Network Security
Framework For Improving Critical Infra Cyber Security Icons PDF
The following slide exhibits framework for protection, resilience of infrastructure and other sectors important to national security. It presents information related to protection, responding, etc. Showcasing this set of slides titled Framework For Improving Critical Infra Cyber Security Icons PDF. The topics addressed in these templates are Identify, Protect, Detect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Companys Data Safety Recognition Security Awareness Program Checklist Portrait PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a companys data safety recognition security awareness program checklist portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, security awareness program, sustaining security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
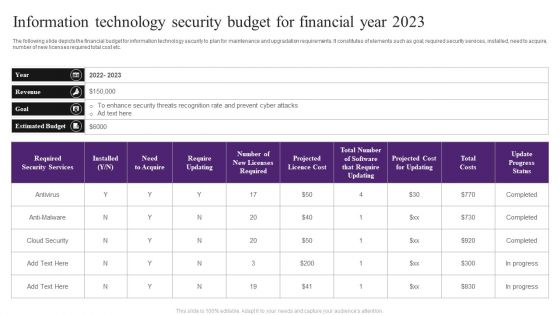
Information Technology Security Budget For Financial Year 2023 Slides PDF
The following slide depicts the financial budget for information technology security to plan for maintenance and upgradation requirements. It constitutes of elements such as goal, required security services, installed, need to acquire, number of new licenses required total cost etc. Showcasing this set of slides titled Information Technology Security Budget For Financial Year 2023 Slides PDF. The topics addressed in these templates are Enhance Security, Estimated Budget, Cloud Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Business Cyber Security Assessment Protection Icon Ideas PDF
Presenting Business Cyber Security Assessment Protection Icon Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Protection Icon, Business Cyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infra Cyber Security Icon For Infrastructure Protection Information PDF
Presenting Infra Cyber Security Icon For Infrastructure Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Infrastructure Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Plan Critical Success Factors Formats PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this current security management plan critical success factors formats pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
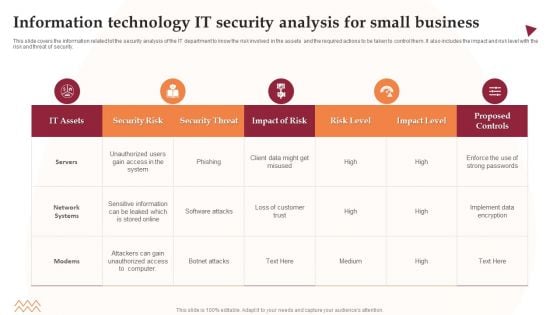
Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Threat Management Strategy With Strategies Ideas PDF
This slide focuses on the security risk mitigation plan which covers security components, vulnerabilities and mitigation strategies such as administrative, physical, technical and organizational safeguards with conducting workforce training, installing alarm systems, etc. Showcasing this set of slides titled Security Threat Management Strategy With Strategies Ideas PDF. The topics addressed in these templates are Security Component, Examples Of Vulnerabilities, Security Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
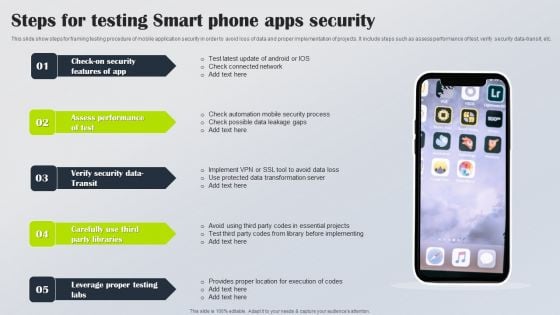
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
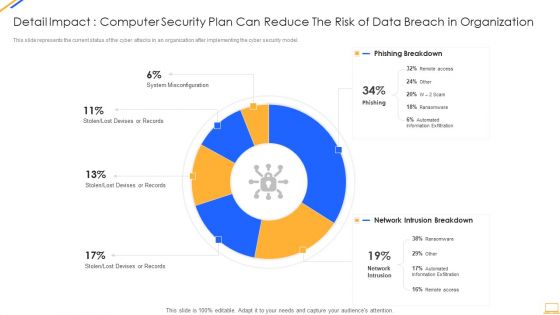
Desktop Security Management Detail Impact Computer Designs PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this desktop security management detail impact computer designs pdf. Use them to share invaluable insights on detail impact computer security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
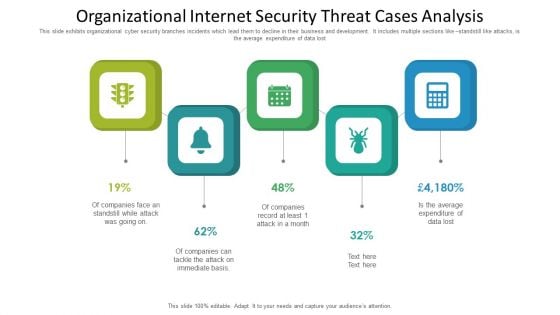
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
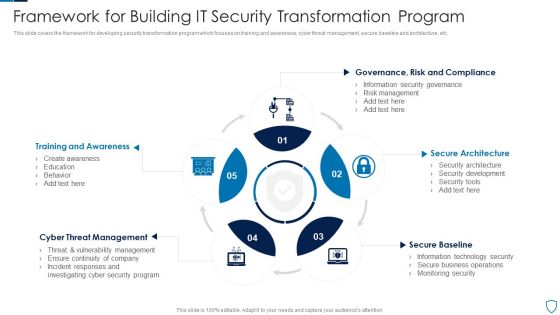
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
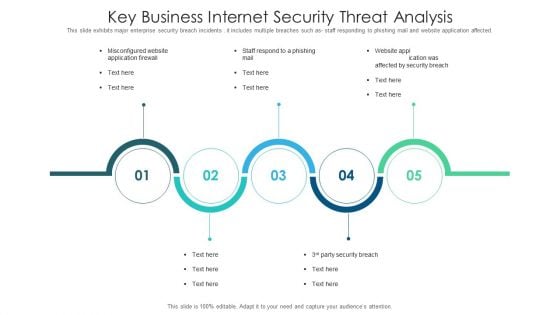
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
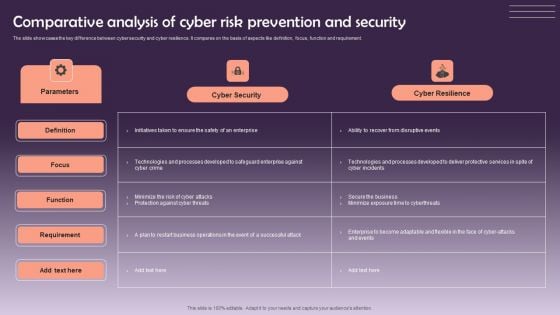
Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF
The slide showcases the key difference between cyber security and cyber resilience. It compares on the basis of aspects like definition, focus, function and requirement. Showcasing this set of slides titled Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF. The topics addressed in these templates are Cyber Security, Cyber Resilience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
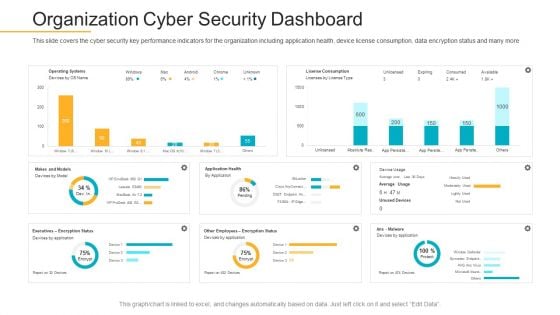
Data Breach Prevention Recognition Organization Cyber Security Dashboard Demonstration PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
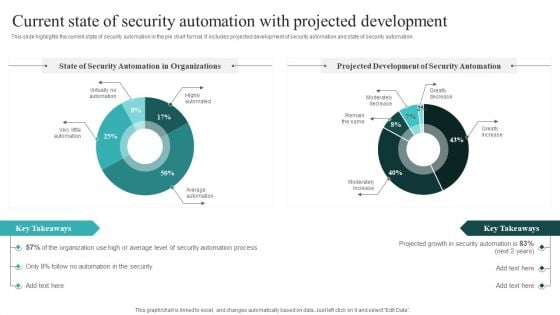
Current State Of Security Automation With Projected Development Slides PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Virus Assistant Performing Concentration Determining Security Powerpoint Ppt Template Bundles
This Virus Assistant Performing Concentration Determining Security Powerpoint Ppt Template Bundles is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This twelve-slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now. Designed, these Concentration Determining Security slides under Our Virus Assistant Perform, our presenters intend to ensure easy follow-up regarding your audience about getting insights from whats inside- that virus, detection concentration measures, and safety. The methodology in detecting these viruses and concentrations using these templates puts your focus sharply.

Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc.

Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising seventeen this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Security Strategic Agenda Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.
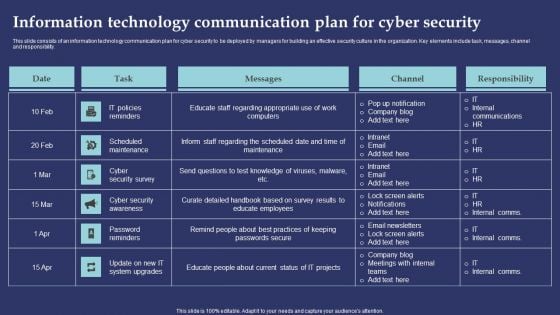
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
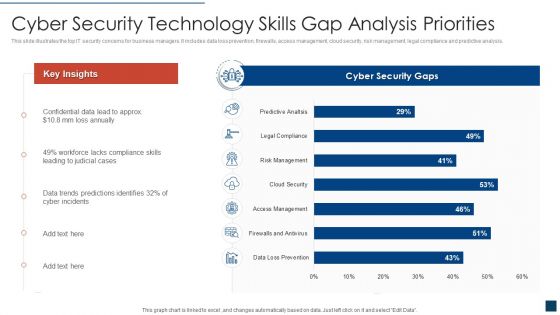
Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF
The following slide shows cyber analytics dashboard to monitor and inspect threats and accordingly plan preventive actions. It includes open and resolved incidents and tickets. Pitch your topic with ease and precision using this Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF. This layout presents information on Energy Security Team, Digital Security Center, Security Operations Center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
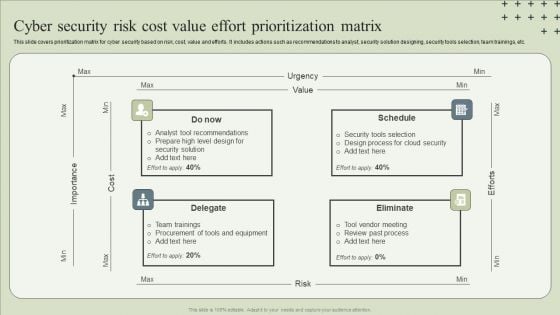
Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF
This slide covers prioritization matrix for cyber security based on risk, cost, value and efforts. It includes actions such as recommendations to analyst, security solution designing, security tools selection, team trainings, etc.Presenting Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Tool Recommendations, Design Process, Team Trainings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
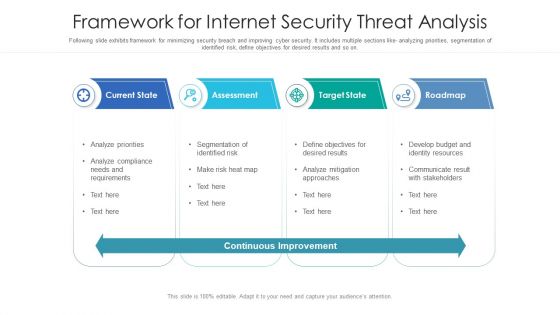
Framework For Internet Security Threat Analysis Structure PDF
Following slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like- analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Showcasing this set of slides titled framework for internet security threat analysis structure pdf. The topics addressed in these templates are current state, assessment, target state, roadmap. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
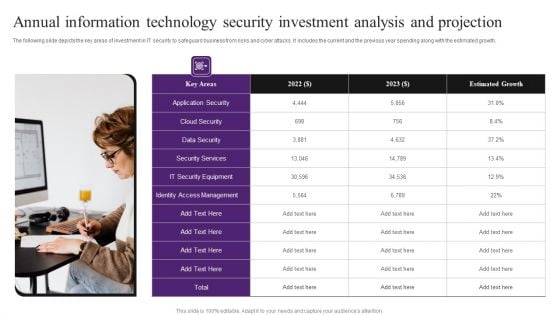
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
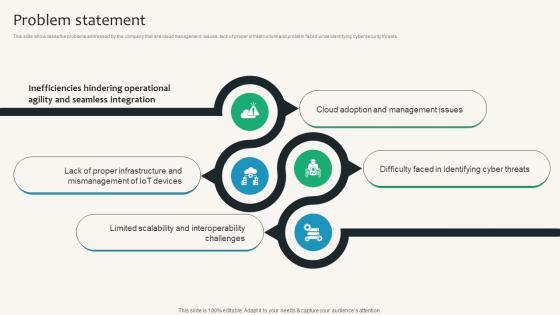
Problem Statement Security Service Provider Business Model BMC SS V
This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Security Service Provider Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Security Service Provider Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats.

Protected Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with folder They say appropriate facial expressions aid communication. Our Protected Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211 can be effective too.
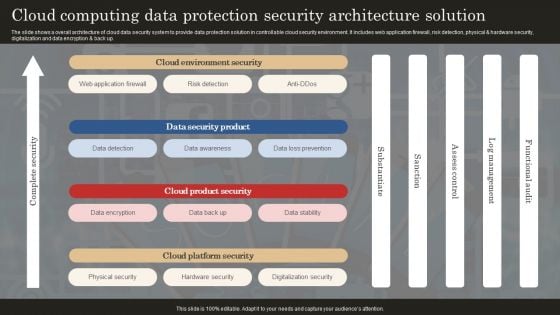
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
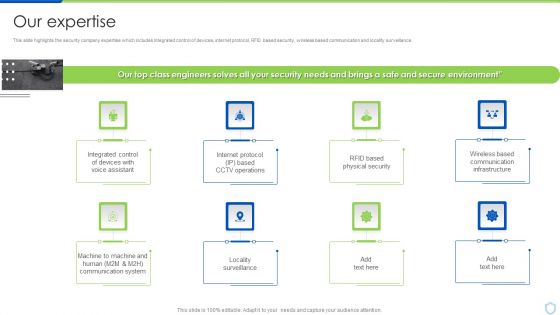
Security And Surveillance Company Profile Our Expertise Professional PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Presenting Security And Surveillance Company Profile Our Expertise Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Secure Environment, Communication Infrastructure, Physical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
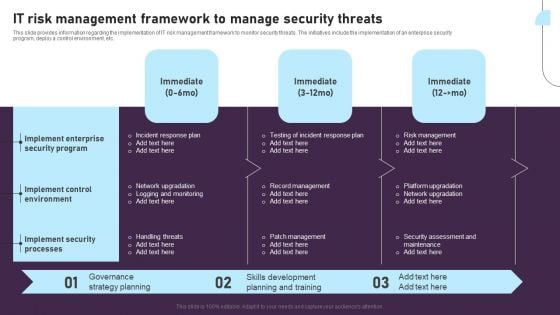
IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
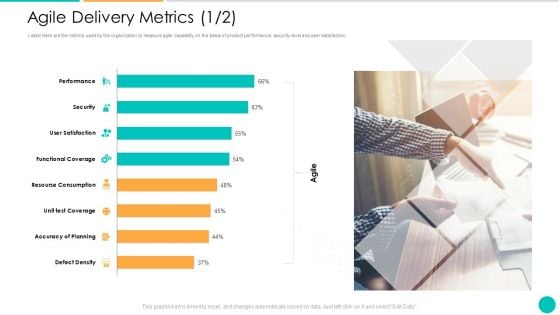
DAD Framework Agile Delivery Metrics Security Ppt Ideas Skills PDF
Listed Here are the metrics used by the organization to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver and pitch your topic in the best possible manner with this DAD framework agile delivery metrics security ppt ideas skills pdf. Use them to share invaluable insights on security, accuracy of planning, functional coverage, performance, resourse consumption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Internet Things Security Concerns Ppt PowerPoint Presentation Show Picture Cpb
Presenting this set of slides with name internet things security concerns ppt powerpoint presentation show picture cpb. This is an editable Powerpoint four stages graphic that deals with topics like internet things security concerns to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
The Roi Of Security Awareness Training Ppt Infographics Icon PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber conscious workforce. Deliver an awe inspiring pitch with this creative the roi of security awareness training ppt infographics icon pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
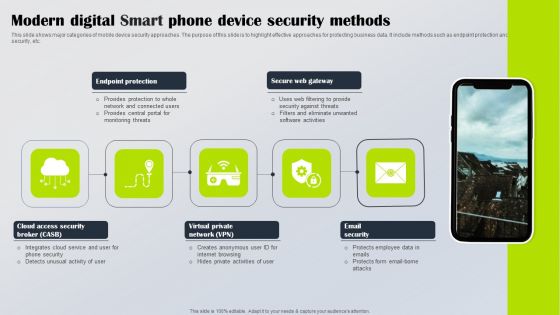
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
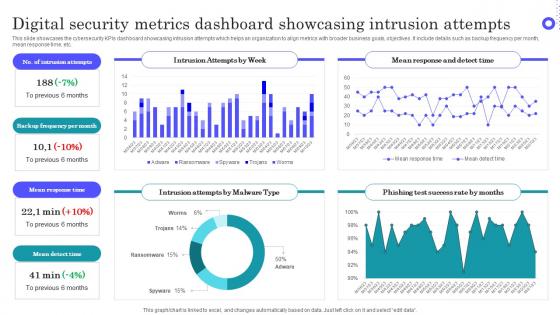
Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf This layout presents information on Intrusion Attempts, Frequency Per Month, Mean Response Time It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cybersecurity KPIs dashboard showcasing intrusion attempts which helps an organization to align metrics with broader business goals, objectives. It include details such as backup frequency per month, mean response time, etc.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.

Smart Home Security Solutions Company Profile Our Expertise Sample PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Our Expertise Sample PDF bundle. Topics like Integrated Control Devices, Internet Protocol Based, RFID Based Physical, Wireless Based Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
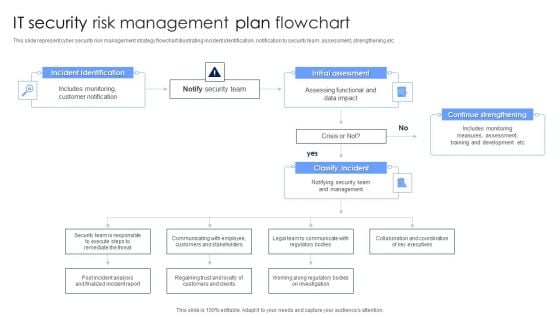
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
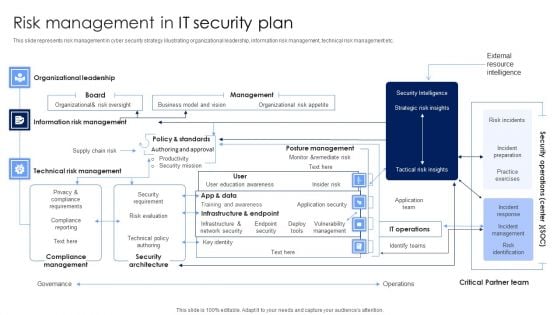
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
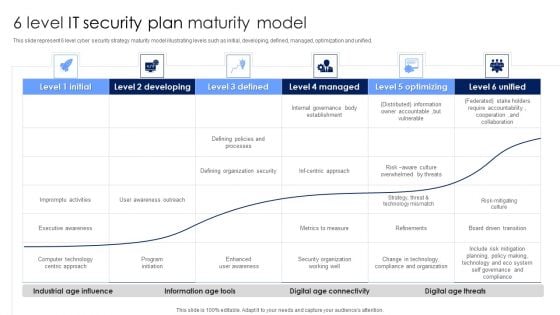
6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
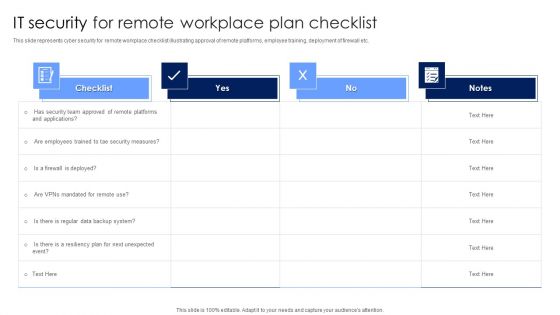
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
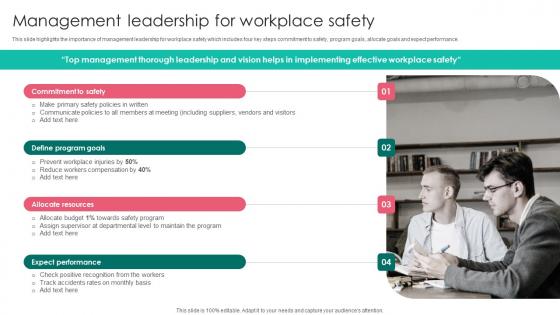
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
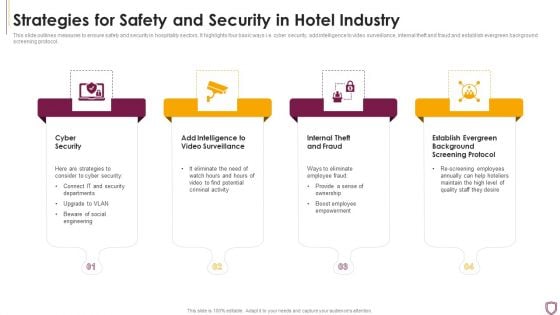
Strategies For Safety And Security In Hotel Industry Sample PDF
This slide outlines measures to ensure safety and security in hospitality sectors. It highlights four basic ways i.e. cyber security, add intelligence to video surveillance, internal theft and fraud and establish evergreen background screening protocol.Persuade your audience using this Strategies For Safety And Security In Hotel Industry Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Internal Theft And Fraud, Establish Evergreen Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
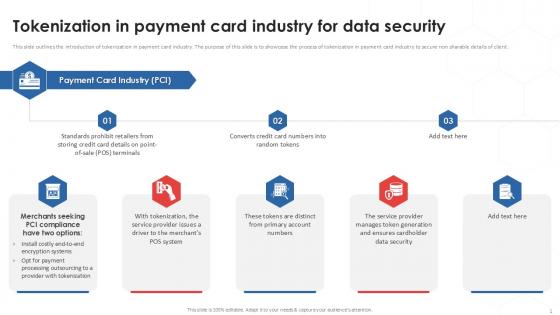
Tokenization In Payment Card Industry For Data Security PPT Sample
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Boost your pitch with our creative Tokenization In Payment Card Industry For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
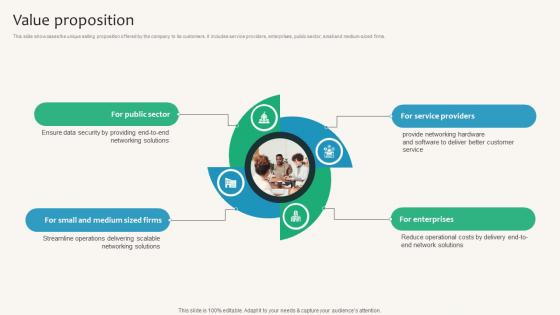
Value Proposition Security Service Provider Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition Security Service Provider Business Model BMC SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms.
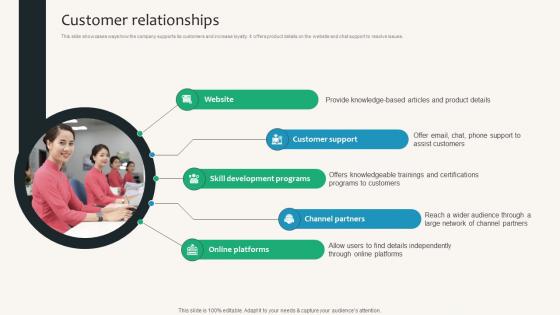
Customer Relationships Security Service Provider Business Model BMC SS V
This slide showcases ways how the company supports its customers and increase loyalty. It offers product details on the website and chat support to resolve issues. Want to ace your presentation in front of a live audience Our Customer Relationships Security Service Provider Business Model BMC SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases ways how the company supports its customers and increase loyalty. It offers product details on the website and chat support to resolve issues.
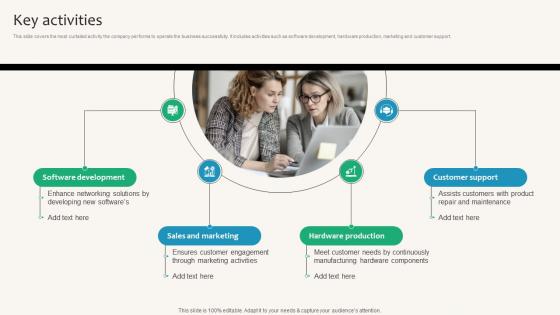
Key Activities Security Service Provider Business Model BMC SS V
This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Security Service Provider Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support.
Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF
Presenting Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Eliminating Cyber Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Icon For Cyber Threat Prevention Information PDF
Presenting Cyber Security Icon For Cyber Threat Prevention Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Security, Icon Cyber Threat, Prevention. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
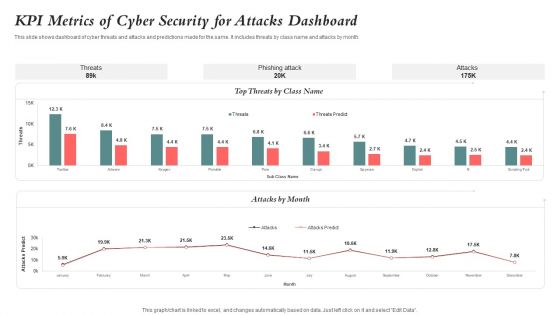
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Camera System Company Profile Awards And Accolades Portrait PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Awards And Accolades Portrait PDF bundle. Topics like Digital Trends, Consumer Technology, Technology Association can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
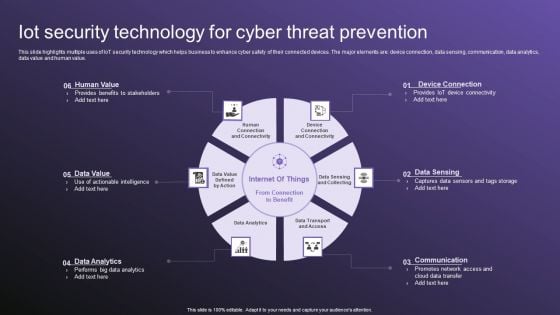
Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































