Cyber Security Attack

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
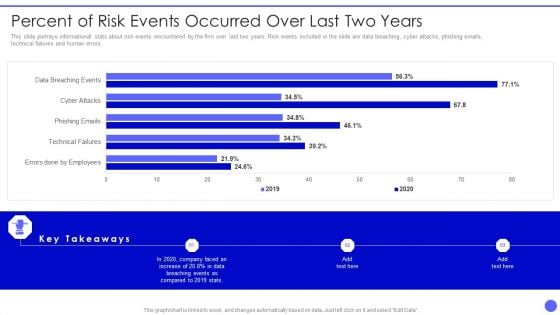
Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF bundle. Topics like Errors Done By Employees, Technical Failures, Phishing Emails, Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
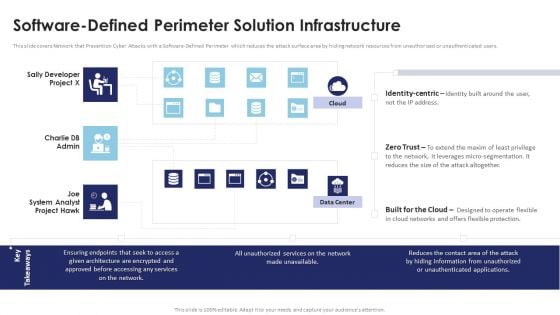
Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF
This slide covers Network that Prevention Cyber Attacks with a Software-Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Are you searching for a Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multi Cloud Infrastructure Management Software Defined Perimeter Solution Infrastructure Ideas PDF from Slidegeeks today.
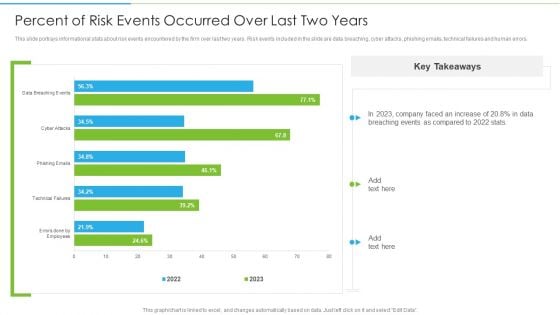
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
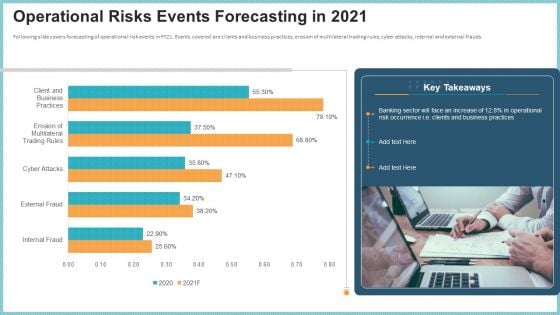
OP Risk Management Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative op risk management operational risks events forecasting in 2021 designs pdf bundle. Topics like client and business practices, erosion of multilateral trading rules, cyber attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Training Program Budget And Schedule Dates Graphics PDF
This slide covers the training schedule for various cyber security incidents program. It further includes budget allocated, training duration, dates for training and review sessions.Showcasing this set of slides titled Cybersecurity Training Program Budget And Schedule Dates Graphics PDF. The topics addressed in these templates are Malware Attack, Emergency Report, Capability Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
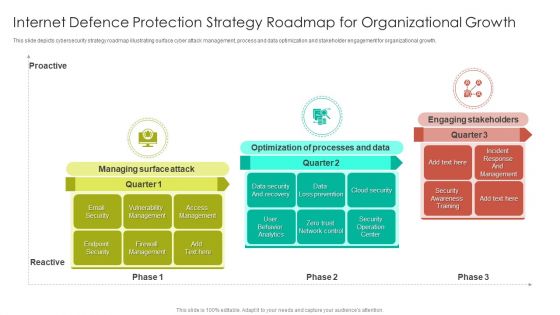
Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF
This slide depicts cybersecurity strategy roadmap illustrating surface cyber attack management, process and data optimization and stakeholder engagement for organizational growth.Persuade your audience using this Internet Defence Protection Strategy Roadmap For Organizational Growth Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Optimization Processes, Engaging Stakeholders, Vulnerability Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Transformation Plan Incident Management Chart For Transition Project Ppt Icon Visuals PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver an awe inspiring pitch with this creative transformation plan incident management chart for transition project ppt icon visuals pdf bundle. Topics like incident, priority, feature enhancement, cyber attack can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

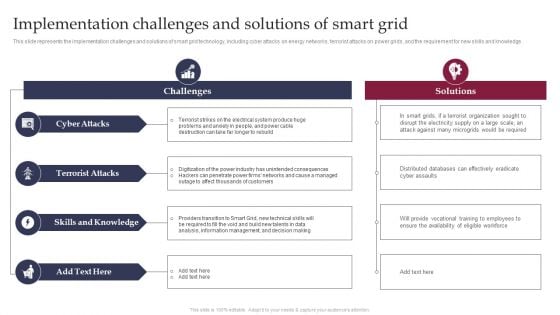
Implementation Challenges And Solutions Of Smart Grid Smart Grid Working
This slide represents the implementation challenges and solutions of smart grid technology, including cyber attacks on energy networks, terrorist attacks on power grids, and the requirement for new skills and knowledge. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementation Challenges And Solutions Of Smart Grid Smart Grid Working and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the implementation challenges and solutions of smart grid technology, including cyber attacks on energy networks, terrorist attacks on power grids, and the requirement for new skills and knowledge.
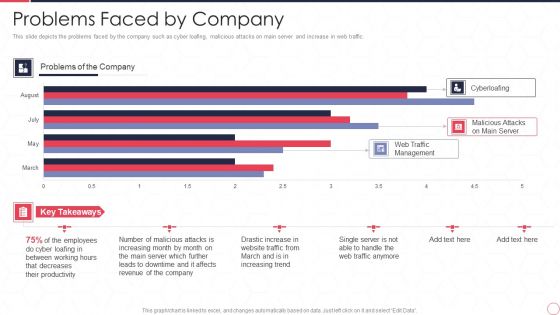
Reverse Proxy Server IT Problems Faced By Company Ppt Summary Inspiration PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Deliver and pitch your topic in the best possible manner with this reverse proxy server it problems faced by company ppt summary inspiration pdf. Use them to share invaluable insights on web traffic management, malicious attacks on main server, cyberloafing, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
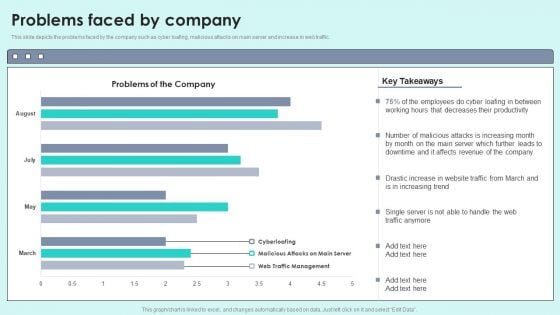
Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic.Deliver and pitch your topic in the best possible manner with this Problems Faced By Company Reverse Proxy For Load Balancing Designs PDF. Use them to share invaluable insights on Decreases Productivity, Malicious Attacks, Affects Revenue and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
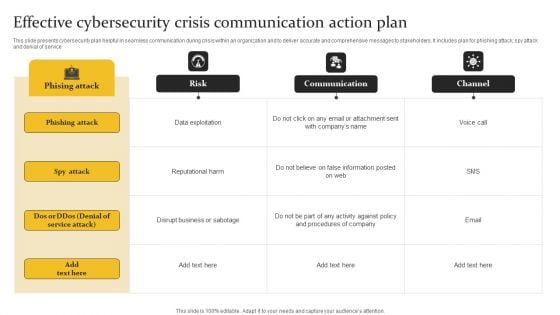
Effective Cybersecurity Crisis Communication Action Plan Graphics PDF
This slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Pitch your topic with ease and precision using this Effective Cybersecurity Crisis Communication Action Plan Graphics PDF. This layout presents information on Phishing Attack, Data Exploitation, Reputational Harm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
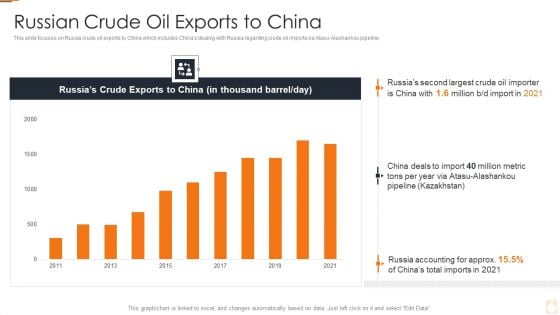
Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF
Deliver an awe inspiring pitch with this creative Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF bundle. Topics like Higher Energy Prices, Trade And Supply Chains, Increase In Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

About Spear Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Spear Phishing Overview And Example Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Spear Phishing Overview And Example Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks.

Table Of Contents For Ukraine Cyberwarfare Demonstration Pdf
Presenting table of contents for ukraine cyberwarfare demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like steps to mitigate russian cyber attacks, are there international laws establishing cyber policies, weaknesses of russian cyber cell. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
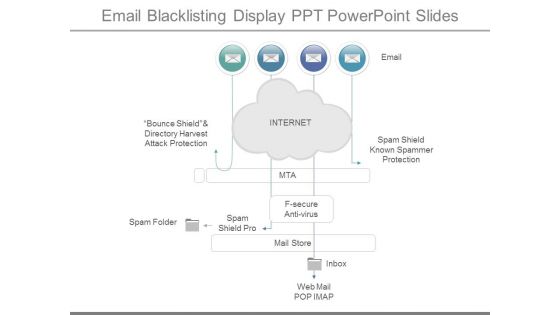
Email Blacklisting Display Ppt Powerpoint Slides
This is a email blacklisting display ppt powerpoint slides. This is a one stage process. The stages in this process are email, spam shield known spammer protection, internet, bounce shield and directory harvest attack protection, mta, spam folder, spam shield pro, f secure anti virus, mail store, inbox, web mail pop imap.

Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF bundle. Topics like Unavailability Of Power, Risk Encountered, Attack Scenario can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
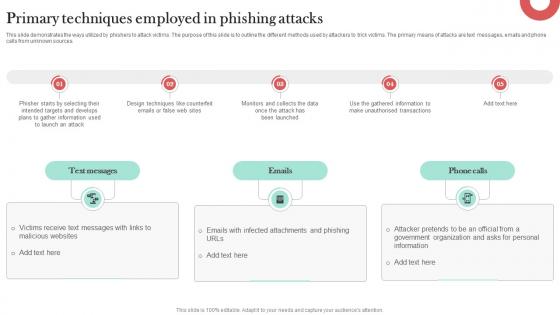
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.
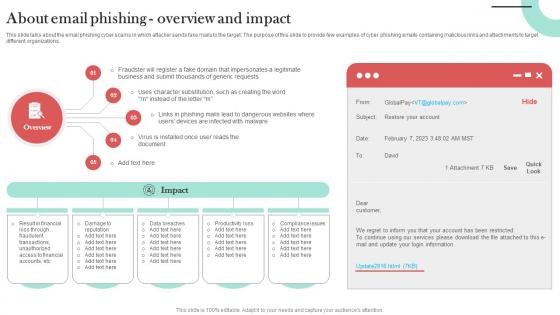
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations.
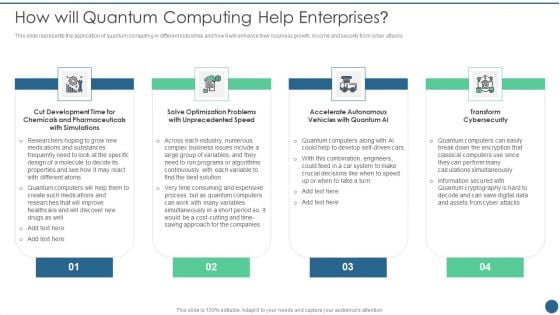
Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks.This is a Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Optimization Problems, Accelerate Autonomous, Vehicles Quantum You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
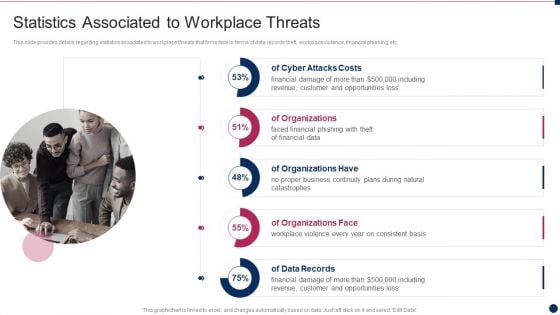
Threat Management At Workplace Statistics Associated To Workplace Threats Summary PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver an awe inspiring pitch with this creative threat management at workplace statistics associated to workplace threats summary pdf bundle. Topics like cyber attacks costs, organization, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
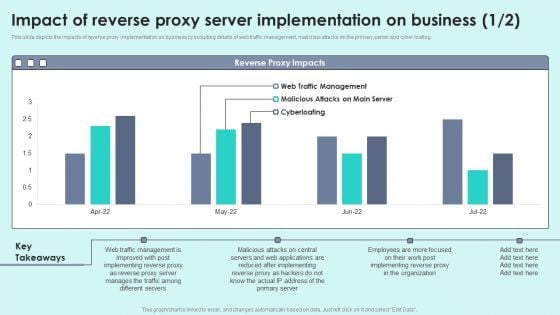
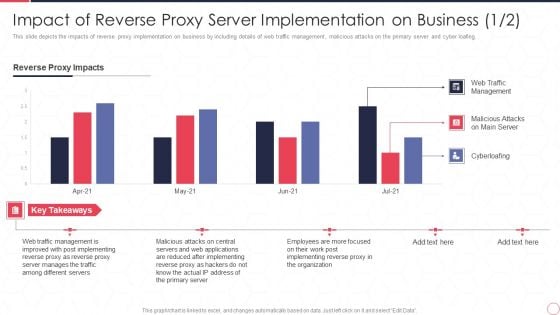
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing.Deliver an awe inspiring pitch with this creative Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy For Load Balancing Infographics PDF bundle. Topics like After Implementing, Manages Traffic, Different Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
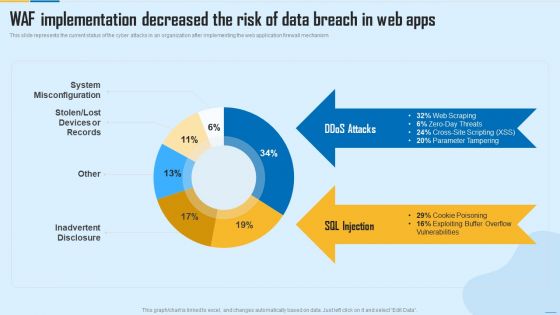
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Terrorism Types And Categories With Examples Sample PDF
This slide shows various categories of cyber terrorism attacks according to their severity . It include categories such as simple unstructured, advance structured, complex coordinated etc. Showcasing this set of slides titled Digital Terrorism Types And Categories With Examples Sample PDF. The topics addressed in these templates are Advance Structured, Complex Coordinated, Simple Unstructured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Smart Grid Technology Implementation Challenges And Solutions Designs PDF
Impact Of Reverse Proxy Server Implementation On Business Reverse Proxy Server IT Ppt Professional Slides PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Deliver an awe inspiring pitch with this creative impact of reverse proxy server implementation on business reverse proxy server it ppt professional slides pdf bundle. Topics like reverse proxy impacts, web traffic management, malicious attacks on main server, cyberloafing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Trends In Business Management Template Ppt Design
This is a trends in business management template ppt design. This is a three stage process. The stages in this process are business strategy focus on growth, corporate strategy, preventing cyber attacks.
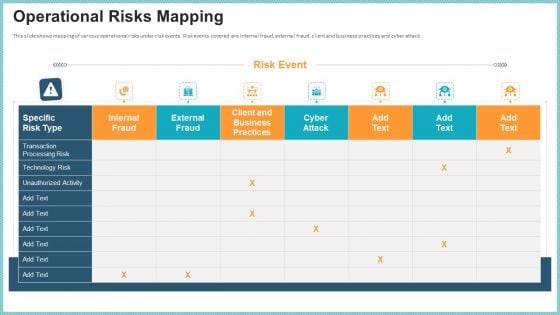
OP Risk Management Operational Risks Mapping Rules PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative op risk management operational risks mapping rules pdf bundle. Topics like external fraud, cyber attack, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
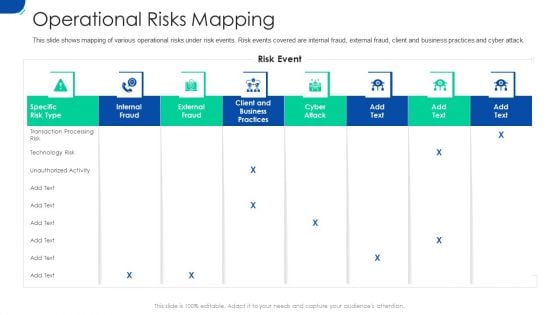
Initiating Hazard Managing Structure Firm Operational Risks Mapping Ideas PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risks mapping ideas pdf bundle. Topics like internal fraud, external fraud, cyber attack, client, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
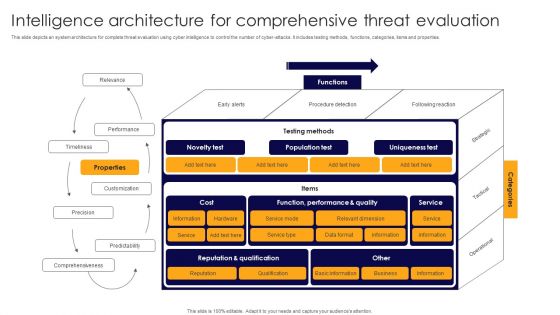
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection.

WAF Features And Capabilities Ppt Pictures Designs Download PDF
This slide represents the capabilities and characteristics of a Web Application Firewall security solution. This slide aims to showcase the various features of WAF, including AI-powered traffic patterns, attack signature databases, application profiling, customization, correlation engines, and so on. Slidegeeks has constructed WAF Features And Capabilities Ppt Pictures Designs Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
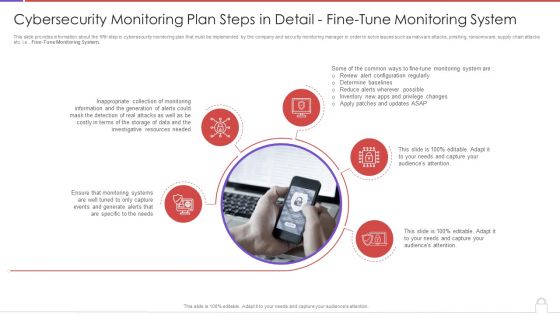
Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Slides PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine-Tune Monitoring System. Presenting cybersecurity monitoring plan steps in detail fine tune monitoring system slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like inappropriate collection, monitoring information, investigative resources needed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
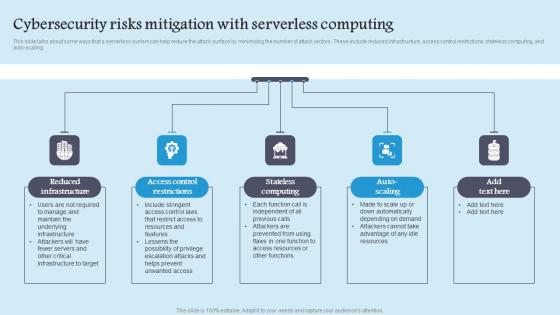
Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf
This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto scaling. Presenting this PowerPoint presentation, titled Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cybersecurity Risks Mitigation Role Serverless Computing Modern Technology Summary Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto scaling.
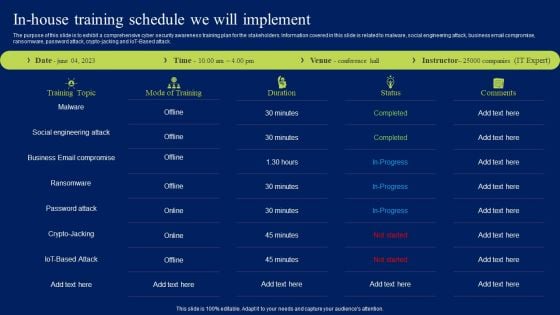
In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
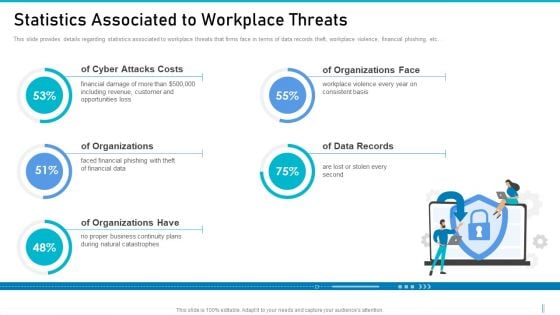
Risk Management For Organization Essential Assets Statistics Associated To Workplace Threats Structure PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Presenting risk management for organization essential assets statistics associated to workplace threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cyber attacks costs, data records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
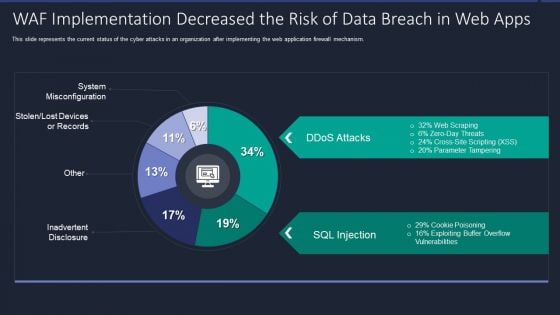
Web App Firewall Services IT WAF Implementation Decreased The Risk Of Data Breach In Web Apps Portrait PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this web app firewall services it waf implementation decreased the risk of data breach in web apps portrait pdf. Use them to share invaluable insights on waf implementation decreased the risk of data breach in web apps and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda For Ukraine Cyberwarfare Template Pdf
This is a agenda for ukraine cyberwarfare template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like to describe the reasons behind ukraine and russia cyber warfare, to demonstrate the technical analysis of ddos attacks against ukrainian websites, to discuss the steps taken globally to mitigate russian cyberattacks against ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Software Services Business Profile SWOT Analysis Ppt PowerPoint Presentation Icon Backgrounds PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Software Services Business Profile SWOT Analysis Ppt PowerPoint Presentation Icon Backgrounds PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Software Products And Solutions Firm Details SWOT Analysis Icons PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Software Products And Solutions Firm Details SWOT Analysis Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Software Development Company Profile SWOT Analysis Infographics PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Presenting Business Software Development Company Profile SWOT Analysis Infographics PDF to provide visual cues and insights. Share and navigate important information on fpour stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
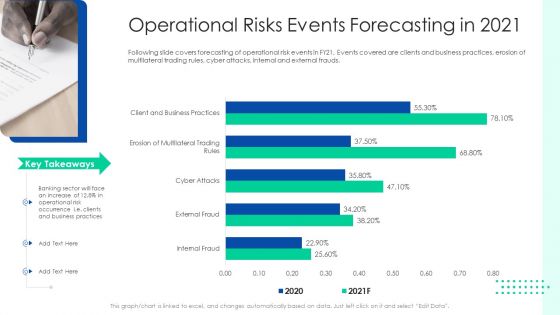
Initiating Hazard Managing Structure Firm Operational Risks Events Forecasting In 2021 Designs PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this initiating hazard managing structure firm operational risks events forecasting in 2021 designs pdf. Use them to share invaluable insights on operational risk events, clients, business practices, cyber attacks, internal and external frauds and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
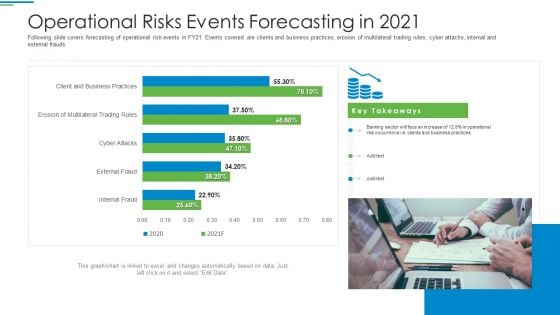
Operational Risk Management Structure In Financial Companies Operational Risks Events Forecasting In 2021 Rules PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks events forecasting in 2021 rules pdf bundle. Topics like business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
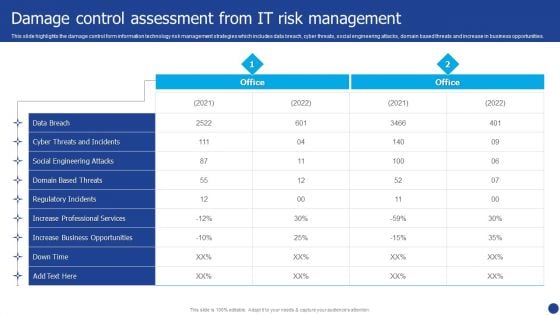
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
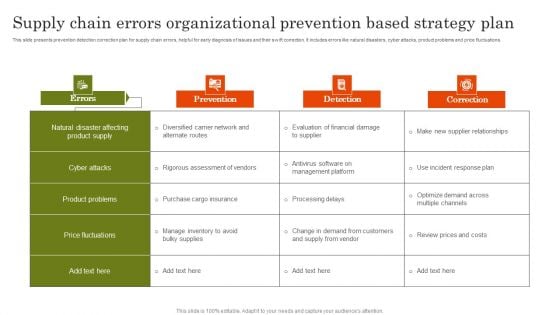
Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF
This slide presents prevention detection correction plan for supply chain errors, helpful for early diagnosis of issues and their swift correction. It includes errors like natural disasters, cyber attacks, product problems and price fluctuations. Present the topic in a bit more detail with this Supply Chain Errors Organizational Prevention Based Strategy Plan Topics PDF. Use it as a tool for discussion and navigation on Cyber Attacks, Product Problems, Price Fluctuations. This template is free to edit as deemed fit for your organization. Therefore download it now.

Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. If you are looking for a format to display your unique thoughts, then the professionally designed Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Supply Chain Disruption Overview And Major Causes Strategic Plan For Enhancing Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.
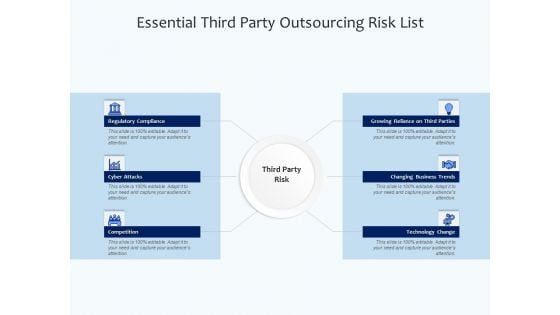
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Scenario Rules PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine threat scenario rules pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
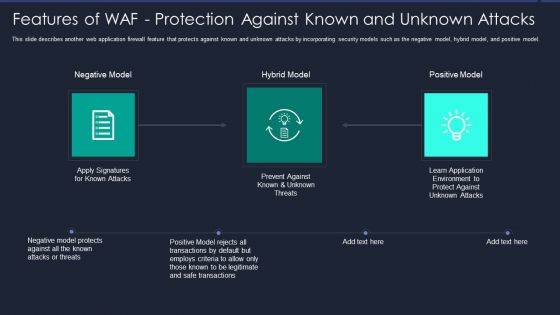
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
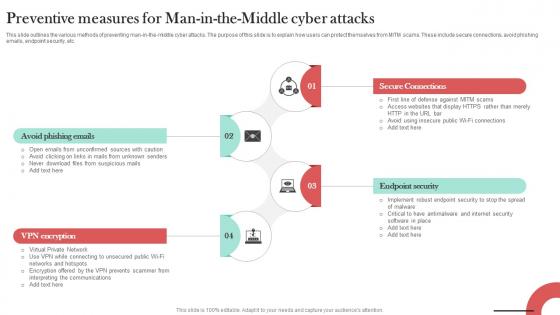
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.

Risk Events Reporting And Likelihood Topics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Events Reporting And Likelihood Topics PDF bundle. Topics like Risk Encountered, Phishing Emails, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF. Use them to share invaluable insights on Risk Encountered, Affected Asset, Phishing Emails and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
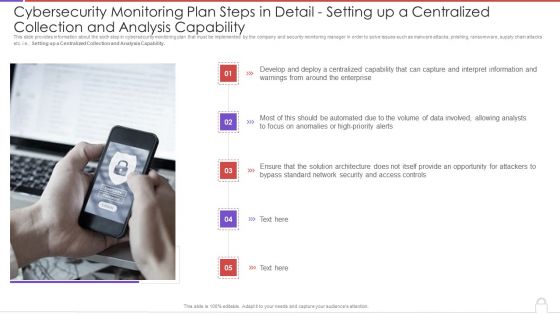
Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































