Cyber Security Attack

Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Model, Negative Model, Positive Model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Understanding The Frequency And Weightage Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
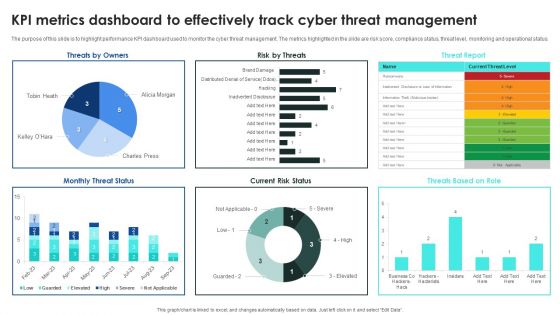
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Welcome to our selection of the Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Metrics Dashboard To Effectively Track Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
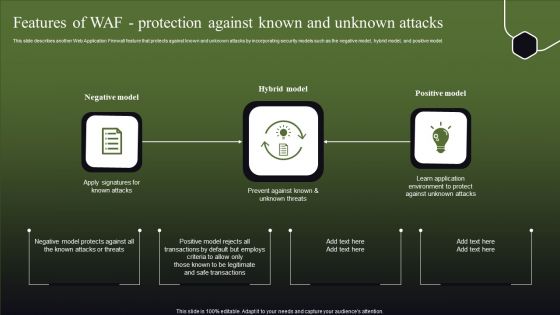
Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF
This slide describes another Web Application Firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. This modern and well-arranged Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
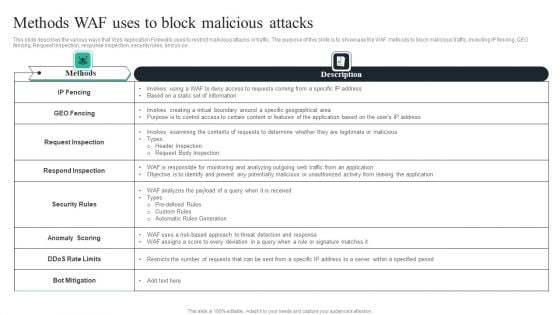
WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF
This slide describes the various ways that Web Application Firewalls uses to restrict malicious attacks or traffic. The purpose of this slide is to showcase the WAF methods to block malicious traffic, including IP fencing, GEO fencing, Request Inspection, response inspection, security rules, and so on. Welcome to our selection of the WAF Introduction Methods WAF Uses To Block Malicious Attacks Graphics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
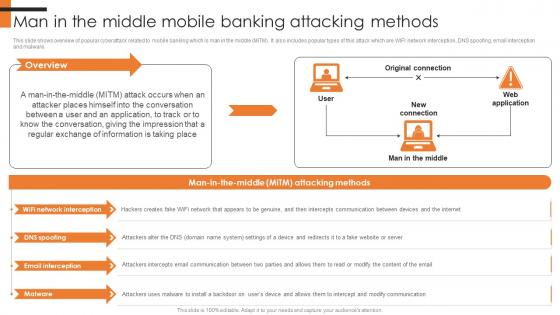
Man In The Middle Mobile Banking Attacking Comprehensive Smartphone Banking Mockup Pdf
This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interceptio and malware.Find a pre-designed and impeccable Man In The Middle Mobile Banking Attacking Comprehensive Smartphone Banking Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM . It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware.

Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V
This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. There are so many reasons you need a Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM . It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware
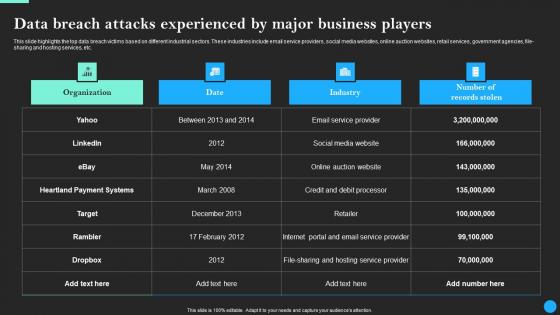
Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf
This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc.
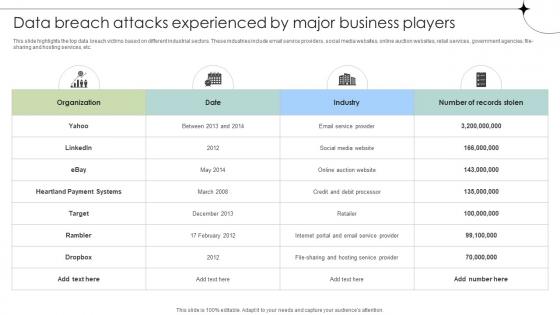
Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses
This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses can be your best option for delivering a presentation. Represent everything in detail using Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc.
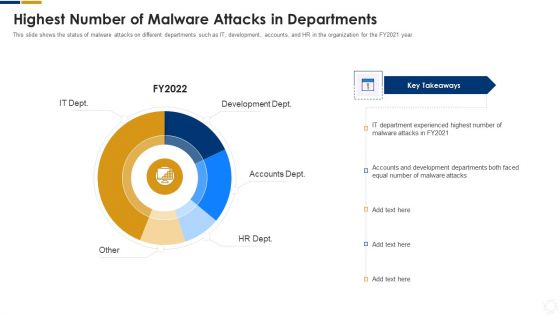
Cybersecurity Highest Number Of Malware Attacks In Departments Ppt Styles Graphic Images PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative cybersecurity highest number of malware attacks in departments ppt styles graphic images pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Various Techniques Designs PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Various Techniques Designs PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
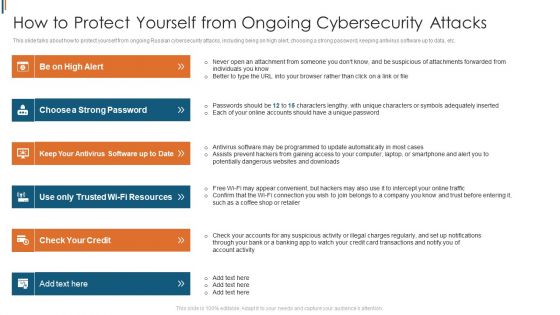
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
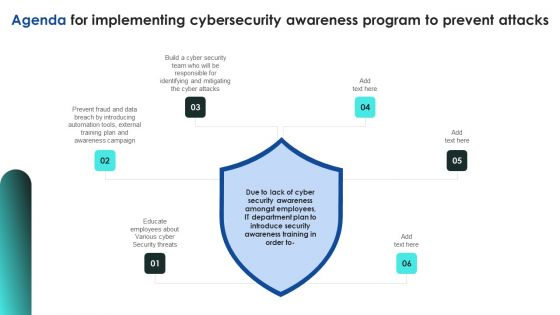
Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF
Create an editable Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Agenda For Implementing Cybersecurity Awareness Program To Prevent Attacks Designs PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Icons Slide Implementing Cybersecurity Awareness Program To Prevent Attacks Elements PDF
Introducing our well designed Icons Slide Implementing Cybersecurity Awareness Program To Prevent Attacks Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF
The purpose of this slide is to showcase the Does and do nots of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cybersecurity Awareness Program To Prevent Attacks Table Of Contents Elements PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Table Of Contents Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
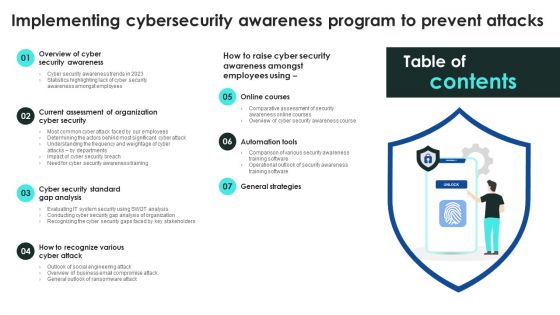
Table Of Contents Implementing Cybersecurity Awareness Program To Prevent Attacks Slides PDF
Boost your pitch with our creative Table Of Contents Implementing Cybersecurity Awareness Program To Prevent Attacks Slides PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF
Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
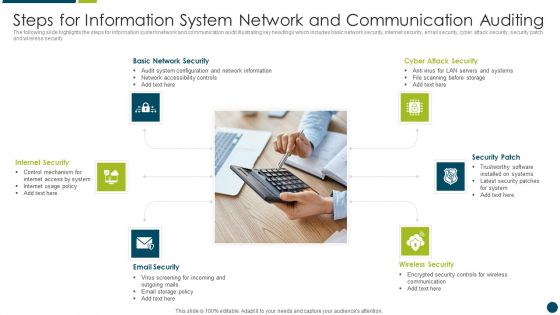
Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

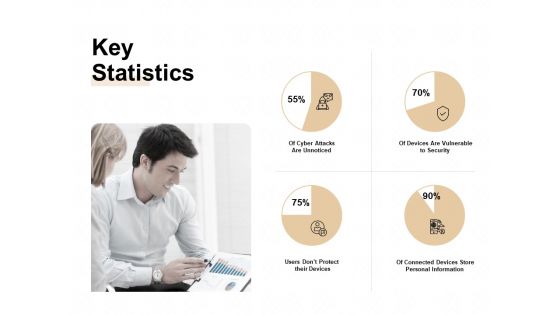
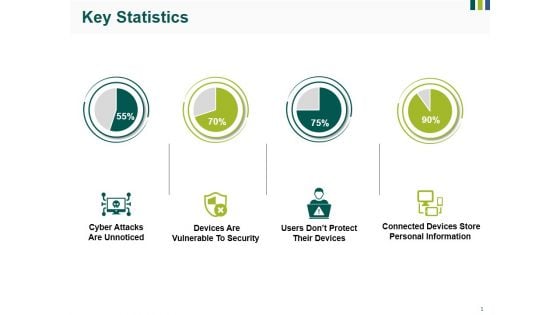
Key Statistics Ppt PowerPoint Presentation Professional Master Slide
This is a key statistics ppt powerpoint presentation professional master slide. This is a four stage process. The stages in this process are users dont protect their devices, cyber attacks are unnoticed, devices are vulnerable to security.

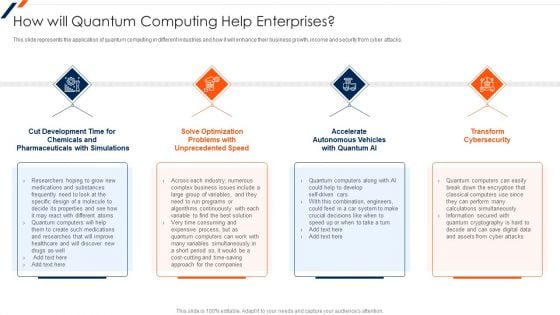
Quantum Computing For Everyone IT How Will Quantum Computing Help Enterprises Download PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it how will quantum computing help enterprises download pdf. Use them to share invaluable insights on development, optimization, accelerate autonomous, transform cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Market Sizing Key Statistics Ppt Infographic Template Design Templates PDF
Presenting this set of slides with name market sizing key statistics ppt infographic template design templates pdf. This is a one stage process. The stages in this process are users dont protect their devices, of connected devices store personal information, of devices are vulnerable to security, of cyber attacks are unnoticed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
TAM SAM And SOM Key Statistics Ppt Inspiration Maker PDF
Presenting tam sam and som key statistics ppt inspiration maker pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like users dont protect their devices, of connected devices store personal information, of devices are vulnerable to security, of cyber attacks are unnoticed. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Market Approach To Business Valuation Key Statistics Summary PDF
Presenting this set of slides with name market approach to business valuation key statistics summary pdf. This is a four stage process. The stages in this process are cyber attacks unnoticed, devices vulnerable security, users dont protect devices, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. This is a How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Time, Optimization Problems, Transform Cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Presenting How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Transform Cybersecurity, Complex Business, Accelerate Autonomous Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
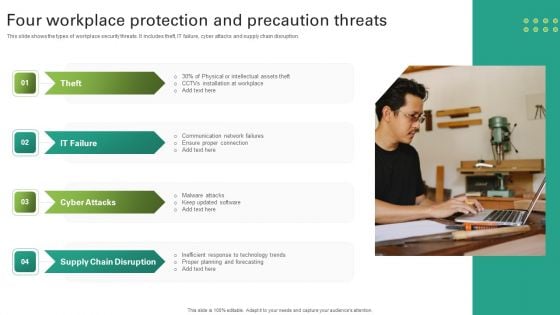
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
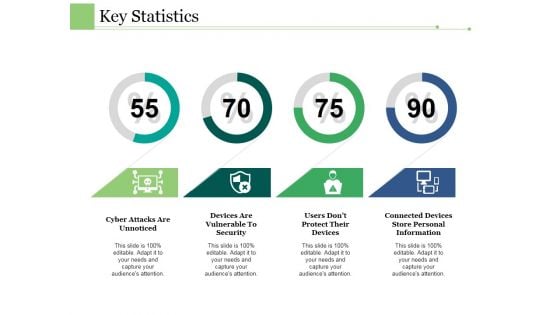
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.
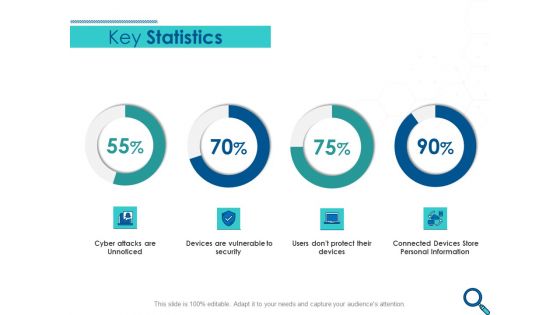
Key Statistics Ppt PowerPoint Presentation Gallery Format Ideas
This is a key statistics ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users dont protect their devices, connected devices store personal information.
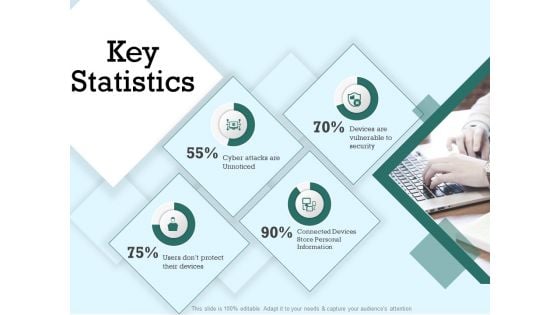
Evaluating Competitive Marketing Effectiveness Key Statistics Ppt Portfolio Ideas PDF
Presenting this set of slides with name evaluating competitive marketing effectiveness key statistics ppt portfolio ideas pdf. The topics discussed in these slides are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Survey Analysis Gain Marketing Insights Key Statistics Sample PDF
Presenting this set of slides with name survey analysis gain marketing insights key statistics sample pdf. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
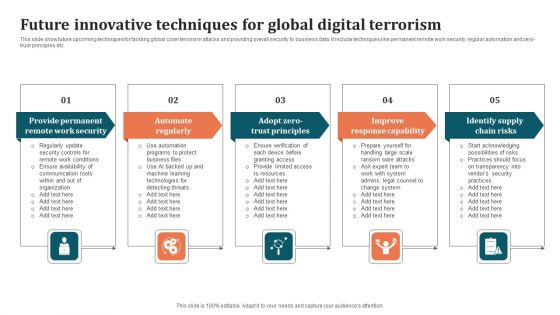
Future Innovative Techniques For Global Digital Terrorism Background PDF
This slide show future upcoming techniques for tackling global cyber terrorism attacks and providing overall security to business data. It include techniques like permanent remote work security, regular automation and zero-trust principles etc. Persuade your audience using this Future Innovative Techniques For Global Digital Terrorism Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Response Capability, Identify Supply Chain Risks, Automate Regularly. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
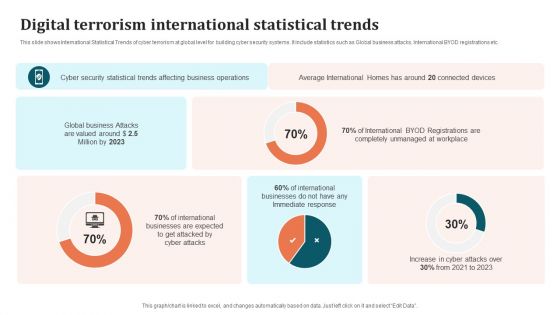
Digital Terrorism International Statistical Trends Brochure PDF
This slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc. Showcasing this set of slides titled Digital Terrorism International Statistical Trends Brochure PDF. The topics addressed in these templates are International Businesses, Cyber Security Statistical Trends, Business Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Best Practices For Online Risk Management Graphics PDF
The purpose of this slide is to represent digital risk areas and solutions for effective risk management. It includes various risks such as mitigating cyber risk attack, managing third party, handling dynamic workforce, securing cloud migration etc. Presenting Best Practices For Online Risk Management Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigating Cyber Risk Attack, Managing Third Party, Handling Dynamic Workforce. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Protection Under Umbrella Savings Finance PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Protection Under Umbrella Savings Finance PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Umbrellas PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download and present our Security PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Use our Signs PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are a sure bet. Gauranteed to win against all odds. Use these PowerPoint slides for presentations relating to Piggy under the umbrella, security, umbrellas, signs, shapes, finance. The prominent colors used in the PowerPoint template are Yellow, Black, Gray. Lead your attack with our Protection Under Umbrella Savings Finance PowerPoint Templates Ppt Backgrounds For Slides 0313. You will come out on top.
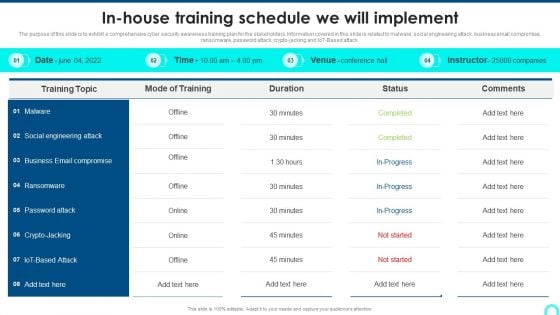
In House Training Schedule We Will Implement Icons PDF
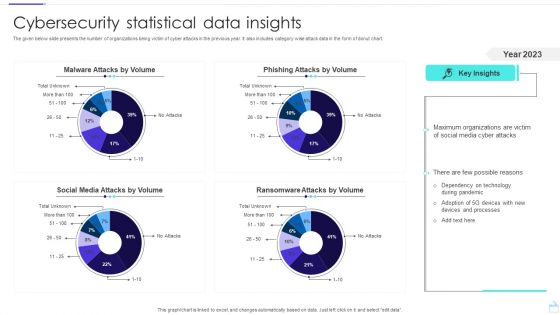
Cybersecurity Statistical Data Insights Sample PDF
The given below slide presents the number of organizations being victim of cyber attacks in the previous year. It also includes category wise attack data in the form of donut chart. Pitch your topic with ease and precision using this Cybersecurity Statistical Data Insights Sample PDF. This layout presents information on Social Media Attacks, Malware Attacks, Phishing Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
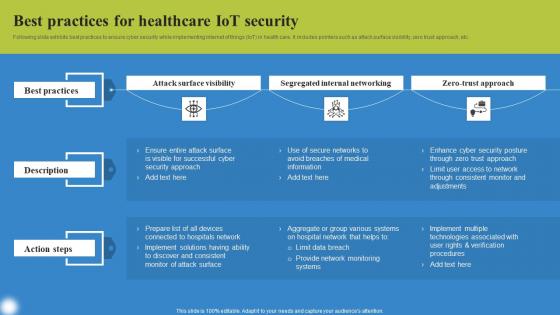
Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc.
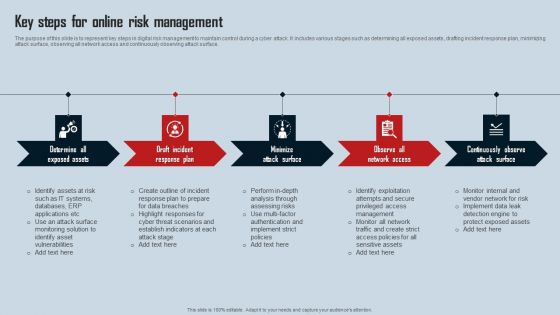
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
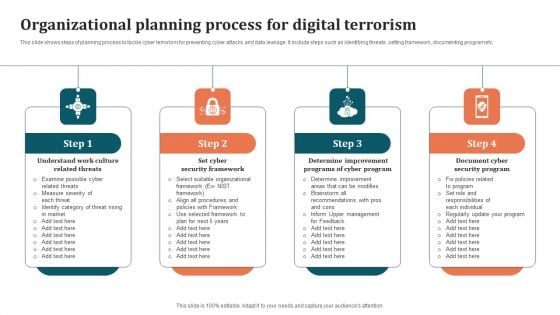
Organizational Planning Process For Digital Terrorism Graphics PDF
This slide shows steps of planning process to tackle cyber terrorism for preventing cyber attacks and data leakage. It include steps such as identifying threats, setting framework, documenting program etc. Presenting Organizational Planning Process For Digital Terrorism Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Program, Determine Improvement Programs, Document Cyber Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Present like a pro with Software Defined Perimeter Enhancing Workload Efficiency Through Cloud Architecture Pictures Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.
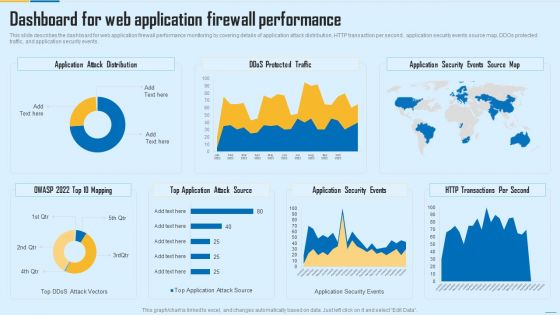
Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver an awe inspiring pitch with this creative Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF bundle. Topics like Application Attack Distribution, Application Security Events, Transactions Per Second can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

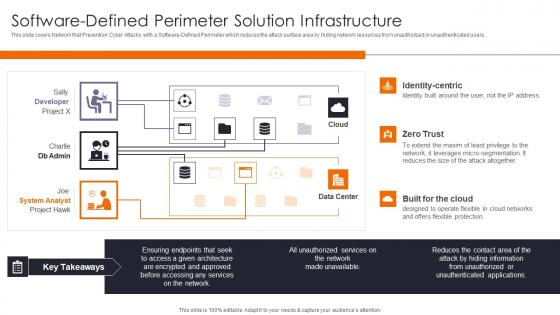
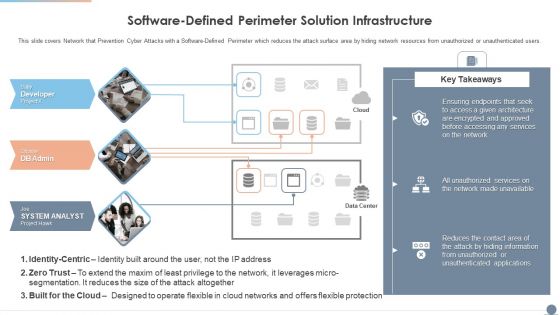
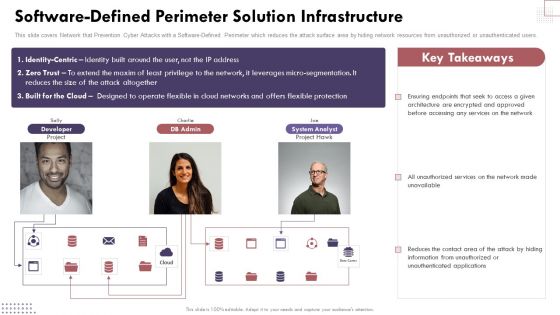
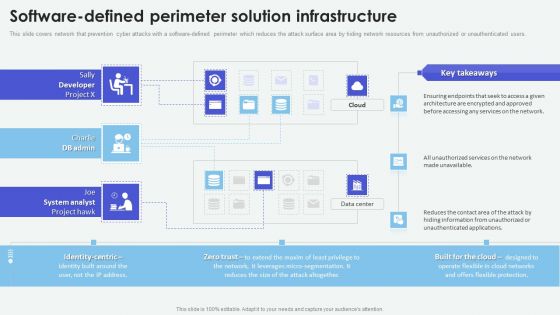
Software Defined Perimeter Solution Infrastructure Elements PDF
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Deliver an awe inspiring pitch with this creative Software Defined Perimeter Solution Infrastructure Elements PDF bundle. Topics like System Analyst, Services, Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
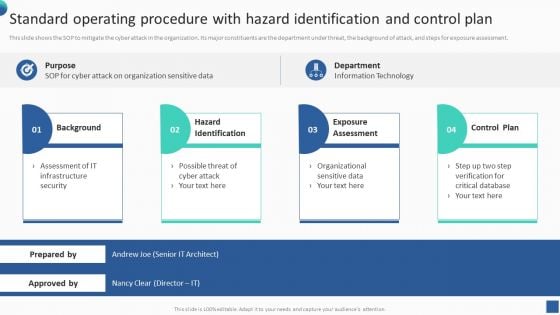
Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF
This slide shows the SOP to mitigate the cyber attack in the organization. Its major constituents are the department under threat, the background of attack, and steps for exposure assessment. There are so many reasons you need a Bundle Of SOP Templates Standard Operating Procedure With Hazard Identification And Control Information PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
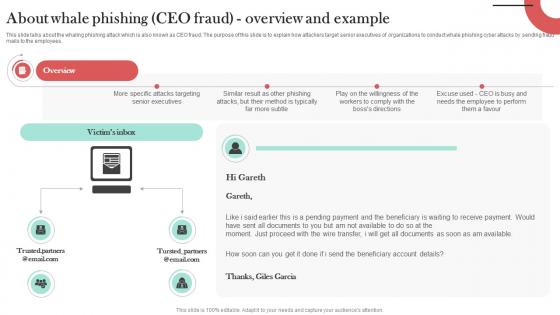
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees.
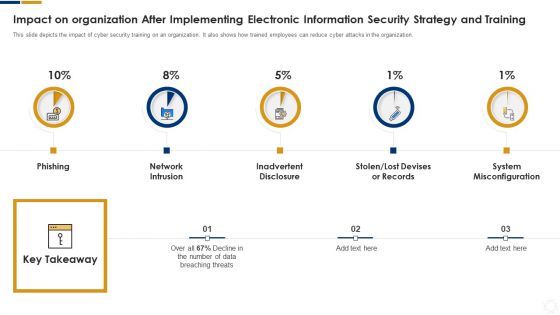
Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
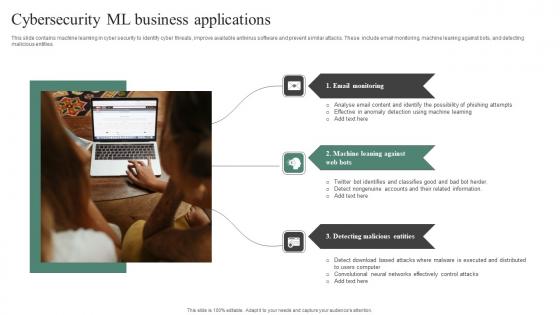
Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities.

Softwaredefined Perimeter Solution Infrastructure Managing Complexity Of Multiple Cloud Platforms Inspiration PDF
This slide covers network that prevention cyber attacks with a software-defined perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.Make sure to capture your audiences attention in your business displays with our gratis customizable Softwaredefined Perimeter Solution Infrastructure Managing Complexity Of Multiple Cloud Platforms Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Multi Cloud Complexity Management Software Defined Perimeter Solution Infrastructure Summary PDF
This slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Presenting Multi Cloud Complexity Management Software Defined Perimeter Solution Infrastructure Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cloud Networks, Services, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Software Defined Perimeter Solution Infrastructure Cloud Computing Complexities And Solutions Infographics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF
This slide covers network that prevention cyber attacks with a software-defined perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Based Computing Analysis Software Defined Perimeter Solution Infrastructure Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest
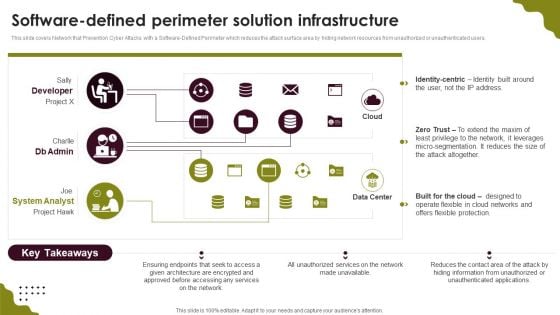
Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Take your projects to the next level with our ultimate collection of Cloud Computing Scalability Software Defined Perimeter Solution Infrastructure Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
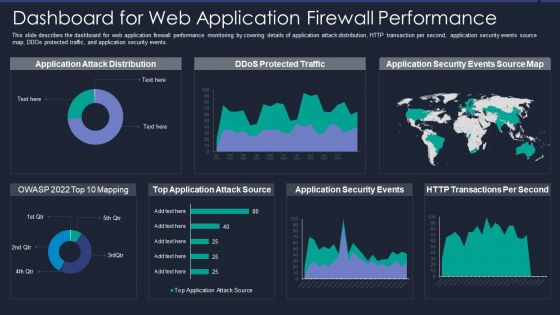
Web App Firewall Services IT Dashboard For Web Application Firewall Performance Microsoft PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver and pitch your topic in the best possible manner with this web app firewall services it dashboard for web application firewall performance microsoft pdf. Use them to share invaluable insights on application, source, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
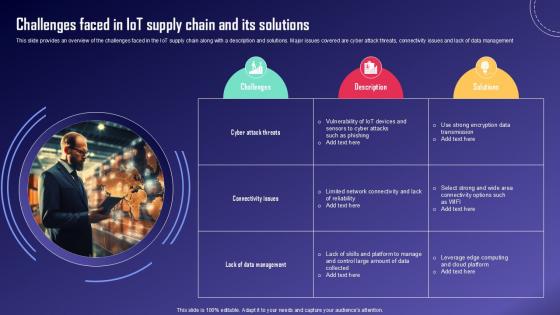
Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V
This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management

Table Of Contents For Ukraine Cyberwarfare Cont Mockup Pdf
This is a table of contents for ukraine cyberwarfare cont mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reasons behind ukraine and russia cyber warfare, russian operations against ukraine, cyber attacks on ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
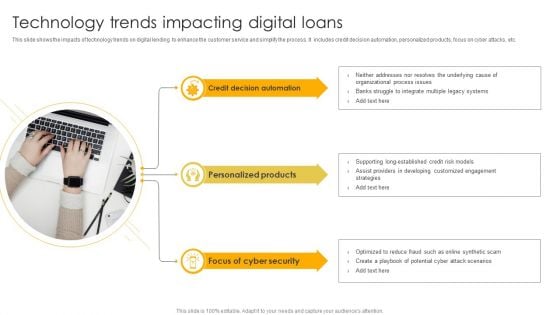
Technology Trends Impacting Digital Loans Ppt Summary Model PDF
This slide shows the impacts of technology trends on digital lending to enhance the customer service and simplify the process. It includes credit decision automation, personalized products, focus on cyber attacks, etc. Persuade your audience using this Technology Trends Impacting Digital Loans Ppt Summary Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Credit Decision Automation, Personalized Products, Focus Cyber Security . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































