Cyber Security Attack

Emerging Challenges In Cybersecurity And Solutions To Overcome PPT Template SS
This slide presents emerging challenges in cybersecurity and their solutions helpful in safeguarding all types of data against loss and protecting systems from threats in cyberspace. It includes risks to supply chain, phishing, cloud computing attacks and ransomware issues. Present like a pro with Emerging Challenges In Cybersecurity And Solutions To Overcome PPT Template SS. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide presents emerging challenges in cybersecurity and their solutions helpful in safeguarding all types of data against loss and protecting systems from threats in cyberspace. It includes risks to supply chain, phishing, cloud computing attacks and ransomware issues
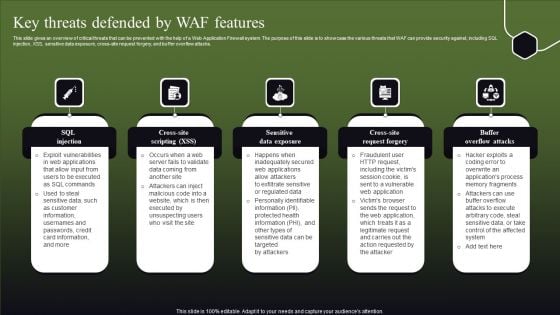
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF
This slide represents the impact of the successful implementation of SecOps in the organization by showing the reduced number of malware attacks on departments. The purpose of this slide is to highlight the reduced number of malware attacks on different departments after implementing SecOps. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
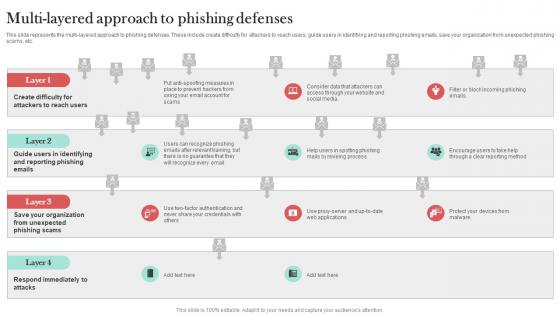
Multi Layered Approach To Phishing Defenses Man In The Middle Phishing IT
This slide represents the multi-layered approach to phishing defenses. These include create difficulty for attackers to reach users, guide users in identifying and reporting phishing emails, save your organization from unexpected phishing scams, etc. Boost your pitch with our creative Multi Layered Approach To Phishing Defenses Man In The Middle Phishing IT. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the multi-layered approach to phishing defenses. These include create difficulty for attackers to reach users, guide users in identifying and reporting phishing emails, save your organization from unexpected phishing scams, etc.
Concept Of Parallel Processing 4 Stages Arrows Linked To Center PowerPoint Templates
We present our concept of parallel processing 4 stages arrows linked to center PowerPoint templates.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Use our Shapes PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners.Use these PowerPoint slides for presentations relating to 3d, around, arrow,browse, click, computer, cursor, design, drag, drop,email, fly, frame, graphic, grey, group, icon, illustration, internet, link, many,marketing, mouse, point, pointer, round, shadow, some, web. The prominent colors used in the PowerPoint template are Gray, White, Black. We assure you our concept of parallel processing 4 stages arrows linked to center PowerPoint templates are readymade to fit into any presentation structure. PowerPoint presentation experts tell us our browse PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. The feedback we get is that our concept of parallel processing 4 stages arrows linked to center PowerPoint templates will make the presenter look like a pro even if they are not computer savvy. We assure you our design PowerPoint templates and PPT Slides are visually appealing. PowerPoint presentation experts tell us our concept of parallel processing 4 stages arrows linked to center PowerPoint templates will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. We assure you our design PowerPoint templates and PPT Slides will get their audience's attention. Plan your attack with our Concept Of Parallel Processing 4 Stages Arrows Linked To Center PowerPoint Templates. You will come out on top.

Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf
This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer. Showcasing this set of slides titled Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf. The topics addressed in these templates are Data Breaches, Respondents, Mitigation Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer.

ML Business Applications In Cybersecurity Business Information PDF
This slide represents machine learning use cases which industries utilize to combat cybersecurity threats, analyze vulnerabilities and provide protection against attacks. Use cases included in this slide are malware detection, software vulnerabilities, phishing attacks, etc. Presenting ML Business Applications In Cybersecurity Business Information PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Network Logs Analysis, Phishing Attacks, Malware Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack. Explore a selection of the finest Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack.
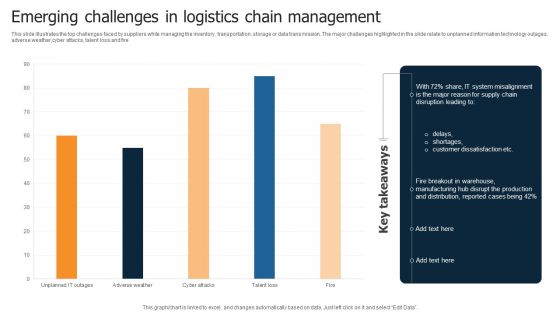
Emerging Challenges In Logistics Chain Management Infographics PDF
This slide illustrates the top challenges faced by suppliers while managing the inventory, transportation, storage or data transmission. The major challenges highlighted in the slide relate to unplanned information technology outages, adverse weather,cyber attacks, talent loss and fire Showcasing this set of slides titled Emerging Challenges In Logistics Chain Management Infographics PDF. The topics addressed in these templates are System Misalignment, Disruption Leading, Customer Dissatisfaction. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Various Techniques To Successfully Prevent Business Email Background PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Prevention Of Information Various Techniques To Successfully Prevent Business Email Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Analyzing The Real Estate Risk With Major Consequences Enhancing Process Improvement By Regularly Brochure PDF
The following slide exhibits measuring the different type of risk involved in the real estate business. The risks highlighted in the slide are administrative, business email compromise, web based attack, adapting to technology trends and phishing attack. Slidegeeks is here to make your presentations a breeze with Analyzing The Real Estate Risk With Major Consequences Enhancing Process Improvement By Regularly Brochure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
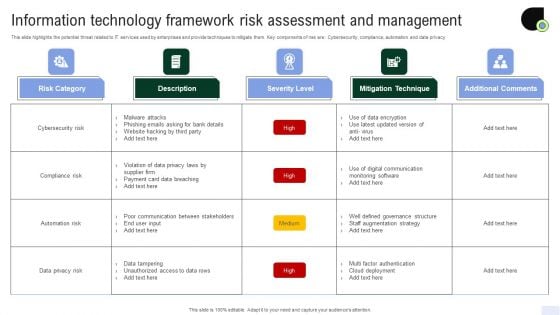
Information Technology Framework Risk Assessment And Management Diagrams PDF
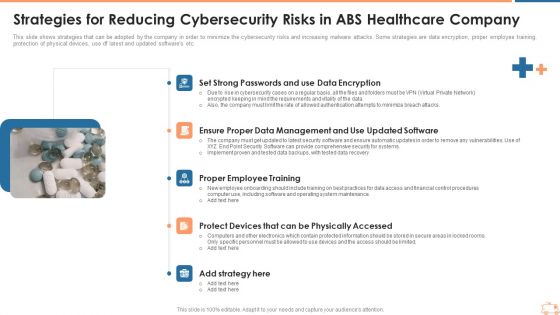
Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Rules PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Presenting strategies for reducing cybersecurity risks in abs healthcare company rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like set strong passwords and use data encryption, proper employee training, protect devices that can be physically accessed, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Gallery Background Images PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Deliver an awe inspiring pitch with this creative strategies for reducing cybersecurity risks in abs healthcare company ppt gallery background images pdf bundle. Topics like set strong passwords and use data encryption, ensure proper data management and use updated software, proper employee training, protect devices that can be physically accessed, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Professional Mockup PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. This is a strategies for reducing cybersecurity risks in ABS healthcare company ppt professional mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data management, operating system maintenance, financial, protect devices that can be physically accessed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































