Collateral Management
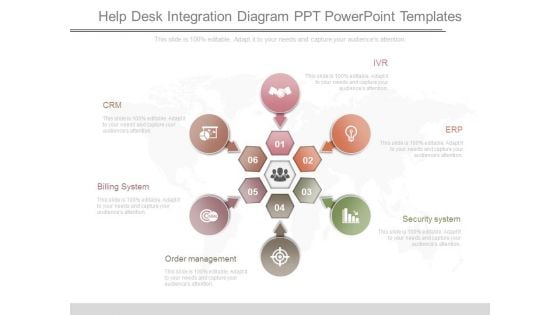
Help Desk Integration Diagram Ppt Powerpoint Templates
This is a help desk integration diagram ppt powerpoint templates. This is a six stage process. The stages in this process are crm, billing system, order management, ivr, erp, security system.

Methods Of Software Risk Assessment Ppt Powerpoint Guide
This is a methods of software risk assessment ppt powerpoint guide. This is a seven stage process. The stages in this process are risk management, risk assessment, risk identification, risk periodization, security requirements, external review, penetration testing.

Components Of Enterprise Architecture Diagram Presentation Diagrams
This is a components of enterprise architecture diagram presentation diagrams. This is a four stage process. The stages in this process are risk and security, program management, technology driven, business driven.
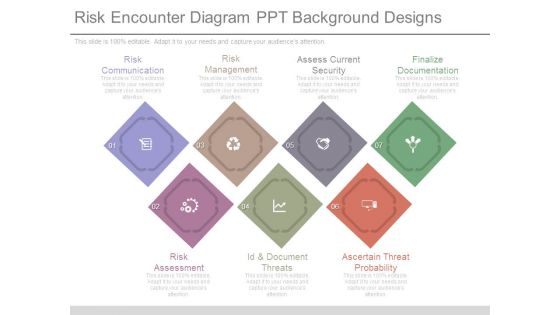
Risk Encounter Diagram Ppt Background Designs
This is a risk encounter diagram ppt background designs. This is a seven stage process. The stages in this process are risk communication, risk management, assess current security, finalize documentation, risk assessment, id and document threats, ascertain threat probability.

Applications Of RFID In Manufacturing Industry Summary PDF
This slide covers applications of RFID in manufacturing industry. It involves plant security, inventory management, quality control and equipment optimisation. Presenting Applications Of RFID In Manufacturing Industry Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Plant Security, Inventory Management, Quality Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure Code, Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
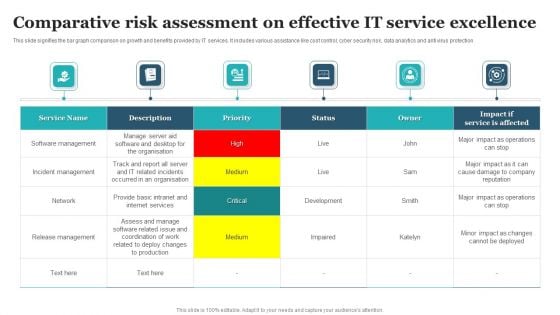
Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
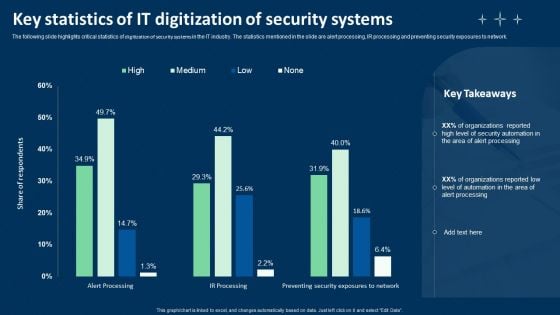
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Checklist Access Control Cloud Computing Security IT Ppt Show PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Deliver and pitch your topic in the best possible manner with this cloud security checklist access control cloud computing security it ppt show pdf. Use them to share invaluable insights on cloud services, security, privileged credentials, administrative and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
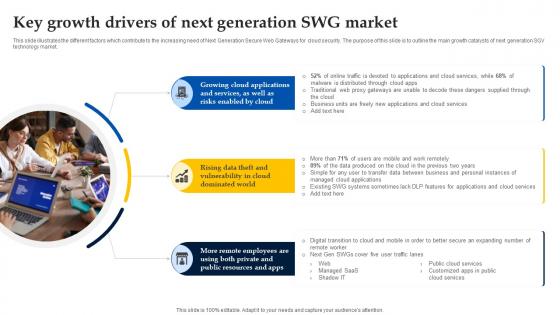
Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Presenting this PowerPoint presentation, titled Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
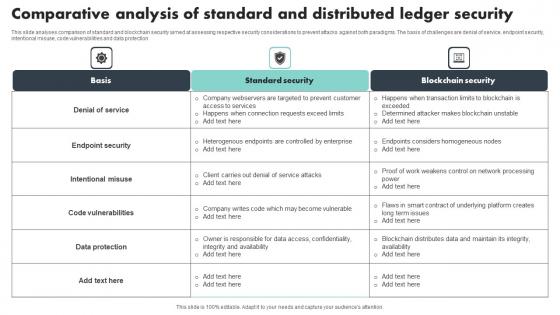
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection

Comparison Between ITIL V2 And ITIL V3 Ppt Outline Microsoft PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions. Deliver an awe inspiring pitch with this creative comparison between itil v2 and itil v3 ppt outline microsoft pdf bundle. Topics like product, process, management, security, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
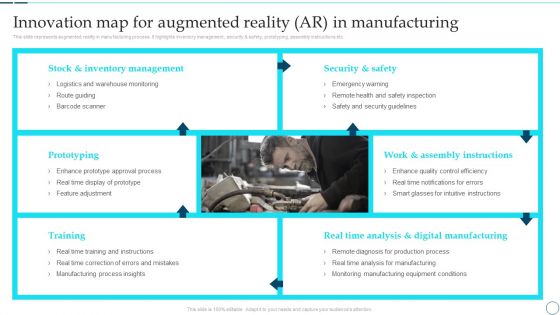
Deployment Of Smart Factory Solutions Innovation Map For Augmented Reality AR In Manufacturing Summary PDF
This slide represents augmented reality in manufacturing process. It highlights inventory management, security and safety, prototyping, assembly instructions etc. Deliver an awe inspiring pitch with this creative Deployment Of Smart Factory Solutions Innovation Map For Augmented Reality AR In Manufacturing Summary PDF bundle. Topics like Prototyping, Inventory Management, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
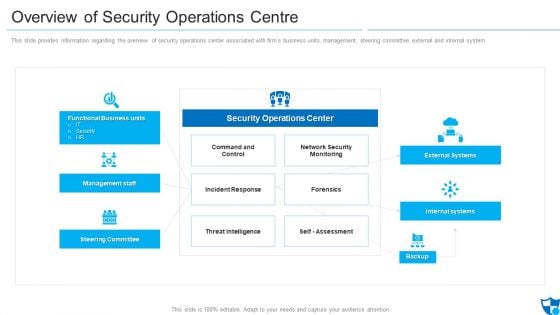
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
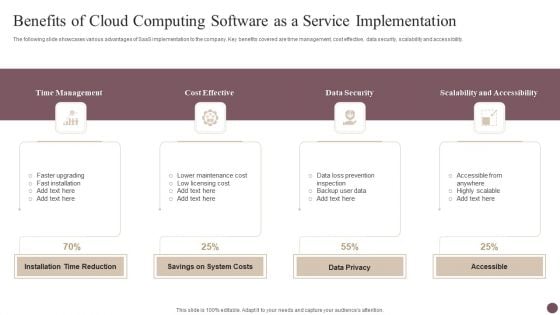
Benefits Of Cloud Computing Software As A Service Implementation Slides PDF
The following slide showcases various advantages of SaaS implementation to the company. Key benefits covered are time management, cost effective, data security, scalability and accessibility. Presenting Benefits Of Cloud Computing Software As A Service Implementation Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Time Management, Cost Effective, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF
This slide covers multiple layers of architectural system based on IoT blockchain platforms. It includes layers such as application, connectivity, IoT physical layers and service layers comprising of device management, data visualization, big data analytics, consensus management, distributed ledger, smart contracts, API interface, message broker, security management, etc. Showcasing this set of slides titled Layer Based Integrate IOT Blockchain Platform Architecture Microsoft PDF. The topics addressed in these templates are Application Layer, Connectivity Layers, IOT Physical Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
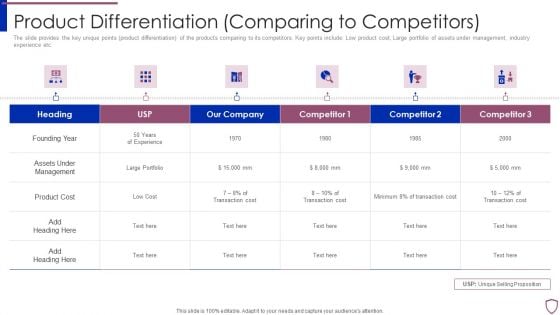
Financing Catalogue For Security Underwriting Agreement Product Differentiation Comparing Professional PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include Low product cost, Large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement product differentiation comparing professional pdf. Use them to share invaluable insights on founding year, assets under management, product cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Information Security Program Values To Business Background PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a data safety initiatives information security program values to business background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detection and response, attack surface management, current network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
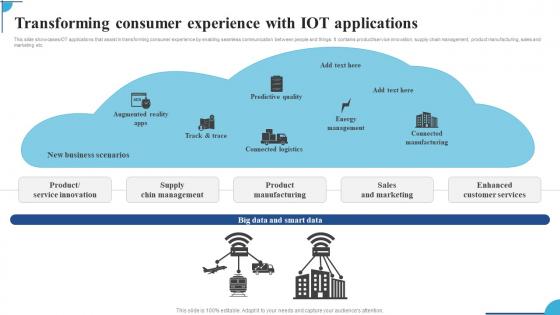
Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf
This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc. Showcasing this set of slides titled Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf. The topics addressed in these templates are Supply Chin Management,Product Manufacturing,Sales And Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color,background,font etc. as per your unique business setting. This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc.

Client Testimonials Manufacturing Control Software Company Investor PPT Presentation
This slide caters to the details related to the clients feedback based on their experiences. It consists of information about a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Create an editable Client Testimonials Manufacturing Control Software Company Investor PPT Presentation that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Client Testimonials Manufacturing Control Software Company Investor PPT Presentation is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide caters to the details related to the clients feedback based on their experiences. It consists of information about a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.
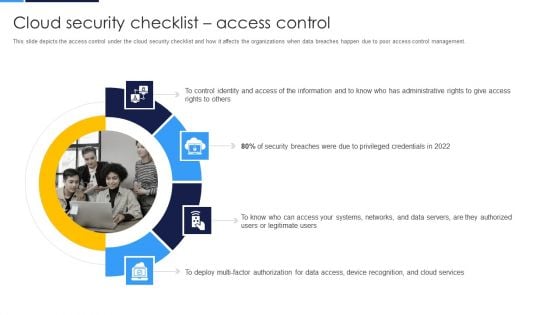
Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.This is a Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Administrative Rights, Privileged Credentials, Legitimate Users You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Impact Of Application Security On Organization Application Security Testing
This slide showcases the after application security impact on business along with factors that have improved the overall performance. Slidegeeks has constructed Major Impact Of Application Security On Organization Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the after application security impact on business along with factors that have improved the overall performance.
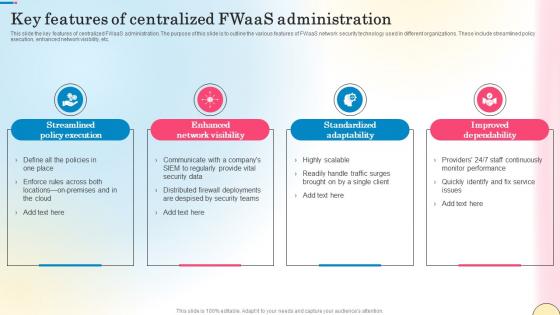
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc.
Food Security Checklist To Fulfill Customer Standards Icons Pdf
Following slide shows the food safety check list to satisfy consumer requirements which will assist in measuring quality standards of food. It includes such as food preparation safety, contamination and frozen food. Showcasing this set of slides titled Food Security Checklist To Fulfill Customer Standards Icons Pdf. The topics addressed in these templates are Parameter, Inspected, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the food safety check list to satisfy consumer requirements which will assist in measuring quality standards of food. It includes such as food preparation safety, contamination and frozen food.
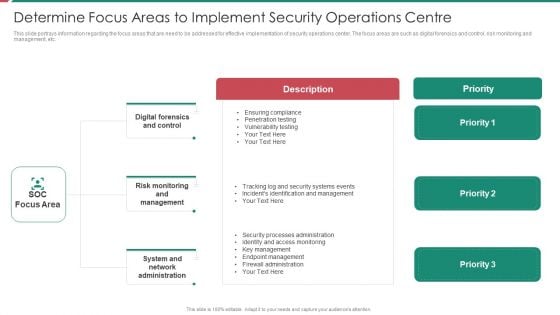
Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
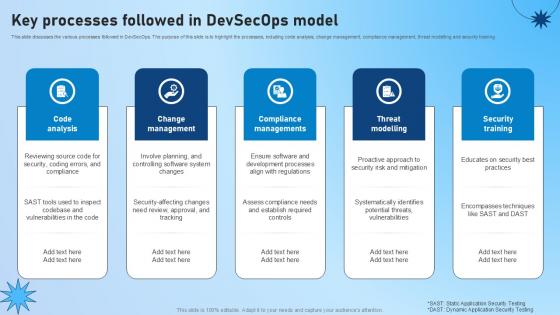
Key Processes Followed In Devsecops Model Role Of Devsecops Ppt Powerpoint
This slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training. Boost your pitch with our creative Key Processes Followed In Devsecops Model Role Of Devsecops Ppt Powerpoint Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training.
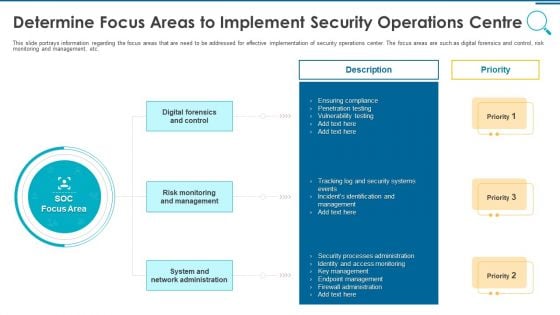
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
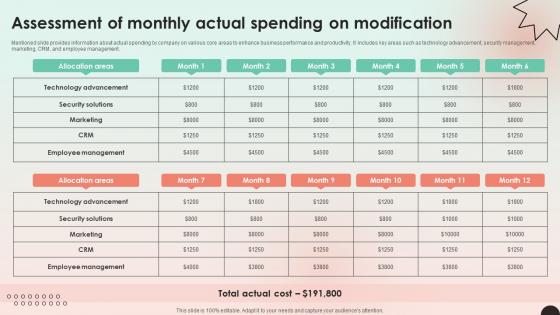
Web Consulting Business Assessment Of Monthly Actual Spending On Modification
Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management. Present like a pro with Web Consulting Business Assessment Of Monthly Actual Spending On Modification. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management.

Ensuring Erp Data Security And Compliance Erp And Digital Transformation For Maximizing DT SS V
This slide presents various strategies to ensure data security and compliance issues. It includes robust access controls, data encryption, compliance with regulations, data backup and recovery, and employee training on security.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Ensuring Erp Data Security And Compliance Erp And Digital Transformation For Maximizing DT SS V from Slidegeeks and deliver a wonderful presentation. This slide presents various strategies to ensure data security and compliance issues. It includes robust access controls, data encryption, compliance with regulations, data backup and recovery, and employee training on security.

Web Consulting Business Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. The Web Consulting Business Estimated Annual Budget Plan For Web Company is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management.

Wireless Banking To Improve Popular Mobile Banking Apps Available In Market Fin SS V
This slide shows details about best mobile banking apps based on different types of features such as customer service, security, money management, account management, etc. which can be used by customers while selecting banking apps. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Wireless Banking To Improve Popular Mobile Banking Apps Available In Market Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows details about best mobile banking apps based on different types of features such as customer service, security, money management, account management, etc. which can be used by customers while selecting banking apps.
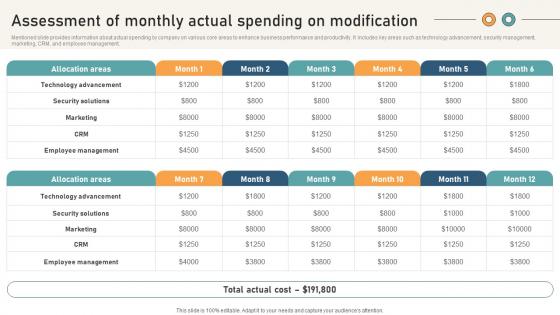
Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification
Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management. Get a simple yet stunning designed Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Guide For Website Assessment Of Monthly Actual Spending On Modification can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Mentioned slide provides information about actual spending by company on various core areas to enhance business performance and productivity. It includes key areas such as technology advancement, security management, marketing, CRM, and employee management.

Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
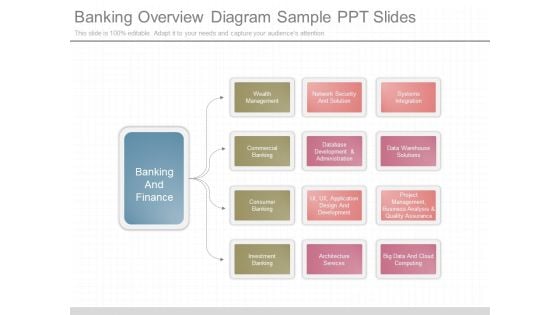
Banking Overview Diagram Sample Ppt Slides
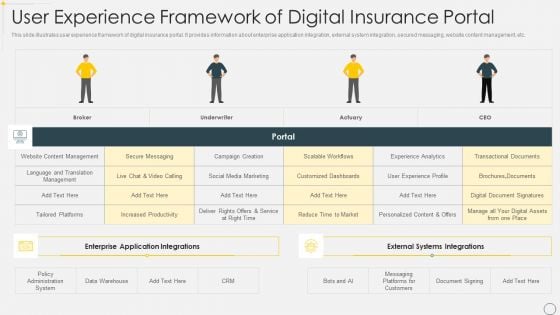
User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
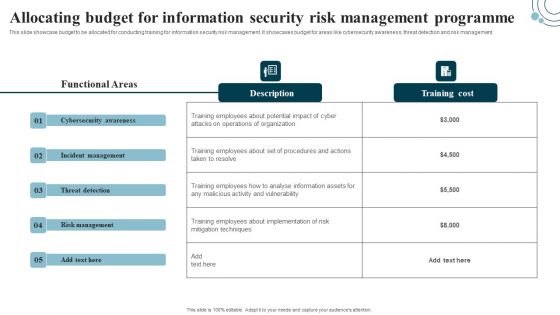
Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
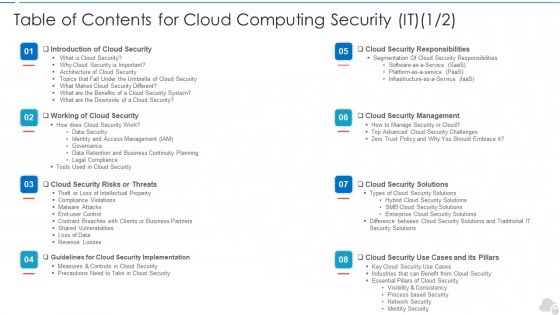
Table Of Contents For Cloud Computing Security IT Business Ppt File Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents for cloud computing security it business ppt file inspiration pdf bundle. Topics like cloud security implementation, cloud security responsibilities, cloud security management, cloud security solutions, cloud security risks or threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
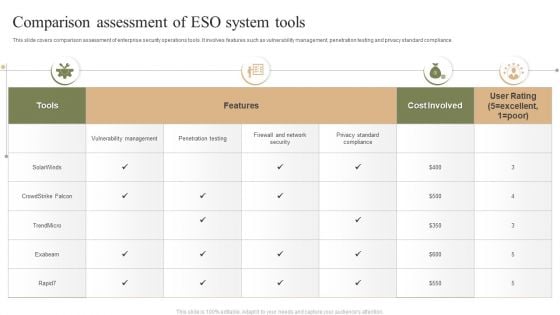
Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF
This slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Showcasing this set of slides titled Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF. The topics addressed in these templates are Cost Involved, Vulnerability Management, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Processing Maturity Model With Information Architecture Background PDF
Persuade your audience using this data processing maturity model with information architecture background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including data services, data management, security management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
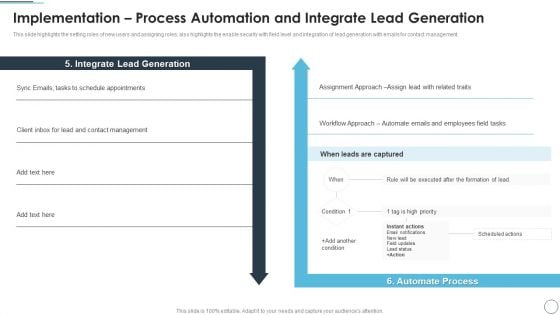
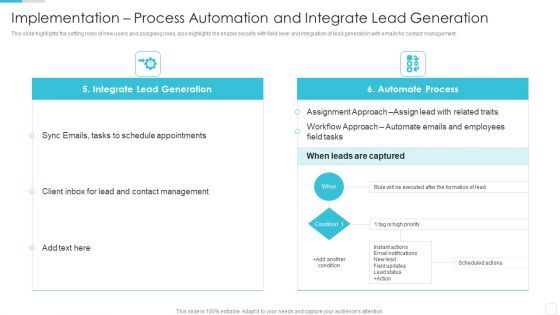
Implementation Process Automation And Integrate Lead Generation Demonstration PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Implementation Process Automation And Integrate Lead Generation Demonstration PDF bundle. Topics like Schedule Appointments, Contact Management, Lead Generation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Sales CRM Cloud Solutions Deployment Implementation Process Automation Elements PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Sales CRM Cloud Solutions Deployment Implementation Process Automation Elements PDF bundle. Topics like Schedule Appointments, Contact Management, Assignment Approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
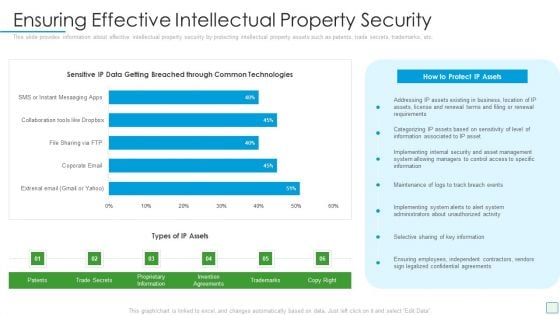
Developing Firm Security Strategy Plan Ensuring Effective Intellectual Property Security Download PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan ensuring effective intellectual property security download pdf. Use them to share invaluable insights on business, management, implementing, maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Technology Facility Maintenance And Provider What Services Do We Offer To Clients Inspiration PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider what services do we offer to clients inspiration pdf bundle. Topics like server monitoring, patch management, performance reporting, automated maintenance, endpoint security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
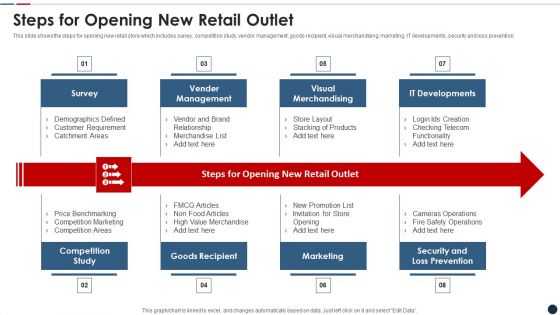
Steps For Opening New Retail Outlet Designs PDF
This slide shows the steps for opening new retail store which includes survey, competition study, vendor management, goods recipient, visual merchandising, marketing, IT developments, security and loss prevention.Pitch your topic with ease and precision using this steps for opening new retail outlet designs pdf This layout presents information on Vender management, visual merchandising, competition study It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
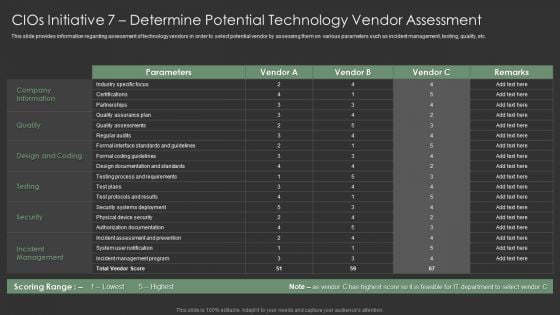
Cios Initiative 7 Determine Potential Technology Vendor Assessment Graphics PDF
This slide provides information regarding assessment of technology vendors in order to select potential vendor by assessing them on various parameters such as incident management, testing, quality, etc. Deliver and pitch your topic in the best possible manner with this Cios Initiative 7 Determine Potential Technology Vendor Assessment Graphics PDF. Use them to share invaluable insights on Quality, Incident Management, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
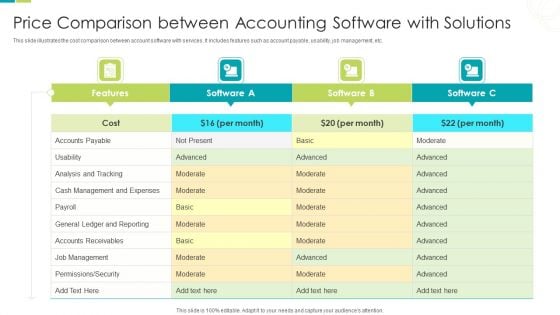
Price Comparison Between Accounting Software With Solutions Ppt PowerPoint Presentation Ideas Structure PDF
This slide illustrates the cost comparison between account software with services. It includes features such as account payable, usability, job management, etc. Pitch your topic with ease and precision using this Price Comparison Between Accounting Software With Solutions Ppt PowerPoint Presentation Ideas Structure PDF. This layout presents information on Cash Management, General Ledger, Permissions Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
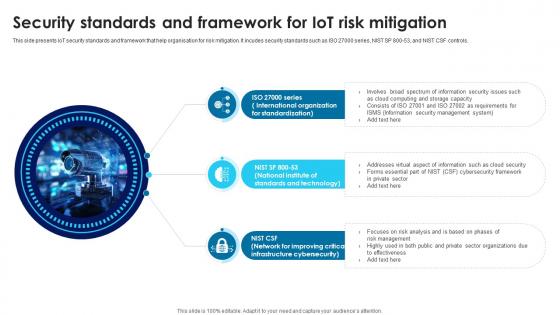
Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.
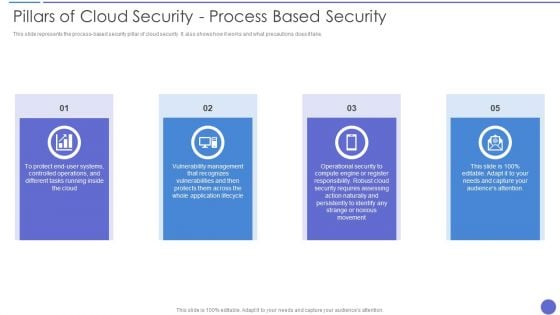
Pillars Of Cloud Security Process Based Security Information PDF
This slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Pillars Of Cloud Security Process Based Security Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Application, Security Requires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
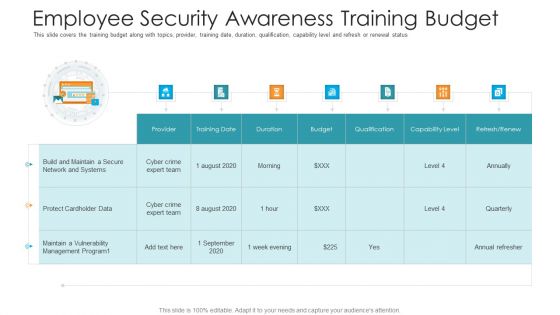
Employee Security Awareness Training Budget Hacking Prevention Awareness Training For IT Security Guidelines PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this employee security awareness training budget hacking prevention awareness training for it security guidelines pdf. Use them to share invaluable insights on training, maintain, management, budget, capability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
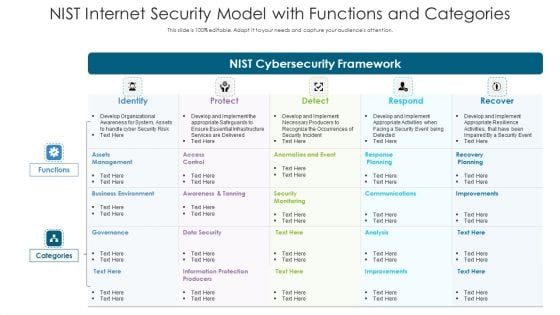
NIST Internet Security Model With Functions And Categories Ppt PowerPoint Presentation Model Show PDF
Showcasing this set of slides titled NIST internet security model with functions and categories ppt powerpoint presentation model show pdf. The topics addressed in these templates are assets management, recovery planning, information protection producers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Developing Firm Security Strategy Plan Information PDF
Deliver an awe inspiring pitch with this creative table of contents for developing firm security strategy plan information pdf bundle. Topics like implementing, security, management, corporate, governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
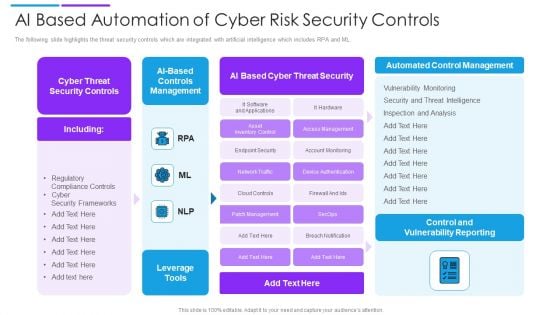
AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
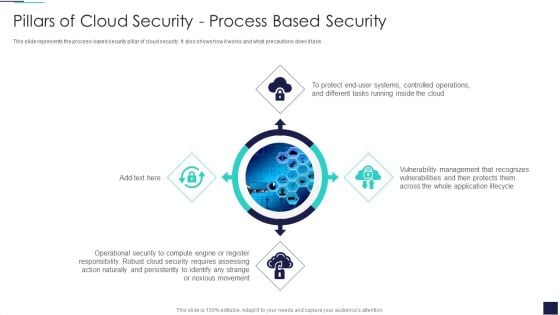
Cloud Information Security Pillars Of Cloud Security Process Based Security Ppt Slides Topics PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Cloud Information Security Pillars Of Cloud Security Process Based Security Ppt Slides Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Controlled Operations, Vulnerability Management, Application Lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf
This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.Pitch your topic with ease and precision using this Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf This layout presents information on Secure Management, Prioritize Personal, Security Awareness It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.
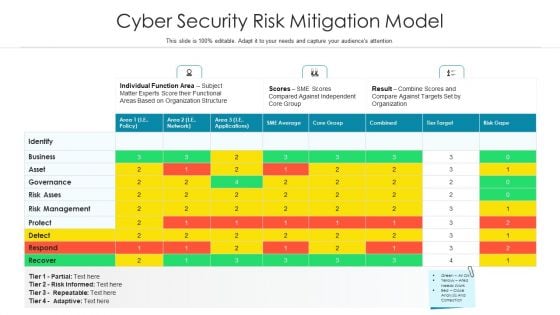
Cyber Security Risk Mitigation Model Ppt PowerPoint Presentation Infographics Sample PDF
Showcasing this set of slides titled cyber security risk mitigation model ppt powerpoint presentation infographics sample pdf. The topics addressed in these templates are risk management, functional areas based, subject matter experts score. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take.This is a Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Recognizes Vulnerabilities, Operational Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
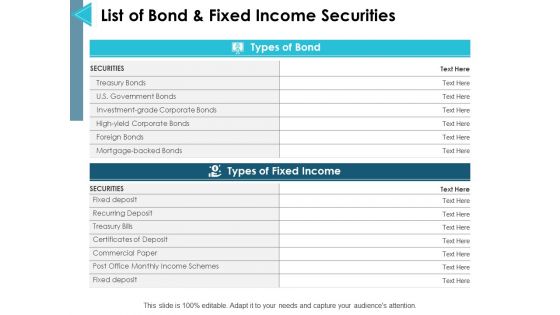
List Of Bond And Fixed Income Securities Ppt PowerPoint Presentation Layouts Graphics Design
This is a list of bond and fixed income securities ppt powerpoint presentation layouts graphics design. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.

Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf
This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner Showcasing this set of slides titled Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf The topics addressed in these templates are Technical Coordinator, Incident Manager, Support Coordinator All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner


 Continue with Email
Continue with Email

 Home
Home


































