Collateral Management
Role Of Security In Open RAN Standards Unlocking The Potential Of Open RAN Information Pdf
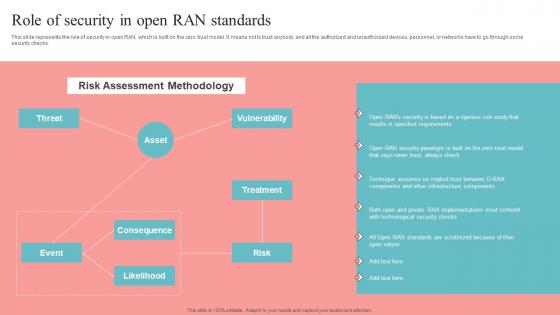
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open RAN Standards Unlocking The Potential Of Open RAN Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks.

Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf
Slidegeeks is here to make your presentations a breeze with Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Tableau Business Intelligence Tool Salesforce Business Profile Diagrams PDF
This slide highlights the salesforce analytics software reports and dashboards which showcases the dashboard that includes chart, table, gauge with real-time reporting, and security controls. Deliver an awe inspiring pitch with this creative Tableau Business Intelligence Tool Salesforce Business Profile Diagrams PDF bundle. Topics like Server Management, Embedded Analytics, Security Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc.

IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.
Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
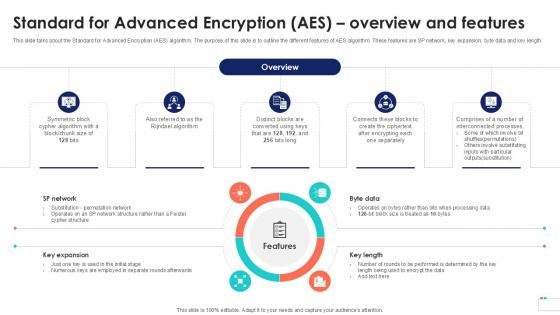
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
Internet Security Defense Maturity Evaluation Strategy Information Pdf
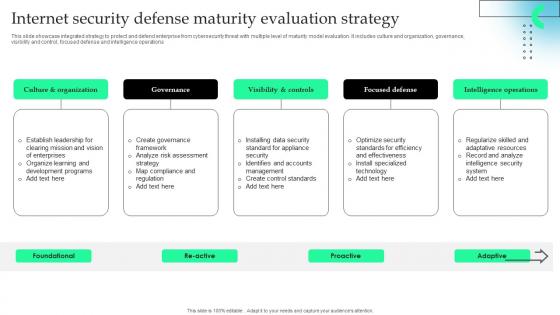
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.

Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Cybersecurity Challenges Comprehensive Guide To Blockchain Digital Security Demonstration Pdf The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc.
Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation
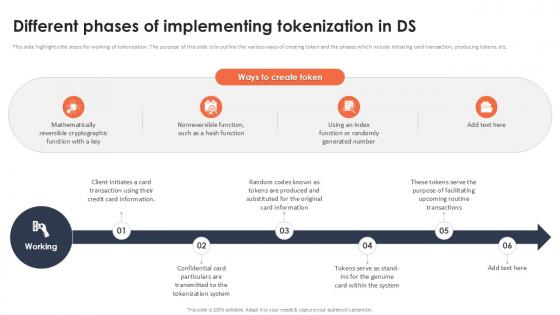
This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc.
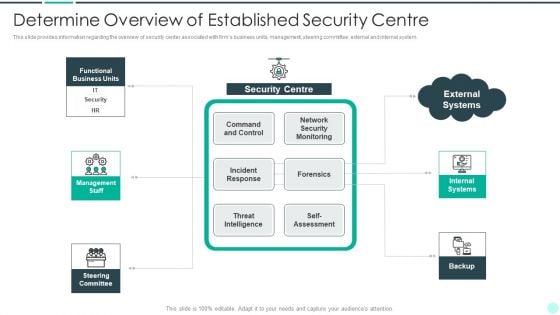
Executing Advance Data Analytics At Workspace Determine Overview Of Established Topics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace determine overview of established topics pdf bundle. Topics like determine overview of established security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
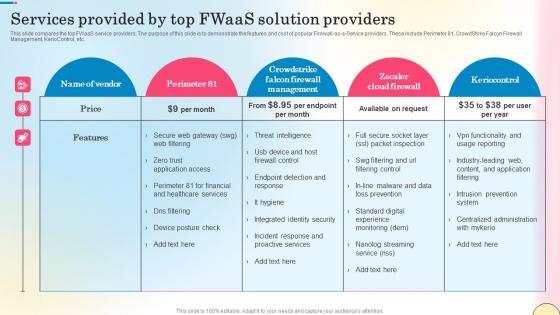
Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf
This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc.

Business Development Team Case Study 2 Internet Security Organization SA SS V
This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Development Team Case Study 2 Internet Security Organization SA SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue.
Agenda Of SIEM Services Ppt Templates PDF
This is a agenda of siem services ppt templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, services, customers, security intelligence, management, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
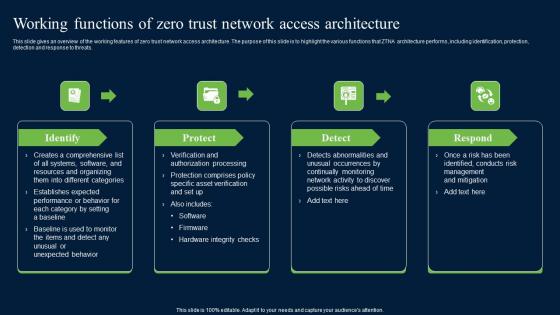
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
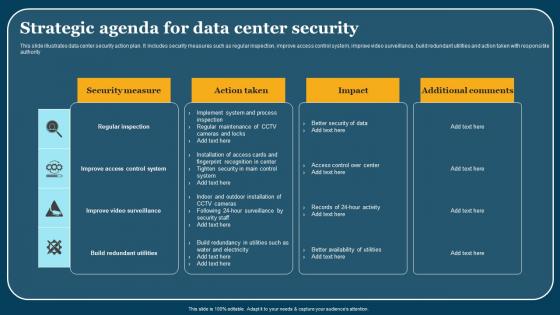
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.

Intelligent Infrastructure Capabilities For Digital Business Table Of Contents Introduction PDF
Presenting Intelligent Infrastructure Capabilities For Digital Business Table Of Contents Introduction PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Improved Security Standards, Facilities Offered, Timeframe for Incident Management, Security Centre. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
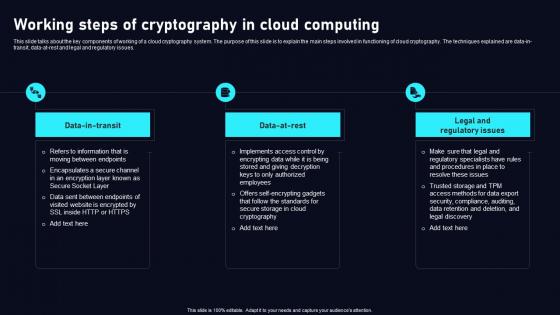
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
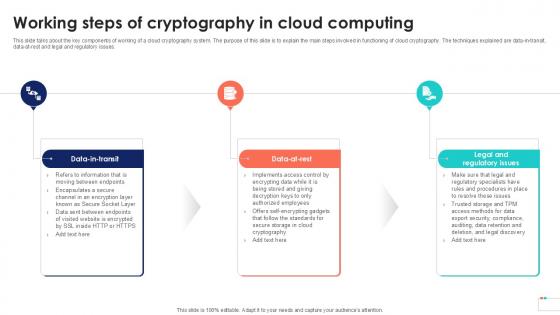
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.
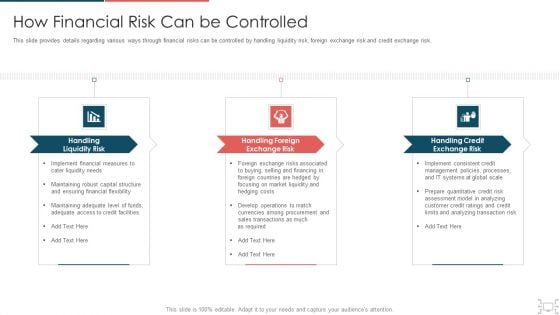
cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
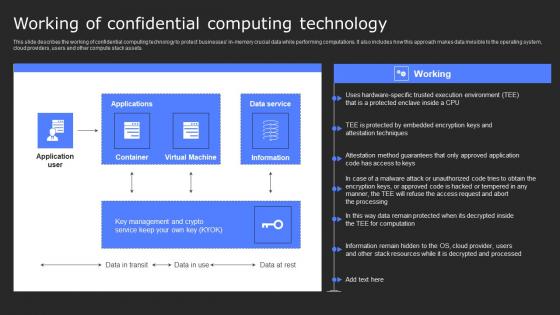
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
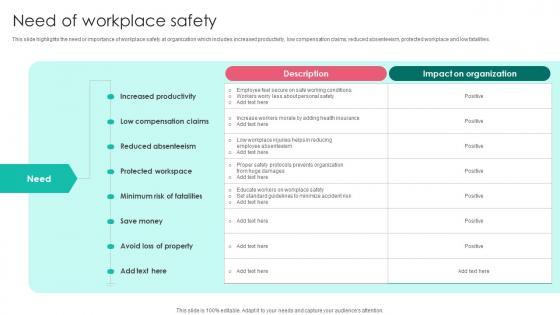
Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Retrieve professionally designed Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities.
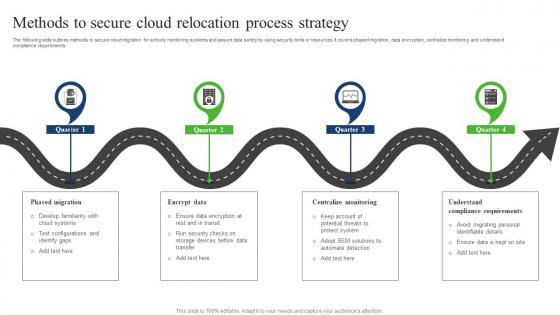
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
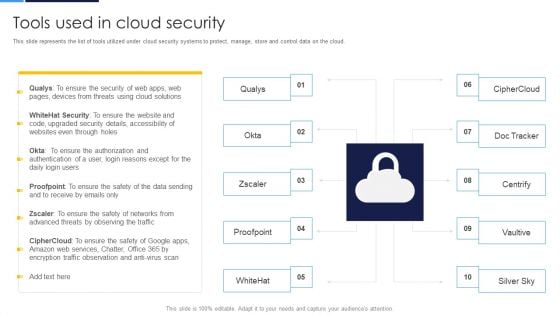
Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
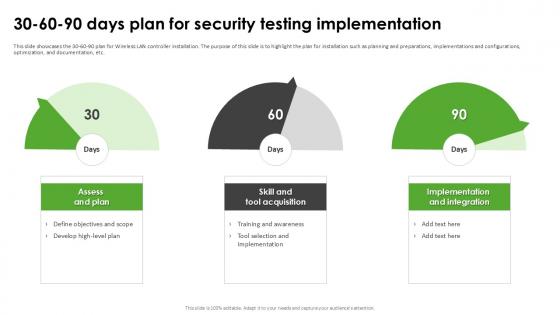
30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample
This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate 30 60 90 Days Plan For Security Harnessing The World Of Ethical Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc.

Automated Government Procedures E Governance Workstream Strategies Introduction PDF
Here we are covering the e-governance strategies which is enable everyone to use effective government services, in a secure, integrated and easy way through multiple electronic channels. Deliver an awe-inspiring pitch with this creative automated government procedures e governance workstream strategies introduction pdf bundle. Topics like infrastructure, institutional framework, change management, human capital, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.

Non Rural Water Resource Administration Post It Notes Summary PDF
This is a non rural water resource administration post it notes summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, financing, technical, securities, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Password Protected Security Control System Ppt PowerPoint Presentation Styles Ideas PDF
Persuade your audience using this password protected security control system ppt powerpoint presentation styles ideas pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including password protected security control system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
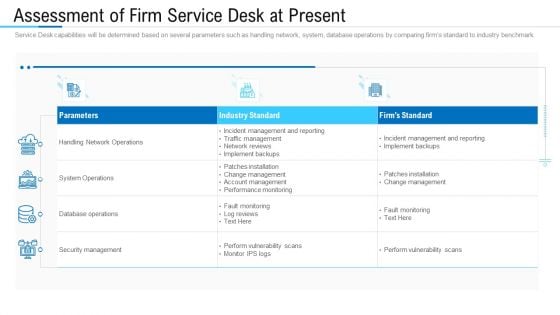
Information Technology Facility Flow Administration Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration assessment of firm service desk at present brochure pdf. Use them to share invaluable insights on network operations, security management, database operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Enhanced Protection Corporate Event Administration Essential Roles And Responsibilities Involved In Secops Guidelines PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration essential roles and responsibilities involved in secops guidelines pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.
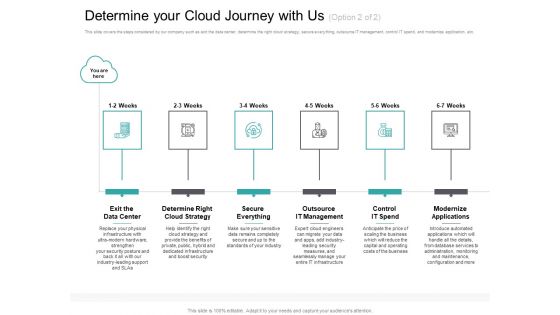
Cloud Based Marketing Determine Your Cloud Journey With Us Strategy Ppt PowerPoint Presentation Layouts Graphics Design PDF
This slide covers the steps considered by our company such as exit the data center, determine the right cloud strategy, secure everything, outsource IT management, control IT spend, and modernize application, etc. Presenting cloud based marketing determine your cloud journey with us strategy ppt powerpoint presentation layouts graphics design pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like exit data center, determine right, cloud strategy, secure everything, outsource it management, control it spend, modernize applications. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
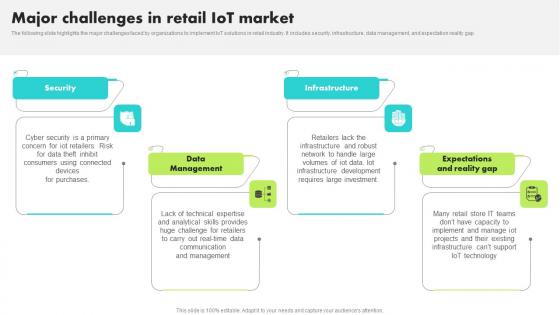
Major Challenges In Retail IoT Market Guide For Retail IoT Solutions Analysis Download Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Challenges In Retail IoT Market Guide For Retail IoT Solutions Analysis Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap
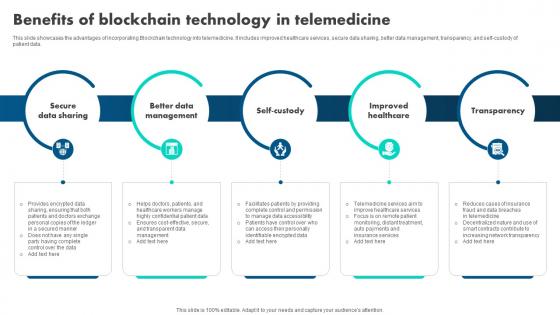
How Blockchain Is Reshaping Benefits Of Blockchain Technology In Telemedicine BCT SS V
This slide showcases the advantages of incorporating Blockchain technology into telemedicine. It includes improved healthcare services, secure data sharing, better data management, transparency, and self-custody of patient data. Present like a pro with How Blockchain Is Reshaping Benefits Of Blockchain Technology In Telemedicine BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the advantages of incorporating Blockchain technology into telemedicine. It includes improved healthcare services, secure data sharing, better data management, transparency, and self-custody of patient data.
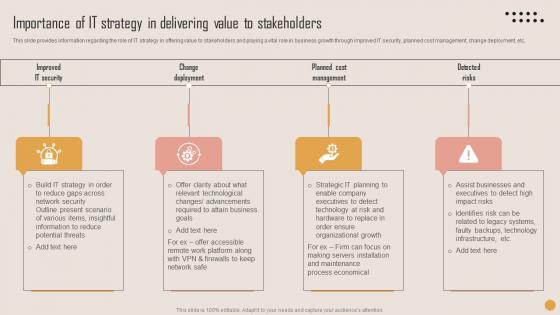
Importance Of IT Strategy Delivering Playbook For Strategic Actions To Improve IT Performance Mockup Pdf
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. This modern and well arranged Importance Of IT Strategy Delivering Playbook For Strategic Actions To Improve IT Performance Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc.
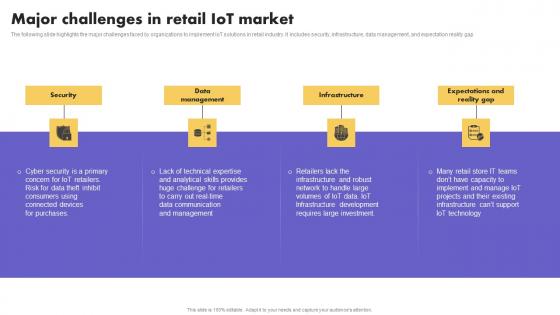
IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap
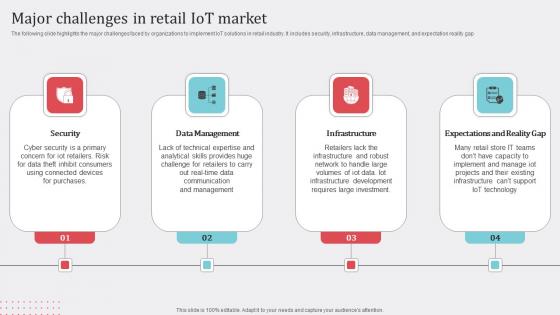
Major Challenges In Retail How Industrial IoT Is Changing Worldwide Slides Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap Welcome to our selection of the Major Challenges In Retail How Industrial IoT Is Changing Worldwide Slides Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap
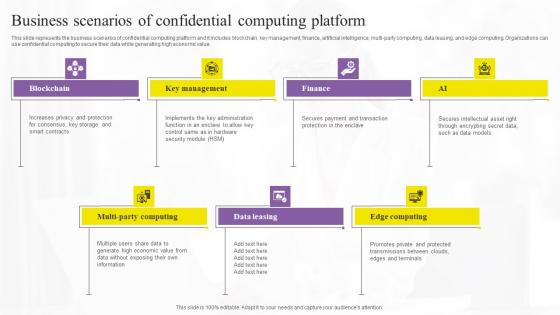
Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
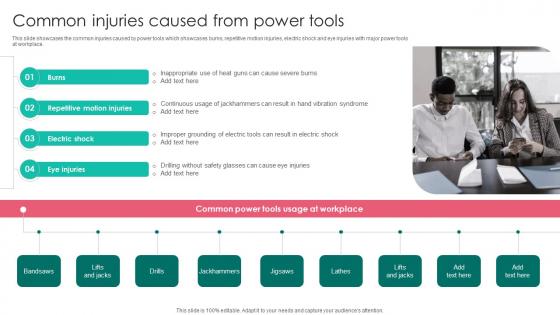
Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf
This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace.
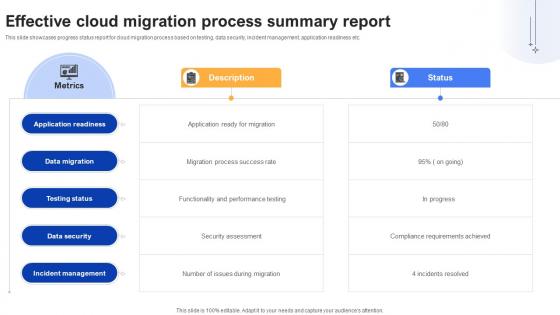
Effective Data Migration Effective Cloud Migration Process Summary Report
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Data Migration Effective Cloud Migration Process Summary Report and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
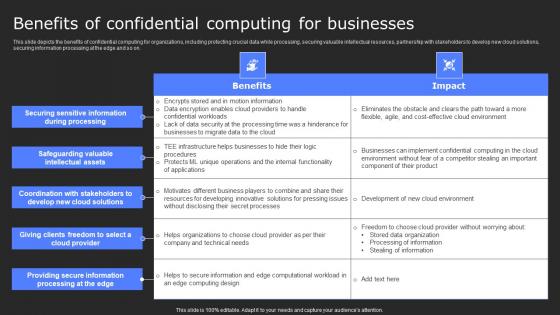
Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
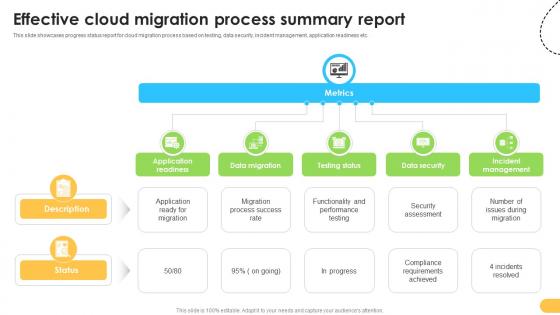
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc.
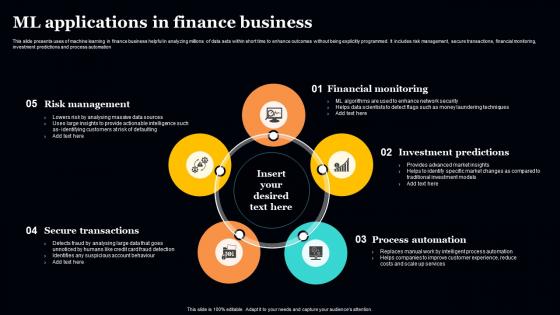
ML Applications In Finance Business Background Pdf
This slide presents uses of machine learning in finance business helpful in analyzing millions of data sets within short time to enhance outcomes without being explicitly programmed. It includes risk management, secure transactions, financial monitoring, investment predictions and process automation. Showcasing this set of slides titled ML Applications In Finance Business Background Pdf. The topics addressed in these templates are Financial Monitoring, Investment Predictions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents uses of machine learning in finance business helpful in analyzing millions of data sets within short time to enhance outcomes without being explicitly programmed. It includes risk management, secure transactions, financial monitoring, investment predictions and process automation.
Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf
This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity. Are you searching for a Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf from Slidegeeks today. This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity.
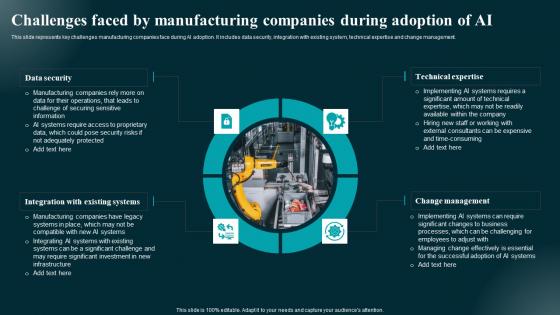
Challenges Faced By Manufacturing Companies Applications And Impact Themes Pdf
This slide represents key challenges manufacturing companies face during AI adoption. It includes data security, integration with existing system, technical expertise and change management. The Challenges Faced By Manufacturing Companies Applications And Impact Themes Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents key challenges manufacturing companies face during AI adoption. It includes data security, integration with existing system, technical expertise and change management.
Mitigation Solutions For Healthcare Deploying IoT Solutions For Enhanced Healthcare Icons Pdf
Following slide exhibits solutions that helps to solve issues faced due to implementation of intent of things in medical industry. It includes pointers such as data security, protocol integration and data management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Mitigation Solutions For Healthcare Deploying IoT Solutions For Enhanced Healthcare Icons Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates Following slide exhibits solutions that helps to solve issues faced due to implementation of intent of things in medical industry. It includes pointers such as data security, protocol integration and data management.
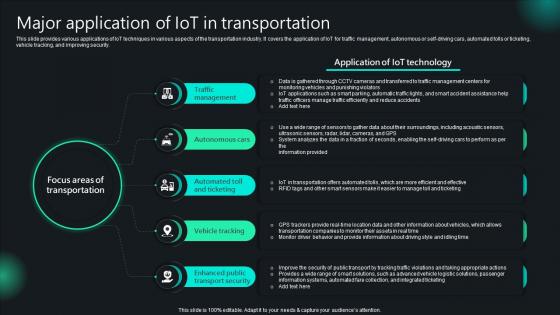
Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V
This slide provides various applications of IoT techniques in various aspects of the transportation industry. It covers the application of IoT for traffic management, autonomous or self-driving cars, automated tolls or ticketing, vehicle tracking, and improving security. Create an editable Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides various applications of IoT techniques in various aspects of the transportation industry. It covers the application of IoT for traffic management, autonomous or self-driving cars, automated tolls or ticketing, vehicle tracking, and improving security.
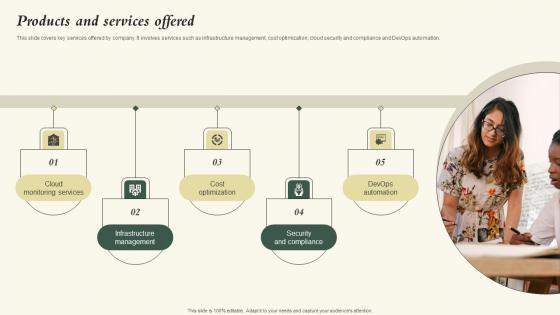
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.

Categories Of Issues And Risks In Cloud Computing PPT Slide SS
This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Categories Of Issues And Risks In Cloud Computing PPT Slide SS to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance.
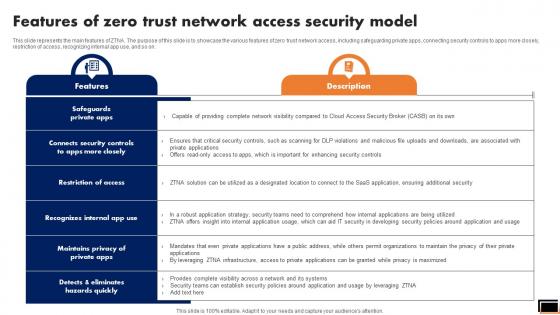
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Implementing Robust Cybersecurity Measures To Safeguard Organizational Data DT SS V
This slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence.Boost your pitch with our creative Implementing Robust Cybersecurity Measures To Safeguard Organizational Data DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence.

Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal
This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.Take your presentations to the next level with our Our Process For Migrating Firewall Network Security Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. This slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc.
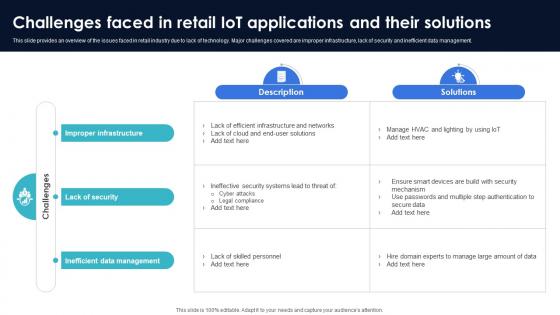
Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V
This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management. Make sure to capture your audiences attention in your business displays with our gratis customizable Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management.


 Continue with Email
Continue with Email

 Home
Home


































