Layered Security
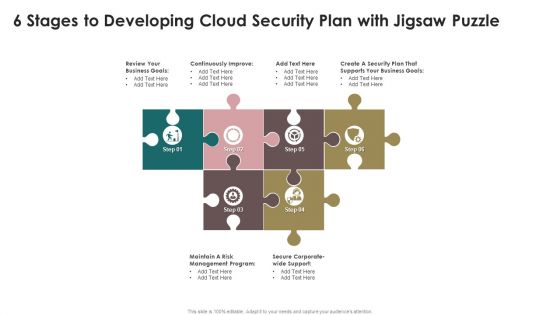
6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF
Persuade your audience using this 6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Business Goals. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
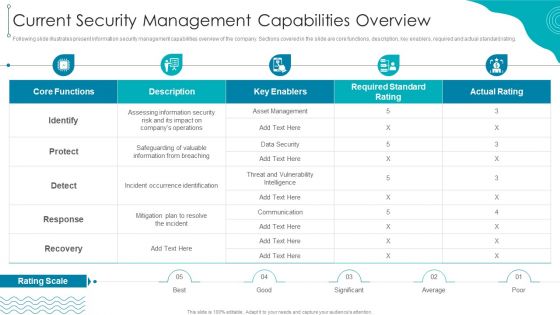
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Digitization Of Security Systems Icon With Gear Ppt Portfolio Tips PDF
Persuade your audience using this Digitization Of Security Systems Icon With Gear Ppt Portfolio Tips PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digitization, Security Systems, Icon With Gear. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF bundle. Topics like Consumers, Implements Applications, Outlines Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
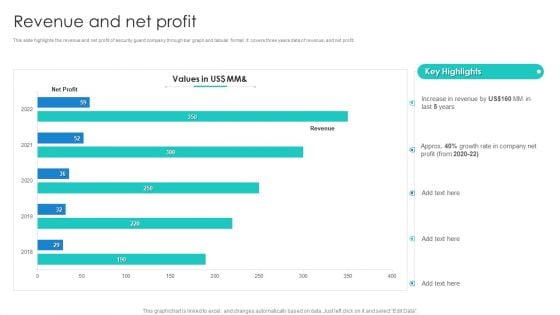
Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF. Use them to share invaluable insights on Revenue, Profit, Growth Rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Deliver and pitch your topic in the best possible manner with this Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF. Use them to share invaluable insights on Ownership, Seen Breakdown, Total Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
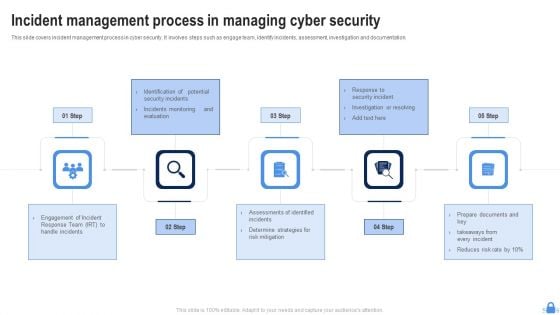
Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
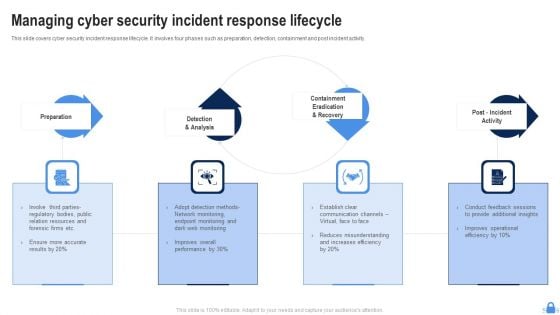
Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF
This slide covers cyber security incident response lifecycle. It involves four phases such as preparation, detection, containment and post incident activity. Presenting Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Preparation, Post Incident Activity, Detection And Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF
Persuade your audience using this Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showing Data Security, Blockchain Technology Supply Chain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security For Cloud Based Systems Management Icon For IT Project Rules PDF
Persuade your audience using this Security For Cloud Based Systems Management Icon For IT Project Rules PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Management, IT Project. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF
Persuade your audience using this Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Alert Icon, Desktop Screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF
Persuade your audience using this Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Icon With Man, Black Hood. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF
Persuade your audience using this Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Online, Certificate Icon, Information Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF
Persuade your audience using this Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Overview Of Key Insights, Cyber Security Trends Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Data Security Assessment Icon Ppt PowerPoint Presentation Gallery Outfit PDF
Persuade your audience using this Cloud Data Security Assessment Icon Ppt PowerPoint Presentation Gallery Outfit PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Security, Assessment Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF
This slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Pitch your topic with ease and precision using this Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF. This layout presents information on Checklist, Execution, Functionality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF
Persuade your audience using this Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Bring Your Own, Device Security Policy, Check Organizations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.

Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document
This slide illustrates the cover letter for the business proposal providing a brief overview of the clients wants and a brief introduction to the project. Presenting you an exemplary Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.
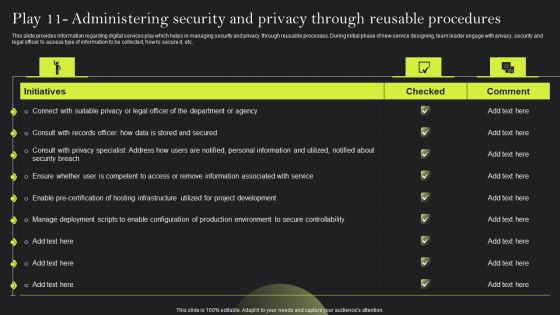
Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
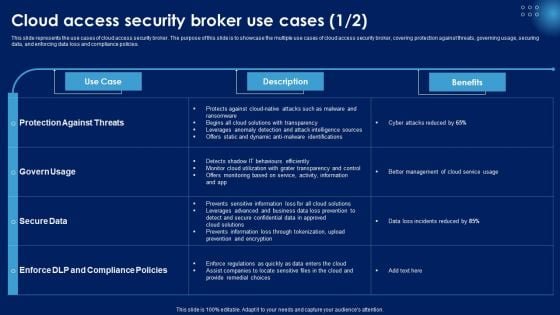
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
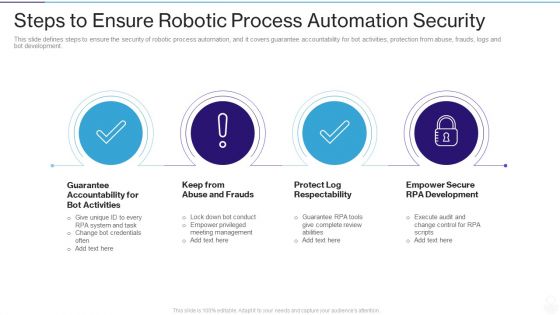
RPA IT Steps To Ensure Robotic Process Automation Security Ppt Layouts Layout Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a rpa it steps to ensure robotic process automation security ppt layouts layout ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like guarantee accountability for bot activities, keep from abuse and frauds, protect log respectability, empower secure rpa development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development.This is a Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Empower Secure, Log Respectability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
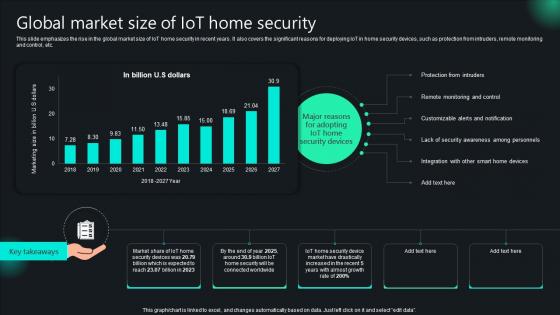
Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V
This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc. The Unlocking Potential IoTs Application Global Market Size Of IoT Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide emphasizes the rise in the global market size of IoT home security in recent years. It also covers the significant reasons for deploying IoT in home security devices, such as protection from intruders, remote monitoring and control, etc.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF
The following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Create an editable Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
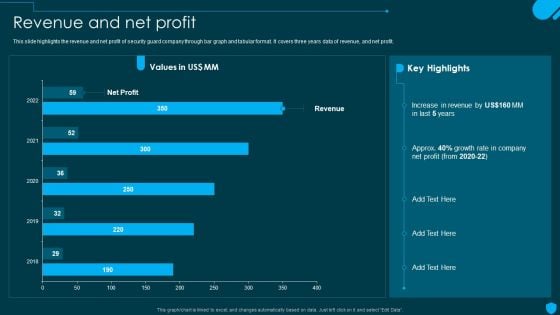
Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Explore a selection of the finest Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
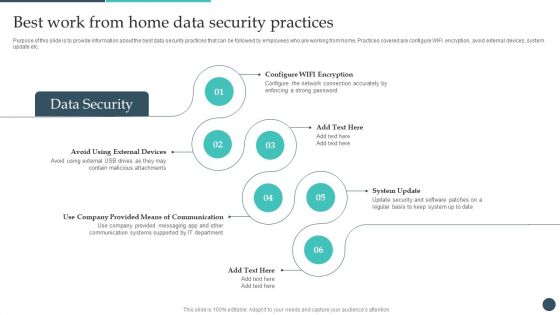
Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Explore a selection of the finest Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
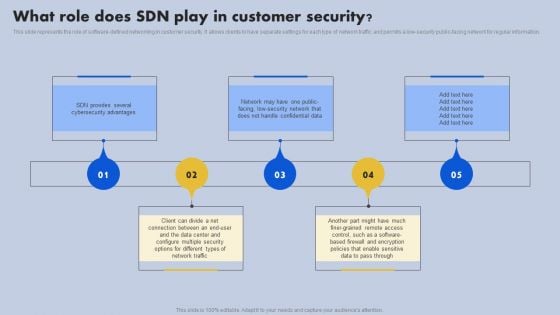
What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
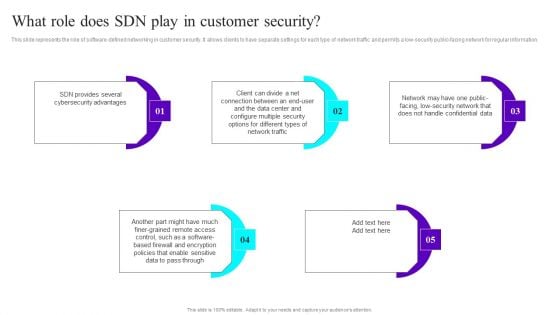
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
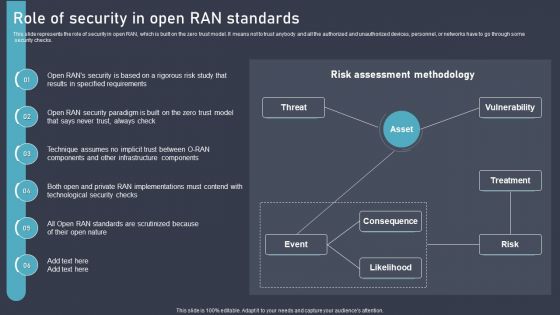
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
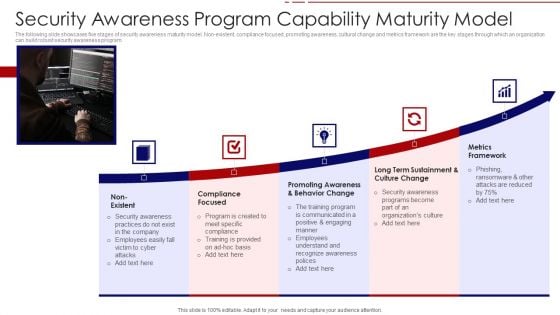
Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
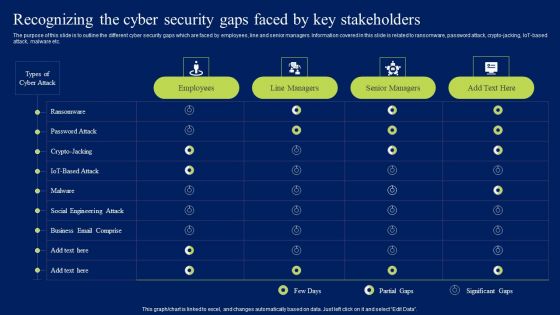
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Explore a selection of the finest CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CRM Software Deployment Journey Implementation Steps Enable Data Security Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

How To Overcome The Security Awareness Training Program Challenges Infographics PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Create an editable How To Overcome The Security Awareness Training Program Challenges Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. How To Overcome The Security Awareness Training Program Challenges Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
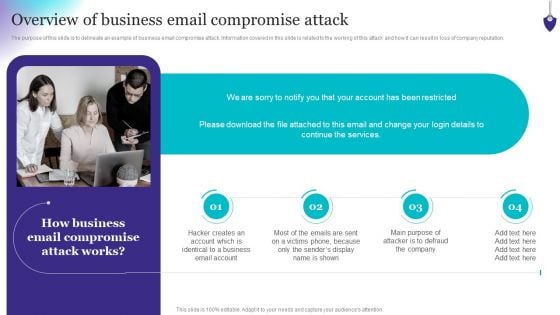
Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF
The purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Presenting this PowerPoint presentation, titled Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizing Security Awareness Overview Of Business Email Compromise Attack Portrait PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
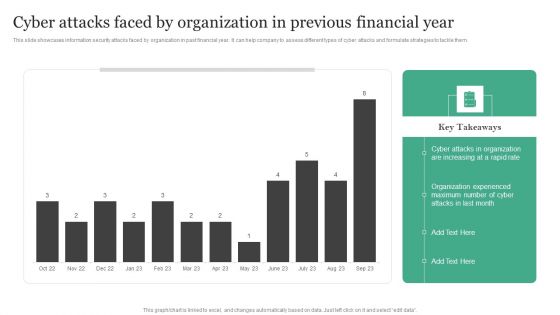
Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them.Create an editable Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
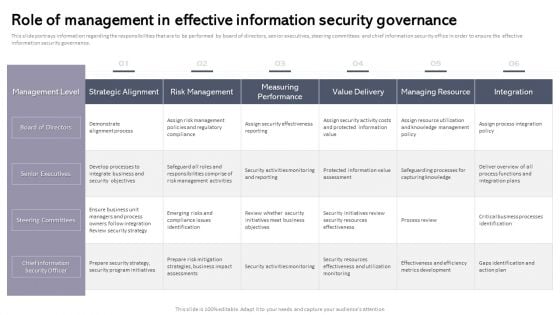
Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Retrieve professionally designed Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
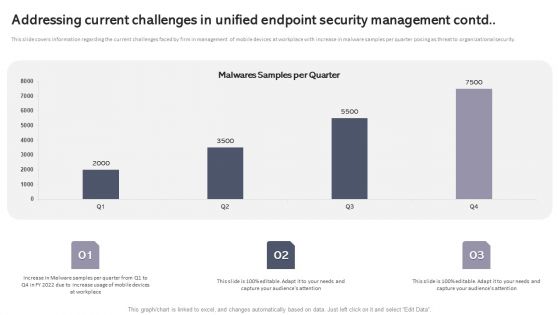
Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with increase in malware samples per quarter posing as threat to organizational security. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Addressing Current Challenges In Unified Endpoint Security Management Contd Introduction PDF.
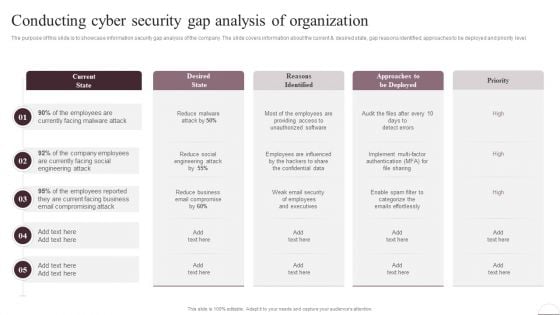
Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard AND regulation etc. This Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
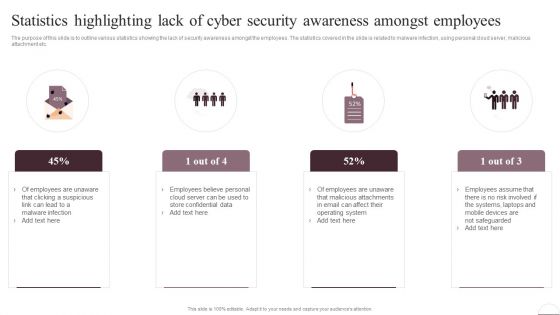
Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Statistics Highlighting Lack Of Cyber Security Awareness Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
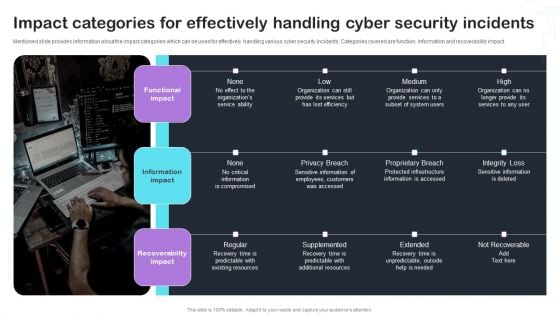
Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. This Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
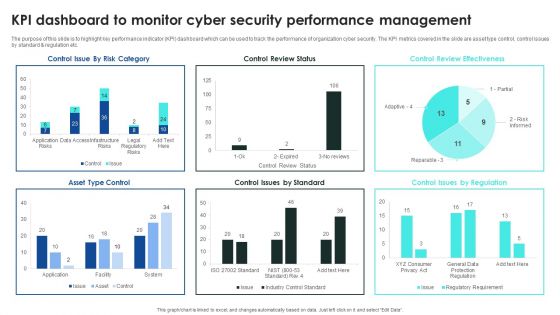
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
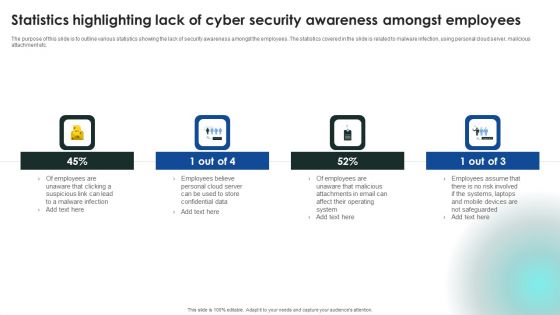
Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Explore a selection of the finest Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF
This slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Retrieve professionally designed Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
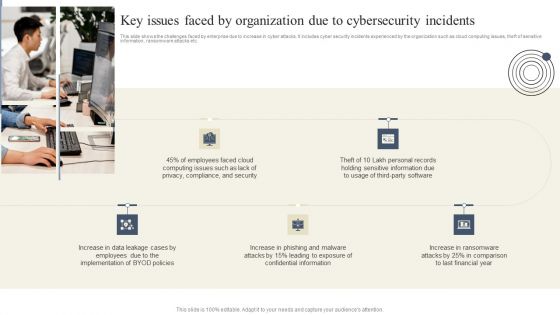
Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Create an editable Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Breache Response Strategy Key Issues Faced By Organization Due To Cybersecurity Incidents Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.


 Continue with Email
Continue with Email

 Home
Home


































