Data Protection
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. The Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
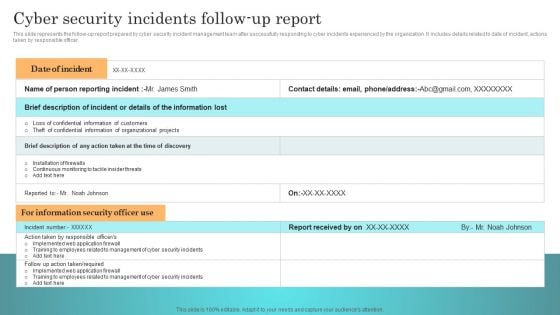
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
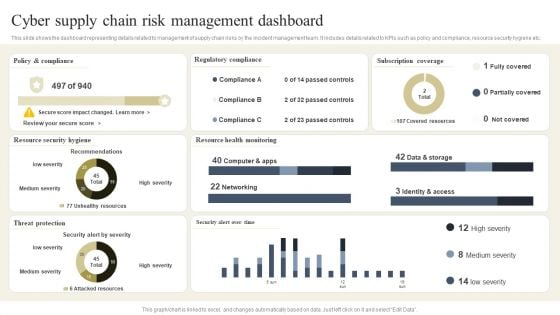
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
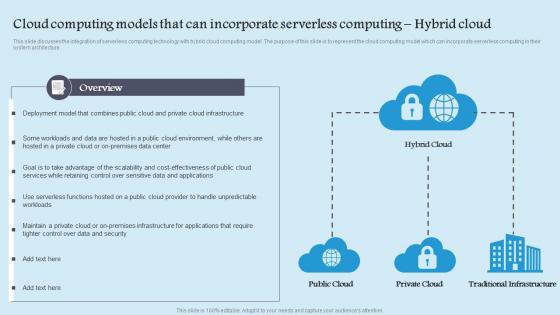
Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf
This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture. This Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture.

Virus Danger Globe PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with virus sign and world map You are considered a multi-faceted person. Add to your charms with our Virus Danger Globe PowerPoint Templates And PowerPoint Backgrounds 0211.

Virus Danger Globe PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with virus sign and world map Failsafe systems are difficult to design. Get to the bottom of it with our Virus Danger Globe PowerPoint Themes And PowerPoint Slides 0211.
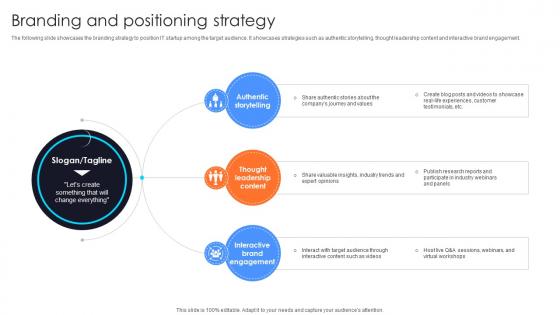
Branding And Positioning Strategy Information Technology Startup Go To Market Strategy GTM SS V
The following slide showcases the branding strategy to position IT startup among the target audience. It showcases strategies such as authentic storytelling, thought leadership content and interactive brand engagement.Boost your pitch with our creative Branding And Positioning Strategy Information Technology Startup Go To Market Strategy GTM SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The following slide showcases the branding strategy to position IT startup among the target audience. It showcases strategies such as authentic storytelling, thought leadership content and interactive brand engagement.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
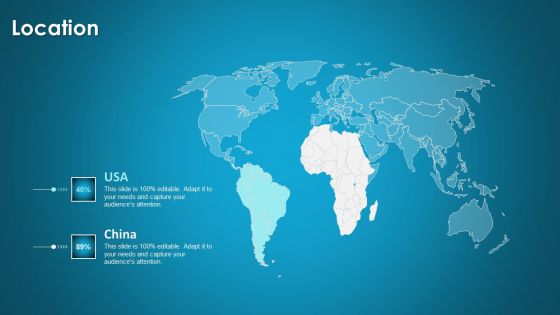
Organizational Network Security Awareness Staff Learning Location Information PDF
Presenting organizational network security awareness staff learning location information pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like location. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
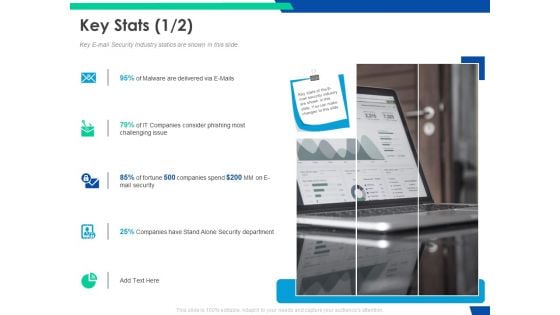
Cloud Based Email Security Market Report Key Stats Department Ppt Outline Brochure PDF
Key E mail Security Industry statics are shown in this slide. This is a cloud based email security market report key stats department ppt outline brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key stats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V
The slide highlights the PESTEL analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external factors on defense market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects. Explore a selection of the finest PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide highlights the PESTEL analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external factors on defense market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects.
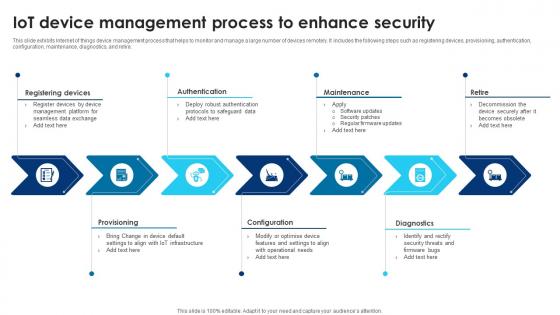
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.
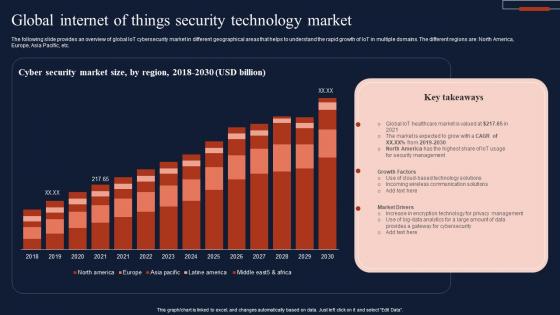
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
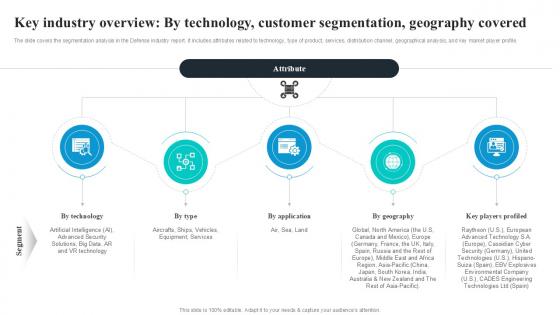
Key Industry Overview By Technology Global Security Industry PPT Template IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Industry Overview By Technology Global Security Industry PPT Template IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Industry Overview By Technology Global Security Industry PPT Template IR SS V The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.
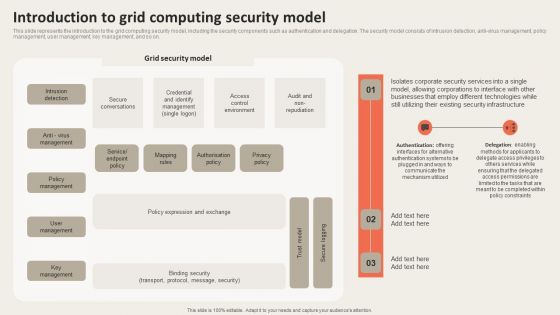
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
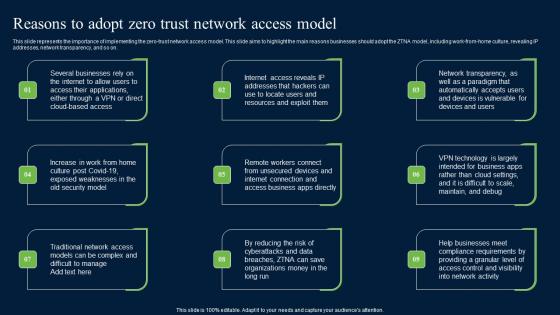
Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
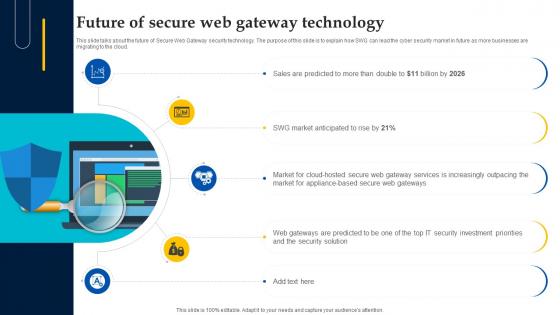
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
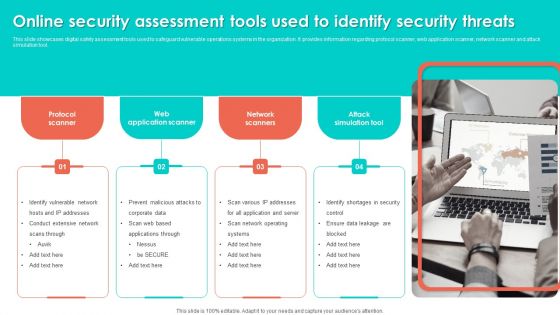
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
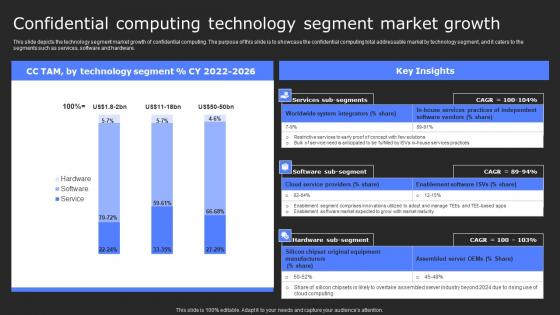
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.
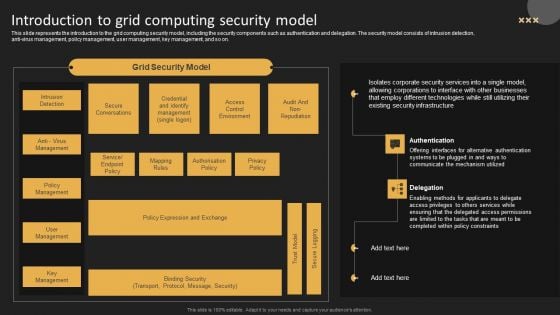
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
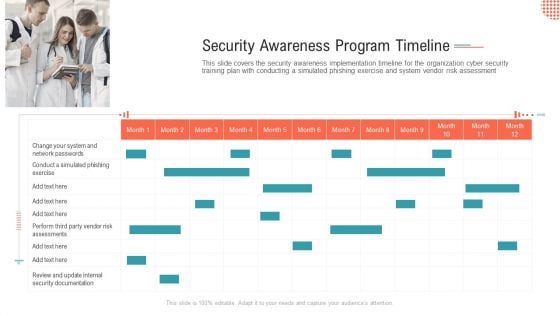
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy Of National Security United Kingdom PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Strategy Of National Security United Kingdom PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Security PowerPoint Templates because the world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised. Use our Success PowerPoint Templates because this diagram depicts the essence of this chain reaction like sequence of events. Download our Business PowerPoint Templates because you have had a great year or so business wise. It is time to celebrate the efforts of your team. Download and present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Finance PowerPoint Templates because let this slide illustrates others piggyback on you to see well over the horizon.Use these PowerPoint slides for presentations relating to Strategy of national security united kingdom, security, success, business, marketing, finance. The prominent colors used in the PowerPoint template are Red, White, Blue navy. Customers tell us our Strategy Of National Security United Kingdom PowerPoint Templates PPT Backgrounds For Slides 1212 are Bright. Presenters tell us our national PowerPoint templates and PPT Slides effectively help you save your valuable time. Use our Strategy Of National Security United Kingdom PowerPoint Templates PPT Backgrounds For Slides 1212 are No-nonsense. PowerPoint presentation experts tell us our national PowerPoint templates and PPT Slides have awesome images to get your point across. Customers tell us our Strategy Of National Security United Kingdom PowerPoint Templates PPT Backgrounds For Slides 1212 are Fashionable. Presenters tell us our business PowerPoint templates and PPT Slides are Festive. Clad your thoughts in our Strategy Of National Security United Kingdom PowerPoint Templates Ppt Backgrounds For Slides 1212. Dress them appropriately for the event.

Key In The Labyrinth Choice Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Business PowerPoint Templates because you have had your share of being a goldfish in a small bowl.you are ready to launch out and spread your wings. Download our Security PowerPoint Templates because our creative template will lay down your views. Present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Success PowerPoint Templates because your quest has taken you well onto the path of success. Download our Shapes PowerPoint Templates because you have the moves to sway the market.Use these PowerPoint slides for presentations relating to Key in the labyrinth security, security, business, marketing, success, shapes. The prominent colors used in the PowerPoint template are White, Yellow, Gray. We assure you our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Fun. Customers tell us our success PowerPoint templates and PPT Slides are Beautiful. Customers tell us our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Swanky. The feedback we get is that our success PowerPoint templates and PPT Slides are Spectacular. PowerPoint presentation experts tell us our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are Majestic. Earn a fabulous reputation with our Key In The Labyrinth Choice Security PowerPoint Templates Ppt Backgrounds For Slides 1212. Talk of your talks will spread far and wide.
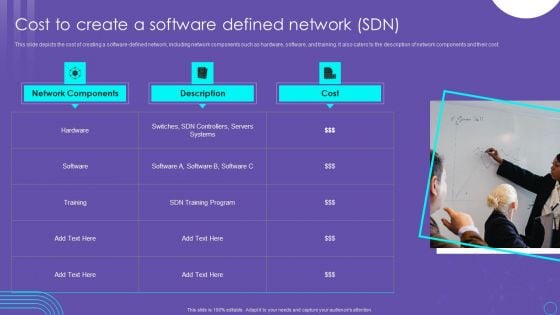
SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF
This slide depicts the cost of creating a software defined network, including network components such as hardware, software, and training. It also caters to the description of network components and their cost. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF

5G Network Applications And Features Security In 5G Technology Architecture Download PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Find highly impressive 5G Network Applications And Features Security In 5G Technology Architecture Download PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download 5G Network Applications And Features Security In 5G Technology Architecture Download PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
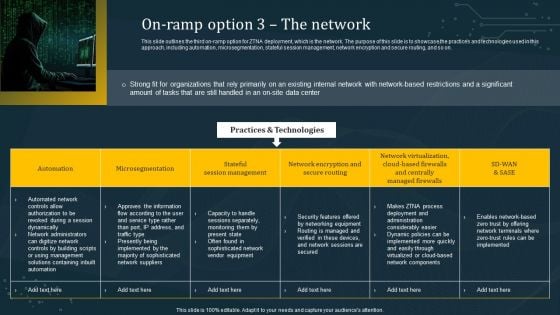
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
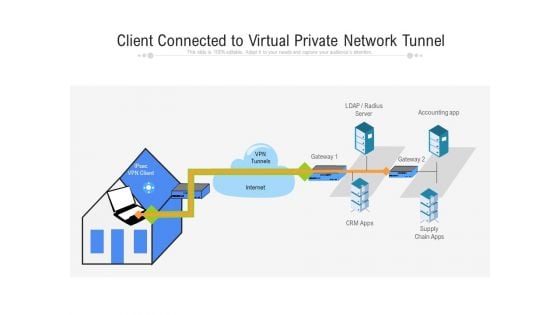
Client Connected To Virtual Private Network Tunnel Ppt PowerPoint Presentation File Graphics Download PDF
Presenting client connected to virtual private network tunnel ppt powerpoint presentation file graphics download pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including client connected to virtual private network tunnel. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Are you searching for a Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF from Slidegeeks today.
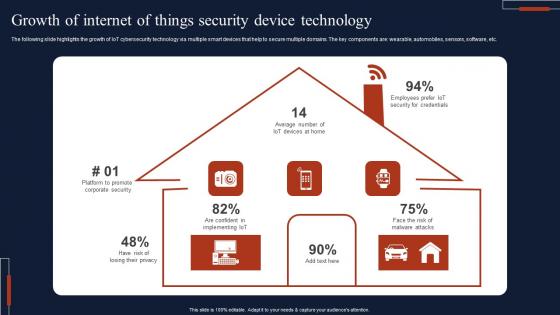
Growth Of Internet Of Things Security Device Technology Professional Pdf
The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc. Pitch your topic with ease and precision using this Growth Of Internet Of Things Security Device Technology Professional Pdf This layout presents information on Growth Of Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc.
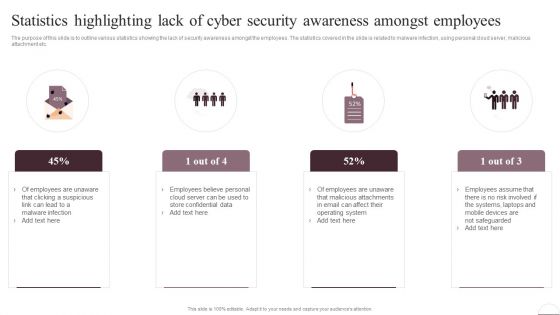
Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
Checklist Icon With Four Text Boxes Ppt PowerPoint Presentation Show Model
This is a checklist icon with four text boxes ppt powerpoint presentation show model. This is a one stage process. The stages in this process are risk management icon, governance icon, compliance icon.

Firewall Secured Network Business Communication PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Firewall Secured Network Business Communication PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to Security plan for a firewall system, business, communication, technology, success, signs. The prominent colors used in the PowerPoint template are Green, Red, Gray. Convincing an audience is no mean feat. Do it with ease with our Firewall Secured Network Business Communication PowerPoint Templates Ppt Backgrounds For Slides 0313.
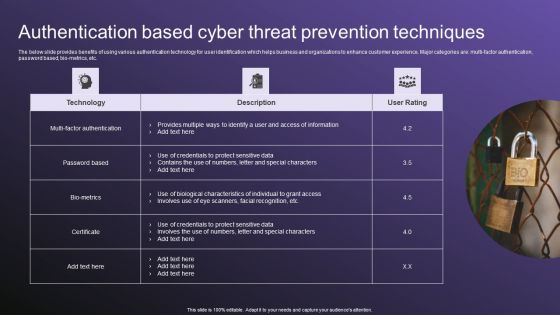
Authentication Based Cyber Threat Prevention Techniques Download PDF
The below slide provides benefits of using various authentication technology for user identification which helps business and organizations to enhance customer experience. Major categories are multi factor authentication, password based, bio-metrics, etc. Showcasing this set of slides titled Authentication Based Cyber Threat Prevention Techniques Download PDF. The topics addressed in these templates are Techniques, Authentication, Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. This modern and well arranged Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.
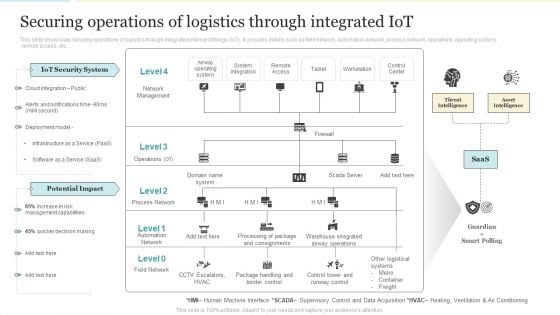
Securing Operations Of Logistics Through Integrated Iot Professional PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver and pitch your topic in the best possible manner with this Securing Operations Of Logistics Through Integrated Iot Professional PDF PDF. Use them to share invaluable insights on Iot Security System, Potential Impact, Management Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
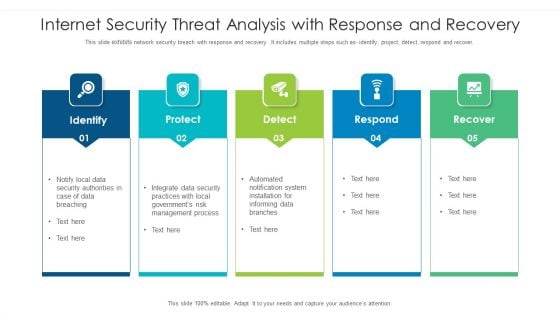
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
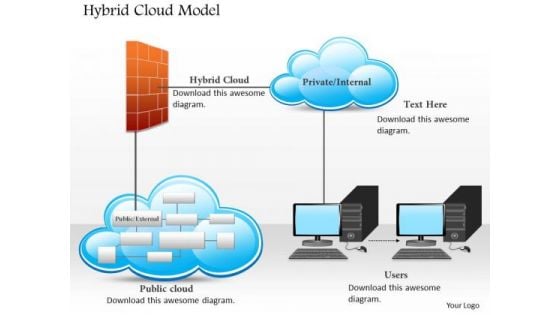
Business Diagram Hybrid Cloud Model With Public Private Cloud And Users Connected Ppt Slide
This technology diagram slide has been designed with graphic of hybrid cloud model. This slide depicts the concept of cloud computing for user benefit. Display private and public user benefits of cloud computing.
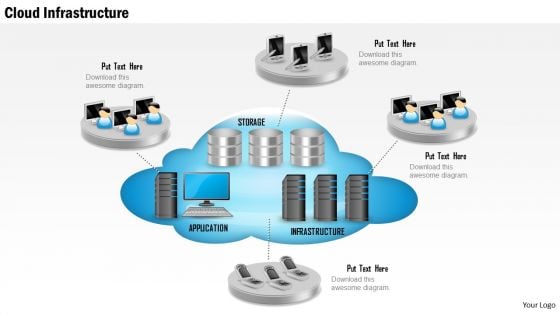
1 Cloud Infrastructure Show With Application Storage And Servers And Mobile Devices Ppt Slides
This image slide displays cloud infrastructure depicted with application, storage and servers. This image slide has been crafted with graphic of cloud with application, storage and infrastructure icons. Graphic of various technology devices has also been used in this image. This image slide depicts cloud computing infrastructure. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology and business. This image slide will help you achieve your goal of making professional presentations.
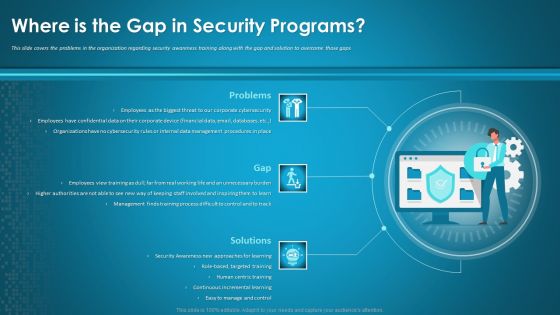
Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
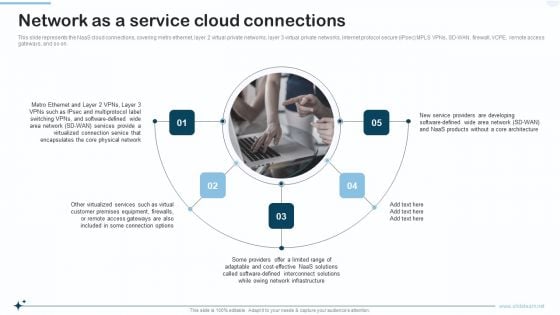
Naas Integrated Solution IT Network As A Service Cloud Connections Topics PDF
This slide represents the NaaS cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure IPsec MPLS VPNs, SD-WAN, firewall, VCPE, remote access gateways, and so on. This is a Naas Integrated Solution IT Network As A Service Cloud Connections Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Services, Network, Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Experiential Retail Store Network Development Success Factors For Experiential Retail In Future Template PDF
This slide provides information regarding success factors for experiential retail in future in terms of data-driven, flexible, augmentation with customized digital interaction. Are you searching for a Experiential Retail Store Network Development Success Factors For Experiential Retail In Future Template PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Experiential Retail Store Network Development Success Factors For Experiential Retail In Future Template PDF from Slidegeeks today.
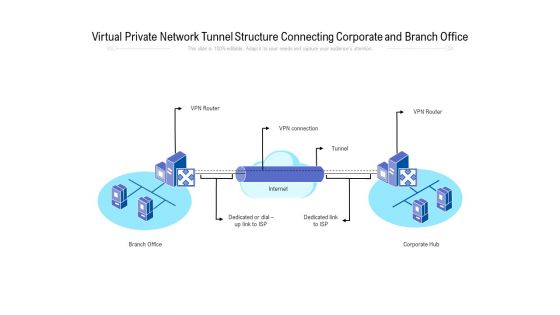
Virtual Private Network Tunnel Structure Connecting Corporate And Branch Office Ppt PowerPoint Presentation File Pictures PDF
Presenting virtual private network tunnel structure connecting corporate and branch office ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virtual private network tunnel structure connecting corporate and branch office. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Organizational Network Security Awareness Staff Learning Comparison Formats PDF
This is a organizational network security awareness staff learning comparison formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Security Awareness Staff Learning Post It Icons PDF
This is a organizational network security awareness staff learning post it icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.
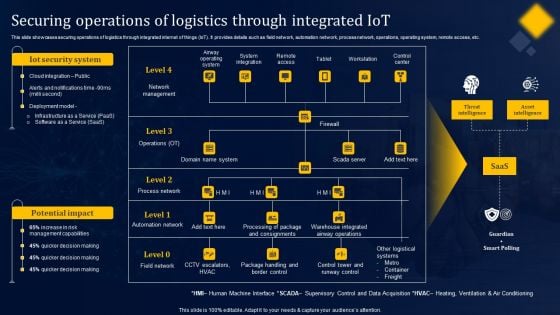
Securing Operations Of Logistics Through Integrated Iot Structure PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Securing Operations Of Logistics Through Integrated Iot Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
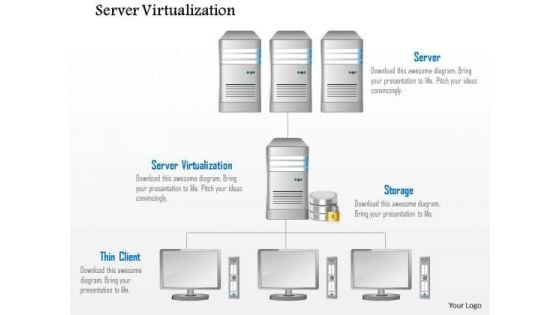
Business Diagram Server Virtulization Thin Client Storage And Database Ppt Slide
This image slide displays network of servers. This image slide has been designed with graphic of server workstation with concepts of server virtualization storage and thin client. This image slide will enhance the quality of your presentations.

Computer Program To Stop Virus Threats Ppt PowerPoint Presentation Portfolio Information PDF
Presenting this set of slides with name computer program to stop virus threats ppt powerpoint presentation portfolio information pdf. This is a three stage process. The stages in this process are computer program to stop virus threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
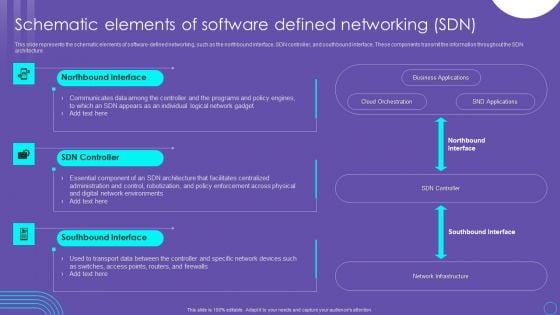
SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF
This slide represents the schematic elements of software defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. Create an editable SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
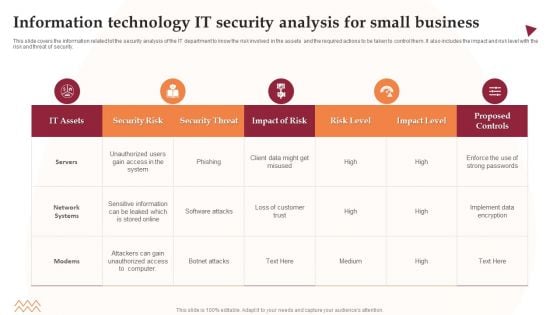
Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization today and make your presentation stand out from the rest This slide defines an all-inclusive timeline of steps in the execution of nanorobotics in healthcare and medicine by incorporating effective use of nanorobots within an organization. This ranges from preparation and research and eventually to the inclusion of nanorobotics with the existing healthcare systems. The timeline also identifies critical factors including security, regulatory compliance, testing, and safety procedures, where nanorobots would be applied safely and effectively.This slide is perfect for advanced medical technology presentations to help the stakeholders understand the systematic process of how nanorobotics could be introduced in healthcare solutions and paved their way for smooth adoption and use.
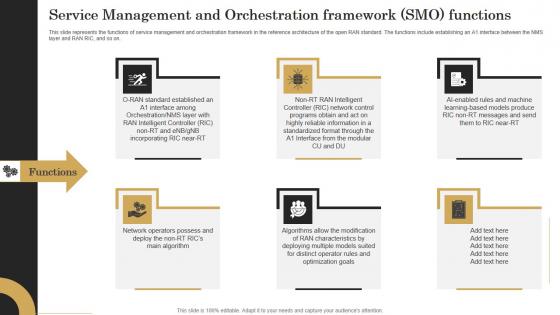
Service Management And Orchestration Revolutionizing Mobile Networks Themes PDF
This slide represents the functions of service management and orchestration framework in the reference architecture of the open RAN standard. The functions include establishing an A1 interface between the NMS layer and RAN RIC, and so on. The Service Management And Orchestration Revolutionizing Mobile Networks Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the functions of service management and orchestration framework in the reference architecture of the open RAN standard. The functions include establishing an A1 interface between the NMS layer and RAN RIC, and so on.


 Continue with Email
Continue with Email

 Home
Home


































