Layered Security
Security Camera System Company Profile Company Operations In US And Canada Mockup PDF
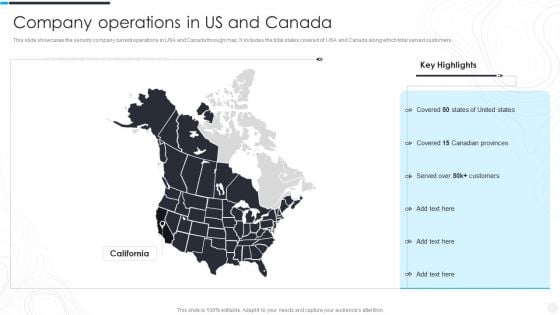
This slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers.Presenting Security Camera System Company Profile Company Operations In US And Canada Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Key Highlights, Customers, Canadian Provinces. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Camera System Company Profile Existing Channel Development Strategy Designs PDF
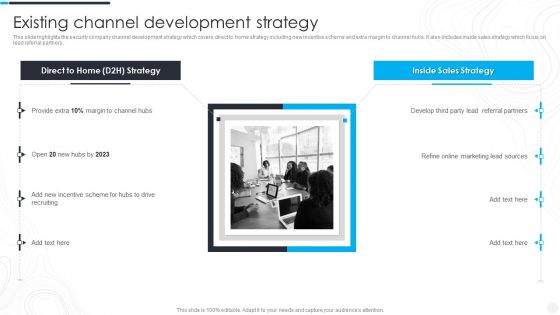
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security Camera System Company Profile Existing Channel Development Strategy Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Referral Partners, Incentive Scheme, Marketing Lead. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
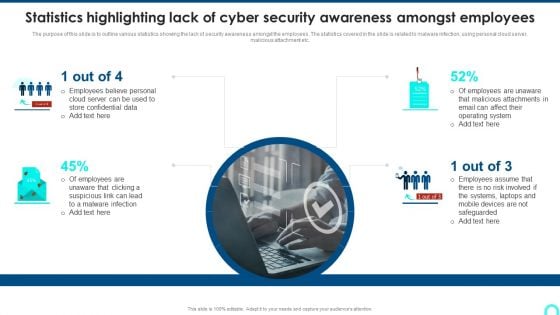
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF
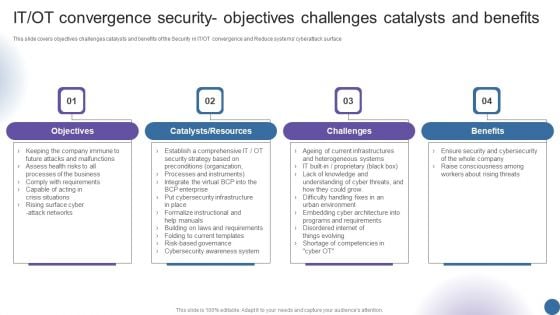
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
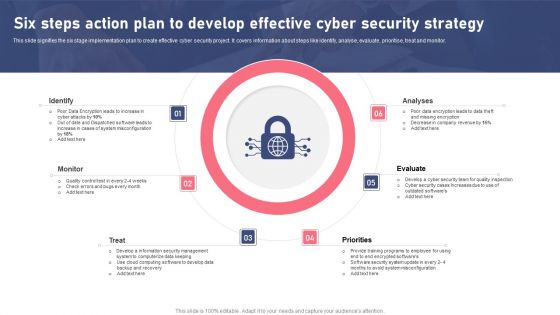
Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF
This slide signifies the six stage implementation plan to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor. Presenting Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Identify, Monitor, Priorities, Evaluate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
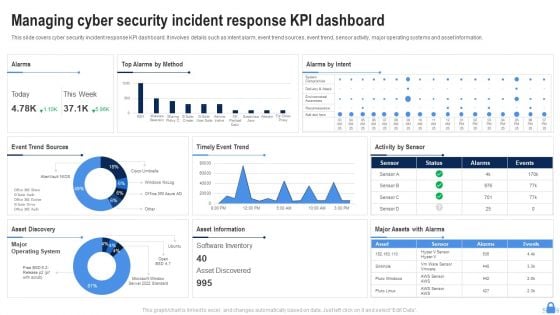
Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
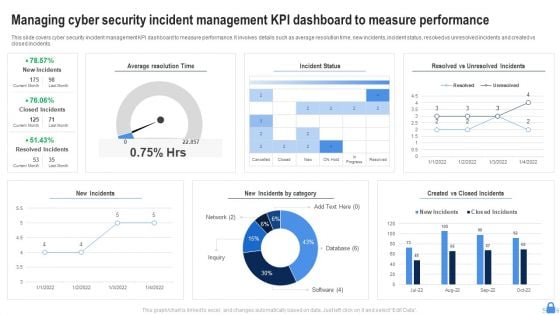
Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF
This slide covers cyber security incident management KPI dashboard to measure performance. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
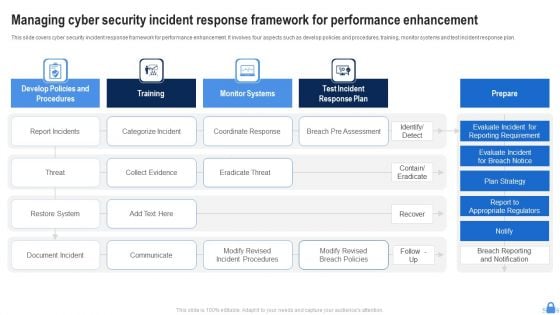
Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF
This slide covers cyber security incident response framework for performance enhancement. It involves four aspects such as develop policies and procedures, training, monitor systems and test incident response plan. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF. This layout presents information on Report Incidents, Threat, Restore System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
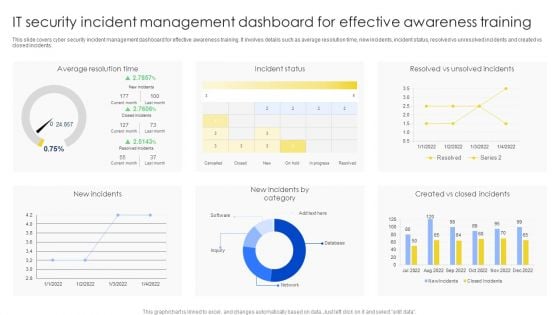
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Take your projects to the next level with our ultimate collection of IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
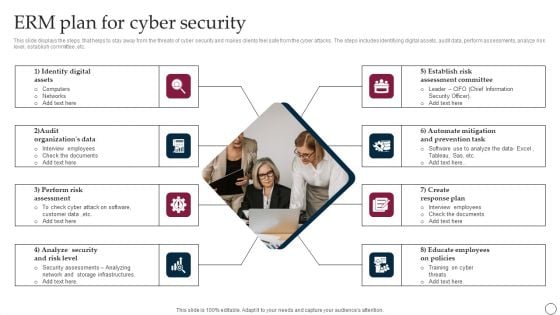
ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
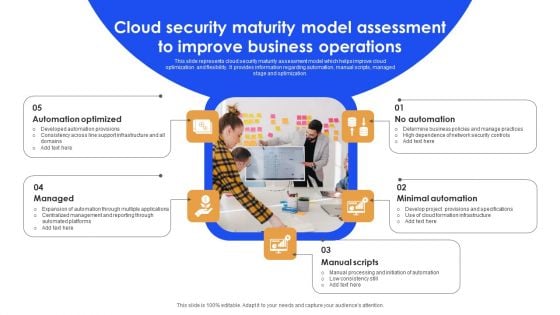
Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF
This slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Persuade your audience using this Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Automation Optimized, Minimal Automation, Manual Scripts. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
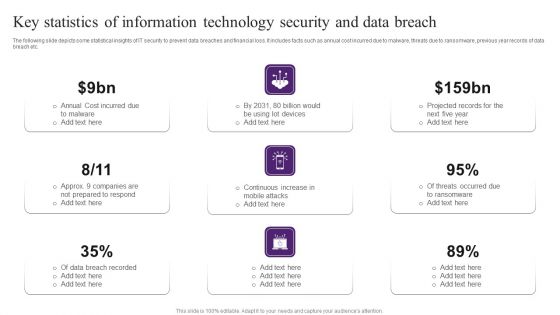
Key Statistics Of Information Technology Security And Data Breach Brochure PDF
The following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Persuade your audience using this Key Statistics Of Information Technology Security And Data Breach Brochure PDF. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including Cost Incurred, Data Breach Recorded, Projected Records. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF
Mentioned slide outlines 3 step process of governance, risk and compliance GRC. Information covered in this slide is related to governance, risk management and compliance which will assist organization to successfully mitigate IT and security risks. Presenting Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk Management, Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
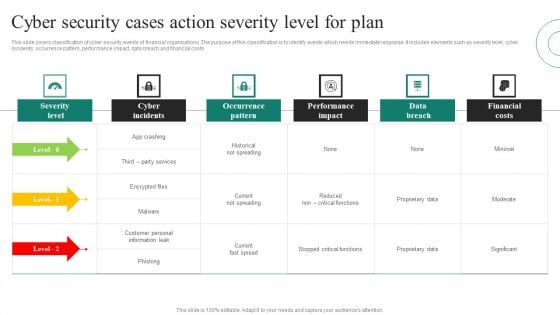
Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
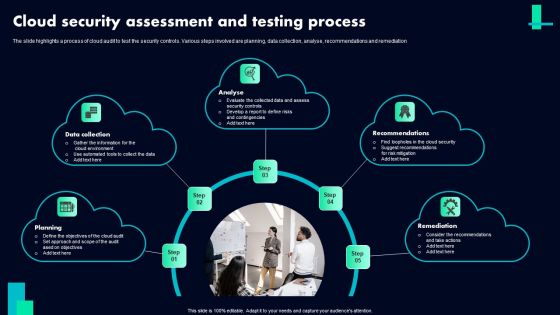
Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF
The slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation Persuade your audience using this Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Analyse, Recommendations, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
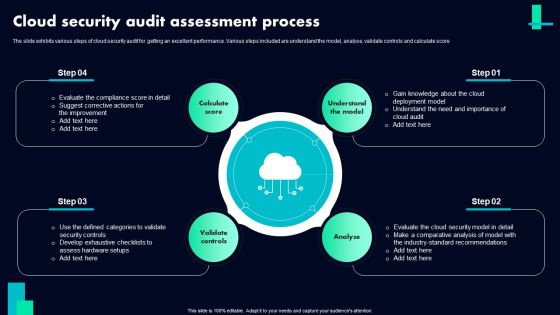
Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
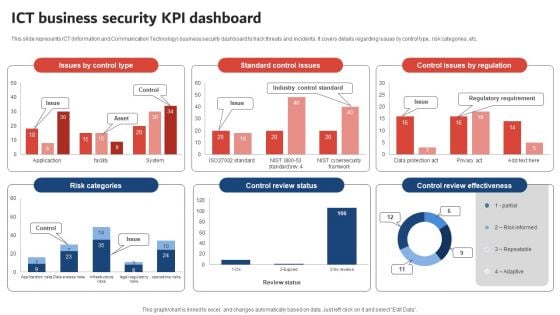
Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF
This slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Boost your pitch with our creative Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
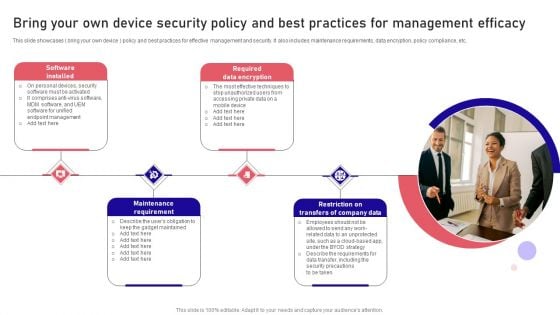
Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
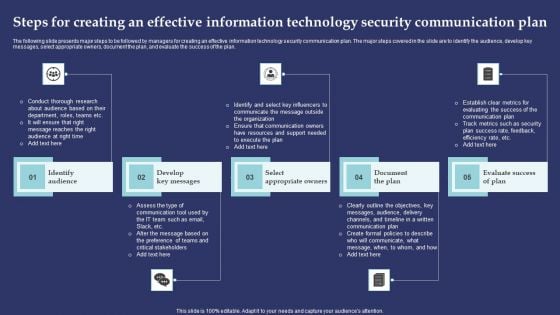
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m
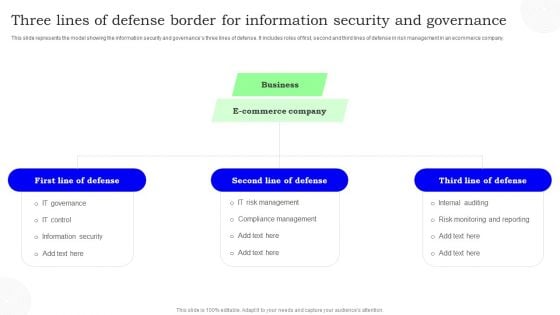
Three Lines Of Defense Border For Information Security And Governance Information PDF
This slide represents the model showing the information security and governances three lines of defense. It includes roles of first, second and third lines of defense in risk management in an ecommerce company. Persuade your audience using this Three Lines Of Defense Border For Information Security And Governance Information PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Defense, Commerce Company, Business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
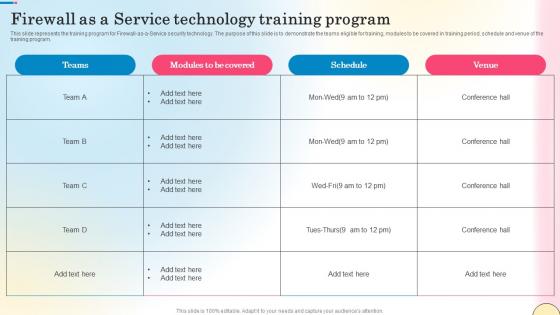
Firewall As A Service Technology Training Program Network Security Brochure Pdf
This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Firewall As A Service Technology Training Program Network Security Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Firewall As A Service Technology Training Program Network Security Brochure Pdf This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
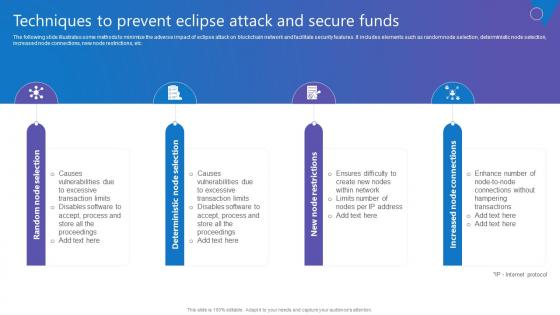
Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Create an editable Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc.

Damage Security Insurance Proposal Cover Letter For Liability Insurance Proposal Ppt Slides Graphic Tips PDF
Presenting damage security insurance proposal cover letter for liability insurance proposal ppt slides graphic tips pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cover letter. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf
This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools Create an editable Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools
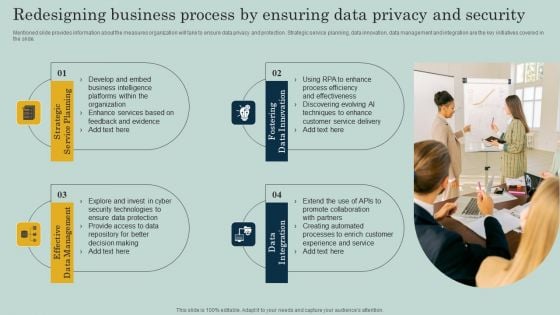
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
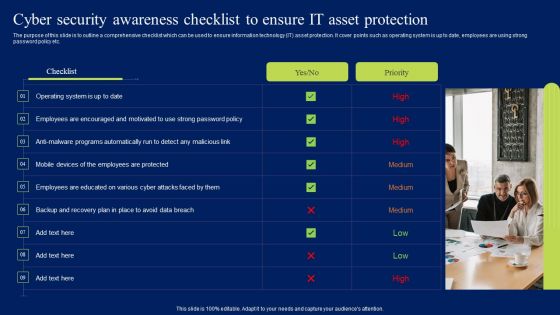
Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
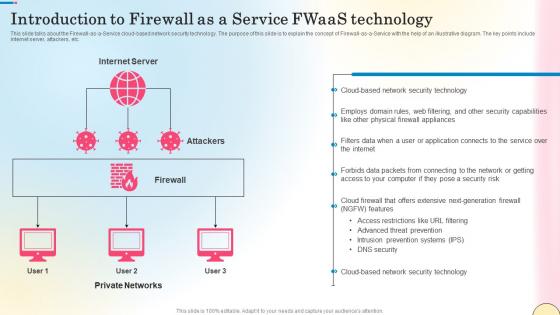
Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf
This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc. Retrieve professionally designed Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc.
Safety Breach Response Playbook Classifying Various Security Issues And Attacks Icons PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Retrieve professionally designed Safety Breach Response Playbook Classifying Various Security Issues And Attacks Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
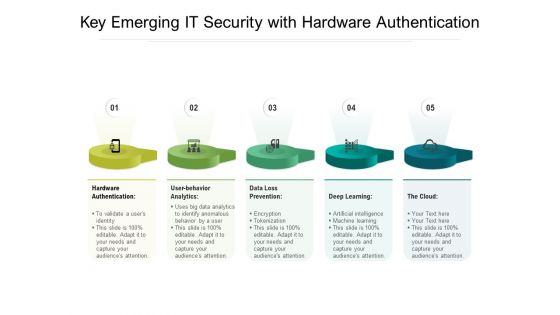
Key Emerging IT Security With Hardware Authentication Ppt PowerPoint Presentation Gallery File Formats PDF
Persuade your audience using this key emerging it security with hardware authentication ppt powerpoint presentation gallery file formats pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hardware authentication, user behavior analytics, data loss prevention, deep learning, the cloud. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
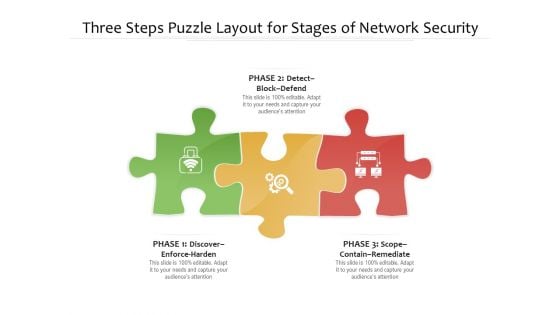
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
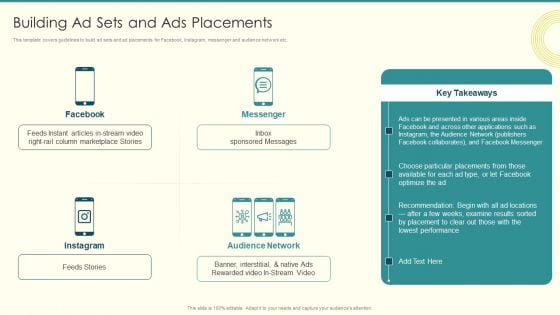
Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF
This template covers guidelines to build ad sets and ad placements for Facebook, Instagram, messenger and audience network etc. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF. Use them to share invaluable insights on Column Marketplace, Presented Various, Choose Particular and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
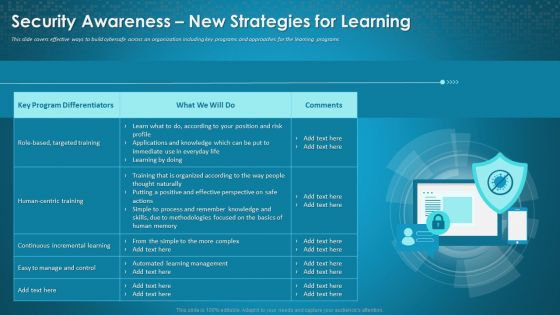
Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact On Food Demand And Food Security Due To Covid Crisis Ppt Pictures Layout PDF
This template covers Impact On Food Demand And Food Security such as demand of food has affected due to reduction in income and purchasing capacity. It also covers the impact of school closure on childrens who are dependent on school meal programs. This is a impact on food demand and food security due to covid crisis ppt pictures layout pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management strategy, price, source, services, production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
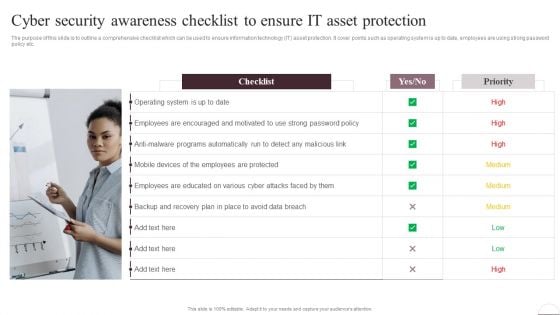
Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
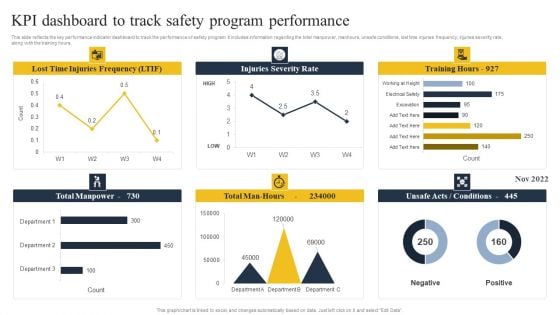
Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF
This slide reflects the key performance indicator dashboard to track the performance of safety program. It includes information regarding the total manpower, manhours, unsafe conditions, lost time injuries frequency, injuries severity rate, along with the training hours. Create an editable Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Control Techniques For Real Estate Project KPI Dashboard To Track Safety Program Performance Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Companys Data Safety Recognition Security Awareness New Strategies For Learning Diagrams PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security awareness new strategies for learning diagrams pdf. Use them to share invaluable insights on learning management, methodologies, risk profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
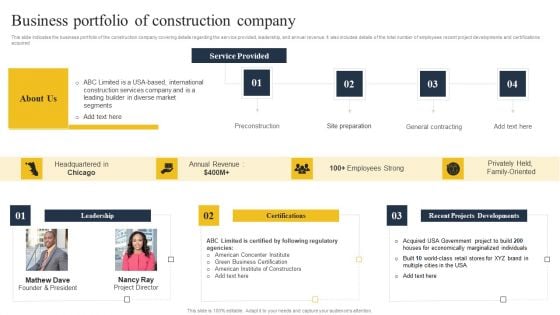
Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
This slide indicates the business portfolio of the construction company covering details regarding the service provided, leadership, and annual revenue. It also includes details of the total number of employees recent project developments and certifications acquired. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
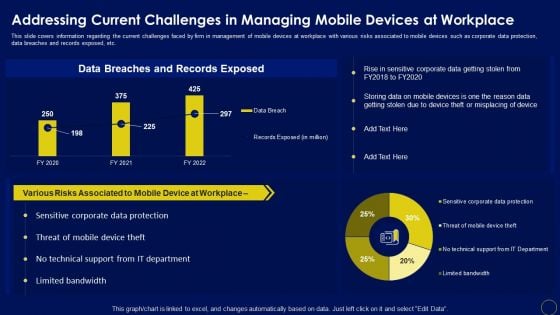
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Real Time Assessment Of Security Threats Calculating Network Device Velocity Sizing Portrait PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Deliver an awe inspiring pitch with this creative real time assessment of security threats calculating network device velocity sizing portrait pdf bundle. Topics like calculating network device velocity sizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Three Levels Vertical Layout For Network Security Phases Ppt PowerPoint Presentation Portfolio Background Designs PDF
Persuade your audience using this three levels vertical layout for network security phases ppt powerpoint presentation portfolio background designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
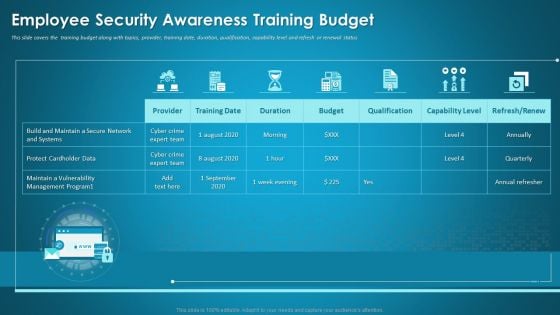
Organizational Network Staff Learning Employee Security Awareness Training Budget Information PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this organizational network staff learning employee security awareness training budget information pdf. Use them to share invaluable insights on capability level, budget, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
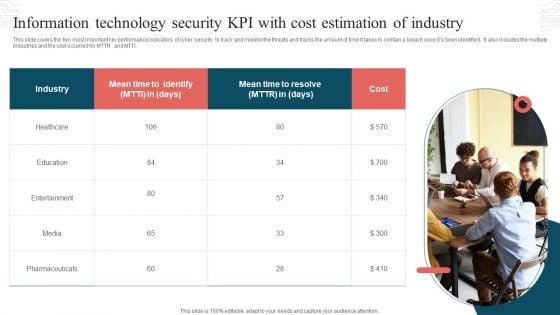
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
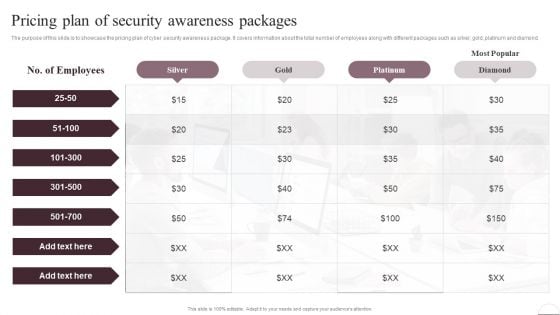
Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
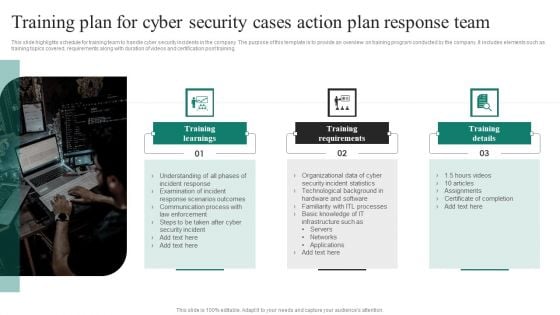
Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF
This slide highlights schedule for training team to handle cyber security incidents in the company. The purpose of this template is to provide an overview on training program conducted by the company. It includes elements such as training topics covered, requirements along with duration of videos and certification post training. Persuade your audience using this Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Training Learnings, Training Requirements, Training Details. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Software Testing Service Differentiators With Digital Security Management Ppt PowerPoint Presentation File Graphics Download PDF
Persuade your audience using this software testing service differentiators with digital security management ppt powerpoint presentation file graphics download pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including attractive design, enterprise solutions, software testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Companys Data Safety Recognition Employee Security Awareness Training Budget Formats PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative companys data safety recognition employee security awareness training budget formats pdf bundle. Topics like budget, capability level, training date, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
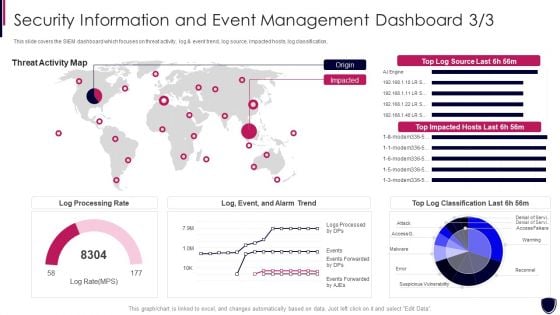
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































