Network Security
System Security Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled System Security Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits System Security Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our System Security Diagram In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb
Introducing our well-designed Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Lifeshield Security Projects Johannesburg. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
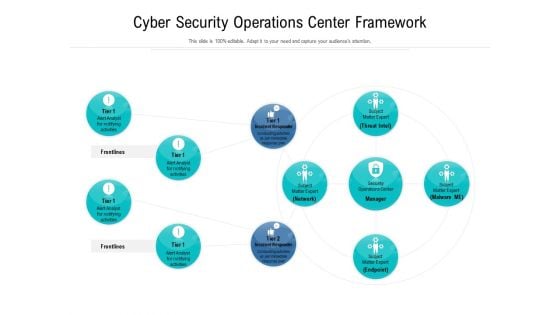
Cyber Security Operations Center Framework Ppt Styles Portfolio PDF
Showcasing this set of slides titled cyber security operations center framework ppt styles portfolio pdf. The topics addressed in these templates are cyber security operations center framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
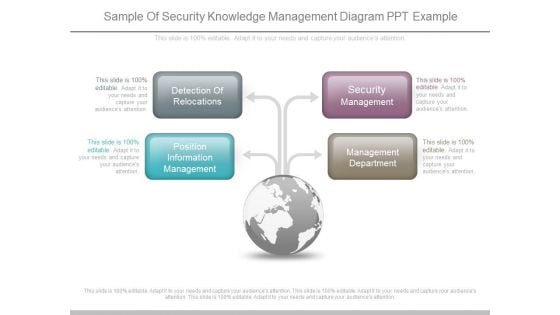
Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.
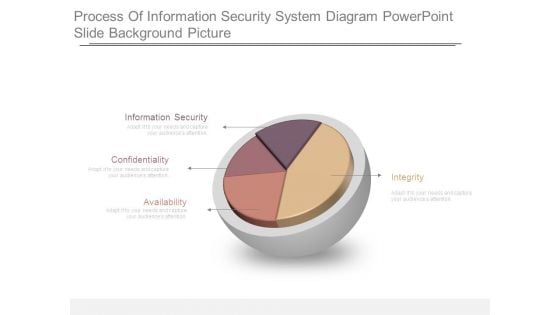
Process Of Information Security System Diagram Powerpoint Slide Background Picture
This is a process of information security system diagram powerpoint slide background picture. This is a four stage process. The stages in this process are information security, confidentiality, availability, integrity.
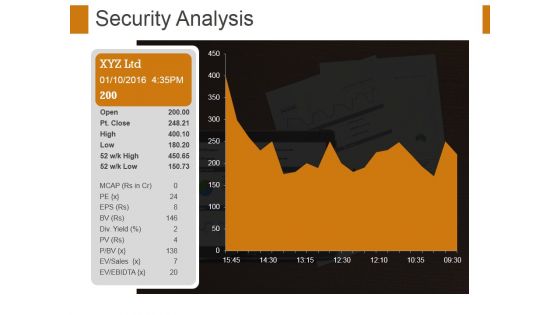
Security Analysis Ppt PowerPoint Presentation File Format Ideas
This is a security analysis ppt powerpoint presentation file format ideas. This is a one stage process. The stages in this process are security analysis, growth, strategy, management, business.
Security Risk Intelligence Collaborative Communities Ppt PowerPoint Presentation Model Styles
This is a security risk intelligence collaborative communities ppt powerpoint presentation model styles. This is a seven stage process. The stages in this process are security risk intelligence, collaborative communities.

Employee Benefits Social Security Ppt PowerPoint Presentation Infographics Graphics Design
This is a employee benefits social security ppt powerpoint presentation infographics graphics design. This is a eight stage process. The stages in this process are social security, pay raise, health insurance, employees allowance.

Computer Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a computer security ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are computer security, business, planning, strategy, marketing.

It Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a . This is a one stage process it security ppt powerpoint presentation complete deck with slides. The stages in this process are it security, business, management, planning, strategy.
Operating Model Tiered Security Metrics Ppt PowerPoint Presentation Model Examples
This is a operating model tiered security metrics ppt powerpoint presentation model examples. This is a six stage process. The stages in this process are business, management, strategy, security, planning.
Enterprise Security Systems Ppt PowerPoint Presentation File Picture Cpb
This is a enterprise security systems ppt powerpoint presentation file picture cpb. This is a five stage process. The stages in this process are enterprise security systems, business, management, marketing.

It Security Risk Management Ppt Powerpoint Presentation Outline Guidelines Cpb
This is a it security risk management ppt powerpoint presentation outline guidelines cpb. This is a five stage process. The stages in this process are it security risk management.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
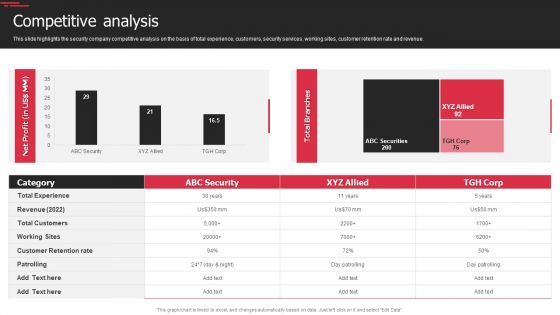
Security Agency Business Profile Competitive Analysis Designs PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Competitive Analysis Designs PDF bundle. Topics like Revenue, Customer Retention Rate, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Data Security In Cloud Computing Ppt Powerpoint
Present like a pro with Agenda For Data Security In Cloud Computing Ppt Powerpoint. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Agenda For Data Security In Cloud Computing Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Diagram Security Market Line PowerPoint Ppt Presentation
Make Some Dough With Our Business Diagram Security Market Line PowerPoint PPT Presentation PowerPoint Templates. Yours Assets Will Rise Significantly.
Security Awareness Tracking Kpis Ppt Slides Shapes PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. Deliver and pitch your topic in the best possible manner with this security awareness tracking kpis ppt slides shapes pdf. Use them to share invaluable insights on security awareness tracking kpis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Challenges The Company Is Facing Demonstration PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers. Deliver an awe inspiring pitch with this creative current security management challenges the company is facing demonstration pdf bundle. Topics like potential insider threats, external security breaches, employee management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Suggested Coverage For Security Management Plan Information PDF
This slide provides information about the areas that are covered under the security management plan. This is a suggested coverage for security management plan information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance arrangement, information including ict security, personnel security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Security Management Challenges The Company Is Facing Microsoft PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers. Deliver an awe inspiring pitch with this creative current security management challenges the company is facing microsoft pdf bundle. Topics like environments, security risk , information, design, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Measures And Ways To Mitigate Security Management Challenges Icons PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver and pitch your topic in the best possible manner with this measures and ways to mitigate security management challenges icons pdf. Use them to share invaluable insights on information, security training, implementing, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
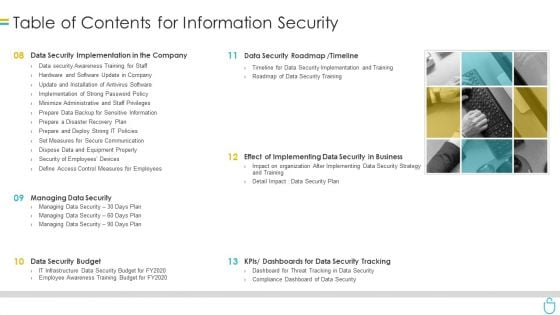
Table Of Contents For Information Security Ppt Styles Outline PDF
Presenting table of contents for information security ppt styles outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security implementation, data security roadmap, data security budget, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
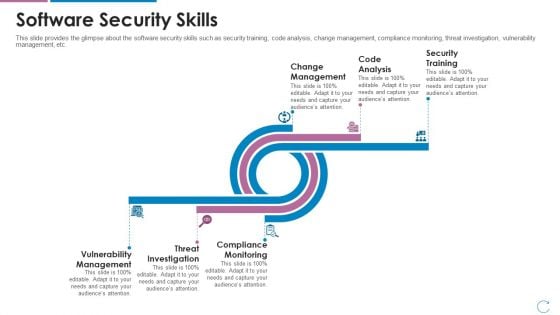
Devops Team Capabilities IT Software Security Skills Ppt Deck PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Deliver an awe inspiring pitch with this creative devops team capabilities it software security skills ppt deck pdf bundle. Topics like change management, code analysis, security training, vulnerability management, threat investigation, compliance monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cloud Data Security System Infographics PDF
This is a Table Of Contents For Cloud Data Security System Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Working Of Cloud Security, Cloud Security Management, Cloud Security Solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Ideas PDF
Presenting Table Of Contents For Cloud Security Assessment Ideas PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Cloud Security, Security Different, Security Is Important. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Awards And Accolades Sample PDF
This slide highlights the awards and allocates received by security company which includes best security company, community member award, great place to work and corporate excellence awards. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Awards And Accolades Sample PDF bundle. Topics like Community, Global Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
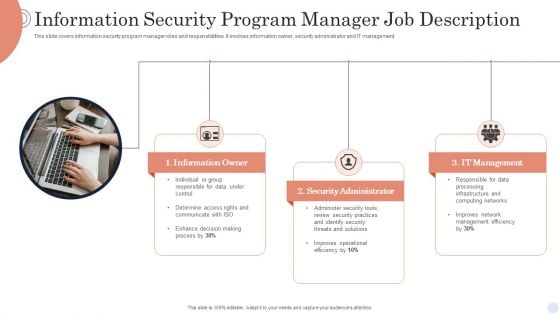
Information Security Program Manager Job Description Background PDF
This slide covers information security program manager roles and responsibilities. It involves information owner, security administrator and IT management. Presenting Information Security Program Manager Job Description Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Owner, Security Administrator, It Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
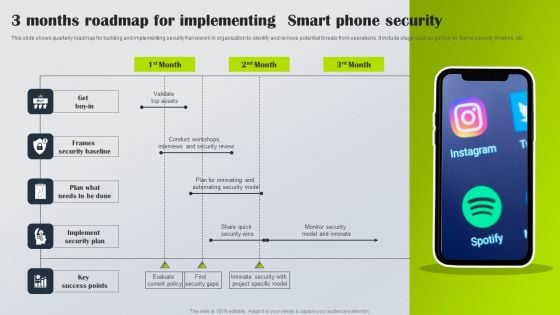
3 Months Roadmap For Implementing Smart Phone Security Information PDF
This slide shows quarterly roadmap for building and implementing security framework in organization to identify and remove potential threats from operations. It include stage such as get buy-in, frame security timeline, etc. Presenting 3 Months Roadmap For Implementing Smart Phone Security Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Get Buy In, Frames Security Baseline, Implement Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
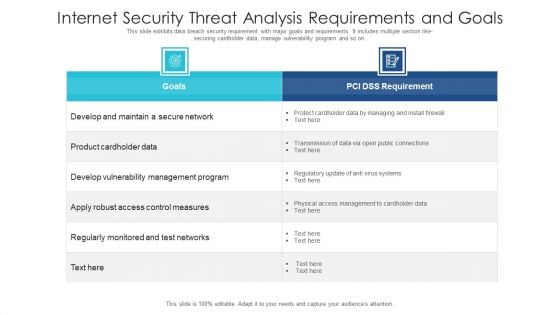
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IOT Cyber Security Ppt PowerPoint Presentation Layouts Clipart Cpb
Presenting this set of slides with name iot cyber security ppt powerpoint presentation layouts clipart cpb. This is an editable Powerpoint four stages graphic that deals with topics like iot cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Measures And Ways To Mitigate Security Management Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges formats pdf bundle. Topics like potential insider threats, external security breaches, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Elements Of Security Monitoring Plan Background PDF
Deliver an awe inspiring pitch with this creative essential elements of security monitoring plan background pdf bundle. Topics like critical infrastructure, application security, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
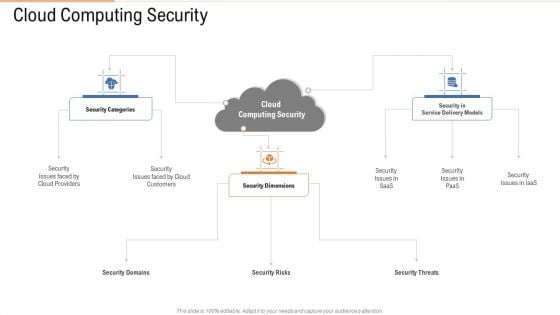
Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
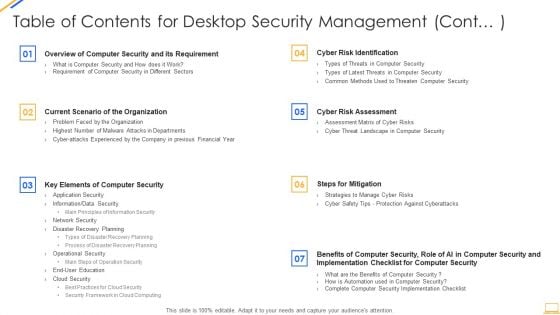
Table Of Contents For Desktop Security Management Cont Ideas PDF
Deliver an awe inspiring pitch with this creative table of contents for desktop security management cont ideas pdf bundle. Topics like security implementation, security budget, dashboards, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
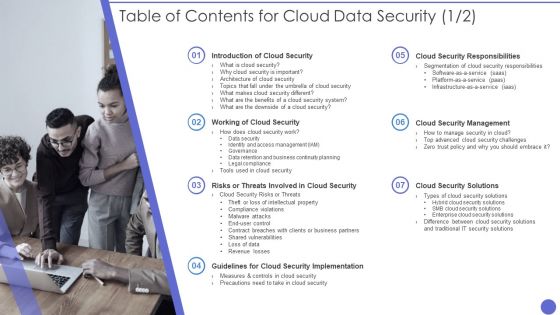
Table Of Contents For Cloud Data Security Formats PDF
Presenting Table Of Contents For Cloud Data Security Formats PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Security, Security System, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
NIST Cybersecurity Framework For Cloud Security Icon Background PDF
Persuade your audience using this NIST Cybersecurity Framework For Cloud Security Icon Background PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including NIST Cybersecurity, Framework, Cloud Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Workplace Safety Protocol And Security Practices Information Pdf
Slidegeeks is here to make your presentations a breeze with Agenda For Workplace Safety Protocol And Security Practices Information Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Agenda For Workplace Safety Protocol And Security Practices Information Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
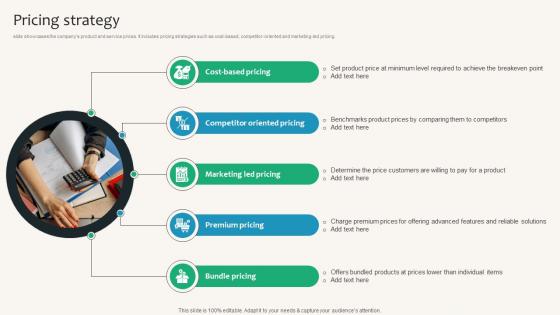
Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing.
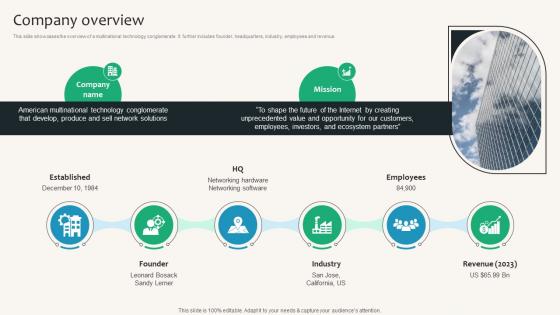
Company Overview Security Service Provider Business Model BMC SS V
This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue. Create an editable Company Overview Security Service Provider Business Model BMC SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Company Overview Security Service Provider Business Model BMC SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue.
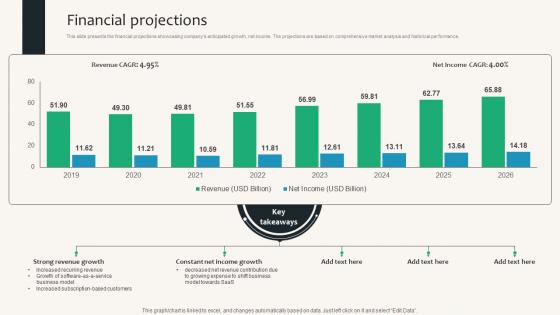
Financial Projections Security Service Provider Business Model BMC SS V
This slide presents the financial projections showcasing companys anticipated growth, net income. The projections are based on comprehensive market analysis and historical performance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Financial Projections Security Service Provider Business Model BMC SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Financial Projections Security Service Provider Business Model BMC SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents the financial projections showcasing companys anticipated growth, net income. The projections are based on comprehensive market analysis and historical performance.
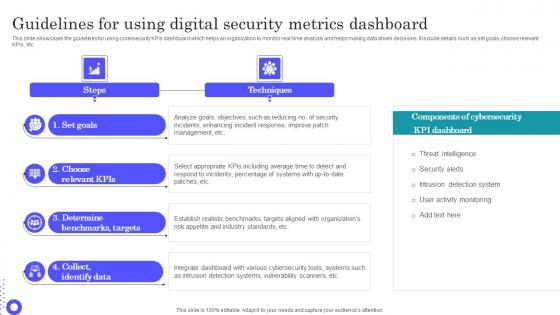
Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf
Pitch your topic with ease and precision using this Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf This layout presents information on Benchmarks Targets, Integrate Dashboard, Incidents Enhancing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the guidelines for using cybersecurity KPIs dashboard which helps an organization to monitor real time analysis and helps making data driven decisions. It include details such as set goals, choose relevant KPIs, etc.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
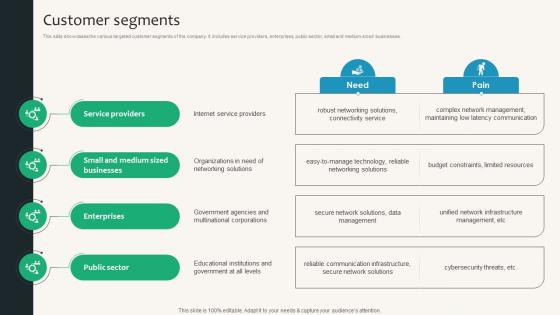
Customer Segments Security Service Provider Business Model BMC SS V
This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses. There are so many reasons you need a Customer Segments Security Service Provider Business Model BMC SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses.

Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF
Persuade Your Audience Using This Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF. This PPT Design Covers Five Stages, Thus Making It A Great Tool To Use. It Also Caters To A Variety Of Topics Including Updating Security Software, Backing Up Data, Block Unreliable Websites. Download This PPT Design Now To Present A Convincing Pitch That Not Only Emphasizes The Topic But Also Showcases Your Presentation Skills.
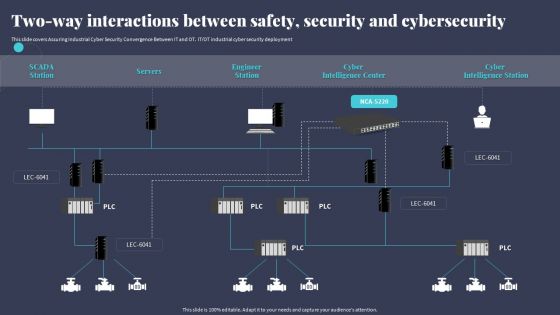
Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
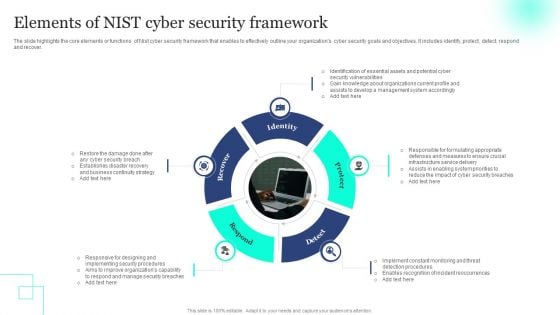
Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
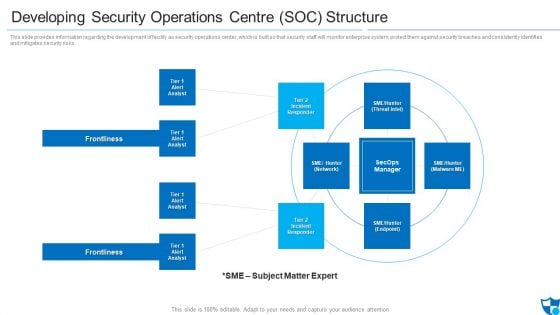
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
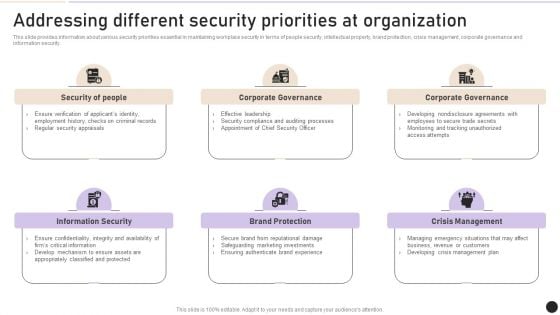
Addressing Different Security Priorities At Organization Clipart PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Find a pre designed and impeccable Addressing Different Security Priorities At Organization Clipart PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
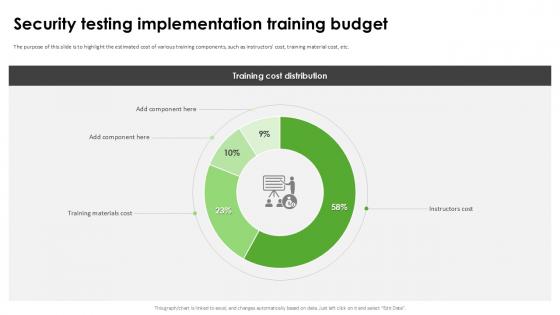
Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation
The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Explore a selection of the finest Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc.
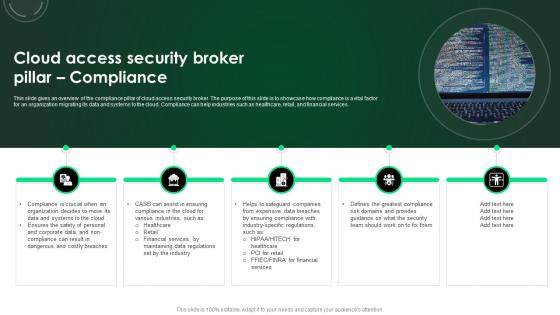
CASB 2 0 IT Cloud Access Security Broker Pillar Compliance
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CASB 2 0 IT Cloud Access Security Broker Pillar Compliance from Slidegeeks and deliver a wonderful presentation. This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services.
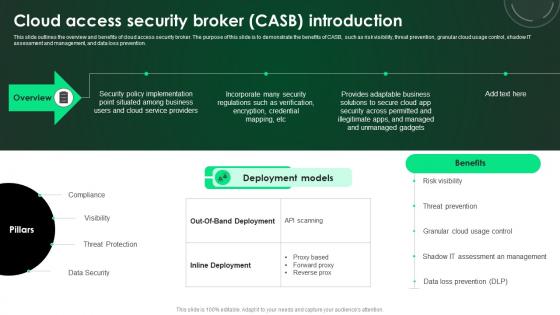
CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention.
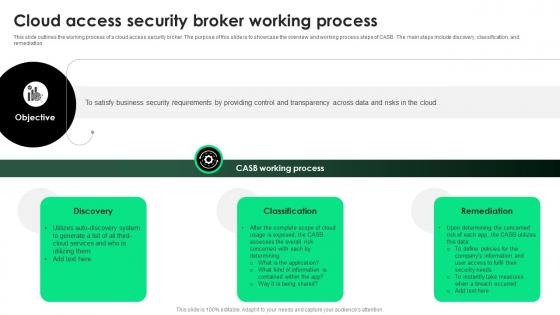
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
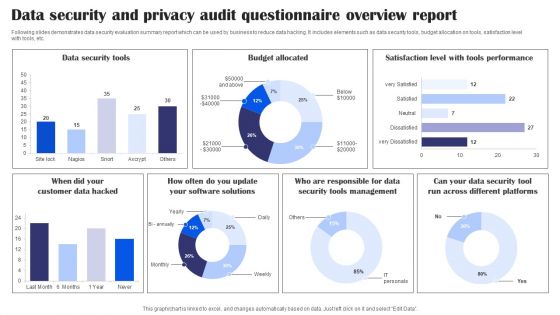
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































