Layered Security

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
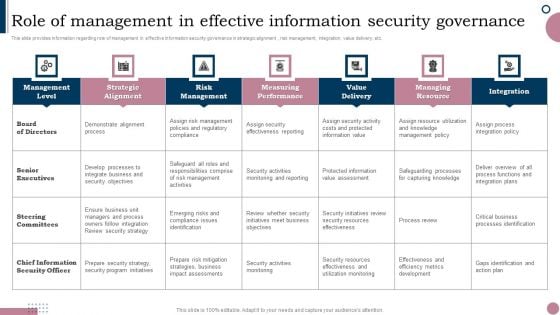
Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Retrieve professionally designed Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
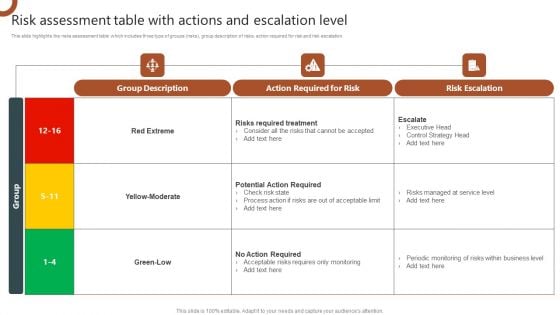
Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc.Find highly impressive Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
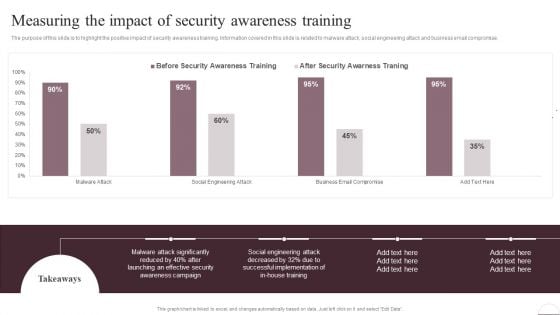
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
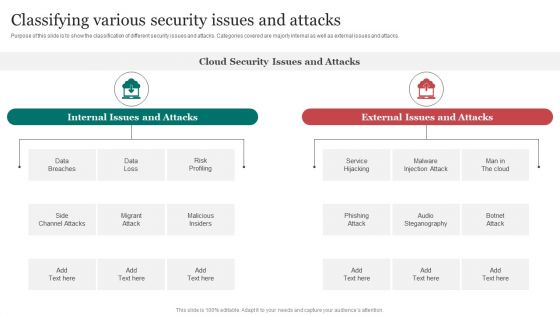
Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
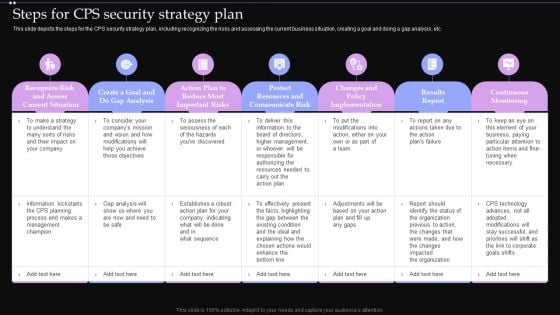
Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
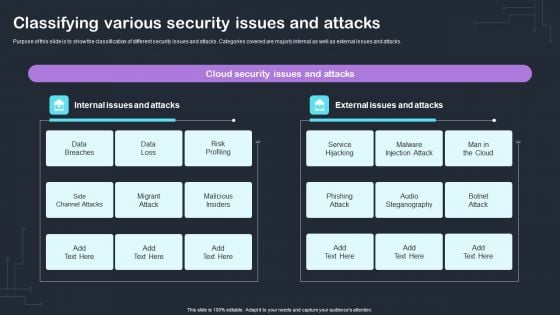
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
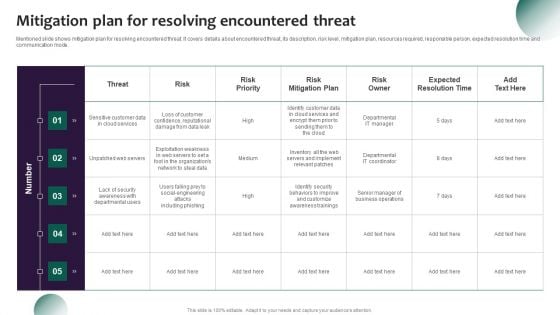
Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
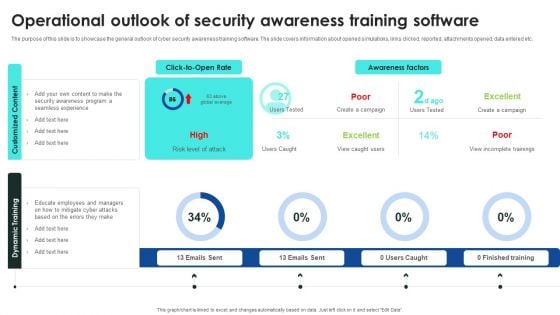
Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
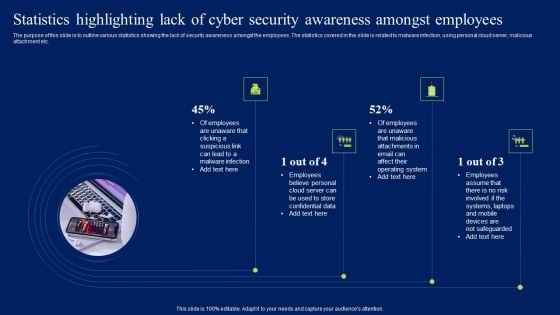
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Present like a pro with Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
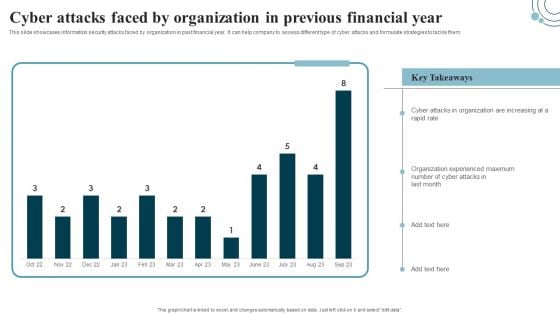
Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
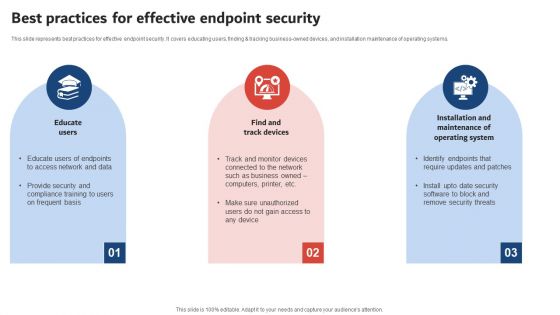
Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF
This slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
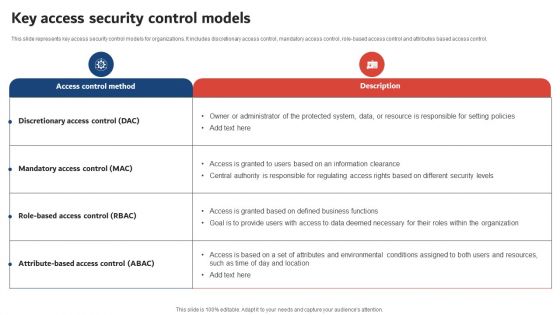
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
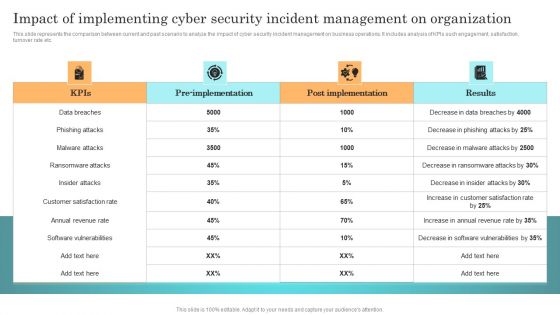
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
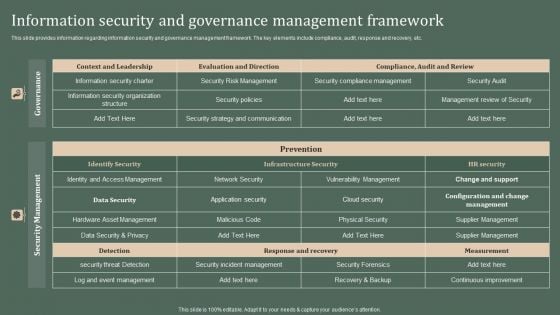
Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.
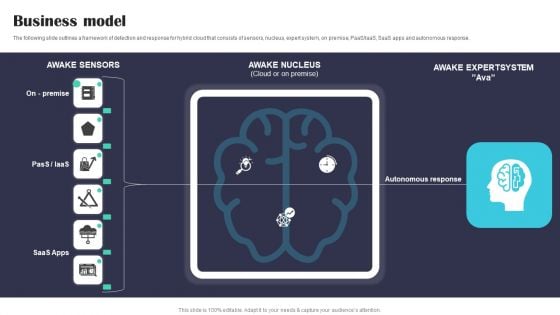
Security Software Company Investor Funding Pitch Deck Business Model Structure PDF
The following slide outlines a framework of detection and response for hybrid cloud that consists of sensors, nucleus, expert system, on premise, PaaS or IaaS, SaaS apps and autonomous response. Create an editable Security Software Company Investor Funding Pitch Deck Business Model Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Security Software Company Investor Funding Pitch Deck Business Model Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
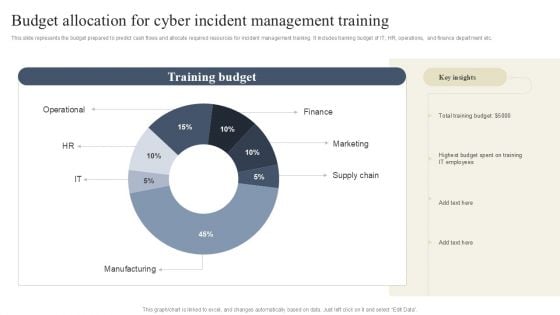
CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
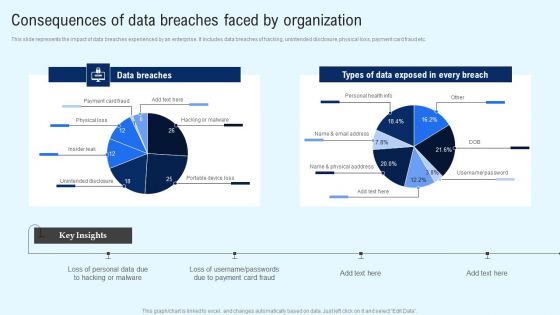
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Info Security Assessment Matrix Of Cyber Risks Ppt PowerPoint Presentation Icon Styles PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative info security assessment matrix of cyber risks ppt powerpoint presentation icon styles pdf bundle. Topics like employee devices, webserver network, cloud, retail, data center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
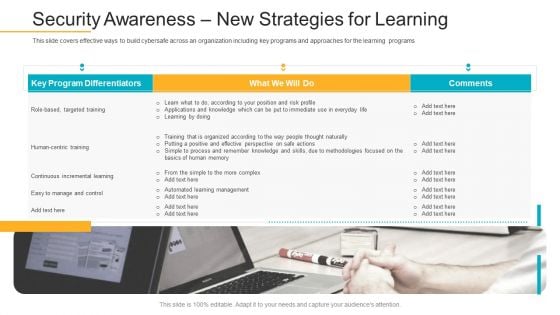
Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images Pdf. Use them to share invaluable insights on key program, targeted training, management, methodologies, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
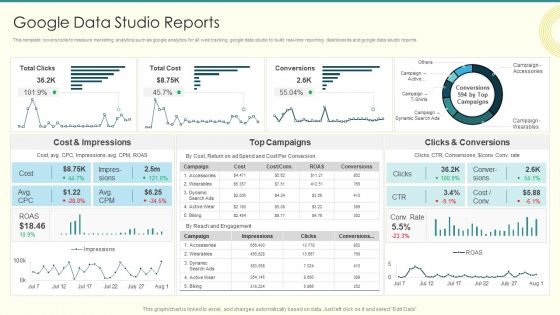
Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF bundle. Topics like Impressions, Clicks Conversions, Cost Impressions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
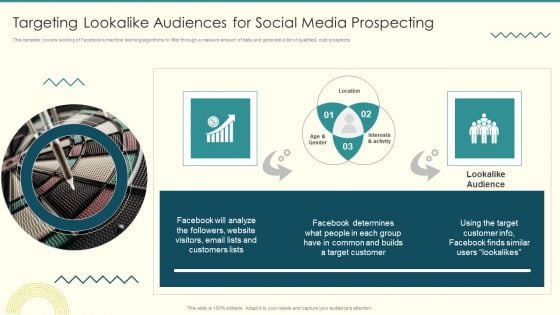
Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
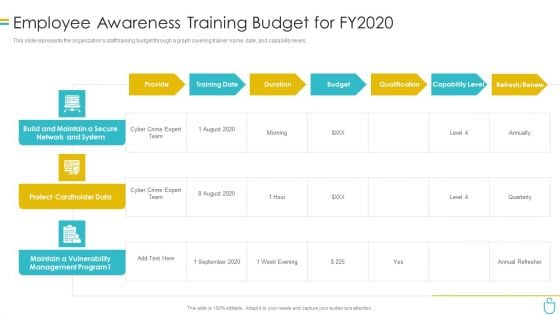
Information Security Employee Awareness Training Budget For Fy2020 Ppt File Portfolio PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative information security employee awareness training budget for fy2020 ppt file portfolio pdf bundle. Topics like budget, protect cardholder data, capability level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
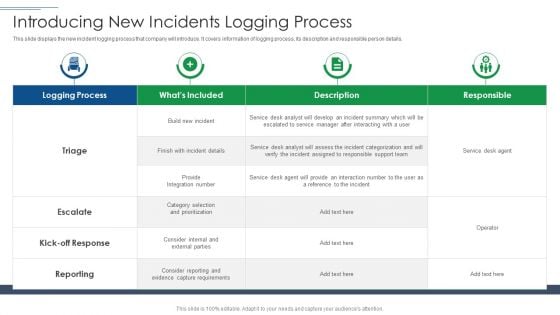
IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
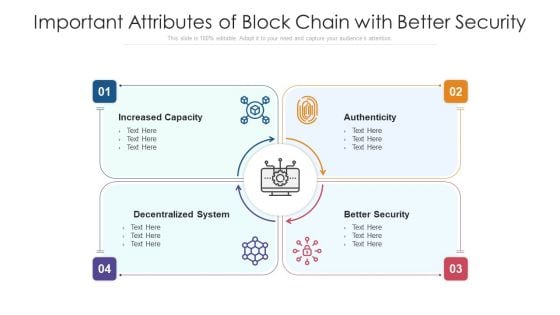
Important Attributes Of Block Chain With Better Security Ppt PowerPoint Presentation Pictures Sample PDF
Persuade your audience using this important attributes of block chain with better security ppt powerpoint presentation pictures sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including decentralized system, authenticity, increased capacity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
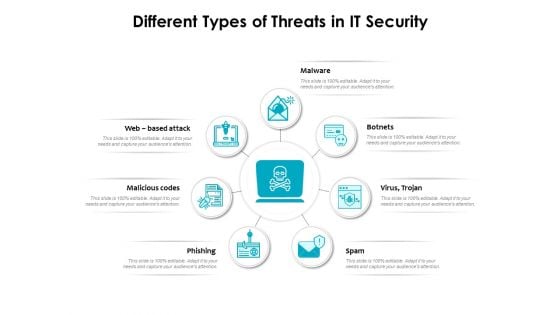
Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Statistical Analysis Of IT Security In Small Enterprise Ppt PowerPoint Presentation Ideas Design Inspiration PDF
Persuade your audience using this statistical analysis of it security in small enterprise ppt powerpoint presentation ideas design inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber attack and breaches, cyber attack and breach type, spear phishing, web attacks, spam, ransomware, identity theft. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Stages To Develop Strong Cyber Security Analysis Process Ppt PowerPoint Presentation Outline Example File PDF
Persuade your audience using this stages to develop strong cyber security analysis process ppt powerpoint presentation outline example file pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including formulate remediation steps and prioritize risks, analysing collected, recipient on the phone, teleconference. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
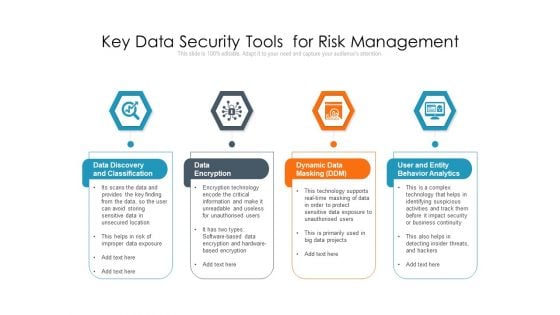
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
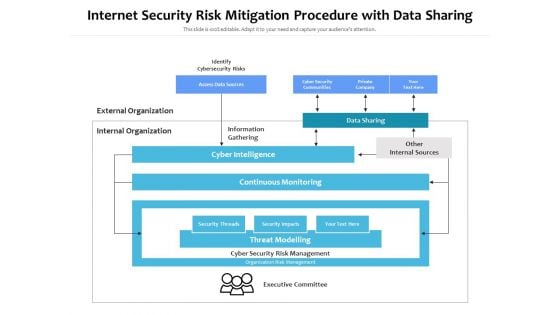
Internet Security Risk Mitigation Procedure With Data Sharing Ppt PowerPoint Presentation Pictures Show PDF
Persuade your audience using this internet security risk mitigation procedure with data sharing ppt powerpoint presentation pictures show pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including identify cybersecurity risks, external organization, internal organization, information gathering, data sharing, other internal sources, cyber intelligence, continuous monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
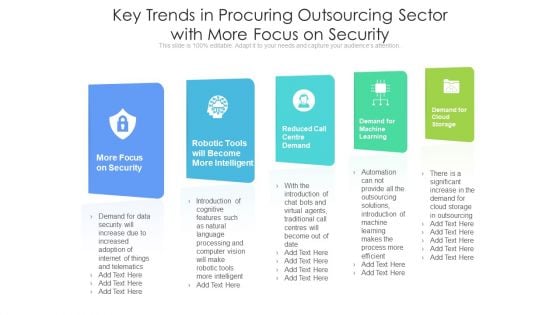
Key Trends In Procuring Outsourcing Sector With More Focus On Security Ppt Gallery Smartart PDF
Persuade your audience using this key trends in procuring outsourcing sector with more focus on security ppt gallery smartart pdf.This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including demand for machine learning, demand for cloud storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Breach Prevention Recognition Employee Security Awareness Training Budget Graphics PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative data breach prevention recognition employee security awareness training budget graphics pdf bundle. Topics like budget, capability level, renew, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
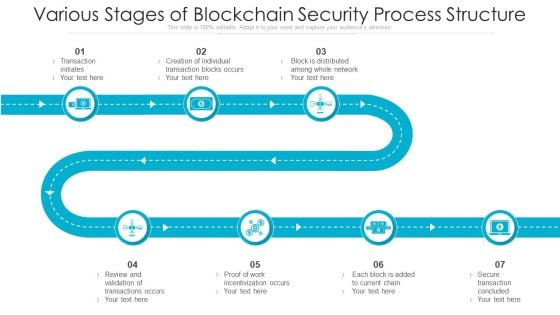
Various Stages Of Blockchain Security Process Structure Ppt PowerPoint Presentation Ideas Information PDF
Persuade your audience using this various stages of blockchain security process structure ppt powerpoint presentation ideas information pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including transaction initiates, each block is added to current chain, proof of work incentivization occurs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
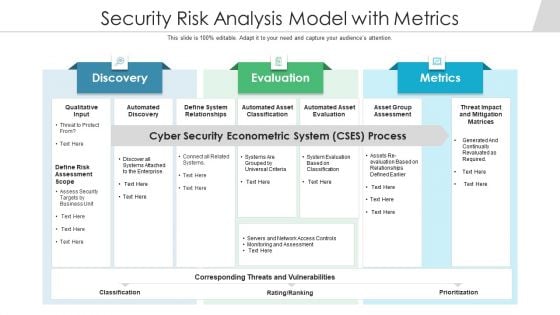
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Case Study 2 Banks Cyber Security Infrastructure Ppt Pictures Example PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Deliver an awe inspiring pitch with this creative case study 2 banks cyber security infrastructure ppt pictures example pdf bundle. Topics like implemented, integrated, approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
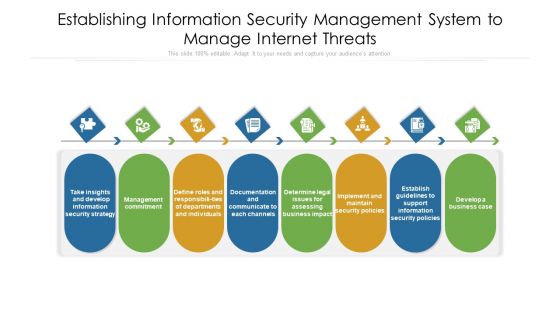
Establishing Information Security Management System To Manage Internet Threats Ppt PowerPoint Presentation File Visuals PDF
Persuade your audience using this establishing information security management system to manage internet threats ppt powerpoint presentation file visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including documentation, departments, management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security IT Awareness Training For Staff Ppt Gallery Example Introduction PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this it security it awareness training for staff ppt gallery example introduction pdf. Use them to share invaluable insights on developers, organizations, senior executives, planning, strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Addressing The Incidents Logging Process Diagrams PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative cyber security risk management plan addressing the incidents logging process diagrams pdf bundle. Topics like process id, procedure, description, responsible person can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
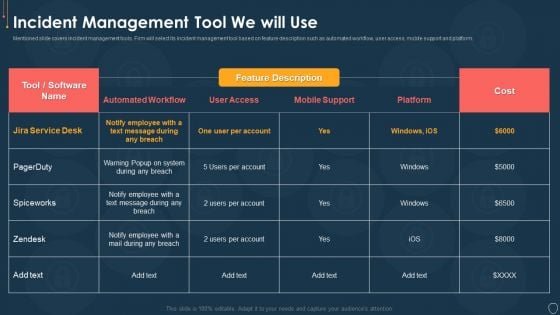
Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
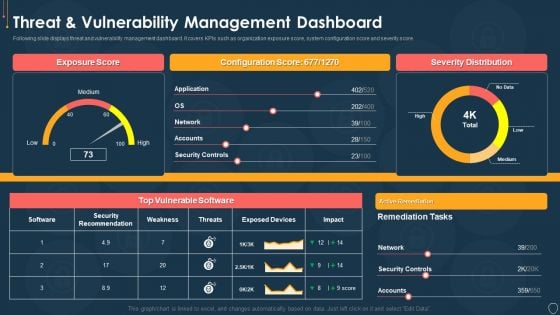
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
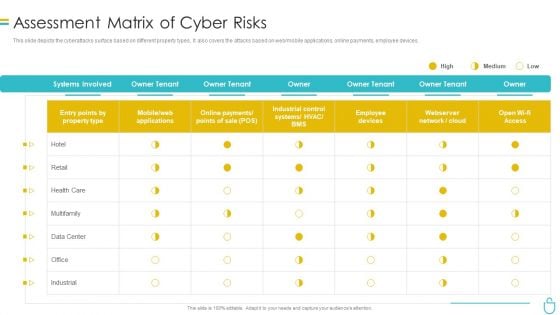
Information Security Assessment Matrix Of Cyber Risks Ppt Infographics Sample PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information security assessment matrix of cyber risks ppt infographics sample pdf bundle. Topics like employee devices, retail, industrial, owner can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Employee Awareness Training Budget For Fy2022 Inspiration PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Presenting desktop security management employee awareness training budget for fy2022 inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like opportunities, threats, weaknesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

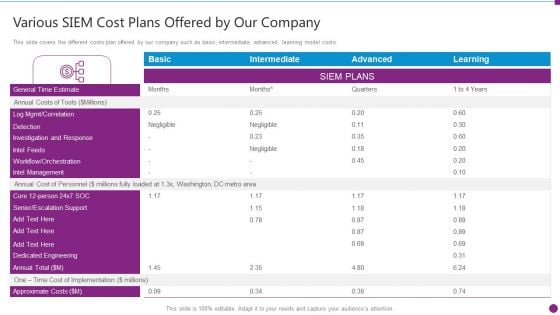
Real Time Assessment Of Security Threats Various SIEM Cost Plans Offered By Our Company Topics PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an awe inspiring pitch with this creative real time assessment of security threats various siem cost plans offered by our company topics pdf bundle. Topics like annual costs of tools, annual cost of personnel, one time cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
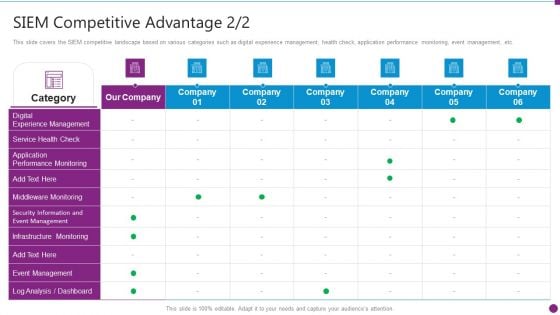
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Advantage Designs PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance siem competitive advantage designs pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Information And Event Management Strategies For Financial Audit And Compliance Various SIEM Cost Clipart PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance various siem cost clipart pdf. Use them to share invaluable insights on intel management, general time, annual costs of tools and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Employee Awareness Training Budget For FY2022 Ppt Show Slide PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Presenting it security employee awareness training budget for fy2022 ppt show slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like training, duration, budget, capability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































