Cyber Security Attack

Iot Device Management Overview And Requirements Iot Device Management Rules Pdf
This slide exhibits an overview and needs of IoT device management to protect confidential information from potential breaches. It covers the increase in the number of cyber attacks, data breaches attack, etc. Get a simple yet stunning designed Iot Device Management Overview And Requirements Iot Device Management Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Device Management Overview And Requirements Iot Device Management Rules Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits an overview and needs of IoT device management to protect confidential information from potential breaches. It covers the increase in the number of cyber attacks, data breaches attack, etc.

Digital Application Software Development Business Profile SWOT Analysis Structure PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth This Digital Application Software Development Business Profile SWOT Analysis Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
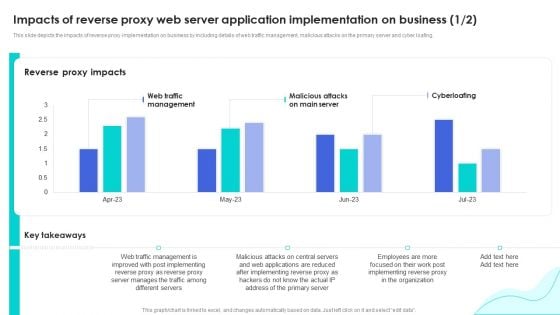
Reverse Proxy Web Server Impacts Of Reverse Proxy Web Server Application Inspiration PDF
This slide depicts the impacts of reverse proxy implementation on business by including details of web traffic management, malicious attacks on the primary server and cyber loafing. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Reverse Proxy Web Server Impacts Of Reverse Proxy Web Server Application Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF
This slide depicts the problems faced by the company such as cyber loafing, malicious attacks on main server and increase in web traffic. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Reverse Proxy Web Server Problems Faced By Company Ppt Slides Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Digital Products Company Outline SWOT Analysis Diagrams PDF
The slide showcases strength, opportunity, weakness and threats of company to estimate companys future prospects. It highlights major points which are company customer base, employee attrition rate, cyber attacks and cloud services growth. Find highly impressive Digital Products Company Outline SWOT Analysis Diagrams PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Products Company Outline SWOT Analysis Diagrams PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
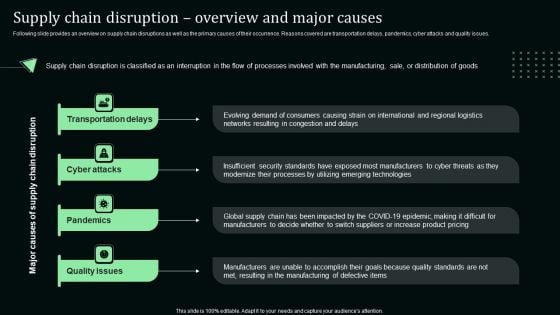
Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Supply Chain Disruption Overview And Major Causes Stand Out Digital Supply Chain Tactics Enhancing Slides PDF

Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF
Following slide provides an overview on supply chain disruptions as well as the primary causes of their occurrence. Reasons covered are transportation delays, pandemics, cyber attacks and quality issues. Get a simple yet stunning designed Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Strategies For Dynamic Supply Chain Agility Supply Chain Disruption Overview And Major Causes Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
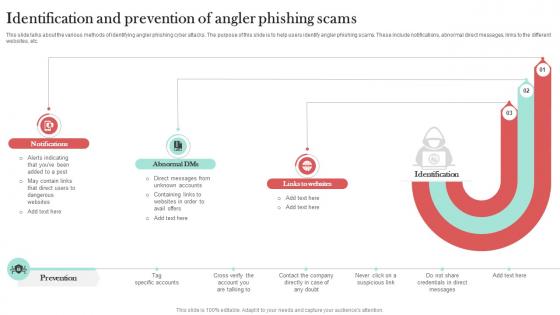
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc.
Key Ways Of Incident Response Planning With Human Observations Ppt PowerPoint Presentation File Sample PDF
Persuade your audience using this key ways of incident response planning with human observations ppt powerpoint presentation file sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including physical alarm, cyber attack, human observations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Operational Risks Events Forecasting In 2021 Ppt PowerPoint Presentation Ideas Picture PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.Deliver an awe-inspiring pitch with this creative operational risks events forecasting in 2021 ppt powerpoint presentation ideas picture pdf. bundle. Topics like operational risks events forecasting in 2021 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
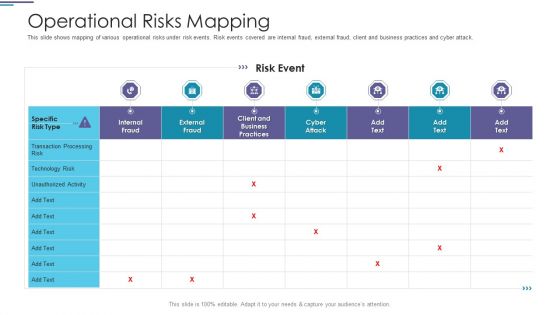
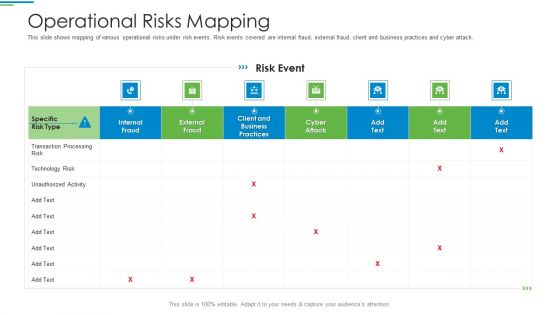
Operational Risks Mapping Ppt PowerPoint Presentation Ideas Graphics Example PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack.Deliver and pitch your topic in the best possible manner with this operational risks mapping ppt powerpoint presentation ideas graphics example pdf. Use them to share invaluable insights on transaction processing, technology risk, client and business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
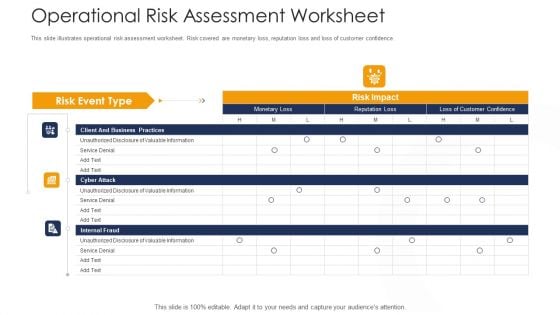
Strategies To Tackle Operational Risk In Banking Institutions Operational Risk Assessment Worksheet Elements PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative strategies to tackle operational risk in banking institutions operational risk assessment worksheet elements pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
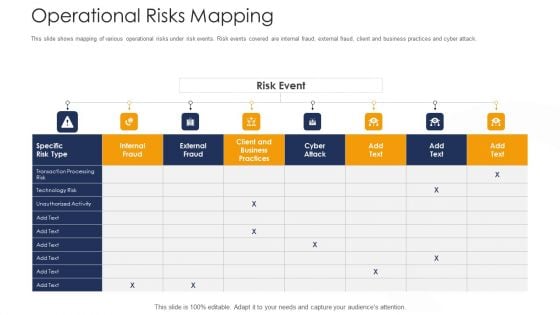
Strategies To Tackle Operational Risk In Banking Institutions Operational Risks Mapping Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative strategies to tackle operational risk in banking institutions operational risks mapping graphics pdf bundle. Topics like technology risk, transaction processing risk, client and business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

OP Risk Management Operational Risk Assessment Worksheet Microsoft PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative op risk management operational risk assessment worksheet microsoft pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiating Hazard Managing Structure Firm Operational Risk Assessment Worksheet Rules PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risk assessment worksheet rules pdf bundle. Topics like business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
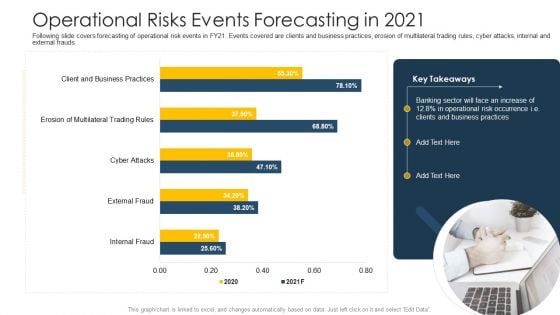
Establishing Operational Risk Framework Banking Operational Risks Events Forecasting In 2021 Portrait PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this establishing operational risk framework banking operational risks events forecasting in 2021 portrait pdf. Use them to share invaluable insights on business practices, operational risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Establishing Operational Risk Framework Banking Operational Risks Mapping Ppt File Icon PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe-inspiring pitch with this creative establishing operational risk framework banking operational risks mapping ppt file icon pdf bundle. Topics like client and business practices, technology risk, transaction processing risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Redundant Array Of Independent Disks Storage IT Checklist To Implement RAID In Business Formats PDF
This slide depicts the checklist to implement RAID in business describing guidelines to follow while implementing RAID. Deliver an awe inspiring pitch with this creative redundant array of independent disks storage it checklist to implement raid in business formats pdf bundle. Topics like organization, implement, cyber attacks, budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Risk Management Structure In Financial Companies Operational Risk Assessment Worksheet Introduction PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risk assessment worksheet introduction pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Operational Risk Management Structure In Financial Companies Operational Risks Mapping Summary PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative operational risk management structure in financial companies operational risks mapping summary pdf bundle. Topics like transaction processing risk, technology risk, unauthorized activity, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
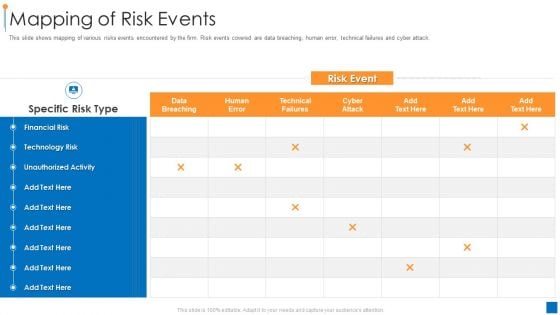
International Organization Standardization 270001 Mapping Of Risk Events Slides PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative international organization standardization 270001 mapping of risk events slides pdf bundle. Topics like financial risk, technology risk, unauthorized activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
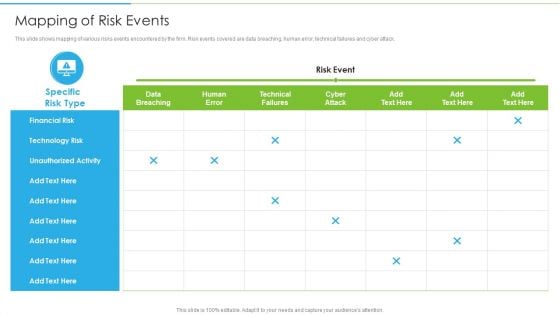
Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF bundle. Topics like Financial Risk, Technology Risk, Unauthorized Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
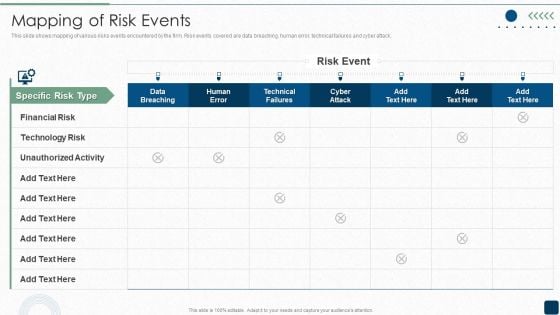
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
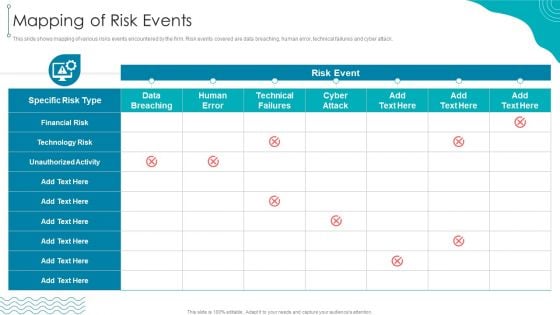
ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
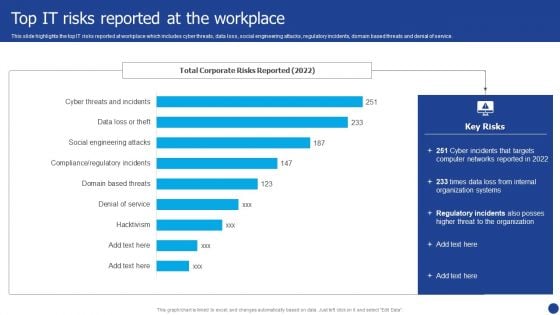
Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Top IT Risks Reported At The Workplace Portrait PDF bundle. Topics like Organization Systems, Networks, Internal can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
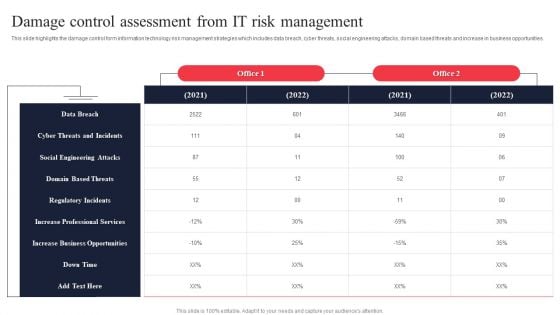
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
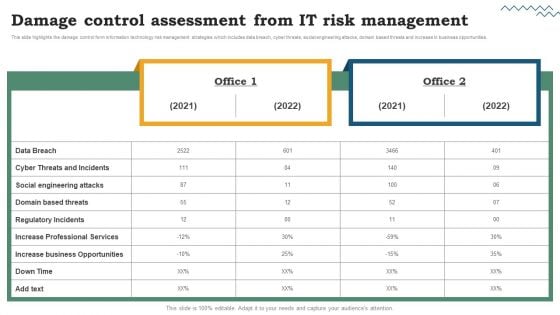
Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
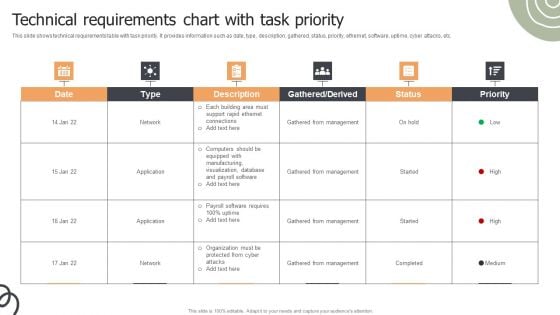
Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF
This slide shows technical requirements table with task priority. It provides information such as date, type, description, gathered, status, priority, ethernet, software, uptime, cyber attacks, etc. Pitch your topic with ease and precision using this Technical Requirements Chart With Task Priority Ppt Infographics Styles PDF. This layout presents information on Gathered From Management, Network, Application. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
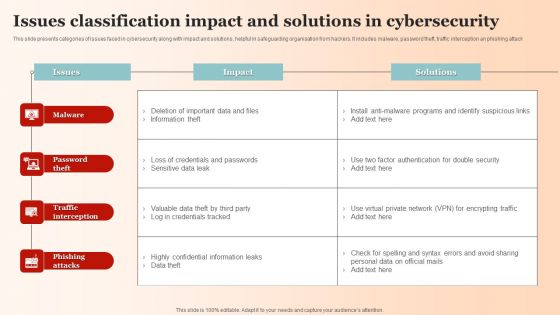
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
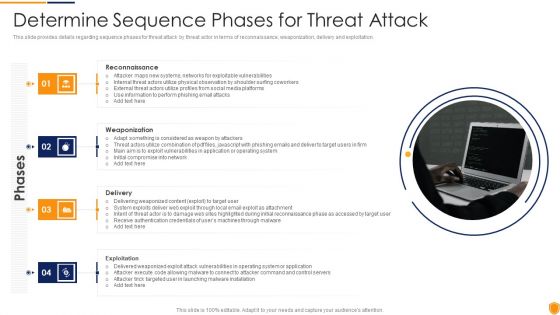
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Estate Development Project Prioritization Slide Download PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Slide Download PDF. Use them to share invaluable insights on Ransomware, Phishing, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Estate Development Project Prioritization Contd Managing Commercial Property Risks Mockup PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide.Deliver and pitch your topic in the best possible manner with this Real Estate Development Project Prioritization Contd Managing Commercial Property Risks Mockup PDF. Use them to share invaluable insights on Ransomware, Business Compromise, Management Response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
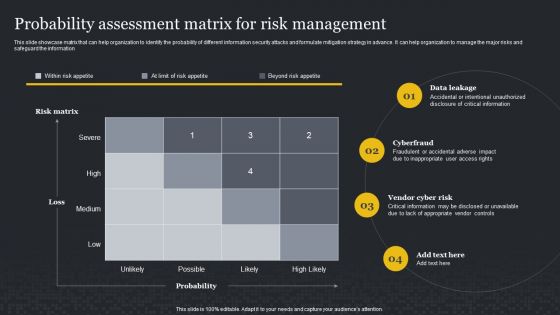
Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Understanding The Process Of E Mail Man In The Middle Phishing IT
This slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Understanding The Process Of E Mail Man In The Middle Phishing IT from Slidegeeks and deliver a wonderful presentation. This slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc.
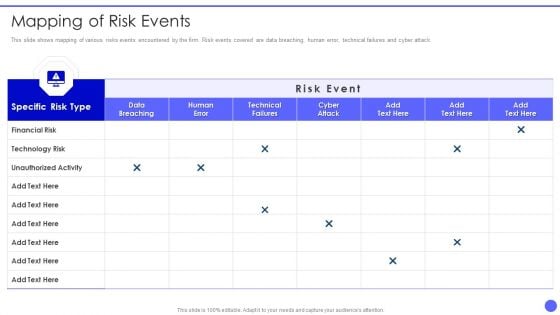
Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Mapping Of Risk Events Ppt PowerPoint Presentation Gallery Design Templates PDF. Use them to share invaluable insights on Specific Risk Type, Financial Risk, Technology Risk, Unauthorized Activity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
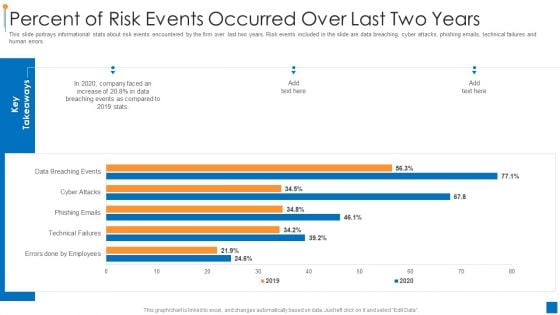
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
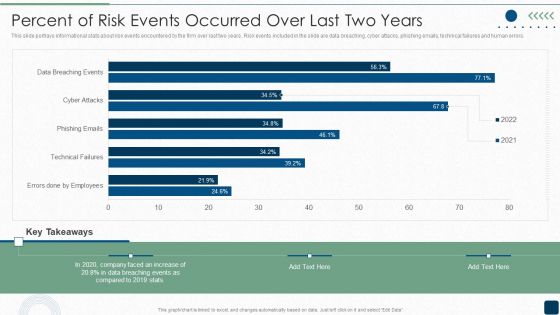
Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Roles And Responsibilities For Managing Operational Risk Slides PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.This is a roles and responsibilities for managing operational risk slides pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
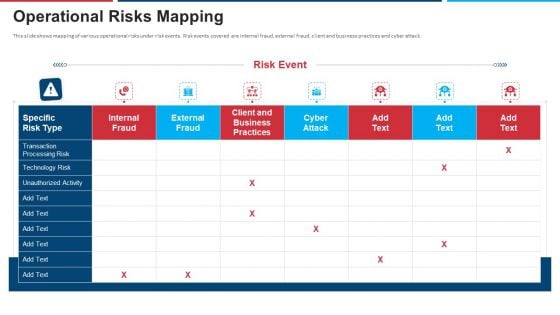
Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
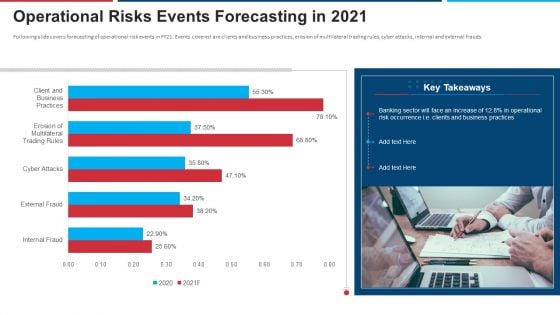
Mitigation Strategies For Operational Threat Operational Risks Events Forecasting In 2021 Ppt Infographic Template Microsoft PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks events forecasting in 2021 ppt infographic template microsoft pdf. Use them to share invaluable insights on banking, operational risk, occurrence, business and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Risk Management Structure In Financial Companies Roles And Responsibilities For Managing Operational Risk Topics PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. This is a operational risk management structure in financial companies roles and responsibilities for managing operational risk topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like board of directors, risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
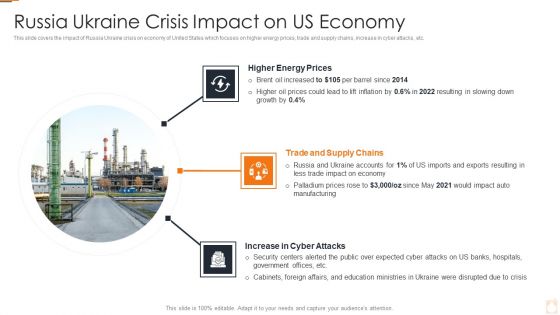
Ukraine Russia Conflict Effect On Petroleum Industry Russia Ukraine Crisis Summary PDF
This slide covers the impact of Russia Ukraine crisis on economy of United States which focuses on higher energy prices, trade and supply chains, increase in cyber attacks, etc.Presenting Ukraine Russia Conflict Effect On Petroleum Industry Russia Ukraine Crisis Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Russian Crude Oil Exports To China In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Analysis Of Phishing And Simulation Training Program Tools Professional PDF
This slide covers comparative analysis of phishing and simulation training tools. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis Of Phishing And Simulation Training Program Tools Professional PDF. The topics addressed in these templates are Assess Employees, Price, User Rating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
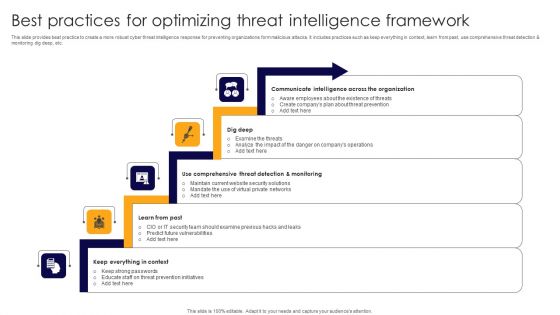
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
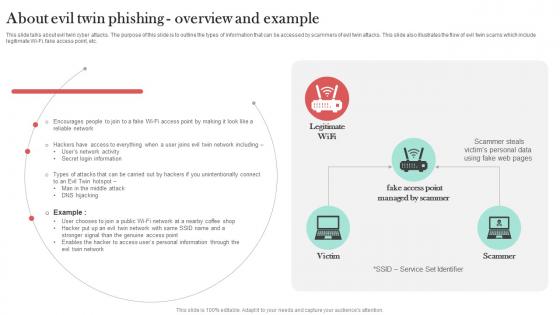
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc.
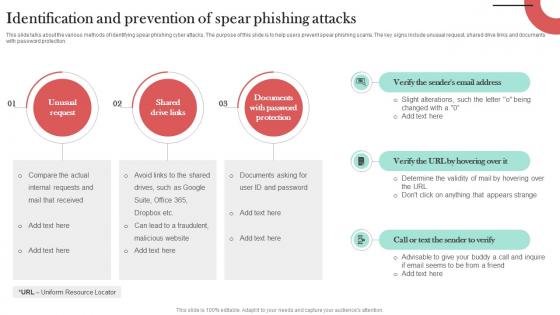
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.
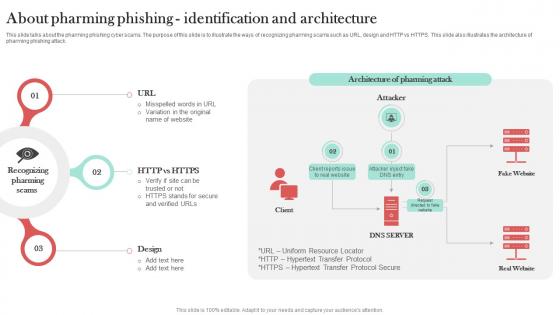
About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.

Successful Risk Administration Real Estate Development Project Prioritization Slides PDF
The following slide exhibits various types of cybersecurity risk faced by the real estate company. Ransomware, phishing, web-based attack and business email compromise are some of the major risks which are mentioned in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Successful Risk Administration Real Estate Development Project Prioritization Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Successful Risk Administration Real Estate Development Project Prioritization Slides PDF.
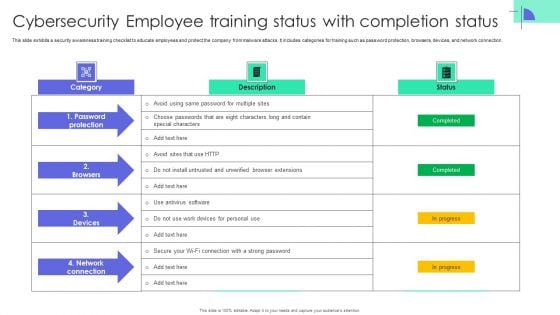
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
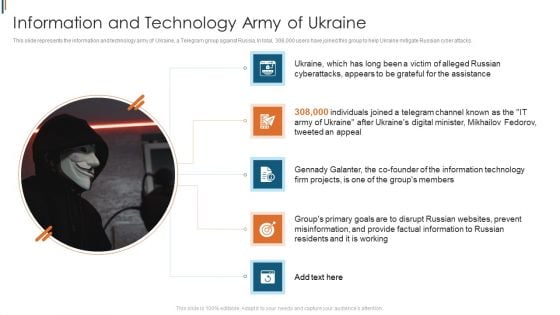
Ukraine Cyberwarfare Information And Technology Army Of Ukraine Topics Pdf
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks. Presenting ukraine cyberwarfare information and technology army of ukraine topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ukraine, which has long been a victim of alleged russian cyberattacks, appears to be grateful for the assistance, gennady galanter, the co founder of the information technology firm projects, is one of the groups members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
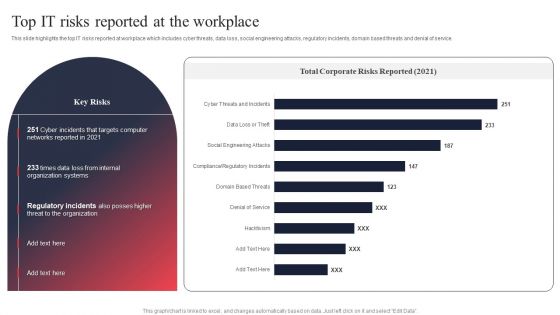
IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT System Risk Management Guide Top IT Risks Reported At The Workplace Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
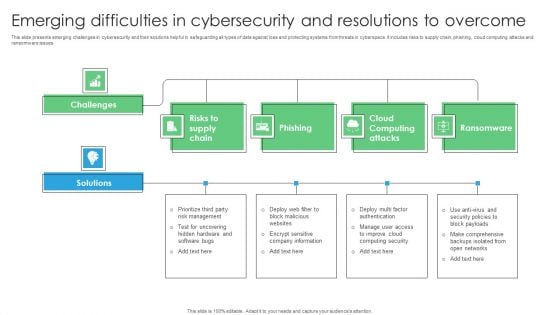
Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF
This slide presents emerging challenges in cybersecurity and their solutions helpful in safeguarding all types of data against loss and protecting systems from threats in cyberspace. It includes risks to supply chain, phishing, cloud computing attacks and ransomware issues. Introducing Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF. to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risks Supply Chain, Phishing, Cloud Computing Attacks, using this template. Grab it now to reap its full benefits.

Cybersecurity Dashboard For ABS Healthcare Company Ppt Themes PDF
This slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Presentingcybersecurity dashboard for abs healthcare company ppt themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like phishing attacks 2021, records stolen 2021, malware cases resolved 2021, malware attacks 2021, hacking incidents 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
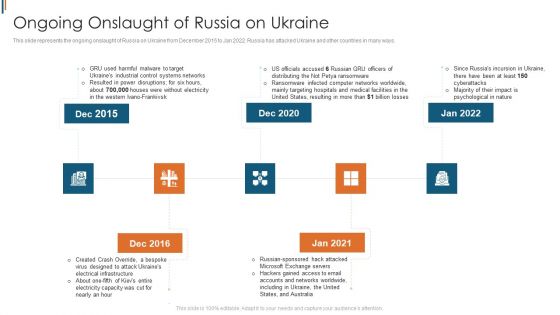
Ukraine Cyberwarfare Ongoing Onslaught Of Russia On Ukraine Brochure Pdf
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. Presenting ukraine cyberwarfare ongoing onslaught of russia on ukraine brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like russian sponsored hack attacked microsoft exchange servers, hackers gained access to email accounts and networks worldwide, including in ukraine, the united states, and australia. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download

Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF
The following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Get a simple yet stunning designed Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Select Cybersecurity Training Program Courses Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
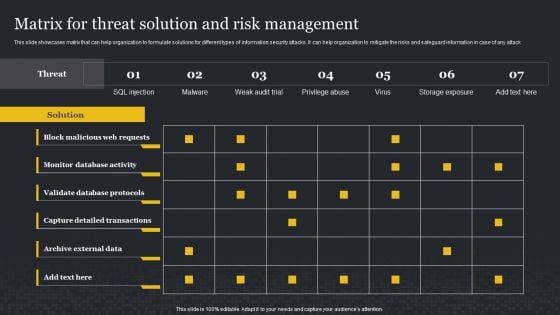
Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Get a simple yet stunning designed Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Matrix For Threat Solution And Risk Management Cybersecurity Risk Assessment Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
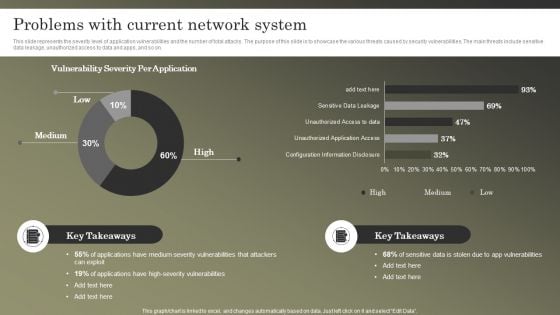
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.


 Continue with Email
Continue with Email

 Home
Home


































