Technology Security

Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112
Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-Use this awesome PowerPoint template for property and ownership concept. This template features golden key with welcome home text. It portrays the concept of home, happiness, investment, mortgage, ownership, property, residence, security etc. This image has been conceived to enable you to emphatically communicate your ideas in your Real Estate PPT presentations. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand.-Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Gold Key With Welcome Home, Security, Business, Technology, Design, Metaphor Flood your audience with great slides with our Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112. Try us out and see what a difference our templates make.
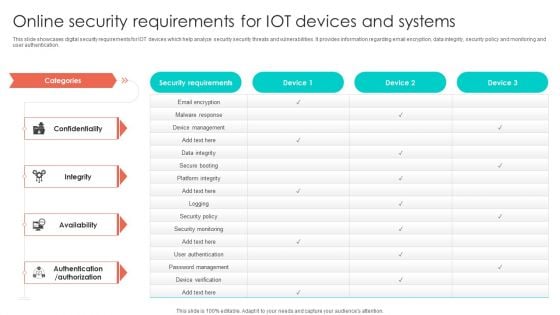
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
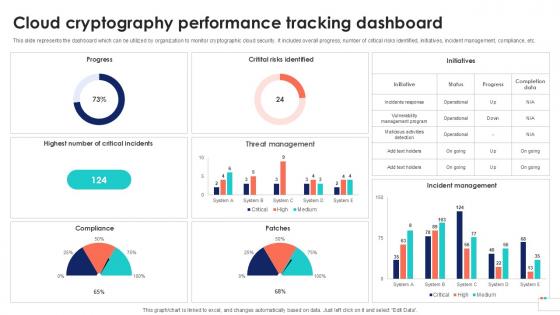
Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.
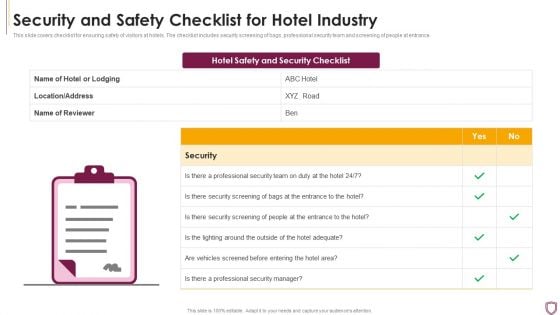
Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
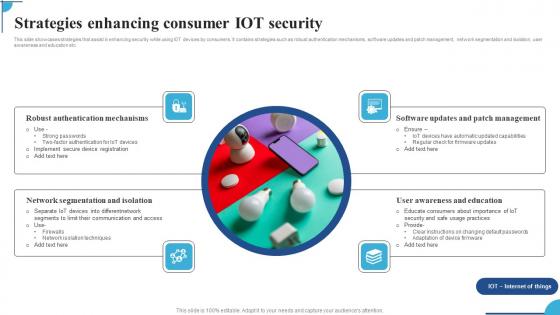
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf
This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner Showcasing this set of slides titled Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf The topics addressed in these templates are Technical Coordinator, Incident Manager, Support Coordinator All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner
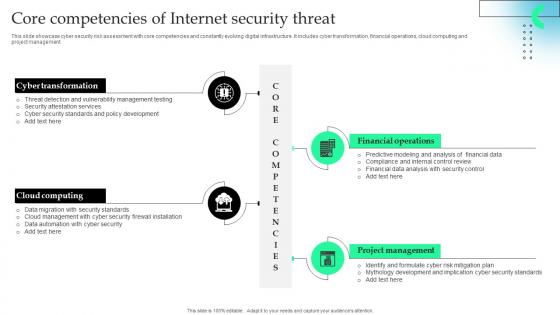
Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.
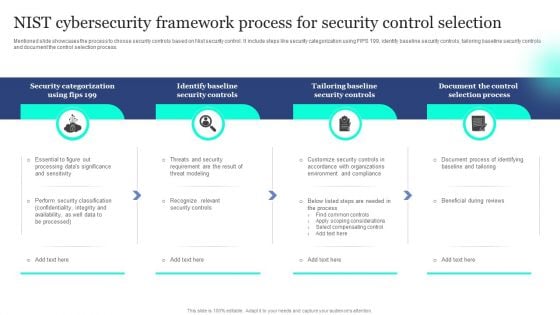
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Radio Military And Security Applications Icon Structure Pdf
Pitch your topic with ease and precision using this Smart Radio Military And Security Applications Icon Structure Pdf. This layout presents information on Smart Radio Military, Security Applications Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Smart Radio Military And Security Applications Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Application Security Testing Ppt Powerpoint Elements
Create an editable Agenda For Application Security Testing Ppt Powerpoint Elements that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Application Security Testing Ppt Powerpoint Elements is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Application Security Testing Ppt Powerpoint Elements are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Instalation Proposal In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Instalation Proposal In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Instalation Proposal that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Instalation Proposal In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
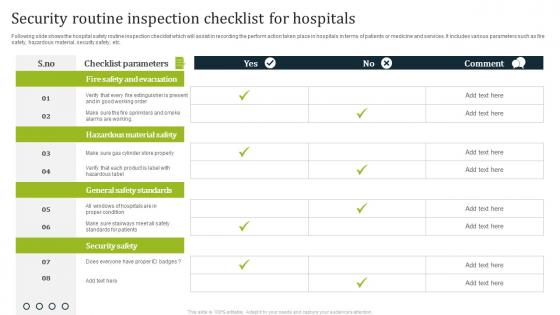
Security Routine Inspection Checklist For Hospitals Diagrams Pdf
Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc. Showcasing this set of slides titled Security Routine Inspection Checklist For Hospitals Diagrams Pdf. The topics addressed in these templates are Checklist Parameters, Comment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.
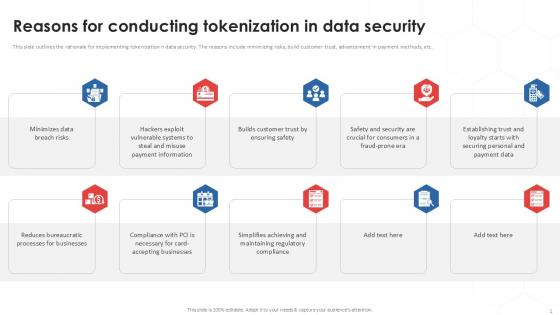
Reasons For Conducting Tokenization In Data Security PPT Template
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
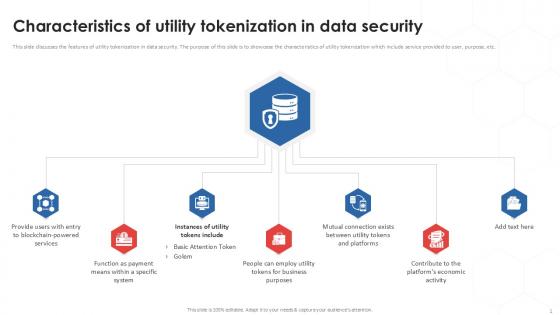
Characteristics Of Utility Tokenization In Data Security PPT Sample
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Find a pre-designed and impeccable Characteristics Of Utility Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.

Personal Security Apps Android In Powerpoint And Google Slides Cpb
Introducing our well designed Personal Security Apps Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Personal Security Apps Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Personal Security Apps Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Application Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Application Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Application Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Global Security In Powerpoint And Google Slides Cpb
Introducing our well designed Icon Global Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Icon Global Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Icon Global Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unblocked Online Security Extension In Powerpoint And Google Slides Cpb
Introducing our well-designed Unblocked Online Security Extension In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Unblocked Online Security Extension. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Unblocked Online Security Extension In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Android Security Malware Detection In Powerpoint And Google Slides Cpb
Introducing our well-designed Android Security Malware Detection In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Android Security Malware Detection. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Android Security Malware Detection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Mobile Android Devices Security In Powerpoint And Google Slides Cpb
Introducing our well designed Mobile Android Devices Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Mobile Android Devices Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Mobile Android Devices Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

E Commerce Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed E Commerce Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like E Commerce Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our E Commerce Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Camera System Business In Powerpoint And Google Slides Cpb
Introducing our well-designed Security Camera System Business In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Camera System Business. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Camera System Business In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
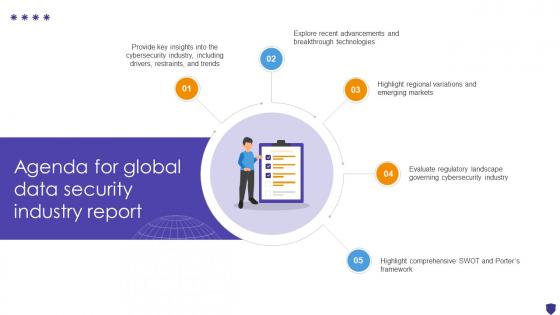
Agenda For Global Data Security Industry Report IR SS V
Find a pre-designed and impeccable Agenda For Global Data Security Industry Report IR SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
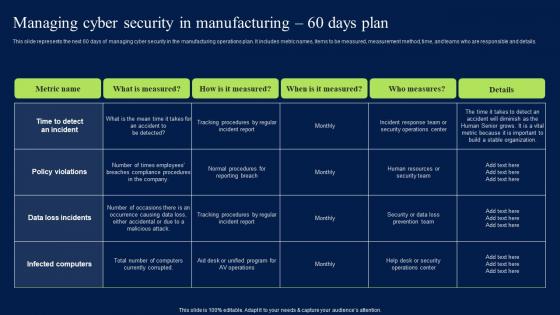
Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
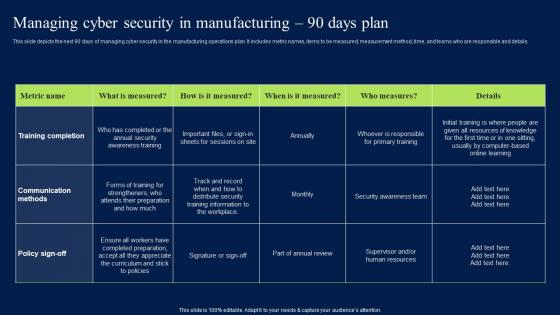
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
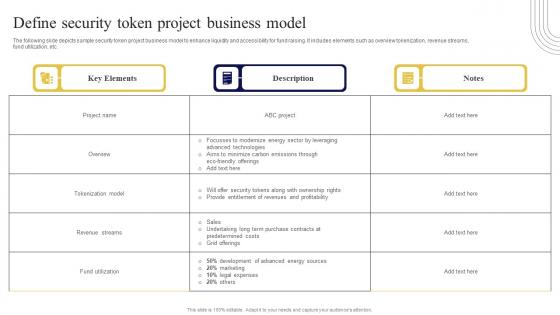
Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf
The following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc.

Zero Trust Security Table Of Contents Ideas Pdf
If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Security Table Of Contents Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Security Table Of Contents Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Zero Trust Security Table Of Contents Ideas Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Training Roadmap that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Reporting Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Reporting Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Reporting Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Reporting Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Best Security Management In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Best Security Management In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Best Security Management that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Best Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Flaw Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Tab Manager Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Tab Manager Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Tab Manager Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Tab Manager Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
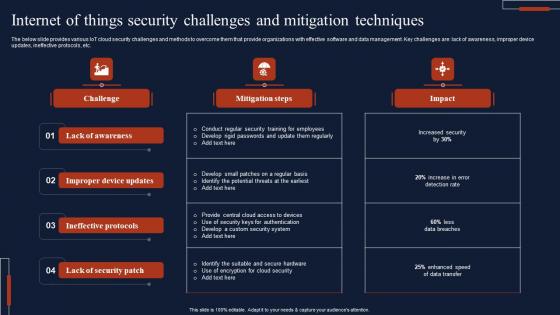
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc.

Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the introduction of encryption in application security for protection of specific fields in an application.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.
Customer Engagement Data Security In Powerpoint And Google Slides Cpb
Introducing our well designed Customer Engagement Data Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Customer Engagement Data Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Customer Engagement Data Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
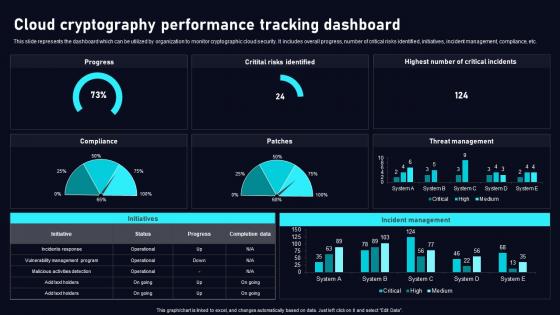
Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.

Best Practices For Tokenization In Data Security PPT Slides
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Boost your pitch with our creative Best Practices For Tokenization In Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.

Challenges And Related Tokenization Strategies For Data Security PPT Sample
This slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc. Boost your pitch with our creative Challenges And Related Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc.
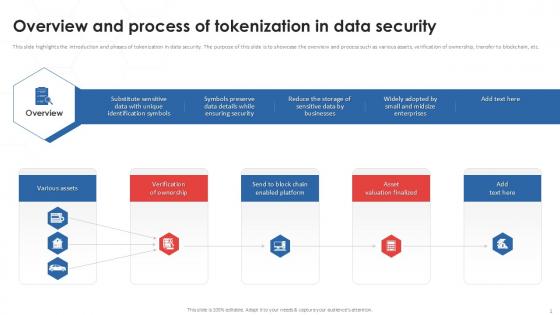
Overview And Process Of Tokenization In Data Security PPT Example
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Find a pre-designed and impeccable Overview And Process Of Tokenization In Data Security PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
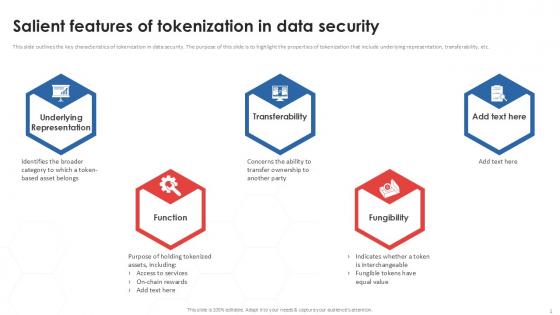
Salient Features Of Tokenization In Data Security PPT Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Boost your pitch with our creative Salient Features Of Tokenization In Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc.
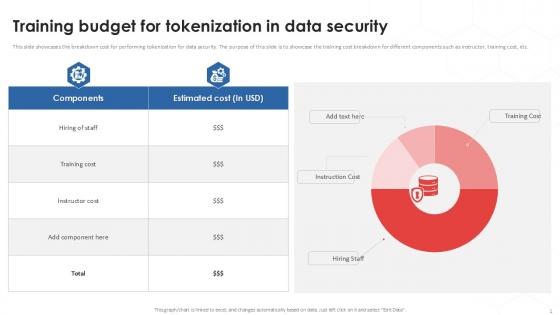
Training Budget For Tokenization In Data Security PPT Template
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. Find a pre-designed and impeccable Training Budget For Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide Security Service Provider Business Model BMC SS V
Download our innovative and attention grabbing Icons Slide Security Service Provider Business Model BMC SS V template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide Security Service Provider Business Model BMC SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Main Features For Robust Application Security Testing Ppt Powerpoint Icons
This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Are you searching for a Main Features For Robust Application Security Testing Ppt Powerpoint Icons that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Features For Robust Application Security Testing Ppt Powerpoint Icons from Slidegeeks today. This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc.

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.
Icons Slide For Application Security Testing Ppt Powerpoint Formats
Download our innovative and attention grabbing Icons Slide For Application Security Testing Ppt Powerpoint Formats template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Application Security Testing Ppt Powerpoint Formats are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
Protections Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Protections Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Protections Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Protections Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf
This modern and well arranged Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
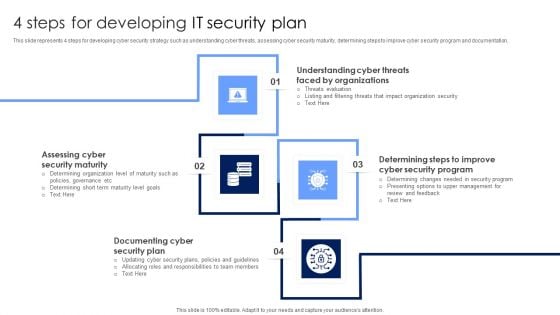
4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
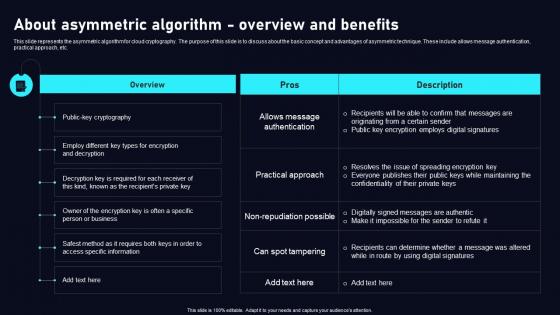
About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Get a simple yet stunning designed About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.

Cyber Deals Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Deals Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Deals Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Deals Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Books In Powerpoint And Google Slides Cpb
Introducing our well-designed Information Security Books In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Books. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Books In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Computer Password Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Computer Password Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Computer Password Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Computer Password Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Password Managers Mac Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Managers Mac Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Managers Mac Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Managers Mac Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































