lock

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing.
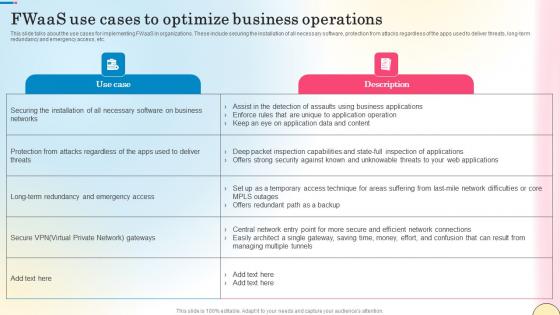
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.
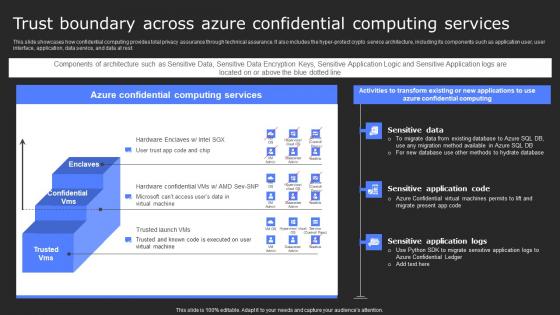
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Major Reasons To Manage Online Protection And Privacy Issues Template PDF
The following slide highlights the major causes to administer digital security and privacy concerns. It includes activities such as setting credibility with users, optimizing social media presence, improving marketing efforts etc. Persuade your audience using this Major Reasons To Manage Online Protection And Privacy Issues Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Set Credibility With Users, Optimize Social Media Presence, To Reduce Damage Expenses. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
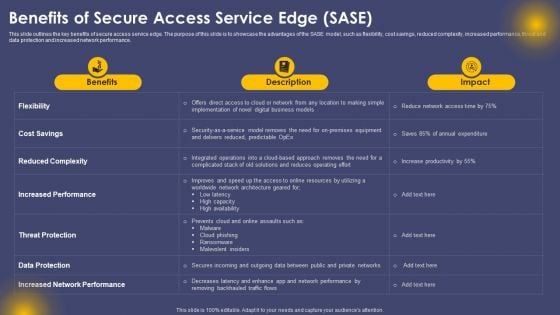
Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF
This slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. This Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
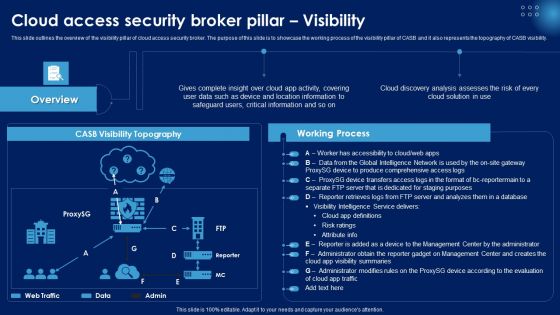
Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
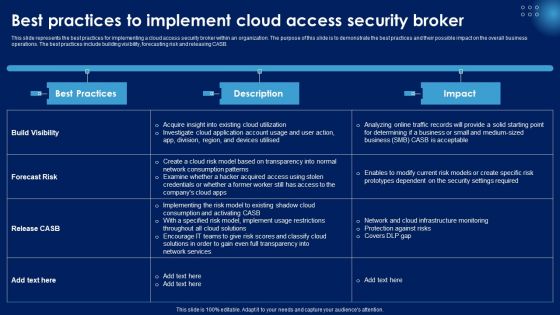
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
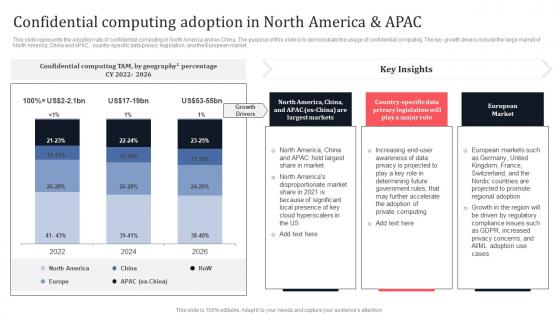
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
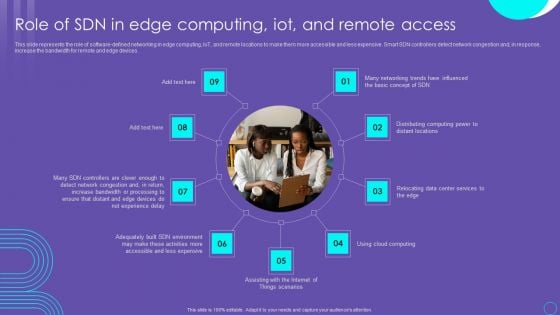
SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc.

Security Control Laptop Access Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security control laptop access ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the eleven slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
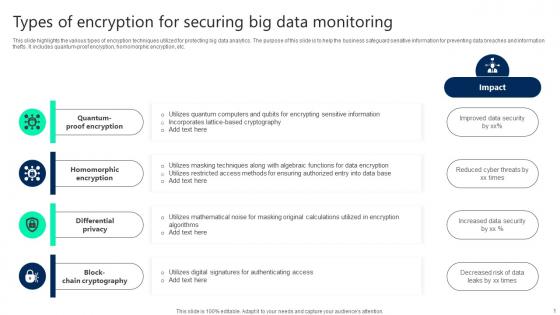
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.

Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Customer Data Platform Safety Privacy Microsoft PDF
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. Welcome to our selection of the Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Customer Data Platform Safety Privacy Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
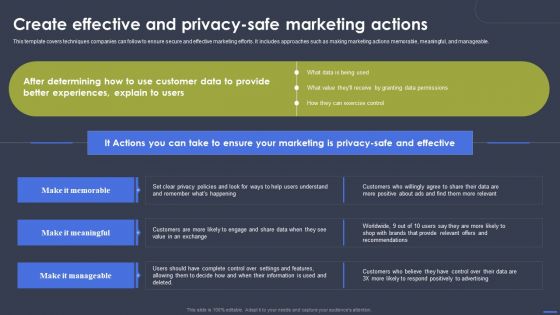
Optimizing Digital Marketing Strategy Create Effective And Privacy Safe Marketing Actions Diagrams PDF
This template covers techniques companies can follow to ensure secure and effective marketing efforts. It includes approaches such as making marketing actions memorable, meaningful, and manageable. Slidegeeks is here to make your presentations a breeze with Optimizing Digital Marketing Strategy Create Effective And Privacy Safe Marketing Actions Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
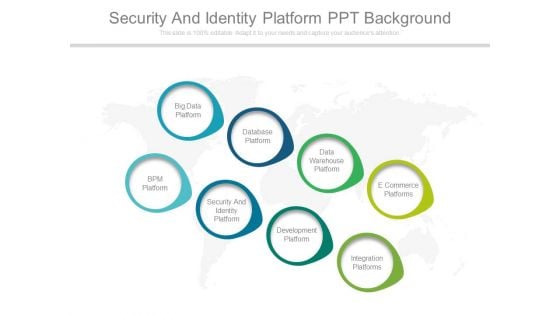
Security And Identity Platform Ppt Background
This is a security and identity platform ppt background. This is a eight stage process. The stages in this process are big data platform, database platform, data warehouse platform, e commerce platforms, bpm platform, security and identity platform, development platform, integration platforms.
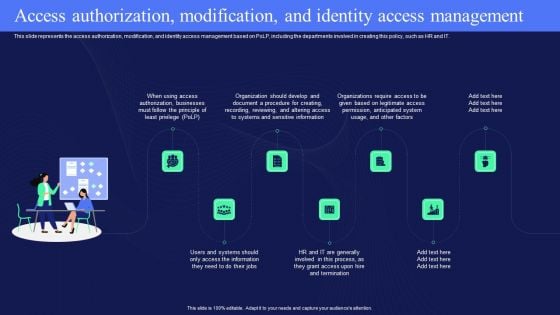
IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF
This slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
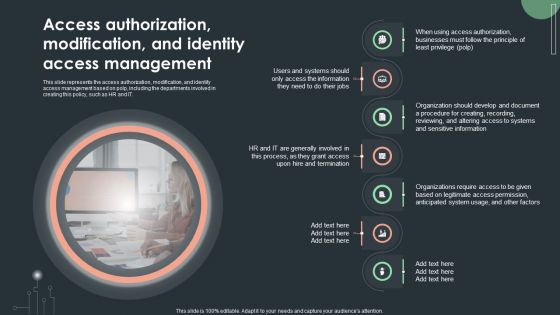
Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF
This slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.
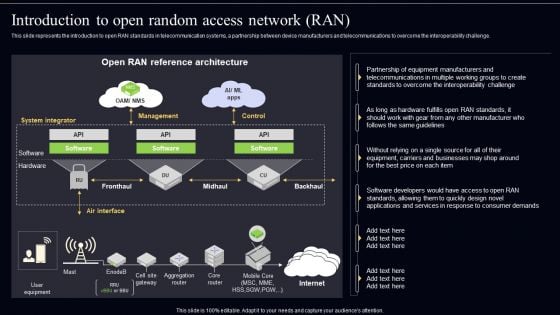
Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
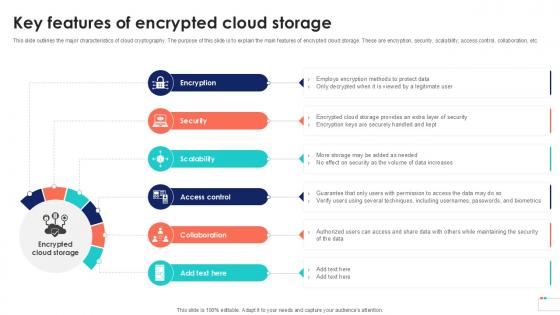
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Company Management Strategy Portrait PDF
This slide shows data safety and privacy benefits of fomfarm digital platform to fred farming company such as ownership, collection and control, transparency, choice, liability and security etc.This is a Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Company Management Strategy Portrait PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Platform Is Committed, Contractual Agreement, Reasonable Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
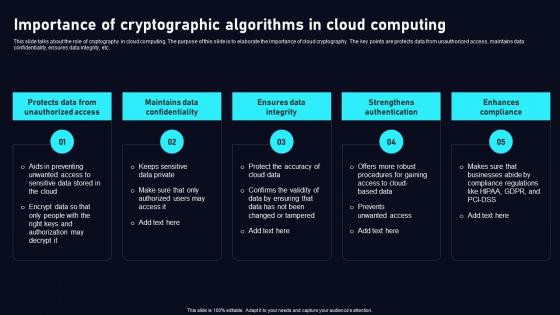
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
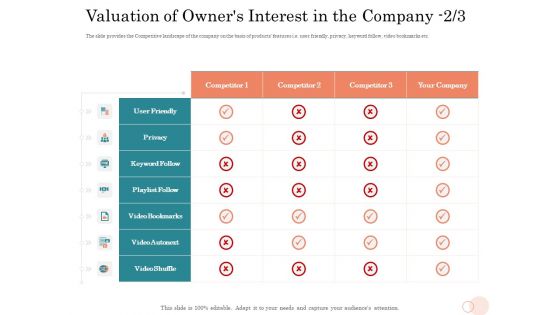
Option Pool Funding Pitch Deck Valuation Of Owners Interest In The Company Privacy Formats PDF
The slide provides the Competitive landscape of the company on the basis of products features i.e. user friendly, privacy, keyword follow, video bookmarks etc. Deliver an awe inspiring pitch with this creative option pool funding pitch deck valuation of owners interest in the company privacy formats pdf bundle. Topics like privacy, video bookmarks, playlist follow, video shuffle, user friendly can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
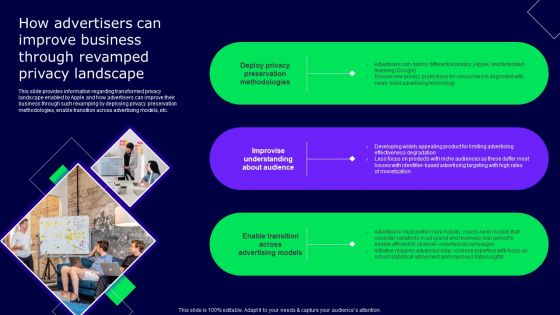
How Advertisers Can Improve Business Through Revamped Privacy Landscape Rules PDF
This slide provides information regarding transformed privacy landscape enabled by Apple and how advertisers can improve their business through such revamping by deploying privacy preservation methodologies, enable transition across advertising models, etc. There are so many reasons you need a How Advertisers Can Improve Business Through Revamped Privacy Landscape Rules PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Business Privacy Policy Icon On Computer Monitor Ppt PowerPoint Presentation Gallery Slide Download PDF
Presenting business privacy policy icon on computer monitor ppt powerpoint presentation gallery slide download pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including business privacy policy icon on computer monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5 Focus Area Diagram For Data Mining Privacy Issues Ppt Icon Clipart Images PDF
Presenting 5 focus area diagram for data mining privacy issues ppt icon clipart images pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including 5 focus area diagram for data mining privacy issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Electoral Mechanism IT Voting System Standards Privacy Usability Accessibility Ppt Professional Templates PDF
This slide represents the voting system standards such as privacy, usability, and accessibility that allow all voters, such as physically challenged or old, to vote freely. This is a electoral mechanism it voting system standards privacy usability accessibility ppt professional templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy, usability, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
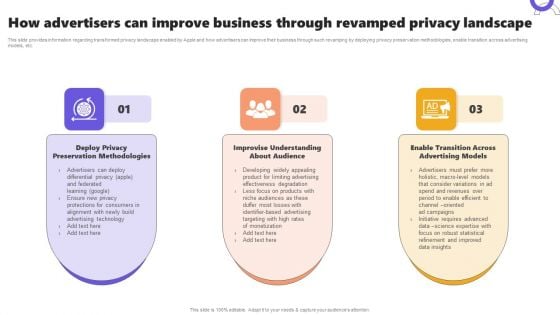
How Advertisers Can Improve Business Through Revamped Privacy Landscape Background PDF
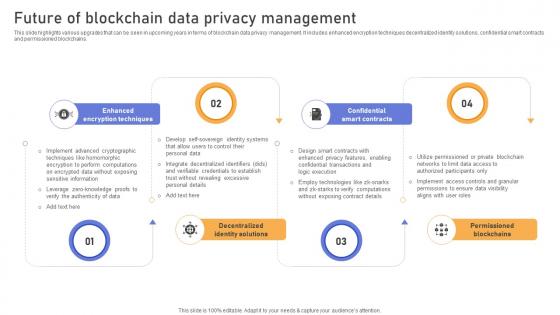
A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V
This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains. Create an editable A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A87 Comprehensive Look At Blockchain Technologys Future Of Blockchain Data Privacy BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights various upgrades that can be seen in upcoming years in terms of blockchain data privacy management. It includes enhanced encryption techniques decentralized identity solutions, confidential smart contracts and permissioned blockchains.
Data Privacy Incident Response Flow Ppt PowerPoint Presentation Slides Images Cpb
Presenting this set of slides with name data privacy incident response flow ppt powerpoint presentation slides images cpb. This is an editable Powerpoint three stages graphic that deals with topics like data privacy incident response flow to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Online Advertising Behavioral Targeting Privacy Ppt PowerPoint Presentation Styles Icons Cpb Pdf
Presenting this set of slides with name online advertising behavioral targeting privacy ppt powerpoint presentation styles icons cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like online advertising behavioral targeting privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Collective Equity Funding Pitch Deck Competitive Landscape Product Comparison Privacy Formats PDF
The slide provides the Competitive landscape of the company on the basis of products features i.e. user friendly, privacy, keyword follow, video bookmarks etc. Deliver and pitch your topic in the best possible manner with this collective equity funding pitch deck competitive landscape product comparison privacy formats pdf. Use them to share invaluable insights on competitive landscape product comparison and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
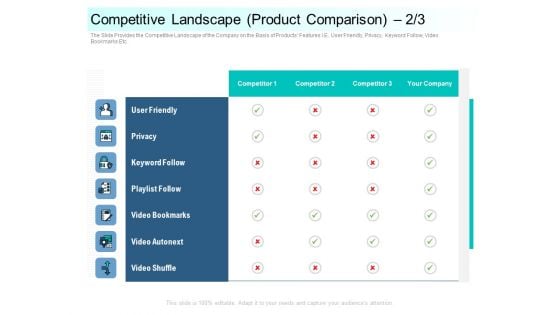
Community Capitalization Pitch Deck Competitive Landscape Product Comparison Privacy Background Pdf
The Slide Provides the Competitive Landscape of the Company on the Basis of Products Features I.E. User Friendly, Privacy, Keyword Follow, Video Bookmarks Etc. Deliver an awe inspiring pitch with this creative community capitalization pitch deck competitive landscape product comparison privacy background pdf bundle. Topics like competitive landscape product comparison can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
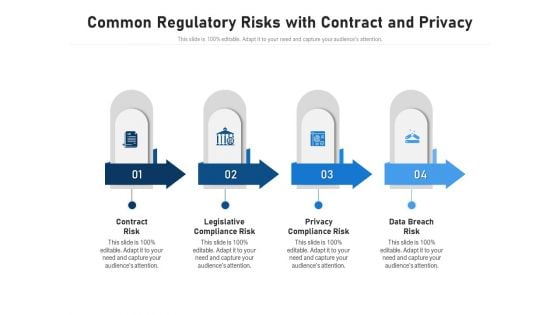
Common Regulatory Risks With Contract And Privacy Ppt PowerPoint Presentation Styles Infographics PDF
Persuade your audience using this common regulatory risks with contract and privacy ppt powerpoint presentation styles infographics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including contract risk, legislative compliance risk, privacy compliance risk, data breach risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Workforce Privacy Claims Vector Icon Ppt PowerPoint Presentation Icon Background Images PDF
Persuade your audience using this business workforce privacy claims vector icon ppt powerpoint presentation icon background images pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including business workforce privacy claims vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Annual Timeline Roadmap Visual For Data Mining Privacy Issues Ppt PowerPoint Presentation Icon Files PDF
Presenting annual timeline roadmap visual for data mining privacy issues ppt powerpoint presentation icon files pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including annual timeline roadmap visual for data mining privacy issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5 Stage Roadmap Visual For Data Mining Privacy Issues Ppt PowerPoint Presentation Icon Outline PDF
Persuade your audience using this 5 stage roadmap visual for data mining privacy issues ppt powerpoint presentation icon outline pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 stage roadmap visual for data mining privacy issues. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
24 Hour Timeframe Slide For Data Mining Privacy Issues Ppt PowerPoint Presentation Gallery Slide Portrait PDF
Persuade your audience using this 24 hour timeframe slide for data mining privacy issues ppt powerpoint presentation gallery slide portrait pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 24 hour timeframe slide for data mining privacy issues. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

8 Steps Infographic Visual For Data Mining Privacy Issues Ppt Powerpoint Presentation File Sample Pdf
Presenting 8 steps infographic visual for data mining privacy issues ppt powerpoint presentation file sample pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including 8 steps infographic visual for data mining privacy issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Optimizing Digital Marketing Strategy Privacy Safe Growth Impact On Digital Marketing Formats PDF
This template covers overview of digital advertising industry approaches towards providing users with more control over their data through durable privacy-safe solutions such as consented first-party data and automation. There are so many reasons you need a Optimizing Digital Marketing Strategy Privacy Safe Growth Impact On Digital Marketing Formats PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
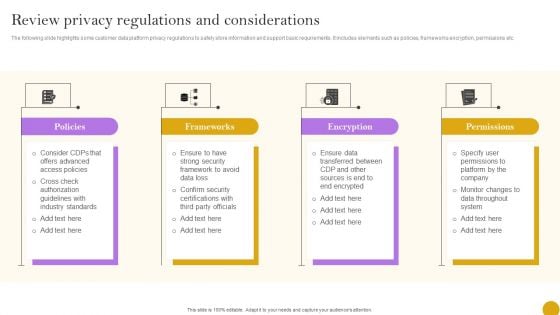
Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Review Privacy Regulations Considerations Ideas PDF
The following slide highlights some customer data platform privacy regulations to safely store information and support basic requirements. It includes elements such as policies, frameworks encryption, permissions etc. There are so many reasons you need a Comprehensive Customer Data Platform Guide Optimizing Promotional Initiatives Review Privacy Regulations Considerations Ideas PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Top Web Application Security Threats Application Security Testing
This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Presenting this PowerPoint presentation, titled Top Web Application Security Threats Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Top Web Application Security Threats Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Top Web Application Security Threats Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc.

Regulations Of Security Tokenization Strategies For Data Security PPT Template
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.
Integrating Data Privacy System Track Record Of Our Company Ppt Gallery Images PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 percent client satisfaction. Are you searching for a Integrating Data Privacy System Storage Limitation Principle Of GDPR Law Ppt Inspiration Aids PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Integrating Data Privacy System Storage Limitation Principle Of GDPR Law Ppt Inspiration Aids PDF from Slidegeeks today.

How Advertisers Can Improve Business Through Revamped Privacy Landscape Diagrams PDF
This slide provides information regarding transformed privacy landscape enabled by Apple and how advertisers can improve their business through such revamping by deploying privacy preservation methodologies, enable transition across advertising models, etc. Slidegeeks is here to make your presentations a breeze with How Advertisers Can Improve Business Through Revamped Privacy Landscape Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Discovering Apples Billion Dollar Branding Secret How Advertisers Can Improve Business Through Revamped Privacy Information PDF
This slide provides information regarding transformed privacy landscape enabled by apple and how advertisers can improve their business through such revamping by deploying privacy preservation methodologies, enable transition across advertising models, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Discovering Apples Billion Dollar Branding Secret How Advertisers Can Improve Business Through Revamped Privacy Information PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Privacy IT Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. This is a information privacy it monitor access to sensitive and regulated data structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitor access to sensitive and regulated data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
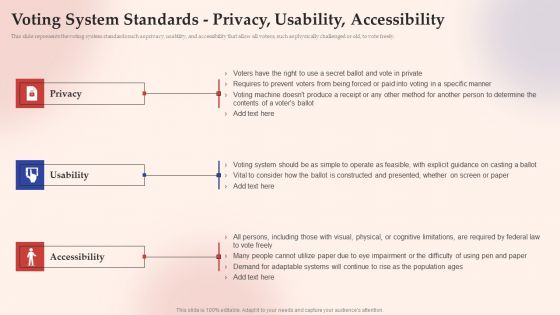
Electronic Voting System Voting System Standards Privacy Usability Accessibility Formats PDF
This slide represents the voting system standards such as privacy, usability, and accessibility that allow all voters, such as physically challenged or old, to vote freely.This is a Electronic Voting System Voting System Standards Privacy Usability Accessibility Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operate Feasible, Constructed Presented, Demand Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Data Privacy System Accuracy Principle Of GDPR Law Ppt Model Graphics Example PDF
This slide depicts the accuracy principle, which emphasizes that you are responsible for all efforts taken to ensure the datas privacy, it must be correct and up to date. Want to ace your presentation in front of a live audience Our Integrating Data Privacy System Accuracy Principle Of GDPR Law Ppt Model Graphics Example PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
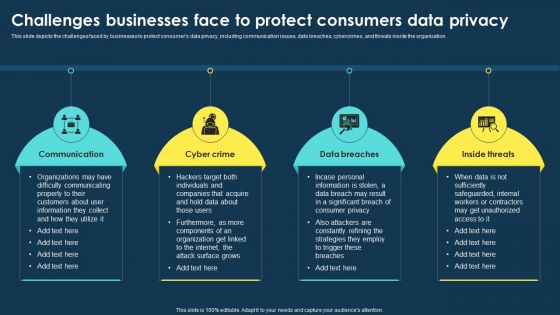
Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
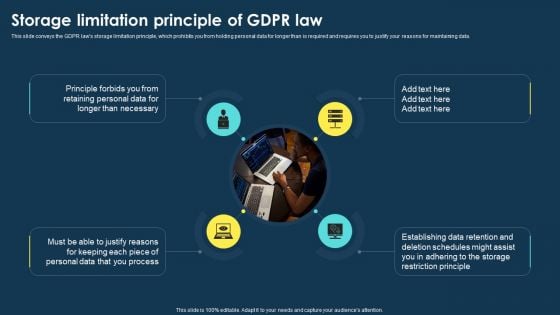
Integrating Data Privacy System Seven Principles Of GDPR Law Ppt Infographics Design Inspiration PDF
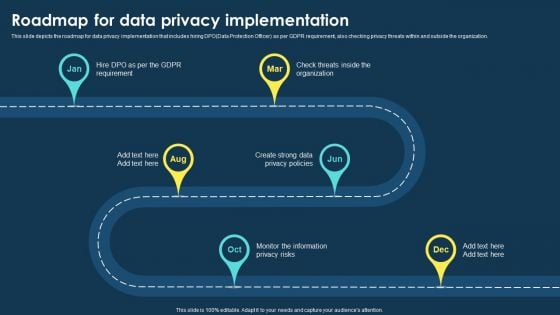
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Integrating Data Privacy System Roadmap For Data Privacy Implementation Ppt Ideas Graphic Images from Slidegeeks and deliver a wonderful presentation.
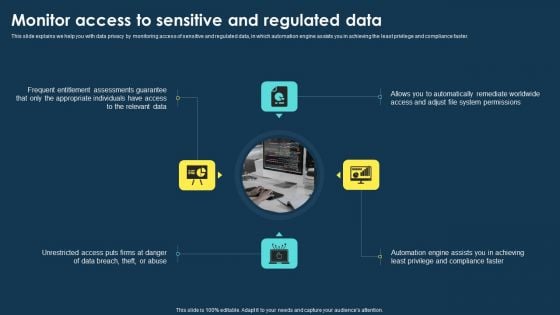
Integrating Data Privacy System Monitor Access To Sensitive And Regulated Data Sample PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. Find a pre-designed and impeccable Integrating Data Privacy System Monitor Access To Sensitive And Regulated Data Sample PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
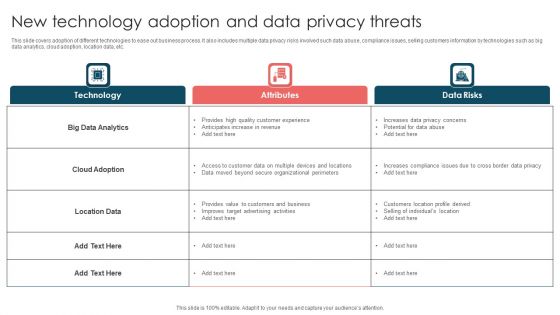
New Technology Adoption And Data Privacy Threats Ppt Pictures Files PDF
This slide covers adoption of different technologies to ease out business process. It also includes multiple data privacy risks involved such data abuse, compliance issues, selling customers information by technologies such as big data analytics, cloud adoption, location data, etc. Showcasing this set of slides titled New Technology Adoption And Data Privacy Threats Ppt Pictures Files PDF. The topics addressed in these templates are Technology, Attributes, Data Risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
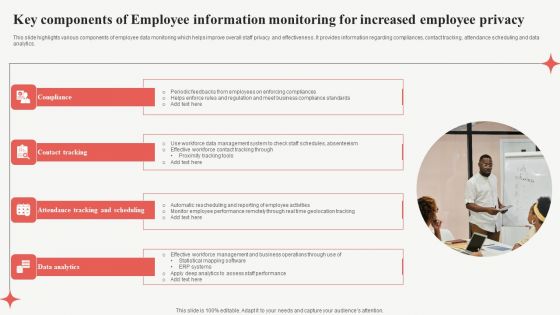
Key Components Of Employee Information Monitoring For Increased Employee Privacy Formats PDF
This slide highlights various components of employee data monitoring which helps improve overall staff privacy and effectiveness. It provides information regarding compliances, contact tracking, attendance scheduling and data analytics. Persuade your audience using this Key Components Of Employee Information Monitoring For Increased Employee Privacy Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analytics, Contact Tracking, Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Optimizing Digital Marketing Strategy One Page Privacy And Performance Summary For Topics PDF
This template covers introduction of the playbook. It summarizes and simplify the changes taking place around consumer privacy and the actions brands can takes to deliver on both customers expectations and brands marketing goals. Want to ace your presentation in front of a live audience Our Optimizing Digital Marketing Strategy One Page Privacy And Performance Summary For Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
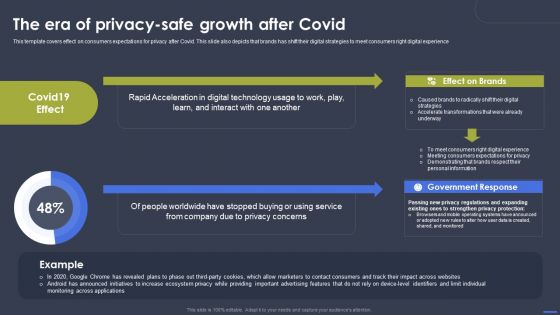
Optimizing Digital Marketing Strategy The Era Of Privacy Safe Growth After Covid Summary PDF
This template covers effect on consumers expectations for privacy after Covid. This slide also depicts that brands has shift their digital strategies to meet consumers right digital experience. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Optimizing Digital Marketing Strategy The Era Of Privacy Safe Growth After Covid Summary PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same.

Control Access To Private Content Ppt PowerPoint Presentation Portfolio Outfit
This is a control access to private content ppt powerpoint presentation portfolio outfit. This is a three stage process. The stages in this process are access rights, access management, business.


 Continue with Email
Continue with Email

 Home
Home


































