Data Protection
Info Security Security Of Employees Devices Ppt PowerPoint Presentation Icon Files PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting info security security of employees devices ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
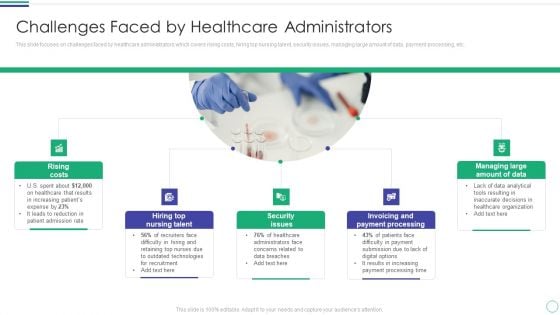
Challenges Faced By Healthcare Administrators Sample PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc.Presenting Challenges Faced By Healthcare Administrators Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Issues, Payment Processing, Managing Large In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
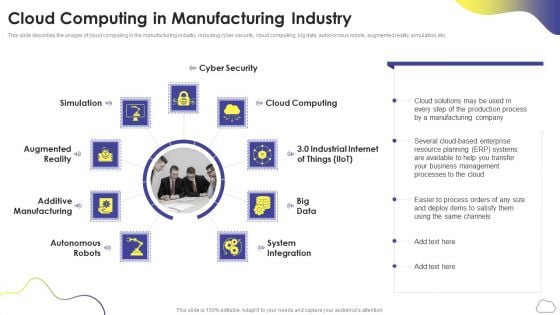
Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. Presenting Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cyber Security, Cloud Computing, System Integration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
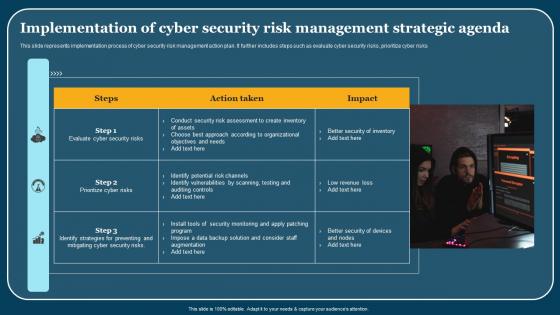
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
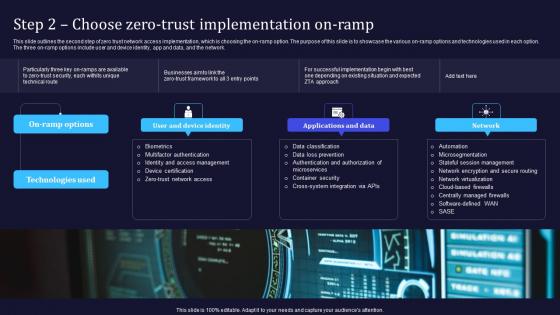
Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Icon For Software Management Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
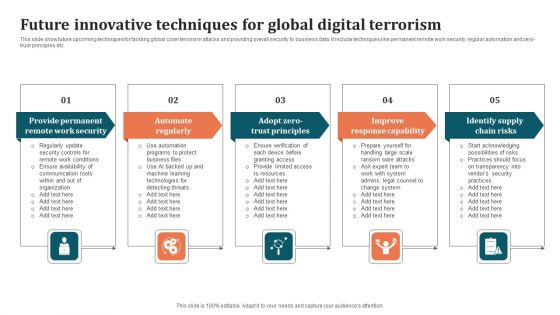
Future Innovative Techniques For Global Digital Terrorism Background PDF
This slide show future upcoming techniques for tackling global cyber terrorism attacks and providing overall security to business data. It include techniques like permanent remote work security, regular automation and zero-trust principles etc. Persuade your audience using this Future Innovative Techniques For Global Digital Terrorism Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Response Capability, Identify Supply Chain Risks, Automate Regularly. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Trends In Customer Finance Market Template PDF
The slide highlights various digital and tech based trends in consumer financing and lending market. It includes key components like better customer experience, enhanced security, greater Omni channel capabilities, Non banking institutions market entry and AI tools. Persuade your audience using this Digital Trends In Customer Finance Market Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate Data, Ensure Security, Lending Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.

Business Development Team Case Study 2 Internet Security Organization SA SS V
This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Development Team Case Study 2 Internet Security Organization SA SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue.
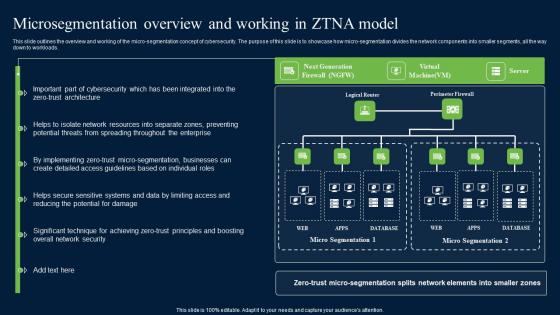
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
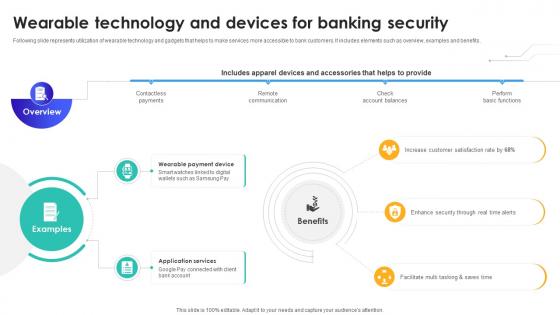
Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V
Following slide represents utilization of wearable technology and gadgets that helps to make services more accessible to bank customers. It includes elements such as overview, examples and benefits. Create an editable Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Wearable Technology And Devices For Banking Security IoT In Banking For Digital Future IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide represents utilization of wearable technology and gadgets that helps to make services more accessible to bank customers. It includes elements such as overview, examples and benefits.
Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
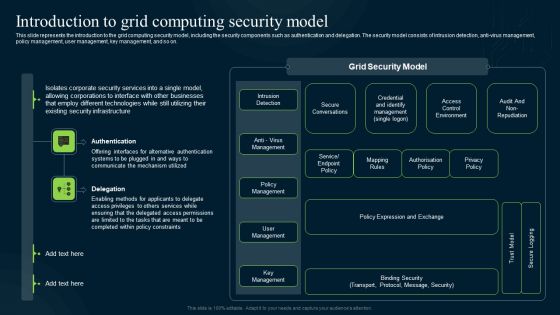
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc.
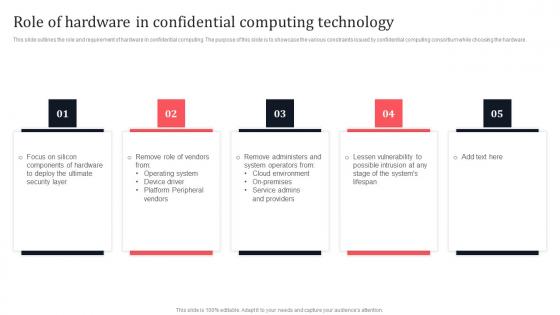
Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf today and make your presentation stand out from the rest. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample
This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Find a pre-designed and impeccable Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc.
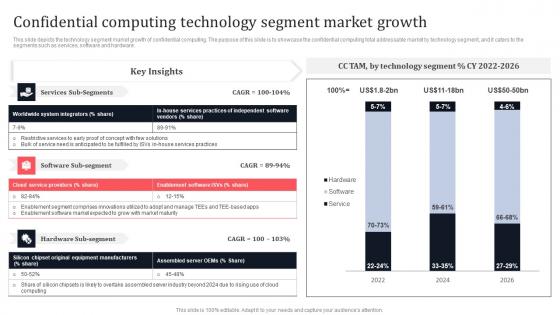
Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. This Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
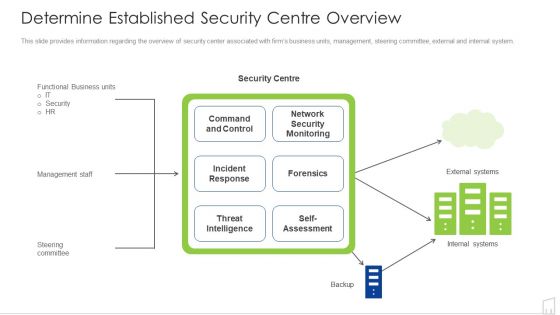
Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Internet Of Things Security Icon For Home Safety Background Pdf
Pitch your topic with ease and precision using this Internet Of Things Security Icon For Home Safety Background Pdf This layout presents information on Internet Of Things Security, Icon For Home Safety It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Of Things Security Icon For Home Safety Background Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
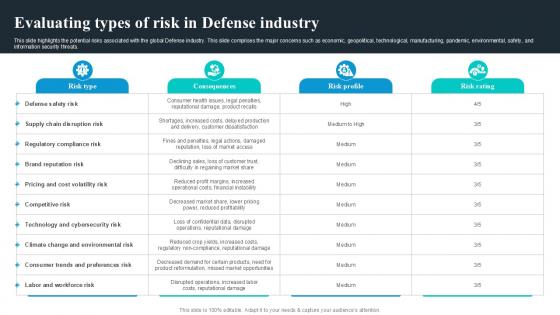
Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V
This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V can be your best option for delivering a presentation. Represent everything in detail using Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats.
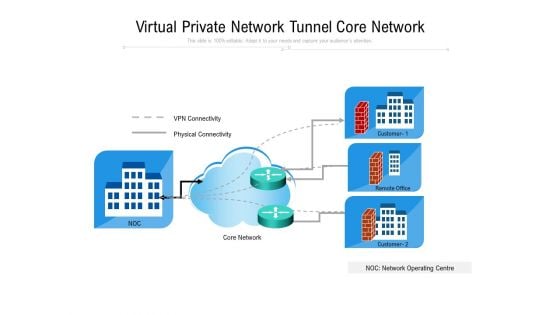
Virtual Private Network Tunnel Core Network Ppt PowerPoint Presentation Gallery Professional PDF
Persuade your audience using this virtual private network tunnel core network ppt powerpoint presentation gallery professional pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network tunnel core network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
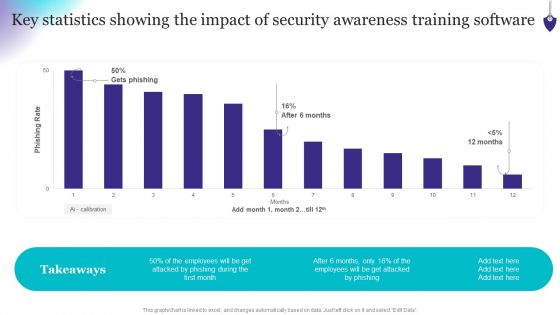
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Devsecops Development Security And Operations Role Of Devsecops Ppt Template
This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Find highly impressive Devsecops Development Security And Operations Role Of Devsecops Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Devsecops Development Security And Operations Role Of Devsecops Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system.

Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF. Use them to share invaluable insights on Information Security Policy, Information Security Training, Asset Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
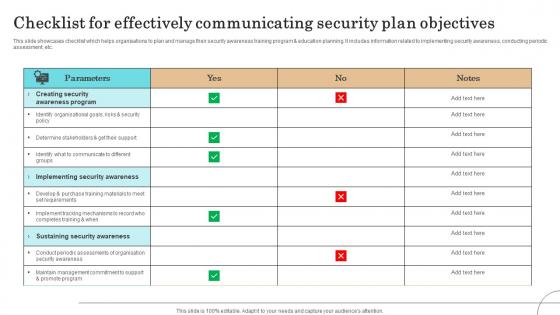
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.

Illustration Of Global Success Key PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Illustration Of Global Success Key PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Globe PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Present our Earth PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Present our Security PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Use our Success PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Use our Future PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Global network with success key, globe, earth, success, future, security. The prominent colors used in the PowerPoint template are Green, Yellow, Gray. Everything falls into place with our Illustration Of Global Success Key PowerPoint Templates Ppt Backgrounds For Slides 0213. They have the correct slots for all your ideas.

Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V
This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results.
Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer. This Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer.
User Clicking On Login Web Based Platform Icon Designs PDF
Pitch your topic with ease and precision using this User Clicking On Login Web Based Platform Icon Designs PDF. This layout presents information on Login Web Based, Platform Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
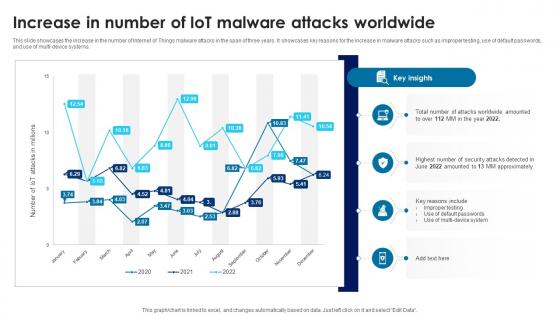
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.

Organizing Security Awareness Statistics Highlighting Lack Of Cyber Security Awareness Guidelines PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. There are so many reasons you need a Organizing Security Awareness Statistics Highlighting Lack Of Cyber Security Awareness Guidelines PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Sales Improvement Strategy With Social Media Marketing Ideas PDF
This slide exhibits methods to increase sales with social media to increase customer base and connect with diverse audience. It includes various tips such as use interactive post, share user generated content, use customer preferred network and use shoppable post. Presenting Sales Improvement Strategy With Social Media Marketing Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Design Attractive, Generated Data, Customer Preferred Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cover Letter For Cloud Security Firewall Proposal
Take your presentations to the next level with our Cover Letter For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. Cover Letter, Cloud Security Firewall Proposal

Channels Security Service Provider Business Model BMC SS V
This slide showcases key channels of the multinational company to connect with the customers. The channels covered in the slide are website, technical assistance center, social media and customer service. Boost your pitch with our creative Channels Security Service Provider Business Model BMC SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases key channels of the multinational company to connect with the customers. The channels covered in the slide are website, technical assistance center, social media and customer service.
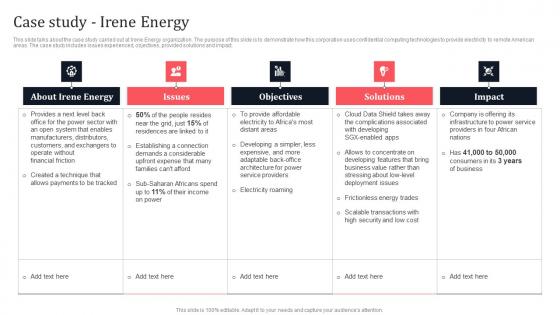
Case Study Irene Energy Secure Multi Party Sample Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Create an editable Case Study Irene Energy Secure Multi Party Sample Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Case Study Irene Energy Secure Multi Party Sample Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
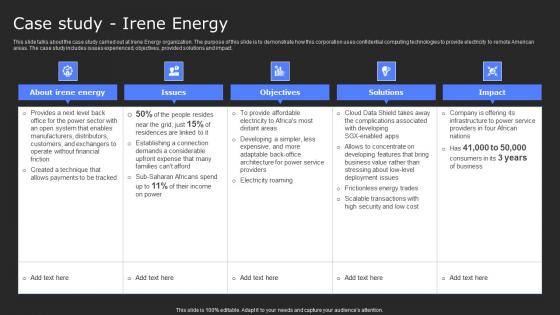
Case Study Irene Energy Secure Computing Framework Ideas Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Secure Computing Framework Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Secure Computing Framework Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
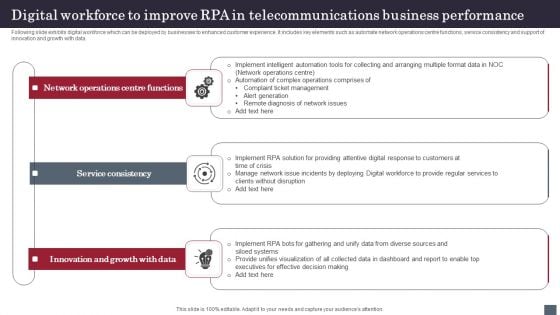
Digital Workforce To Improve RPA In Telecommunications Business Performance Mockup PDF
Following slide exhibits digital workforce which can be deployed by businesses to enhanced customer experience. It includes key elements such as automate network operations centre functions, service consistency and support of innovation and growth with data. Presenting Digital Workforce To Improve RPA In Telecommunications Business Performance Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Operations, Service Consistency, Innovation And Growth. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf
Pitch your topic with ease and precision using this Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf This layout presents information on Cyber Security Device, Icon To Prevent Form Malicious Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Construction Worker Security Checklist Icon Portrait Pdf
Pitch your topic with ease and precision using this Construction Worker Security Checklist Icon Portrait Pdf. This layout presents information on Construction Worker, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Construction Worker Security Checklist Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Food Quality Security Checklist Icon Guidelines Pdf
Pitch your topic with ease and precision using this Food Quality Security Checklist Icon Guidelines Pdf. This layout presents information on Food Quality, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Food Quality Security Checklist Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Web Access Control Solution Integration Of Swg Inside Sase Architecture
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. The Web Access Control Solution Integration Of Swg Inside Sase Architecture is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.

Picture Showing Login Page Ppt PowerPoint Presentation Professional Files
Presenting this set of slides with name picture showing login page ppt powerpoint presentation professional files. This is a one stage process. The stage in this process is picture showing login page. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with security minded digital collage of human profile with key Make your presentations helpful with our Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711. Dont waste time struggling with PowerPoint. Let us do it for you.

Internet Protocol Security PPT Example
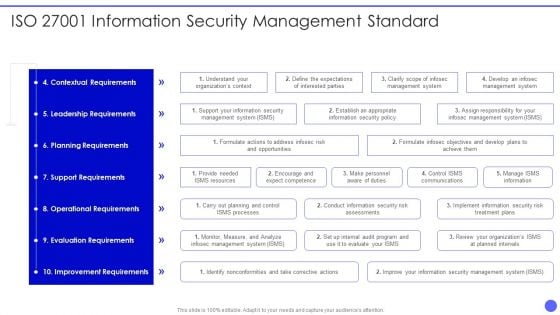
Info Safety And ISO 27001 Information Security Management Standard Download PDF
Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Information Security Management Standard Download PDF. Use them to share invaluable insights on Contextual Requirements, Leadership Requirements, Planning Requirements, Support Requirements, Operational Requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Deals Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Deals Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Deals Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Deals Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Shell Protocol In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Shell Protocol In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Shell Protocol. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Shell Protocol In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
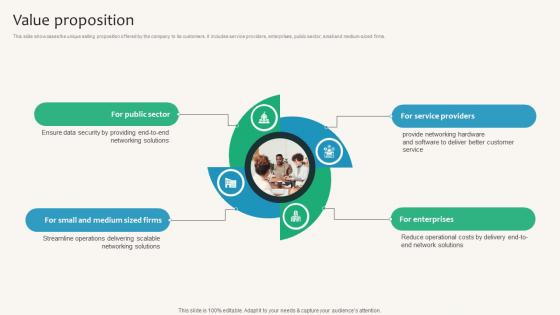
Value Proposition Security Service Provider Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition Security Service Provider Business Model BMC SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Wireless In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
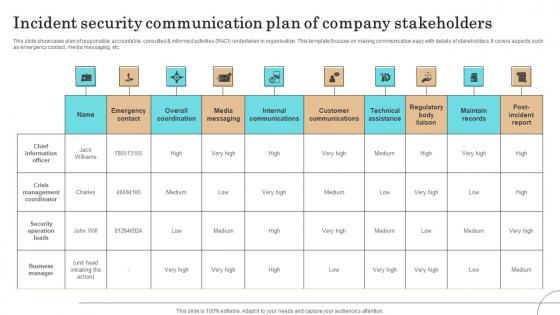
Incident Security Communication Plan Of Company Stakeholders Pictures Pdf
This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.Showcasing this set of slides titled Incident Security Communication Plan Of Company Stakeholders Pictures Pdf The topics addressed in these templates are Crisis Management Coordinator, Security Operation Leads, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.
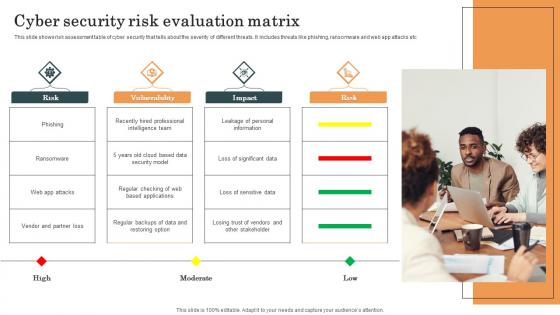
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.

Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
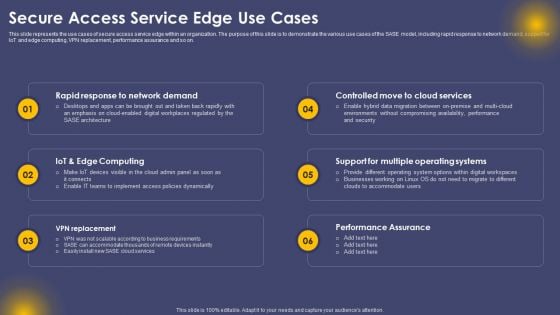
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


 Continue with Email
Continue with Email

 Home
Home


































