation, training duration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
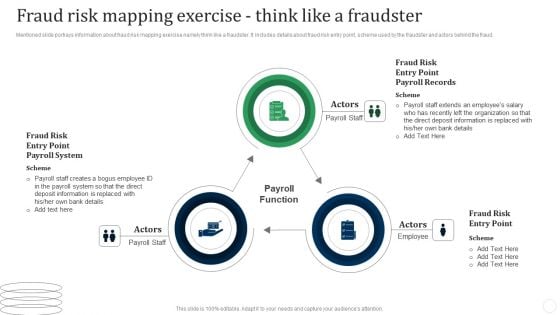
Fraud Risk Mapping Exercise Think Like A Fraudster Fraud Threat Administration Guide Rules PDF
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud.Presenting Fraud Risk Mapping Exercise Think Like A Fraudster Fraud Threat Administration Guide Rules PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Deposit Information, Staff Creates, Payroll Function. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
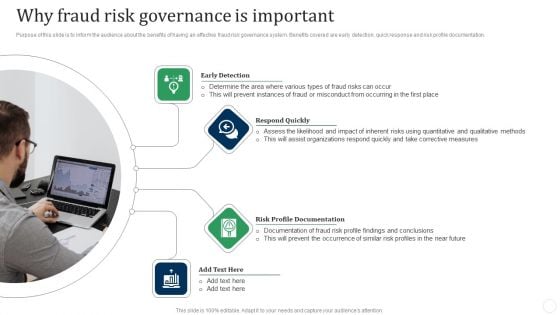
Why Fraud Risk Governance Is Important Fraud Threat Administration Guide Diagrams PDF
Purpose of this slide is to inform the audience about the benefits of having an effective fraud risk governance system. Benefits covered are early detection, quick response and risk profile documentation. This is a Why Fraud Risk Governance Is Important Fraud Threat Administration Guide Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Early Detection, Respond Quickly, Profile Documentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
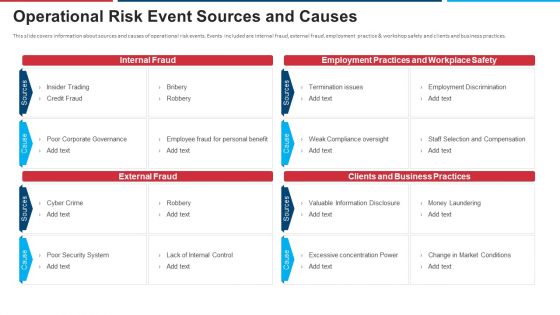
Mitigation Strategies For Operational Threat Operational Risk Event Sources And Causes Ppt Inspiration Introduction PDF
This slide covers information about sources and causes of operational risk events. Events included are internal fraud, external fraud, employment practice and workshop safety and clients and business practices. Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat operational risk event sources and causes ppt inspiration introduction pdf bundle. Topics like internal fraud, external fraud, employment practices and workplace safety, clients and business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
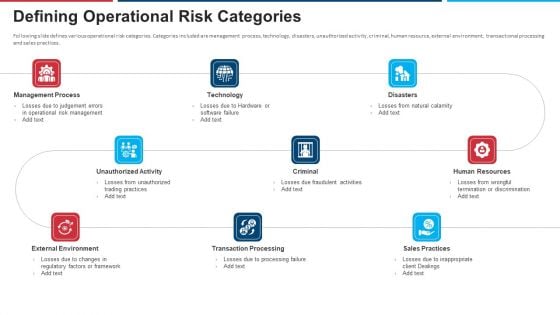
Mitigation Strategies For Operational Threat Defining Operational Risk Categories Ppt Styles Designs Download PDF
Following slide defines various operational risk categories. Categories included are management process, technology, disasters, unauthorized activity, criminal, human resource, external environment, transactional processing and sales practices. This is a mitigation strategies for operational threat defining operational risk categories ppt styles designs download pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management process, technology, disasters, external environment, human resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management For Organization Essential Assets Budget For Effective Threat Management Summary PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets budget for effective threat management summary pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process, document management, information management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Budget For Effective Threat Management At Workplace Portrait PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative corporate security and risk management budget for effective threat management at workplace portrait pdf bundle. Topics like incident management, risk management, client onboarding process, document management, information management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
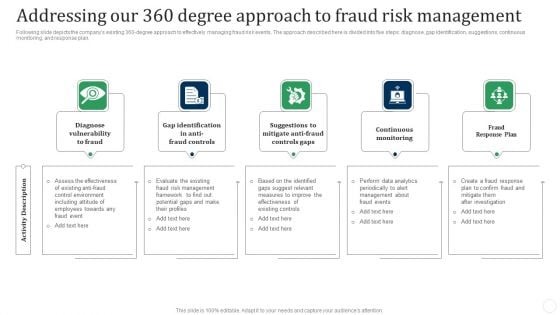
Addressing Our 360 Degree Approach To Fraud Risk Management Fraud Threat Administration Guide Structure PDF
Following slide depicts the companys existing 360-degree approach to effectively managing fraud risk events. The approach described here is divided into five steps diagnose, gap identification, suggestions, continuous monitoring, and response plan.This is a Addressing Our 360 Degree Approach To Fraud Risk Management Fraud Threat Administration Guide Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Assess Effectiveness, Control Environment, Including Attitude. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
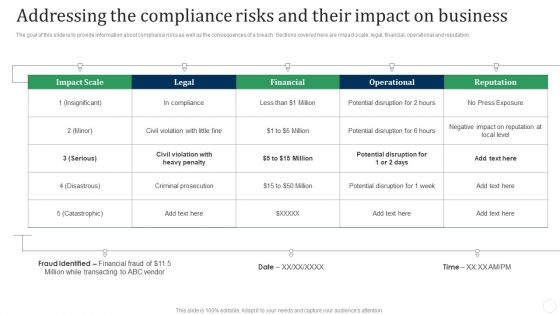
Addressing The Compliance Risks And Their Impact On Business Fraud Threat Administration Guide Topics PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation.Deliver an awe inspiring pitch with this creative Addressing The Compliance Risks And Their Impact On Business Fraud Threat Administration Guide Topics PDF bundle. Topics like Potential Disruption, Criminal Prosecution, Press Exposure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
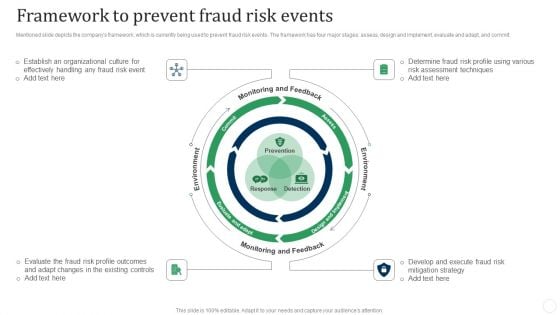
Framework To Prevent Fraud Risk Events Fraud Threat Administration Guide Pictures PDF
Mentioned slide depicts the companys framework, which is currently being used to prevent fraud risk events. The framework has four major stages assess, design and implement, evaluate and adapt, and commit.Presenting Framework To Prevent Fraud Risk Events Fraud Threat Administration Guide Pictures PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Establish Organizational, Effectively Handling, Evaluate Fraud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modifying Fraud Risk Management Activities Based On Continuous Feedback Fraud Threat Background PDF
Mentioned slide showcases the details about the three step feedback process that company will incorporate in order to effectively manage the fraud risks events.Presenting Modifying Fraud Risk Management Activities Based On Continuous Feedback Fraud Threat Background PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Gather Information, Information Collected, Sources Understand. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
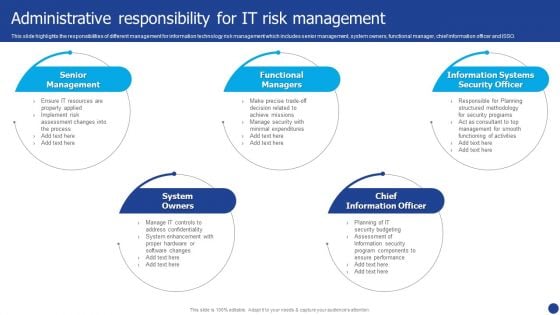
Information Technology Threat Mitigation Methods Administrative Responsibility For IT Risk Management Brochure PDF
This slide highlights the responsibilities of different management for information technology risk management which includes senior management, system owners, functional manager, chief information officer and ISSO. This is a Information Technology Threat Mitigation Methods Administrative Responsibility For IT Risk Management Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Managers, Chief Information Officer, System Owners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
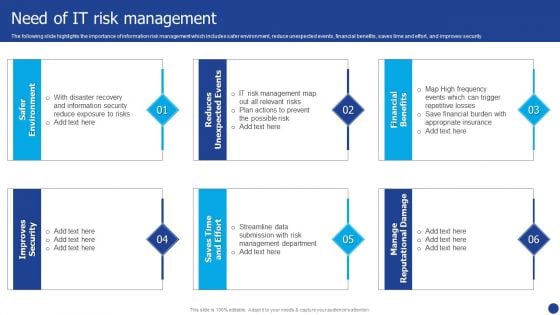
Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF
The following slide highlights the importance of information risk management which includes safer environment, reduce unexpected events, financial benefits, saves time and effort, and improves security. Presenting Information Technology Threat Mitigation Methods Need Of IT Risk Management Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Financial Benefits, Saves Time And Effort, Improves Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
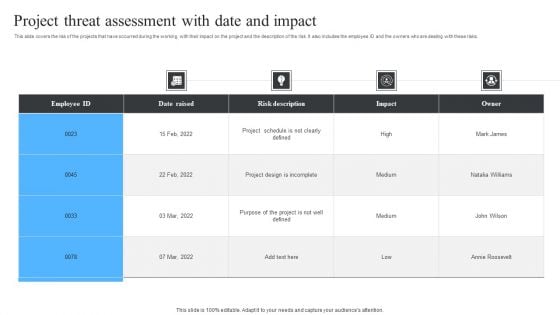
Project Threat Assessment With Date And Impact Ppt File Layout Ideas PDF
This slide covers the risk of the projects that have occurred during the working with their impact on the project and the description of the risk. It also includes the employee ID and the owners who are dealing with these risks. Pitch your topic with ease and precision using this Project Threat Assessment With Date And Impact Ppt File Layout Ideas PDF. This layout presents information on Employee ID, Risk Description, Project Design Incomplete. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
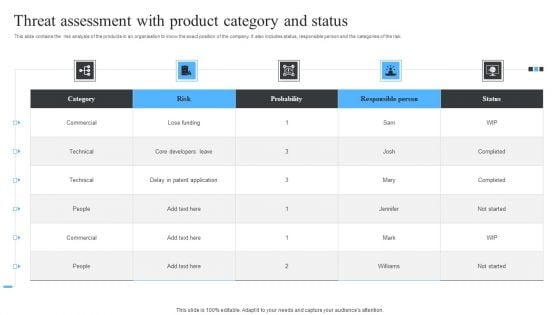
Threat Assessment With Product Category And Status Ppt Slides Master Slide PDF
This slide contains the risk analysis of the products in an organisation to know the exact position of the company. It also includes status, responsible person and the categories of the risk. Pitch your topic with ease and precision using this Threat Assessment With Product Category And Status Ppt Slides Master Slide PDF. This layout presents information on Risk, Probability, Commercial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Corrective Action Plan To Prevent Fraud In Future Fraud Threat Administration Guide Graphics PDF
Purpose of this slide is to address companys fraud risk prevention plan covering details about the activity, fraud risk and mitigation plan.Presenting Corrective Action Plan To Prevent Fraud In Future Fraud Threat Administration Guide Graphics PDF to provide visual cues and insights. Share and navigate important information on onestage that need your due attention. This template can be used to pitch topics like Financial Transactions, Personal Identification, Incorporate Identity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
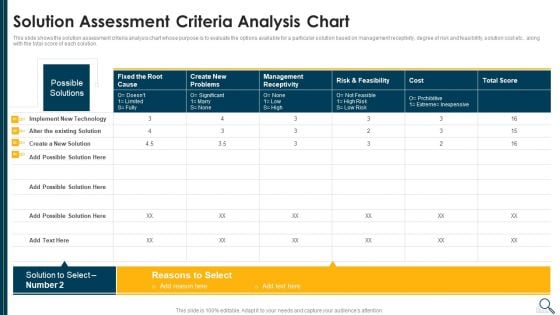
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment Criteria Themes PDF
This slide shows the solution assessment criteria analysis chart whose purpose is to evaluate the options available for a particular solution based on management receptivity, degree of risk and feasibility, solution cost etc. along with the total score of each solution. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment criteria themes pdf bundle. Topics like solution assessment criteria analysis chart can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
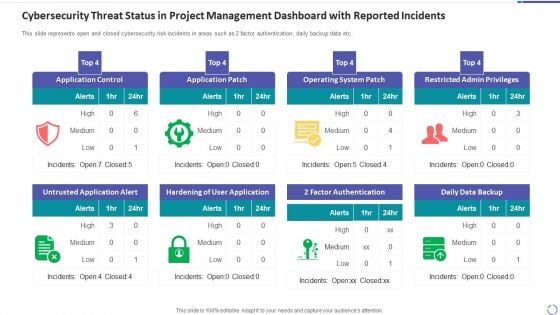
Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
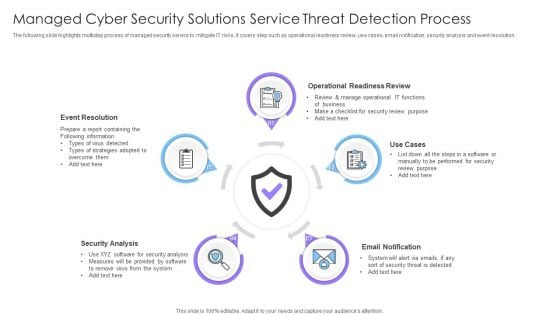
Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
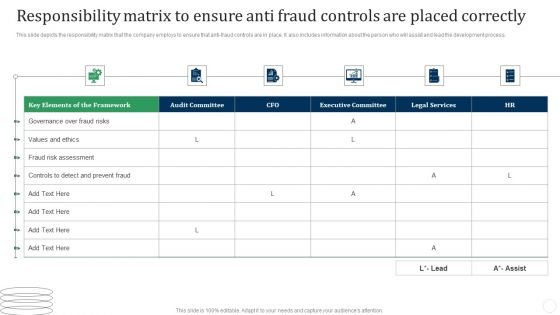
Responsibility Matrix To Ensure Anti Fraud Controls Are Placed Correctly Fraud Threat Introduction PDF
This slide depicts the responsibility matrix that the company employs to ensure that anti fraud controls are in place. It also includes information about the person who will assist and lead the development process.Deliver and pitch your topic in the best possible manner with this Responsibility Matrix To Ensure Anti Fraud Controls Are Placed Correctly Fraud Threat Introduction PDF. Use them to share invaluable insights on Elements Framework, Governance Over, Risk Assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
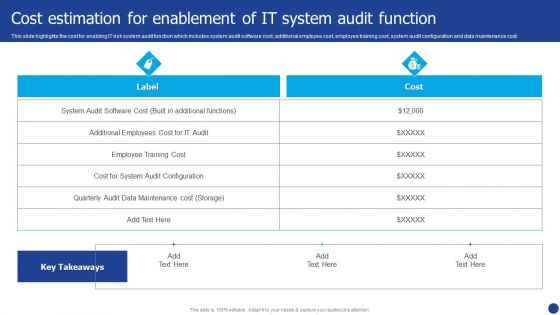
Information Technology Threat Mitigation Methods Cost Estimation For Enablement Of IT System Audit Function Topics PDF
This slide highlights the cost for enabling IT risk system audit function which includes system audit software cost, additional employee cost, employee training cost, system audit configuration and data maintenance cost. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Cost Estimation For Enablement Of IT System Audit Function Topics PDF. Use them to share invaluable insights on Additional Employees Cost, Data Maintenance Cost, System Audit Software Cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
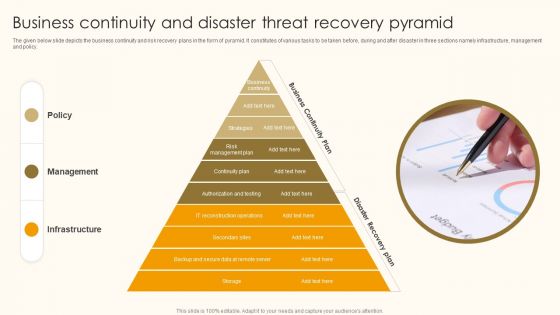
Business Continuity And Disaster Threat Recovery Pyramid Ppt Ideas Pictures PDF
The given below slide depicts the business continuity and risk recovery plans in the form of pyramid. It constitutes of various tasks to be taken before, during and after disaster in three sections namely infrastructure, management and policy. Presenting Business Continuity And Disaster Threat Recovery Pyramid Ppt Ideas Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Policy, Management, Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Continuity And Disaster Threat Reduction Methodology Ppt Portfolio Show PDF
The given below slide illustrates the steps for disaster risk reduction to reduce its impact on business. It begins with program initiation, stating requirements, strategy identification, plan documentation and ends with program management and testing. Persuade your audience using this Business Continuity And Disaster Threat Reduction Methodology Ppt Portfolio Show PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Program Initiation, State Requirements, Strategy Identification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
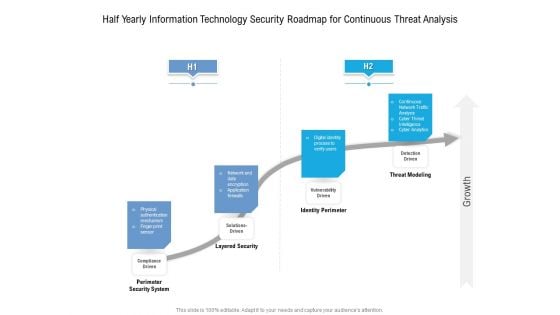
Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
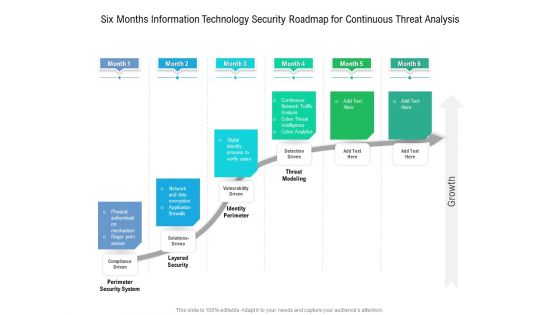
Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
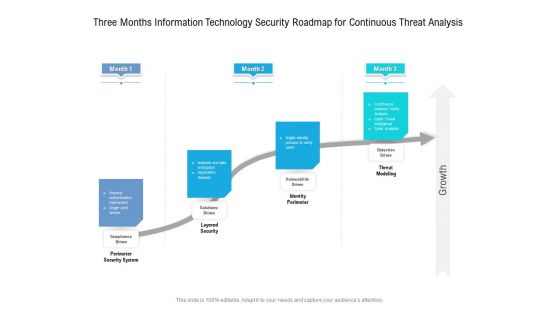
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
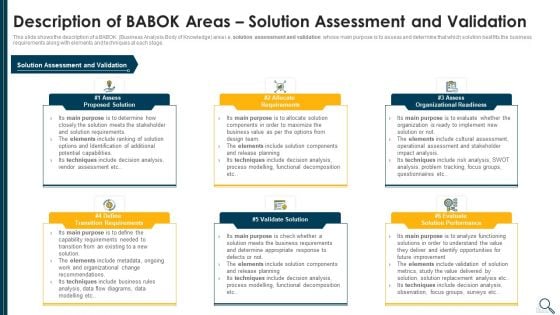
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Slides PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like requirements, organizational readiness, validate solution, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
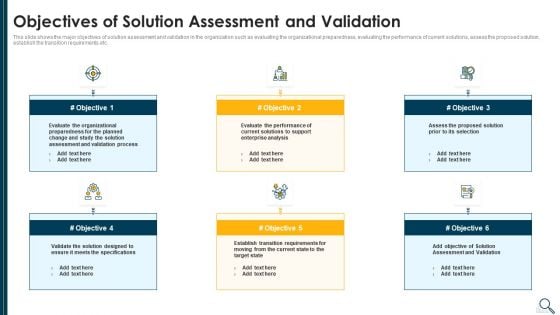
Solution Evaluation Criteria Assessment And Threat Impact Matrix Objectives Of Solution Assessment Rules PDF
This slide shows the major objectives of solution assessment and validation in the organization such as evaluating the organizational preparedness, evaluating the performance of current solutions, assess the proposed solution, establish the transition requirements etc. This is a solution evaluation criteria assessment and threat impact matrix objectives of solution assessment rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, process, enterprise analysis, performance, evaluate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
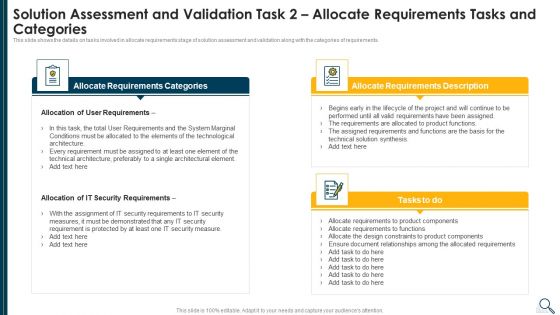
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Task Ideas PDF
This slide shows the solution assessment and validation model or framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix solution assessment and validation task ideas pdf. Use them to share invaluable insights on solution assessment and validation model of the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
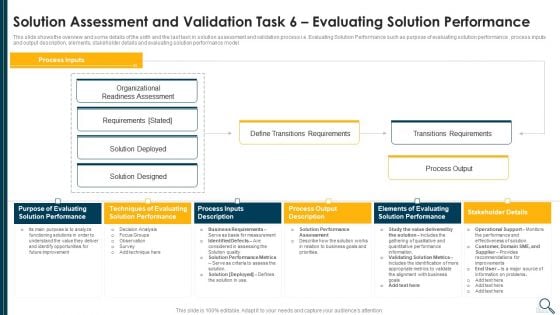
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Information PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment and validation information pdf bundle. Topics like evaluating, performance, organizational, process output can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Assess Organizational Readiness Icons PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc. along with the benefits of force field analysis tool. This is a solution evaluation criteria assessment and threat impact matrix assess organizational readiness icons pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce issues, execution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
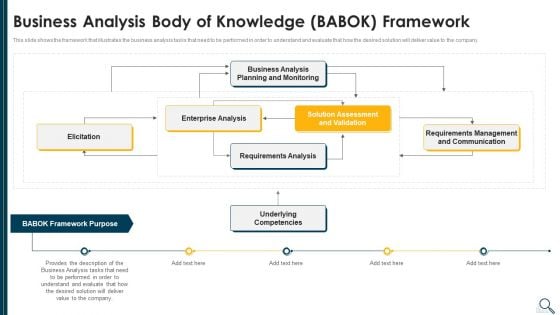
Solution Evaluation Criteria Assessment And Threat Impact Matrix Business Analysis Body Introduction PDF
This slide shows the framework that illustrates the business analysis tasks that need to be performed in order to understand and evaluate that how the desired solution will deliver value to the company. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix business analysis body introduction pdf bundle. Topics like enterprise analysis, requirements analysis, communication, requirements management, business analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Importance Of Solution Assessment Clipart PDF
This slide shows the importance of solution assessment and validation process with details such as assessment details, customer needs, validation details, product component and product requirement details, alternative solutions etc. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix importance of solution assessment clipart pdf. Use them to share invaluable insights on requirements development, product integration, customer, product components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Contingency Plan For Threat Handling Slides PDF
This slide covers details regarding the network optimization capabilities in terms of advanced caching capabilities, TCP layer optimization, global balancing of load, etc. This is a executing advance data analytics at workspace contingency plan for threat handling slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like caching capabilities, routing optimization, layer optimization, distributed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
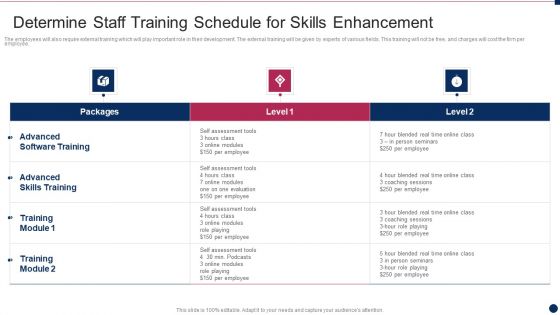
Threat Management At Workplace Determine Staff Training Schedule For Skills Enhancement Graphics Pdf
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver and pitch your topic in the best possible manner with this threat management at workplace determine staff training schedule for skills enhancement graphics pdf. Use them to share invaluable insights on advanced skills training, advanced software training, blended real time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
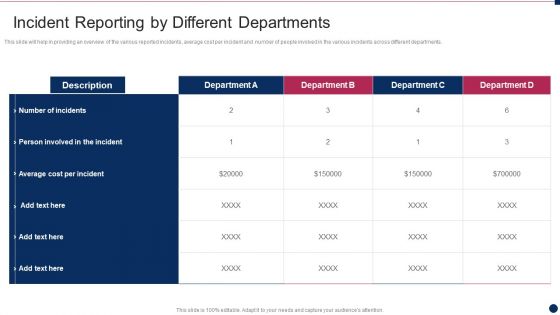
Threat Management At Workplace Incident Reporting By Different Departments Download PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative threat management at workplace incident reporting by different departments download pdf bundle. Topics like average cost per incident, person involved in the incident, across different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Roles And Responsibilities To Ensure Work Environment Sample PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a threat management at workplace roles and responsibilities to ensure work environment sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, internal investigations unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
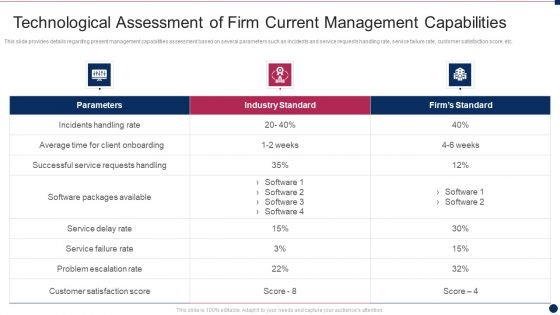
Threat Management At Workplace Technological Assessment Of Firm Current Management Structure PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace technological assessment of firm current management structure pdf. Use them to share invaluable insights on service delay rate, average time for client onboarding, successful service requests handling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware.This is a Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compromise Scams, Ransomware, Confidential Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF
This slide provides an overview about corporate frauds along with the factual information of global fraud events. It also includes the statistics on fraud volume as well as fraud value.Deliver and pitch your topic in the best possible manner with this Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF. Use them to share invaluable insights on Experienced Fraud, Event Past, Experienced Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
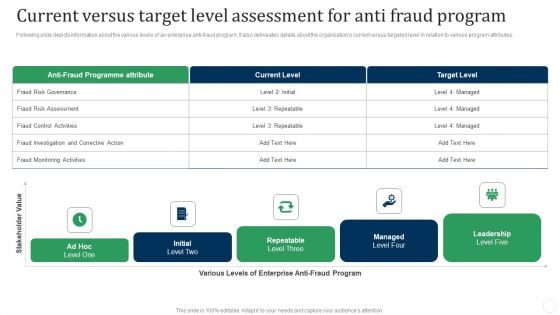
Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF
Following slide depicts information about the various levels of an enterprise anti-fraud program. It also delineates details about the organizations current versus targeted level in relation to various program attributes.Deliver an awe inspiring pitch with this creative Current Versus Target Level Assessment For Anti Fraud Program Fraud Threat Administration Guide Microsoft PDF bundle. Topics like Programmed Attribute, Fraud Investigation, Monitoring Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
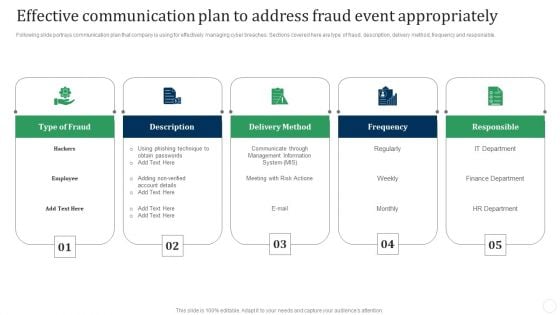
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide.This is a Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Compromise, Ransomware, Malicious Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
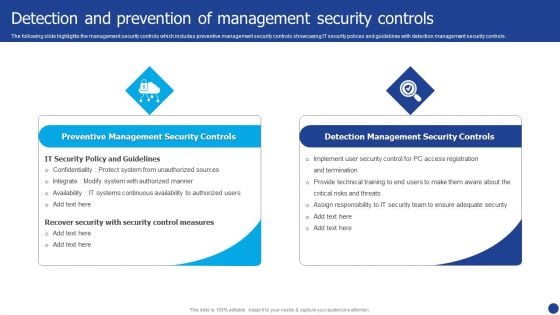
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
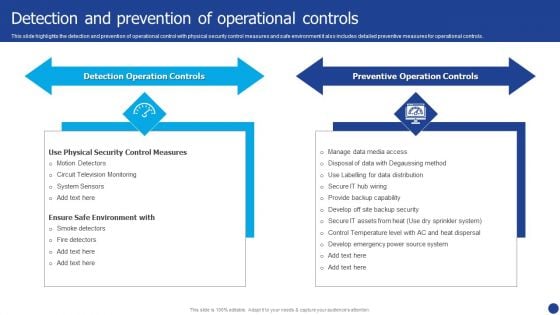
Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
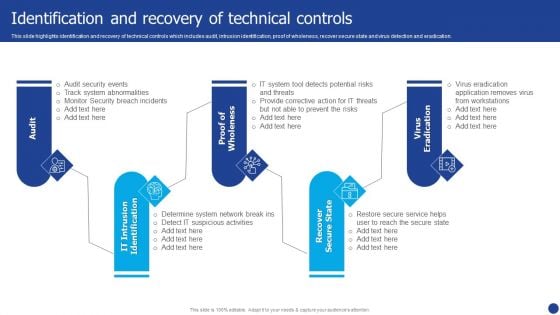
Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
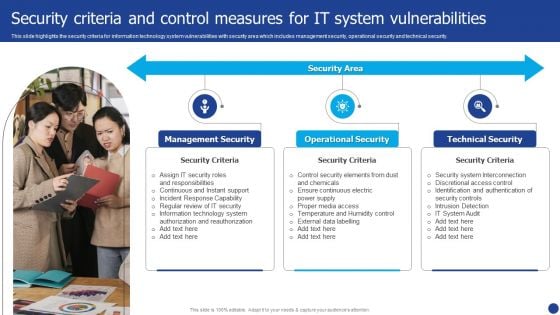
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
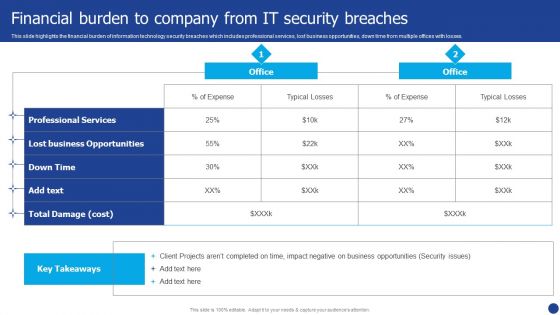
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
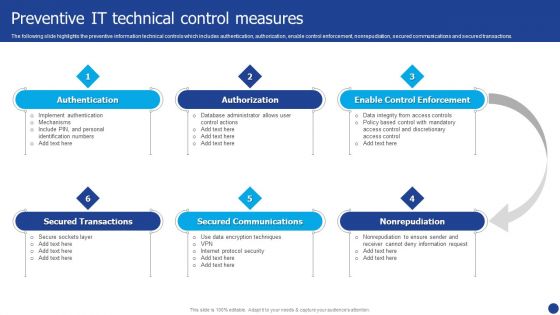
Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Business Disaster Threat Recovery Plan Ppt Inspiration Design Ideas PDF
The given below slide depicts a checklist to successfully implement disaster recovery plan. It includes elements such as BIA, RTO, response strategy, recovery site, response team, maintenance and testing. Presenting Checklist For Business Disaster Threat Recovery Plan Ppt Inspiration Design Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Elements, Business Impact Analysis, Response Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threat Icon Business Risk Ppt PowerPoint Presentation Complete Deck With Slides
This threat icon business risk ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this threat icon business risk ppt powerpoint presentation complete deck with slides PPT slideshow.

Incident Business Security Threat Ppt PowerPoint Presentation Complete Deck With Slides
This incident business security threat ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this incident business security threat ppt powerpoint presentation complete deck with slides PPT slideshow.

Risk Analysis Risk Analysis Register To Determine Potential Threat Infographics PDF
This slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Present like a pro with Risk Analysis Risk Analysis Register To Determine Potential Threat Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

 Home
Home