lock

Table Of Contents For Screen Reader Accessible Website Pictures Pdf
Boost your pitch with our creative Table Of Contents For Screen Reader Accessible Website Pictures Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Table Of Contents For Screen Reader Accessible Website Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Explore a selection of the finest Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Setting Up Access Control System In Organization Application Security Testing
This slide represents the installation process of access control system for application security in an organization. Explore a selection of the finest Setting Up Access Control System In Organization Application Security Testing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Setting Up Access Control System In Organization Application Security Testing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the installation process of access control system for application security in an organization.

Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V
This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing. Make sure to capture your audiences attention in your business displays with our gratis customizable Building Trust With IoT Security Emerging Technologies Enhancing IoT Security And Privacy IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing.

Zero Trust Network Access Ppt Powerpoint Presentation Complete Deck With Slides
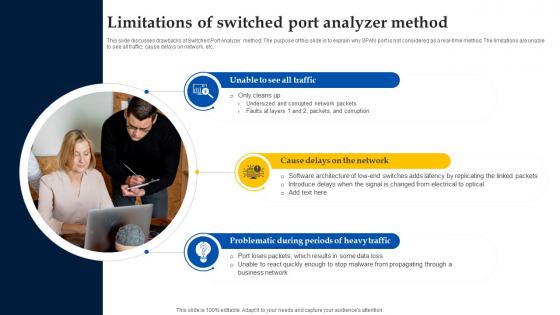
Web Access Control Solution Limitations Of Switched Port Analyzer Method
This slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. This Web Access Control Solution Limitations Of Switched Port Analyzer Method from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc.
Right Lymphatic Duct In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Right Lymphatic Duct In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Right Lymphatic Duct that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Right Lymphatic Duct In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Privacy Security Ppt PowerPoint Presentation File Background Image
Presenting this set of slides with name privacy security ppt powerpoint presentation file background image. This is a four stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Zero Trust Network Access On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Boost your pitch with our creative Zero Trust Network Access On Ramp Option 1 User And Device Identity. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
Organs Under Right Rib Cage In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Organs Under Right Rib Cage In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Organs Under Right Rib Cage that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Organs Under Right Rib Cage In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. Make sure to capture your audiences attention in your business displays with our gratis customizable Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Information Privacy IT Five Data Privacy Rules Topics PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. This is a information privacy it five data privacy rules topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disposal and destruction, access and security, accountability and disclosure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
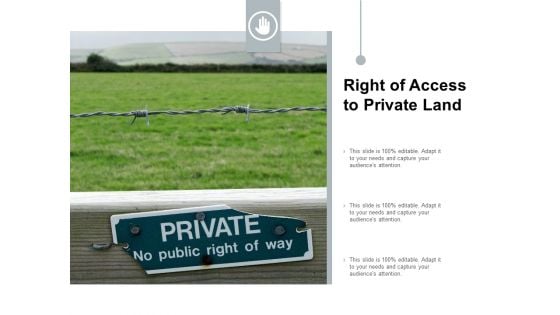
Right Of Access To Private Land Ppt PowerPoint Presentation Pictures Ideas
This is a right of access to private land ppt powerpoint presentation pictures ideas. This is a three stage process. The stages in this process are access rights, access management, business.

Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. This modern and well-arranged Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation. This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc.
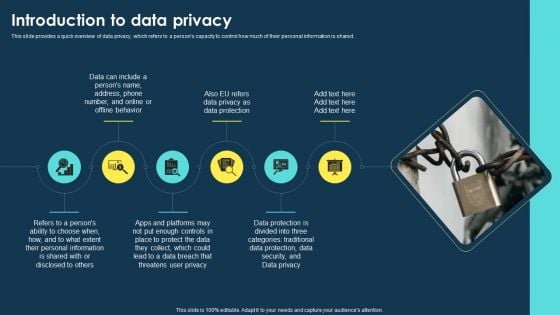
Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF
This slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. This Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
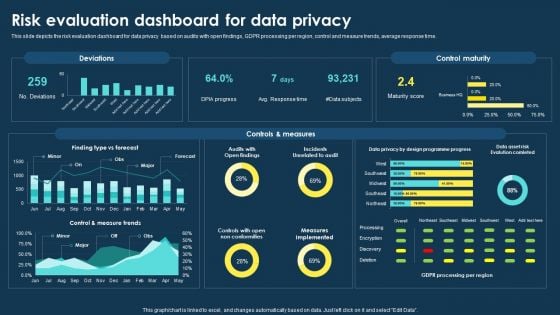
Integrating Data Privacy System Roadmap For Data Privacy Implementation Ppt Ideas Graphic Images
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Explore a selection of the finest Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
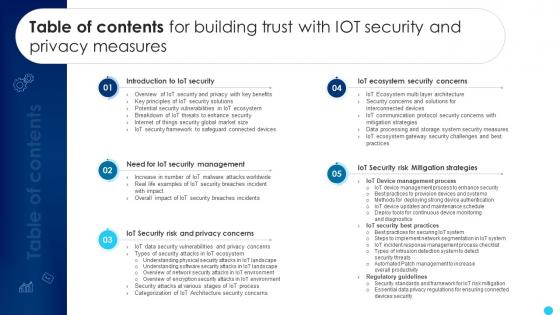
Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Our Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
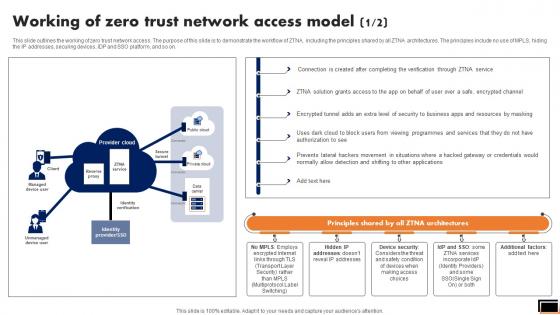
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
Corporate Data Management And Privacy Security Mechanism Icon Slides PDF
Persuade your audience using this Corporate Data Management And Privacy Security Mechanism Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Data, Management Privacy, Security Mechanism Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
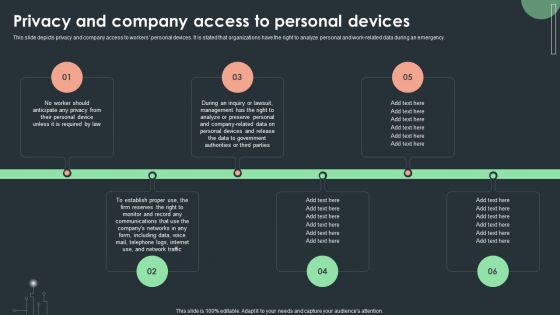
Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
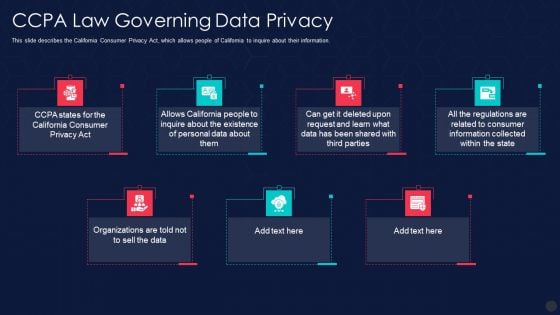
Information Privacy IT Ccpa Law Governing Data Privacy Graphics PDF
This slide describes the California Consumer Privacy Act, which allows people of California to inquire about their information. Presenting information privacy it ccpa law governing data privacy graphics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like ccpa law governing data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Data Privacy In Healthcare Designs PDF
This slide represents data privacy in the healthcare industry, decreasing risks and keeping the business operations functioning. This is a information privacy it data privacy in healthcare designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data privacy in healthcare. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Our Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Information Privacy It Privacy Clipart PDF
Presenting table of contents for information privacy it privacy clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like overview, privacy, industries. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Checklist For Data Privacy Implementation Summary PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. This is a information privacy it checklist for data privacy implementation summary pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like checklist for data privacy implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT Elements Of Data Privacy Graphics PDF
This slide depicts the elements of data privacy, including individuals having the right to privacy and control over personal information, laws being followed, and processing data properly. This is a information privacy it elements of data privacy graphics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of data privacy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT Roadmap For Data Privacy Implementation Brochure PDF
This slide depicts the roadmap for data privacy implementation that includes hiring DPO as per GDPR requirement, also checking privacy threats within and outside the organization. This is a information privacy it roadmap for data privacy implementation brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap for data privacy implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
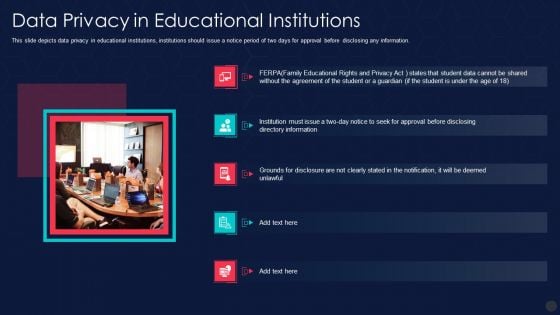
Information Privacy IT Data Privacy In Educational Institutions Summary PDF
This slide depicts data privacy in educational institutions, institutions should issue a notice period of two days for approval before disclosing any information. Presenting information privacy it data privacy in educational institutions summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data privacy in educational institutions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Data Privacy In Financial Institutions Information PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This is a information privacy it data privacy in financial institutions information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data privacy in financial institutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
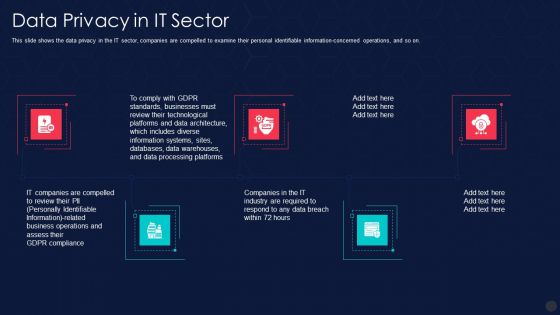
Information Privacy IT Data Privacy In It Sector Elements PDF
This slide shows the data privacy in the IT sector, companies are compelled to examine their personal identifiable information concerned operations, and so on. Presenting information privacy it data privacy in it sector elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data privacy in it sector. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Data Privacy In Social Media Inspiration PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. This is a information privacy it data privacy in social media inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data privacy in social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Privacy IT Introduction To Data Privacy Icons PDF
This slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. Presenting information privacy it introduction to data privacy icons pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like introduction to data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Training Schedule For Data Privacy Demonstration PDF
This slide represents the data privacy training program by covering the details of topics such as benefits and laws and duration for each topic to be covered. This is a information privacy it training schedule for data privacy demonstration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like training schedule for data privacy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
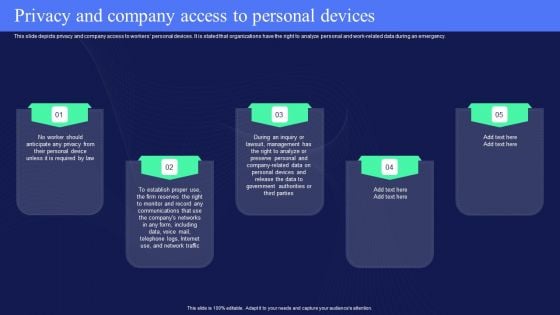
IT Policies And Procedures Privacy And Company Access To Personal Devices Download PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download IT Policies And Procedures Privacy And Company Access To Personal Devices Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the IT Policies And Procedures Privacy And Company Access To Personal Devices Download PDF.

Overview Sharing Access Over Ownership Business Model DT SS V
This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.This Overview Sharing Access Over Ownership Business Model DT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide presents an overview of sharing model or access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner.
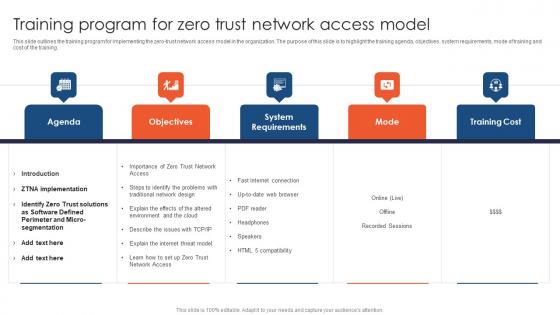
Zero Trust Network Access Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Explore a selection of the finest Zero Trust Network Access Training Program For Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Training Program For Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.
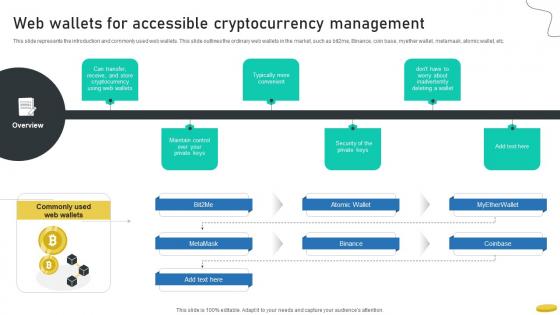
Web Wallets For Accessible Cryptocurrency Management Cryptocurrency Management With Blockchain
This slide represents the introduction and commonly used web wallets. This slide outlines the ordinary web wallets in the market, such as bit2me, Binance, coin base, myether wallet, metamask, atomic wallet, etc.Explore a selection of the finest Web Wallets For Accessible Cryptocurrency Management Cryptocurrency Management With Blockchain here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Wallets For Accessible Cryptocurrency Management Cryptocurrency Management With Blockchain to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the introduction and commonly used web wallets. This slide outlines the ordinary web wallets in the market, such as bit2me, Binance, coin base, myether wallet, metamask, atomic wallet, etc.
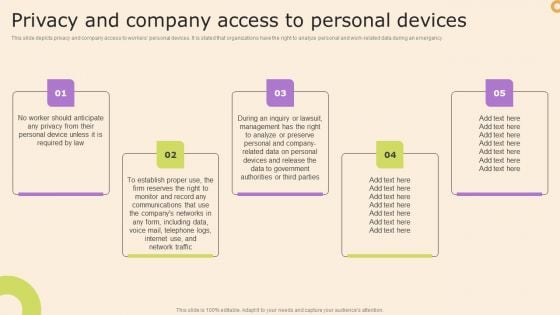
Information Technology Policy And Processes Privacy And Company Access To Personal Devices Graphics PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Retrieve professionally designed Information Technology Policy And Processes Privacy And Company Access To Personal Devices Graphics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
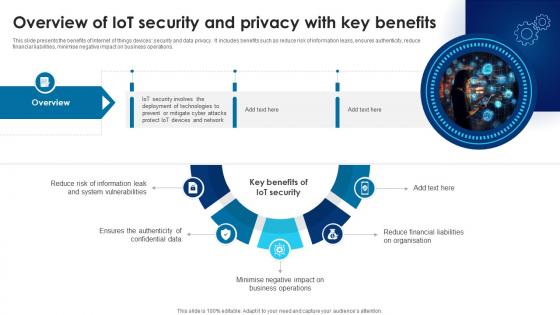
Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V
This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations.
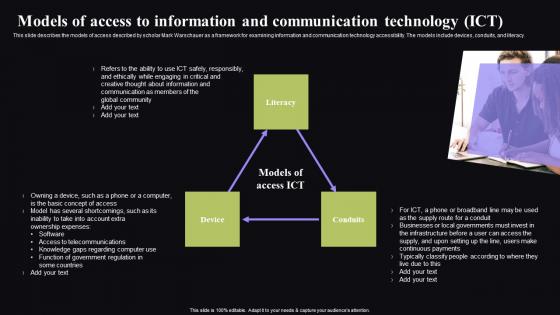
Models Of Access To Information Video Conferencing In Corporate Inspiration Pdf
This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Models Of Access To Information Video Conferencing In Corporate Inspiration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the models of access described by scholar Mark Warschauer as a framework for examining information and communication technology accessibility. The models include devices, conduits, and literacy.
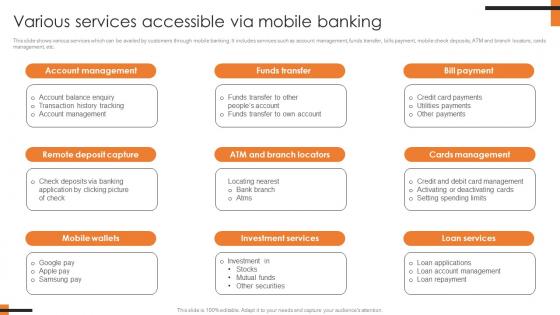
Various Services Accessible Via Mobile Banking Comprehensive Smartphone Banking Mockup Pdf
This slide shows various services which can be availed by customers through mobile banking. It includes services such as account management, funds transfer, bills payment, mobile check deposits, ATM and branch locators, cards management, etc.This Various Services Accessible Via Mobile Banking Comprehensive Smartphone Banking Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide shows various services which can be availed by customers through mobile banking. It includes services such as account management, funds transfer, bills payment, mobile check deposits, ATM and branch locators, cards management, etc.

Accessing Metaverse Through Technologies 3D Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding development and growth of metaverse through emerging technologies such as 3D modeling. It is process of creating 3D representation of object or surface in virtual space. Boost your pitch with our creative Accessing Metaverse Through Technologies 3D Continuum Of Technology Revamping Business AI SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide provides information regarding development and growth of metaverse through emerging technologies such as 3D modeling. It is process of creating 3D representation of object or surface in virtual space.
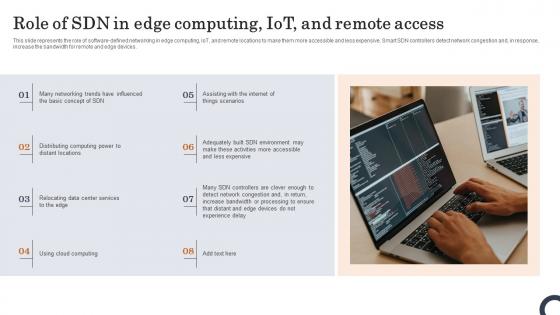
Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. This Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices.
VPN Privacy And Security Vector Icon Ppt PowerPoint Presentation Model Slides PDF
Presenting vpn privacy and security vector icon ppt powerpoint presentation model slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn privacy and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Security And Privacy With Biometric Ppt PowerPoint Presentation Gallery Slides PDF
Presenting data security and privacy with biometric ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data security and privacy with biometric. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Privacy Vector Icon Ppt PowerPoint Presentation File Graphic Images
Presenting this set of slides with name information privacy vector icon ppt powerpoint presentation file graphic images. This is a one stage process. The stage in this process is information privacy vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Privacy IT Accuracy Principle Of Gdpr Law Clipart PDF
This slide depicts the accuracy principle, which emphasizes that you are responsible for all efforts taken to ensure the datas privacy it must be correct and up to date. This is a information privacy it accuracy principle of gdpr law clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like accuracy principle of gdpr law. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
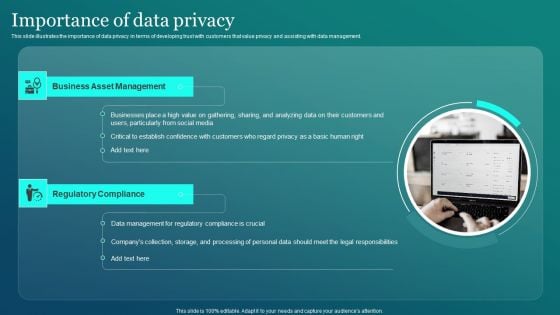
Information Security Importance Of Data Privacy Demonstration PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Explore a selection of the finest Information Security Importance Of Data Privacy Demonstration PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Security Importance Of Data Privacy Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
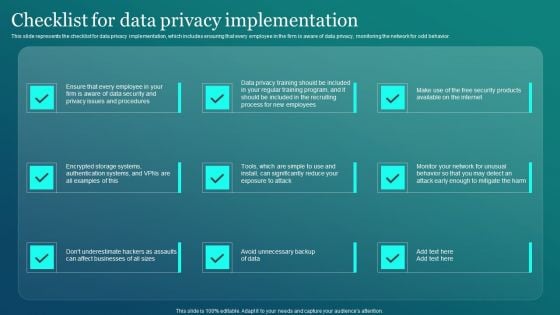
Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
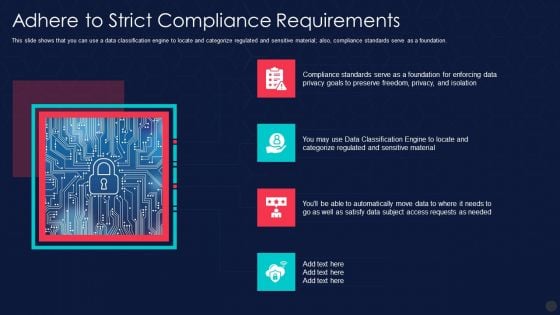
Information Privacy IT Adhere To Strict Compliance Requirements Slides PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. Presenting information privacy it adhere to strict compliance requirements slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like adhere to strict compliance requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
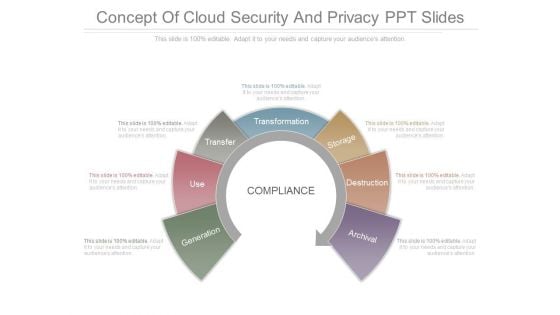
Concept Of Cloud Security And Privacy Ppt Slides
This is a concept of cloud security and privacy ppt slides. This is a seven stage process. The stages in this process are generation, use, transfer, transformation, storage, destruction, archival, compliance.
Data Security Privacy Ppt PowerPoint Presentation Icon Deck Cpb
Presenting this set of slides with name data security privacy ppt powerpoint presentation icon deck cpb. This is an editable Powerpoint six stages graphic that deals with topics like data security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Privacy Ppt PowerPoint Presentation Gallery Deck Cpb Pdf
Presenting this set of slides with name information security privacy ppt powerpoint presentation gallery deck cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like information security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
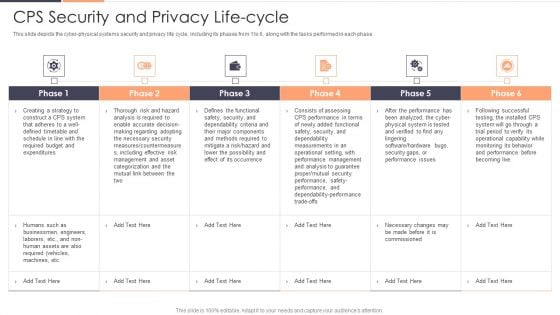
CPS Security And Privacy Life Cycle Ppt Gallery Professional PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Deliver and pitch your topic in the best possible manner with this CPS Security And Privacy Life Cycle Ppt Gallery Professional PDF. Use them to share invaluable insights on Risk, Required, Securityand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
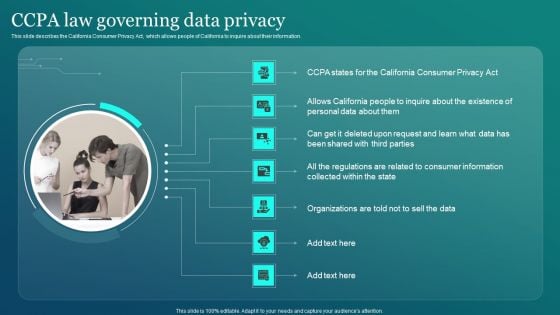
Information Security CCPA Law Governing Data Privacy Clipart PDF
This slide describes the California Consumer Privacy Act, which allows people of California to inquire about their information. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Security CCPA Law Governing Data Privacy Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Security CCPA Law Governing Data Privacy Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
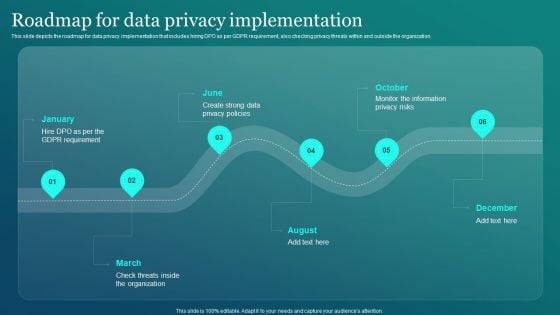
Information Security Roadmap For Data Privacy Implementation Information PDF
This slide depicts the roadmap for data privacy implementation that includes hiring DPO as per GDPR requirement, also checking privacy threats within and outside the organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Security Roadmap For Data Privacy Implementation Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Security Roadmap For Data Privacy Implementation Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.


 Continue with Email
Continue with Email

 Home
Home


































