lock

Fingerprint Access Control Biometric Solution Ppt PowerPoint Presentation Pictures Format
This is a fingerprint access control biometric solution ppt powerpoint presentation pictures format. This is a two stage process. The stages in this process are access rights, access management, business.
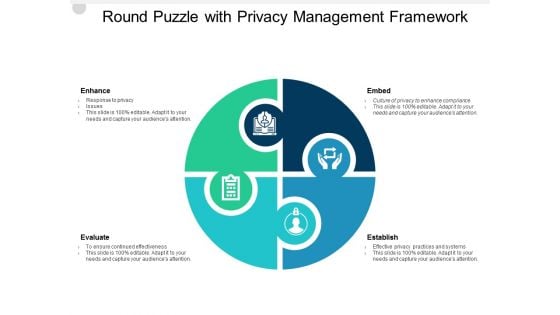
Round Puzzle With Privacy Management Framework Ppt PowerPoint Presentation Pictures Portfolio
Presenting this set of slides with name round puzzle with privacy management framework ppt powerpoint presentation pictures portfolio. This is a four stage process. The stages in this process are process, round puzzle, circle puzzle. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Accessing Metaverse Through Technologies Artificial Intelligence AI Microsoft PDF
This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Boost your pitch with our creative Accessing Metaverse Through Technologies Artificial Intelligence AI Microsoft PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.
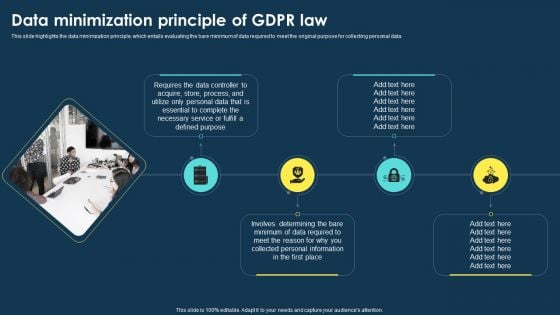
Integrating Data Privacy System Data Minimization Principle Of GDPR Law Ppt File Summary PDF
This slide highlights the data minimization principle, which entails evaluating the bare minimum of data required to meet the original purpose for collecting personal data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Integrating Data Privacy System Data Minimization Principle Of GDPR Law Ppt File Summary PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Integrating Data Privacy System Data Minimization Principle Of GDPR Law Ppt File Summary PDF today and make your presentation stand out from the rest.
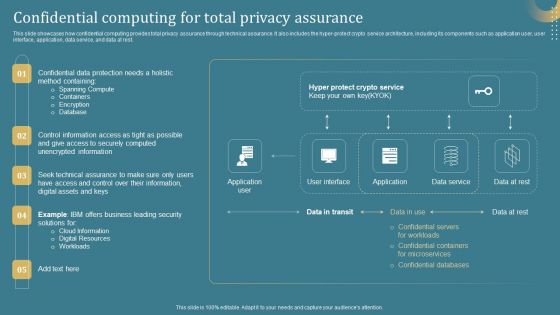
Confidential Computing System Technology Confidential Computing For Total Privacy Assurance Graphics PDF
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. This modern and well-arranged Confidential Computing System Technology Confidential Computing For Total Privacy Assurance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Integrating Data Privacy System Adhere To Strict Compliance Requirements Ppt Summary Slides PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material, also, compliance standards serve as a foundation. There are so many reasons you need a Integrating Data Privacy System Adhere To Strict Compliance Requirements Ppt Summary Slides PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Internet Protocol Security PPT Example

Network Security Model PPT Example
Big Data Monitoring Security Icon Download pdf
Pitch your topic with ease and precision using this Big Data Monitoring Security Icon Download pdf. This layout presents information on Big Data Monitoring, Security Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Big Data Monitoring Security Icon Download pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.
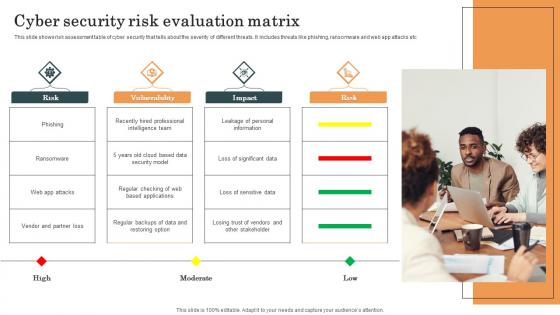
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.

Information Privacy IT Data Minimization Principle Of Gdpr Law Graphics PDF
This slide highlights the data minimization principle, which entails evaluating the bare minimum of data required to meet the original purpose for collecting personal data. Presenting information privacy it data minimization principle of gdpr law graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data minimization principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
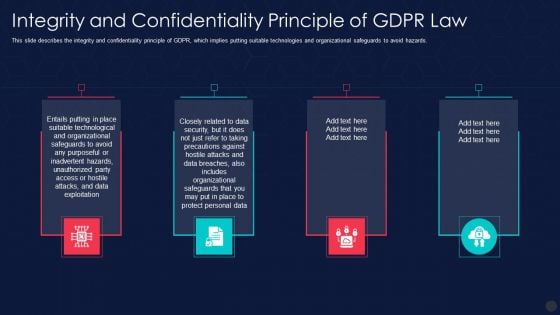
Information Privacy IT Integrity And Confidentiality Principle Of Gdpr Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. This is a information privacy it integrity and confidentiality principle of gdpr law structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity and confidentiality principle of gdpr law. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Data Privacy System Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Take your projects to the next level with our ultimate collection of Integrating Data Privacy System Integrity And Confidentiality Principle Of GDPR Law Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
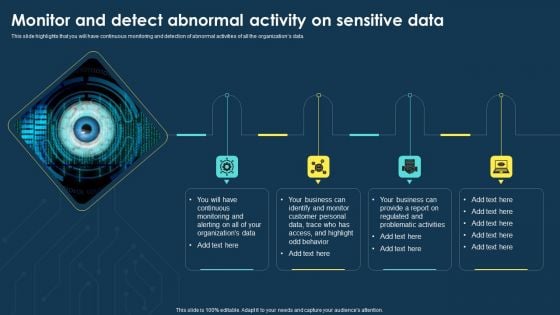
Integrating Data Privacy System Monitor And Detect Abnormal Activity On Sensitive Data Microsoft PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Boost your pitch with our creative Integrating Data Privacy System Monitor And Detect Abnormal Activity On Sensitive Data Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Are you searching for a Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks today. The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc.
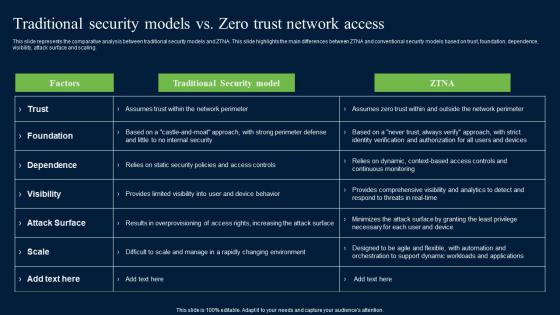
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
Agenda For Secure Computing Framework Portrait Pdf
Create an editable Agenda For Secure Computing Framework Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Secure Computing Framework Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Secure Computing Framework Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today. This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.
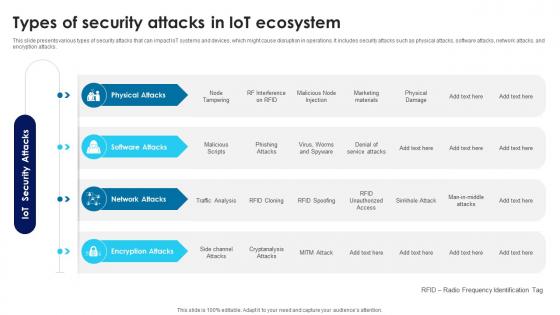
Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks.
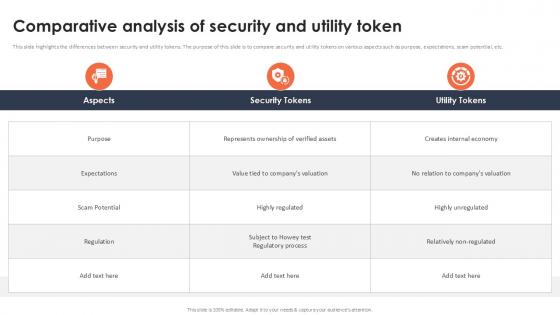
Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.
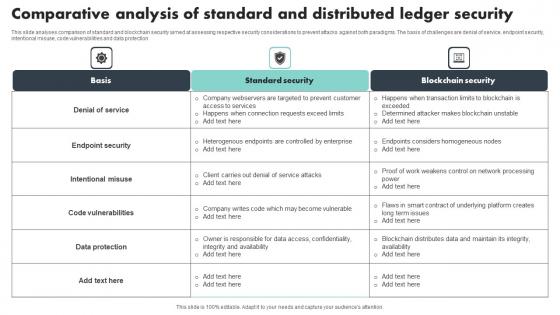
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection

Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.

Integrating Data Privacy System Accountability Principle Of GDPR Law Ppt Gallery Files PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrating Data Privacy System Accountability Principle Of GDPR Law Ppt Gallery Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Integrating Data Privacy System Storage Limitation Principle Of GDPR Law Ppt Inspiration Aids PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. The Integrating Data Privacy System Seven Principles Of GDPR Law Ppt Infographics Design Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Integrating Data Privacy System Lawfulness Fairness And Transparency Principle Graphics PDF
This slide shows the lawfulness, fairness, and transparency concept, which establishes explanations for data processing and includes six legitimate basis for personal data. Do you know about Slidesgeeks Integrating Data Privacy System Lawfulness Fairness And Transparency Principle Graphics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Gantt Chart For Cloud Security Firewall Proposal
Power up your presentations with our Gantt Chart For Cloud Security Firewall Proposal single-slide PPT template. Our visually-stunning template will help you deliver your message with confidence. With easy-to-use editing options and fully customizable features, you can create polished and captivating presentations in no time. Say goodbye to boring slides and hello to impactful presentations with our top-quality template. Download now and get ready to wow your audience. singles Our Gantt Chart For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V
This slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN. Explore a selection of the finest Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Building Trust With IoT Security IoT Communication Protocol Security Concerns With Mitigation IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN.
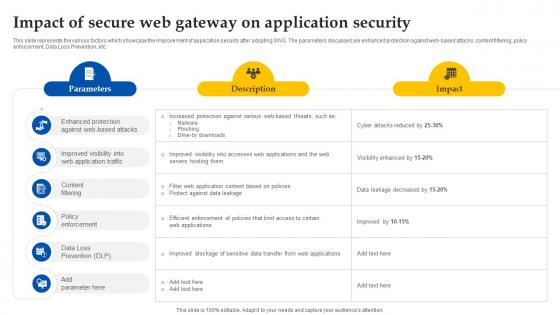
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.
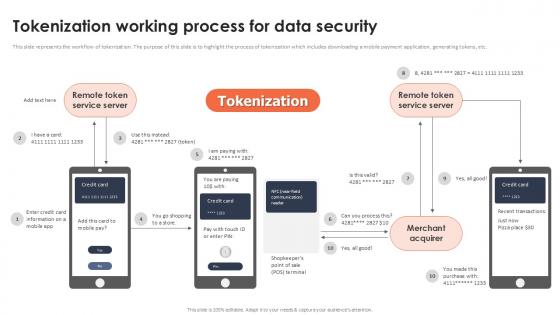
Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
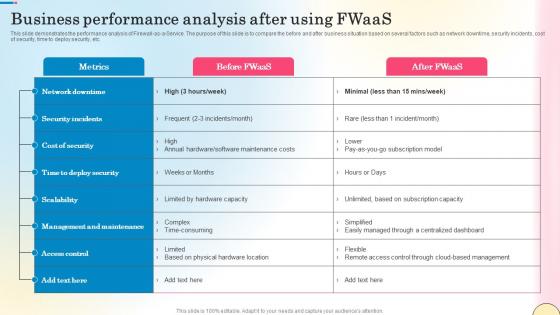
Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc.
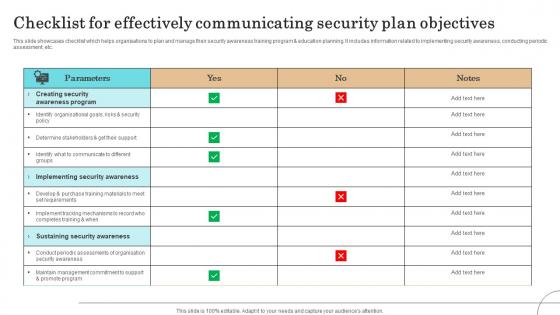
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.
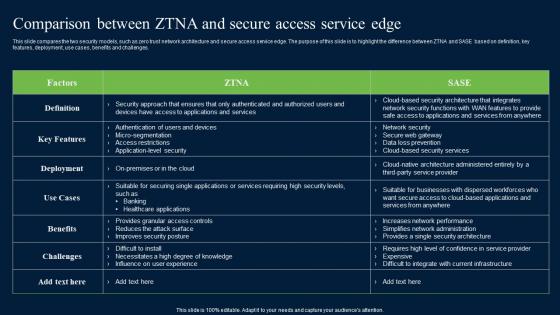
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
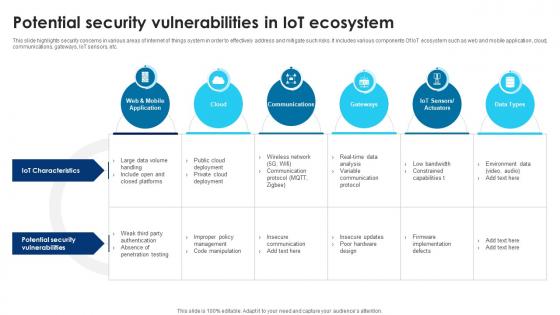
Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V
This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
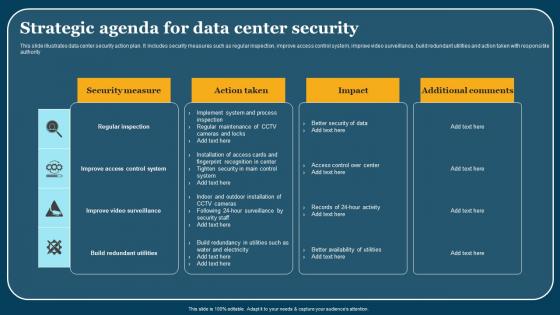
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.
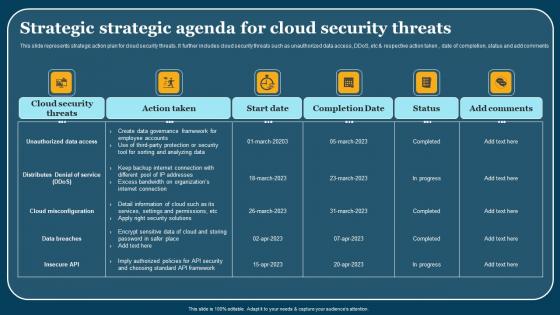
Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf
This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments. Showcasing this set of slides titled Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf. The topics addressed in these templates are Cloud Security Threats, Action Taken, Start Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments.

Checklist To Implement Secure Web Gateway Web Threat Protection System
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Get a simple yet stunning designed Checklist To Implement Secure Web Gateway Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Secure Web Gateway Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Data Security In Cloud Computing Ppt Presentation

Cloud Security Implementation Strategy Ppt Template

Cloud Security Implementation Strategy Ppt Presentation

Mobile Application Security Testing PPT Sample

Cloud Native Application Security PPT Template

Implementing Authentication In Application Security PPT Example
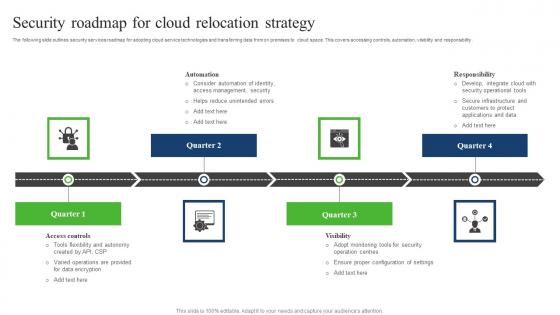
Security Roadmap For Cloud Relocation Strategy Sample Pdf
The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility. Showcasing this set of slides titled Security Roadmap For Cloud Relocation Strategy Sample Pdf. The topics addressed in these templates are Responsibility, Automation, Security Roadmap, Cloud Relocation Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
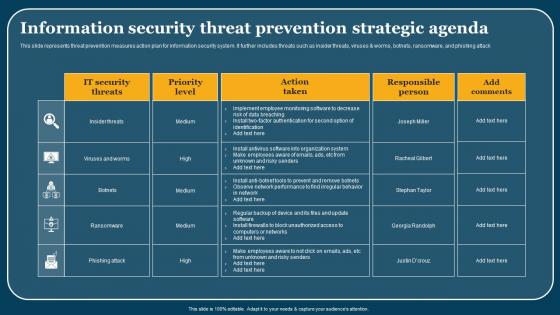
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
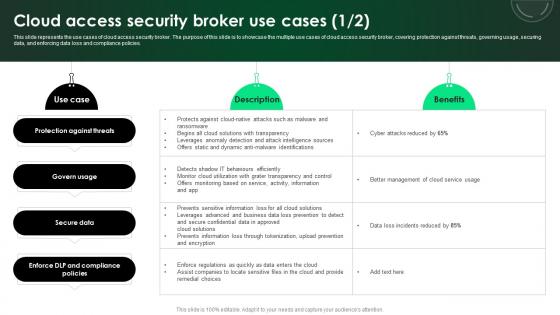
CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.
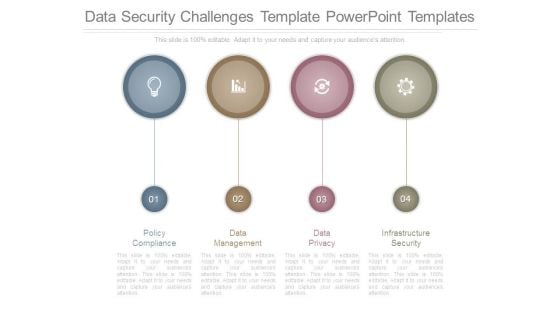
Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.
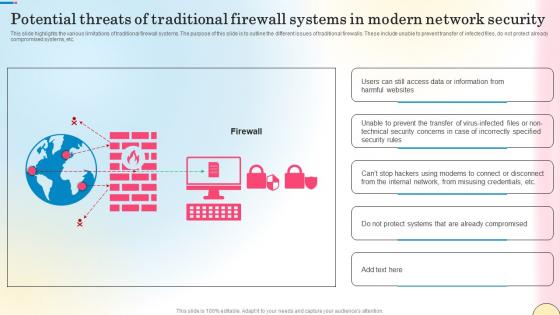
Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf
This slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Create an editable Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.

Improving Security By Green Computing Technology Eco Friendly Computing IT
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.Are you searching for a Improving Security By Green Computing Technology Eco Friendly Computing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Improving Security By Green Computing Technology Eco Friendly Computing IT from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.


 Continue with Email
Continue with Email

 Home
Home


































