Data Protection
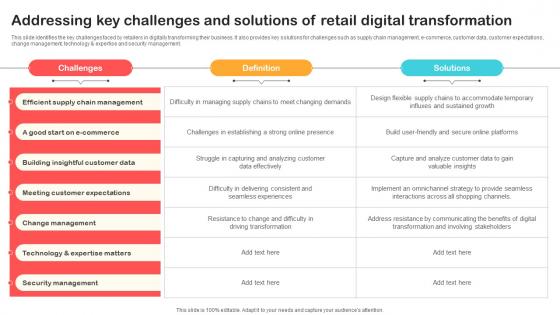
Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.
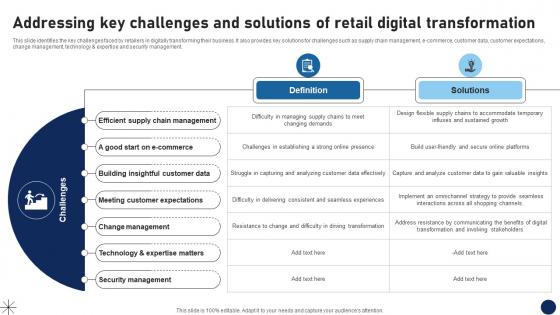
Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.

Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide
This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc. Find highly impressive Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc.
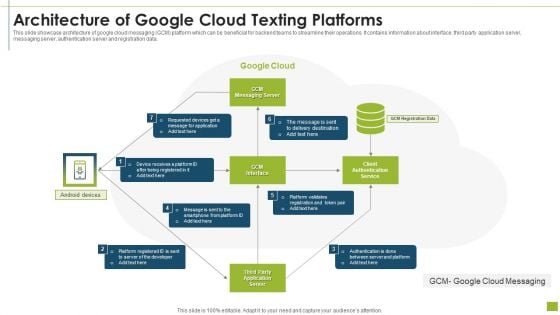
Architecture Of Google Cloud Texting Platforms Demonstration PDF
This slide showcase architecture of google cloud messaging GCM platform which can be beneficial for backend teams to streamline their operations. It contains information about interface, third party application server, messaging server, authentication server and registration data.Showcasing this set of slides titled architecture of google cloud texting platforms demonstration pdf The topics addressed in these templates are authentication is done between, server and platform, client authentication service All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
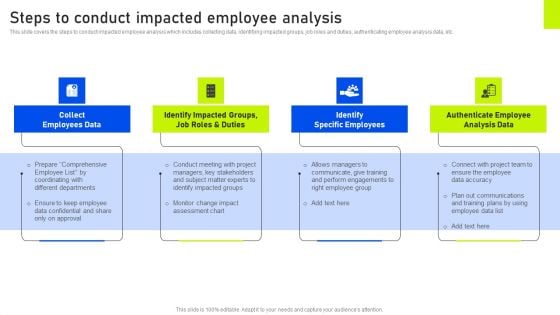
Steps To Conduct Impacted Employee Analysis Ppt Gallery Example Introduction PDF
This slide covers the steps to conduct impacted employee analysis which includes collecting data, identifying impacted groups, job roles and duties, authenticating employee analysis data, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Steps To Conduct Impacted Employee Analysis Ppt Gallery Example Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Steps To Conduct Impacted Employee Analysis Ppt Gallery Example Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Transition Plan For Business Management Steps To Conduct Impacted Employee Analysis Clipart PDF
This slide covers the steps to conduct impacted employee analysis which includes collecting data, identifying impacted groups, job roles and duties, authenticating employee analysis data, etc. Retrieve professionally designed Transition Plan For Business Management Steps To Conduct Impacted Employee Analysis Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
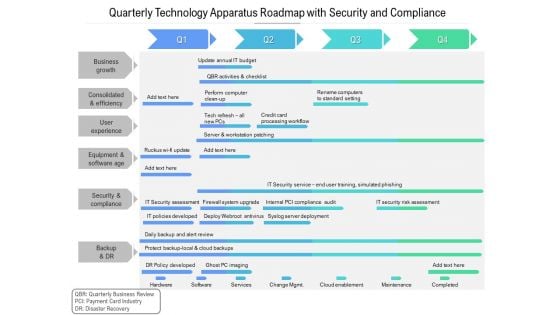
Quarterly Technology Apparatus Roadmap With Security And Compliance Rules
Presenting the quarterly technology apparatus roadmap with security and compliance rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Components Of Information And Communication Technology Telecommunications Formats Pdf
This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi. There are so many reasons you need a Components Of Information And Communication Technology Telecommunications Formats Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi.
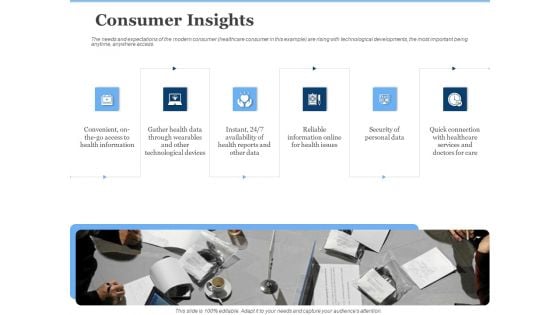
Generate Digitalization Roadmap For Business Consumer Insights Pictures PDF
This is a generate digitalization roadmap for business consumer insights pictures pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of personal data, convenient, on the go access to health information, reliable information online for health issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why Organizations Recruit Ethical Hackers Ppt Slides Smartart PDF
This is a why organizations recruit ethical hackers ppt slides smartart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information systems, security, measures, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
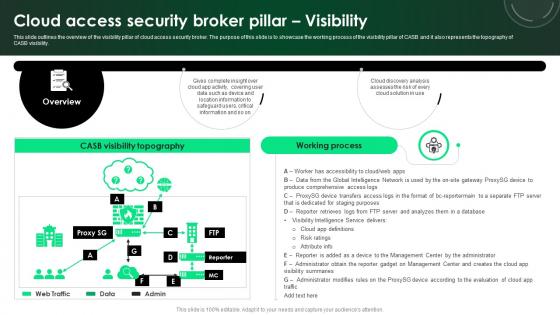
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.
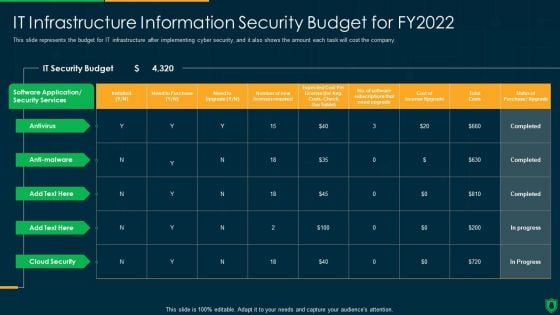
Info Security IT Infrastructure Information Security Budget For FY2022 Ppt PowerPoint Presentation File Pictures PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative info security it infrastructure information security budget for fy2022 ppt powerpoint presentation file pictures pdf bundle. Topics like it security budget, security services, cost license upgrade can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Multiple Device Based Internet Of Things Security Icon Formats Pdf
Showcasing this set of slides titled Multiple Device Based Internet Of Things Security Icon Formats Pdf The topics addressed in these templates are Multiple Device Based, Internet Of Things, Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Multiple Device Based Internet Of Things Security Icon Formats Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf
Showcasing this set of slides titled Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf. The topics addressed in these templates are Unauthorized Computer, Access, Causing Virtual Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
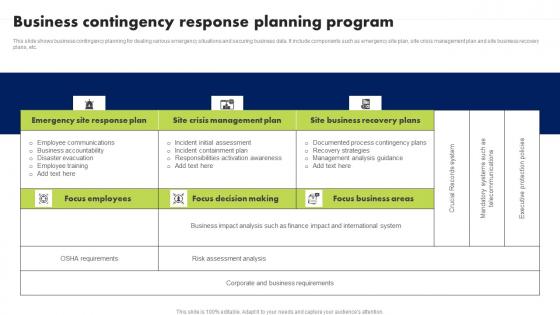
Business Contingency Response Planning Program Formats Pdf
This slide shows business contingency planning for dealing various emergency situations and securing business data. It include components such as emergency site plan, site crisis management plan and site business recovery plans, etc. Pitch your topic with ease and precision using this Business Contingency Response Planning Program Formats Pdf. This layout presents information on Focus Employees, Focus Decision Making. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows business contingency planning for dealing various emergency situations and securing business data. It include components such as emergency site plan, site crisis management plan and site business recovery plans, etc.
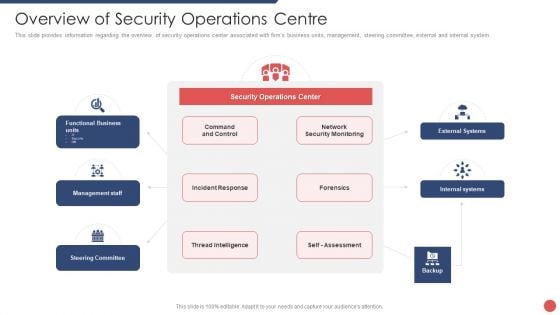
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
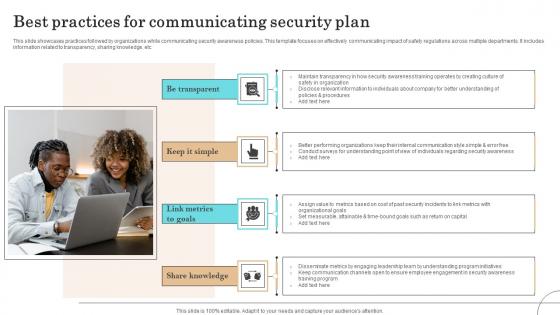
Best Practices For Communicating Security Plan Infographics Pdf
This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc Pitch your topic with ease and precision using this Best Practices For Communicating Security Plan Infographics Pdf This layout presents information on Measurable Attainable, Keep Communication, Maintain Transparency It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc

Digital Wallet Transaction Process Workflow In Depth Guide To Digital Wallets Fin SS V
This slide explains the transaction process of a digital wallet and helps to understand the payment flow from customer to merchant. The various steps involved are Payment initiation, Securing financial data, payment status notification, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Digital Wallet Transaction Process Workflow In Depth Guide To Digital Wallets Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide explains the transaction process of a digital wallet and helps to understand the payment flow from customer to merchant. The various steps involved are Payment initiation, Securing financial data, payment status notification, etc.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
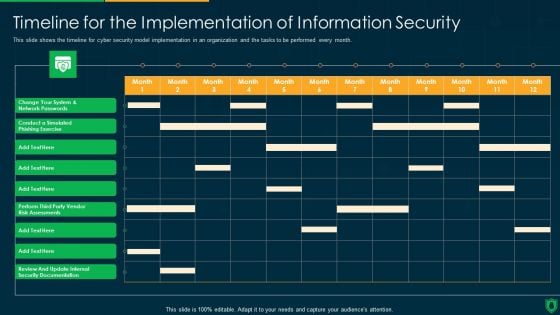
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
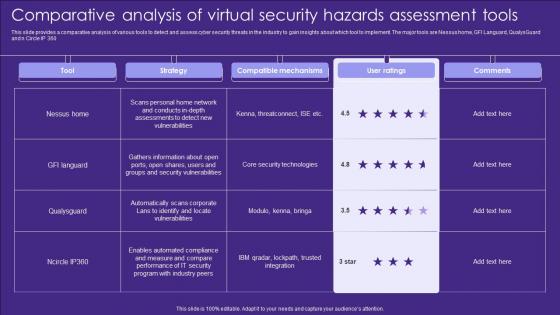
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360
Cyber Security Breach Icon To Prevent Threat Brochure Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon To Prevent Threat Brochure Pdf This layout presents information on Cyber Security Breach, Icon To Prevent Threat It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon To Prevent Threat Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
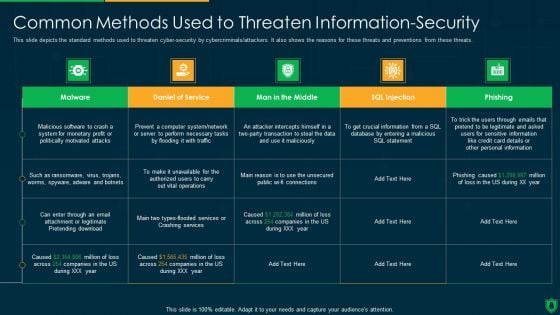
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Password Vault Web Access In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Password Vault Web Access In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Password Vault Web Access that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Password Vault Web Access In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Specific Password In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Application Specific Password In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Specific Password that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Specific Password In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
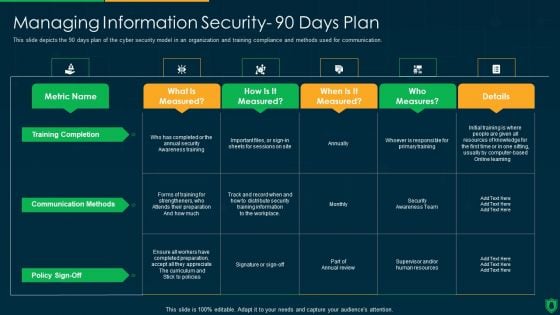
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
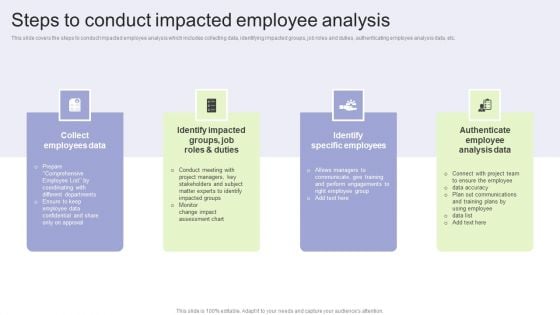
Implementing Change Management Strategy To Transform Business Processes Steps To Conduct Impacted Themes PDF
This slide covers the steps to conduct impacted employee analysis which includes collecting data, identifying impacted groups, job roles and duties, authenticating employee analysis data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Change Management Strategy To Transform Business Processes Steps To Conduct Impacted Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Change Management Strategy To Transform Business Processes Steps To Conduct Impacted Themes PDF today and make your presentation stand out from the rest.

Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This modern and well-arranged Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Electronic Initiative For International Commerce Business Infographics PDF
This slide contains the initiatives for ecommerce business to expand globally. It includes ace, national trade platforms, skill framework, etc. Persuade your audience using this Electronic Initiative For International Commerce Business Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Secure Data, Productivity, Retail. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
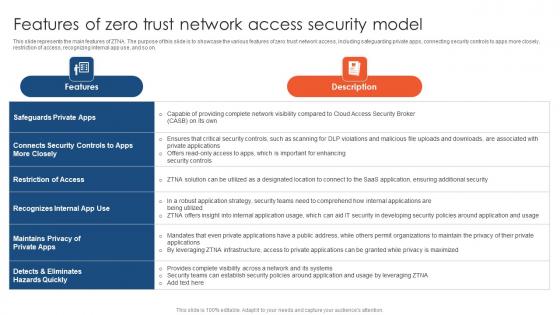
Zero Trust Network Access Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Slidegeeks has constructed Zero Trust Network Access Features Of Zero Trust Network Access Security Model after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
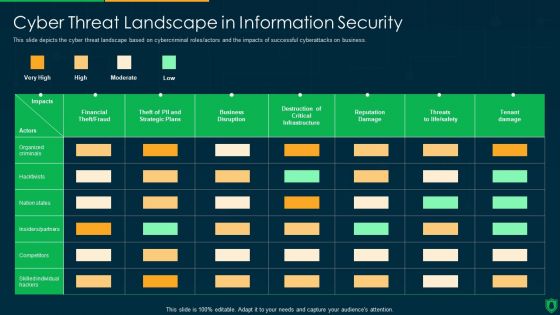
Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
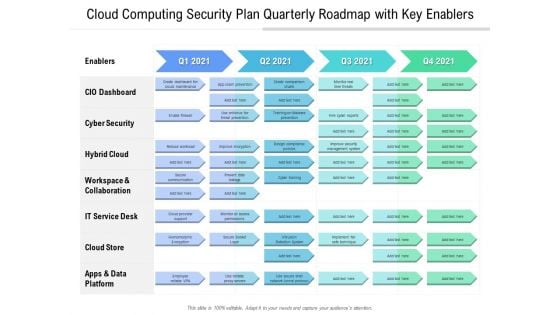
Cloud Computing Security Plan Quarterly Roadmap With Key Enablers Information
Introducing our cloud computing security plan quarterly roadmap with key enablers information. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Networking Events Steps To Prepare Successful Conference Meeting Clipart PDF
This slide provides an overview of the process followed to create conference meetings. Major steps covered ae planning, finalizing speakers, creating agenda, beginning registrations, promoting conferences and focusing on attendee engagement. The Networking Events Steps To Prepare Successful Conference Meeting Clipart PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
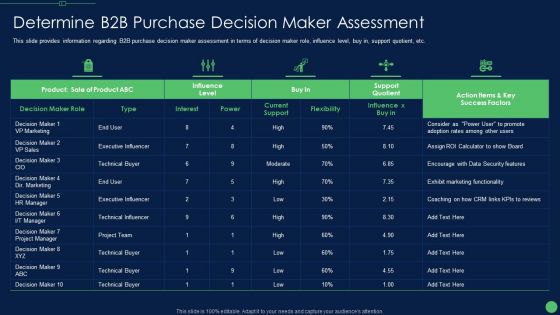
Most Effective Sales Enablement Strategies For B2B Marketers Determine B2B Purchase Decision Diagrams PDF
This slide provides information regarding B2B purchase decision maker assessment in terms of decision maker role, influence level, buy in, support quotient, etc. Deliver an awe inspiring pitch with this creative most effective sales enablement strategies for b2b marketers determine b2b purchase decision diagrams pdf bundle. Topics like encourage with data, exhibit marketing functionality, security features can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
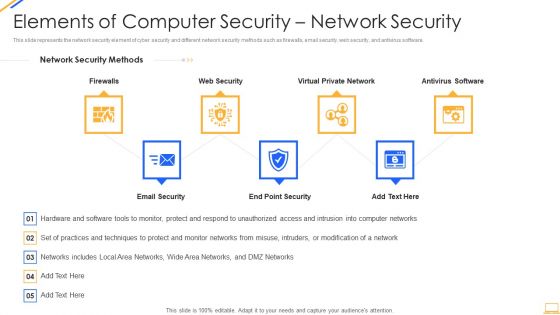
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
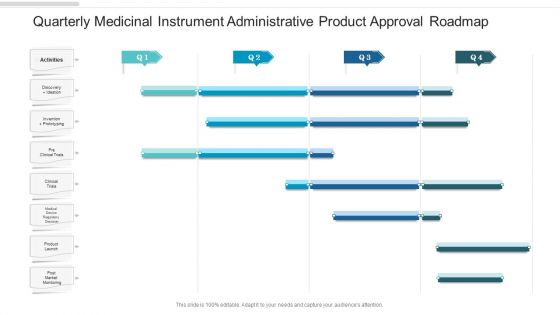
Quarterly Medicinal Instrument Administrative Product Approval Roadmap Template
We present our quarterly medicinal instrument administrative product approval roadmap template. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly medicinal instrument administrative product approval roadmap template in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
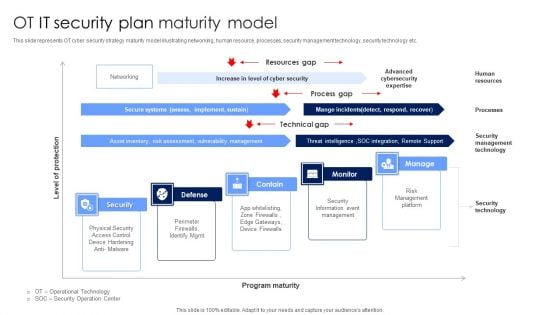
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
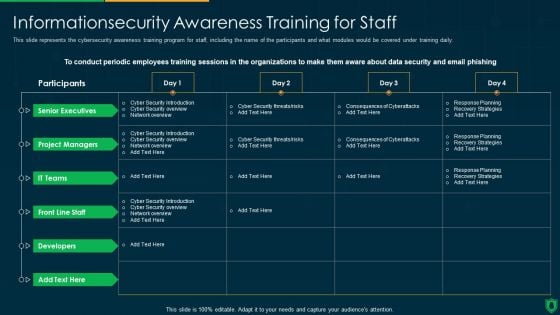
Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.
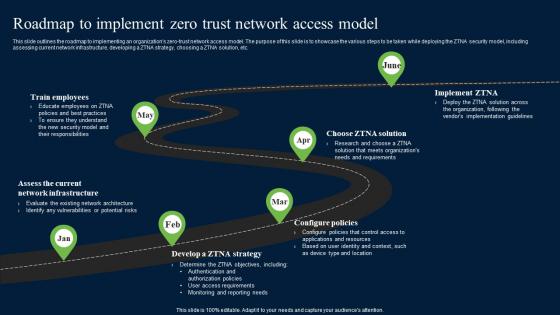
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
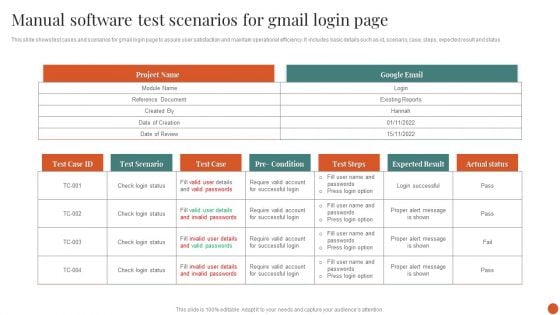
Manual Software Test Scenarios For Gmail Login Page Elements PDF
This slide shows test cases and scenarios for gmail login page to assure user satisfaction and maintain operational efficiency. It includes basic details such as id, scenario, case, steps, expected result and status.Showcasing this set of slides titled Manual Software Test Scenarios For Gmail Login Page Elements PDF. The topics addressed in these templates are Valid Passwords, Invalid Passwords, Successful Login. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
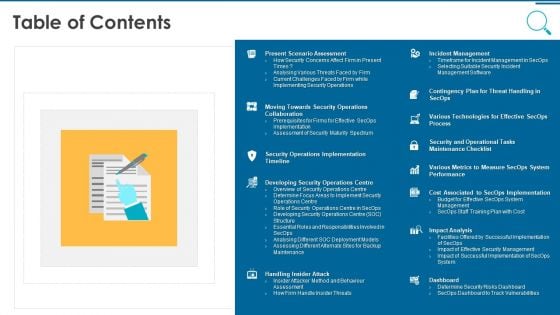
Information And Technology Security Operations Table Of Contents Pictures PDF
This is a information and technology security operations table of contents pictures pdf template with various stages. Focus and dispense information on thirteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, implementation, analysis, technologies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
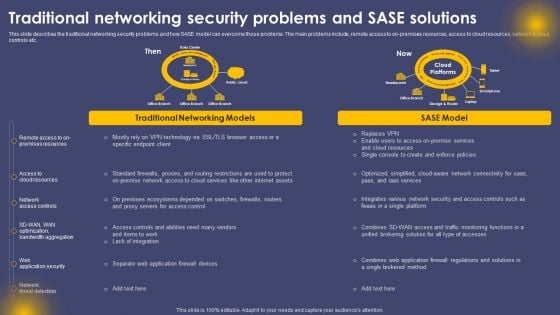
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.

Organizational Network Security Awareness Staff Learning Idea Generation Designs PDF
This is a organizational network security awareness staff learning idea generation designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
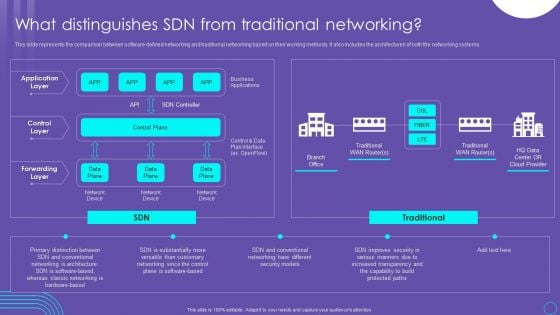
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
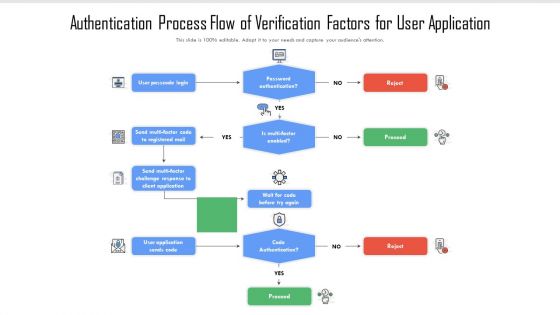
Authentication Process Flow Of Verification Factors For User Application Rules PDF
Pitch your topic with ease and precision using this authentication process flow of verification factors for user application rules pdf. This layout presents information on password authentication, code authentication, user passcode login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
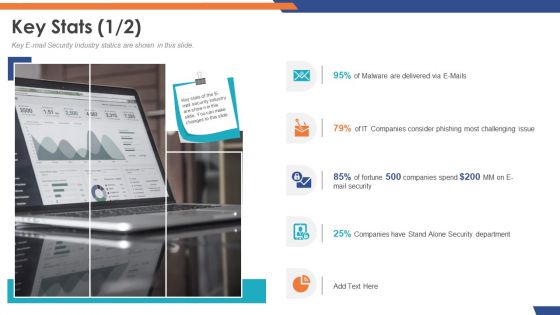
Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Online Technology Security Chip Icon For Network Safety Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this online technology security chip icon for network safety ppt powerpoint presentation file graphics example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online technology security chip icon for network safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.

Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
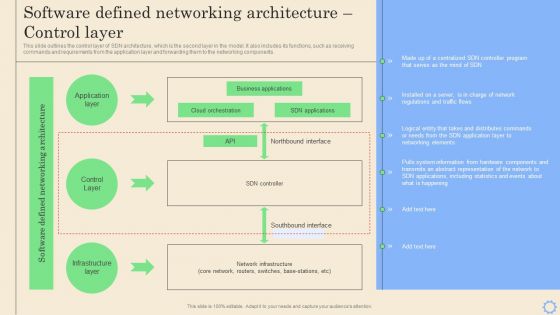
Software Defined Networking Development Strategies Software Defined Networking Architecture Control Layer Portrait PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. The Software Defined Networking Development Strategies Software Defined Networking Architecture Control Layer Portrait PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
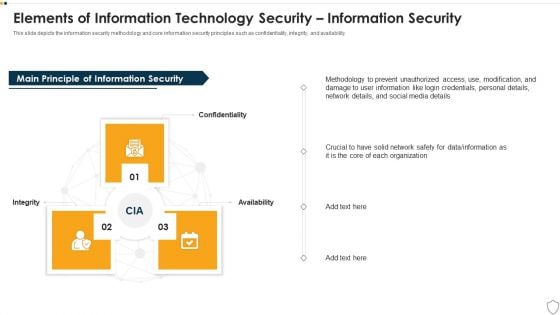
IT Security Elements Of Information Technology Security Information Security Ppt Gallery Grid PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a it security elements of information technology security information security ppt gallery grid pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity, confidentiality, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Virus Alert Computer PowerPoint Backgrounds And Templates 0111
Microsoft PowerPoint Template and Background with confused man about a virus alert computer dialog box Our Virus Alert Computer PowerPoint Backgrounds And Templates 0111 exemplify global awareness. They have taken the best from all cultures.


 Continue with Email
Continue with Email

 Home
Home


































