Technology Security
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
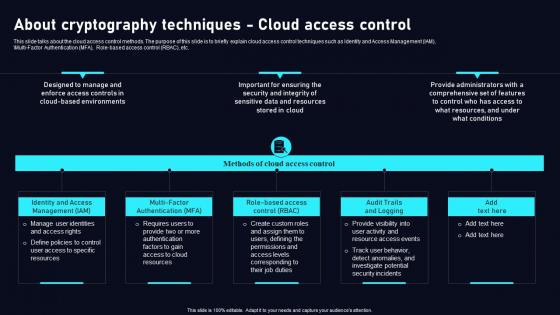
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
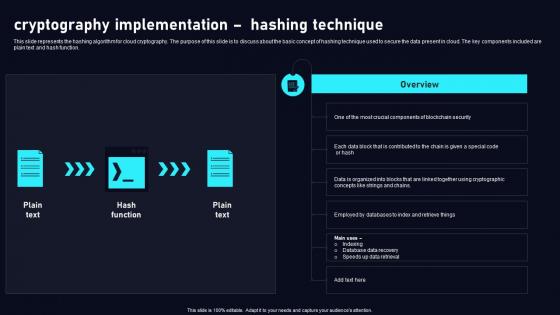
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
IT Security Risk Management Plan Flowchart Diagrams PDF
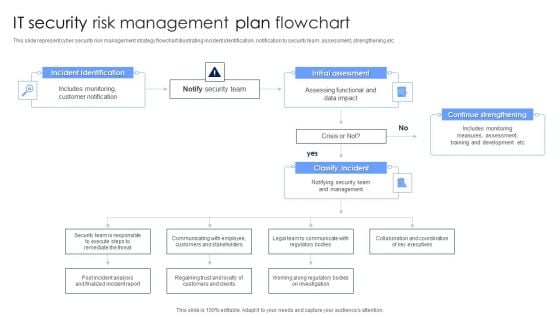
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Risk Management Framework To Manage Security Threats Background PDF
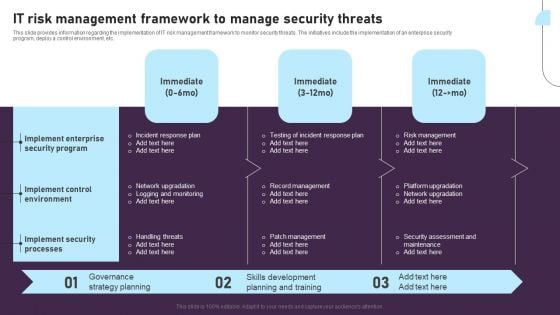
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Companys Data Safety Recognition Security Awareness Training Roadmap Themes PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a companys data safety recognition security awareness training roadmap themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical security, data security, personal information, privacy threats, practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
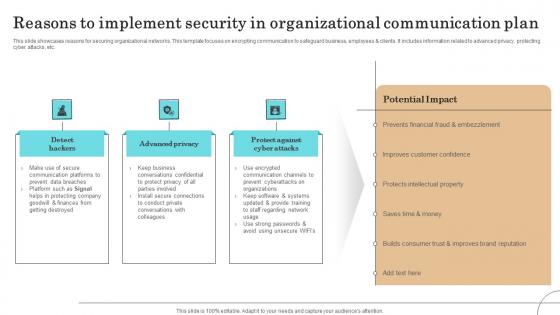
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.
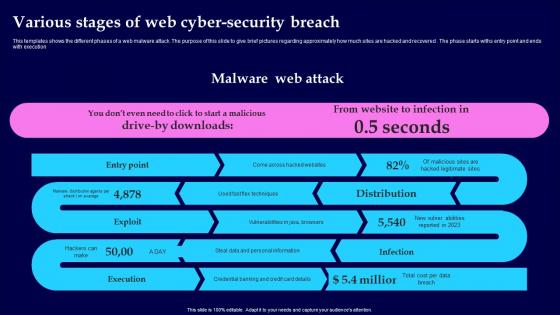
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.
Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
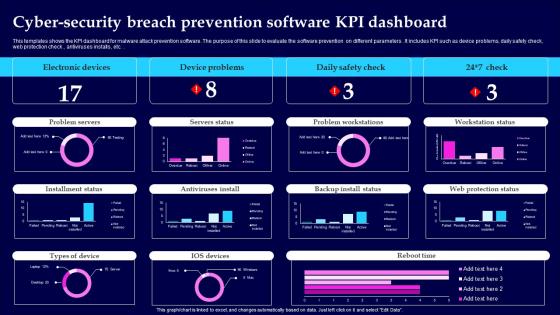
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.
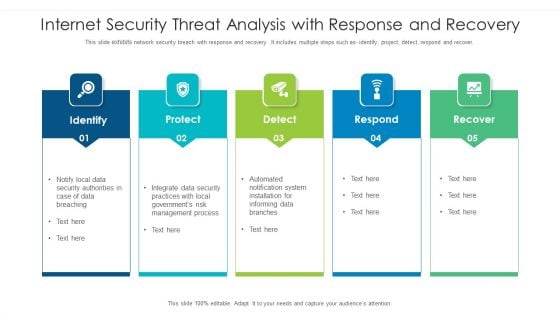
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
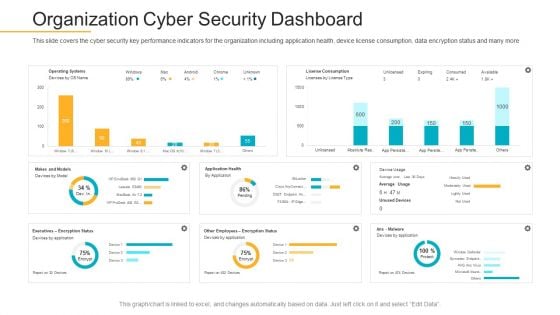
Data Breach Prevention Recognition Organization Cyber Security Dashboard Demonstration PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
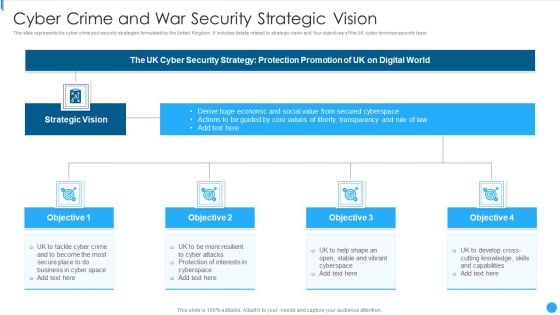
Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Awareness Program Checklist Ppt Model Graphics Design PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness.Presenting security awareness program checklist ppt model graphics design pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating the security awareness program, implementing security awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
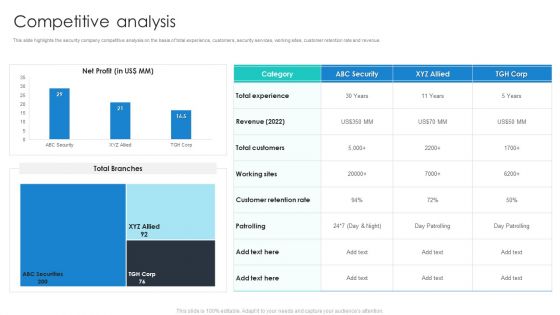
Manpower Corporate Security Business Profile Competitive Analysis Portrait PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Competitive Analysis Portrait PDF bundle. Topics like Revenue, Total Customers, Customer Retention Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
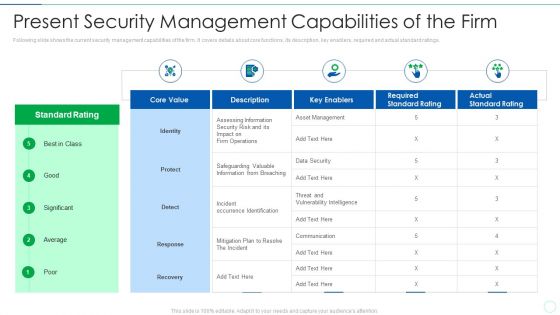
Effective IT Risk Management Process Present Security Management Formats PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this effective it risk management process present security management formats pdf. Use them to share invaluable insights on information, risk, security, plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
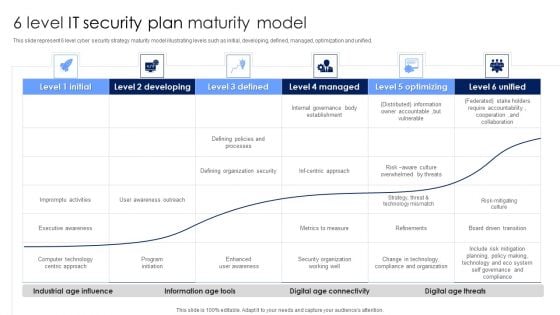
6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
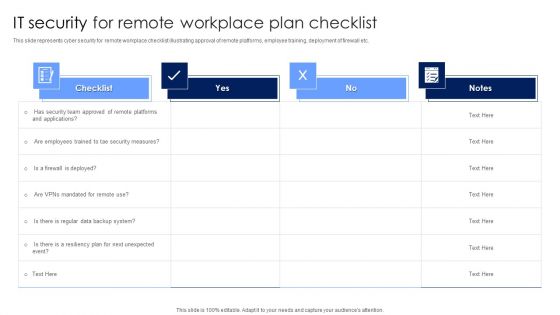
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
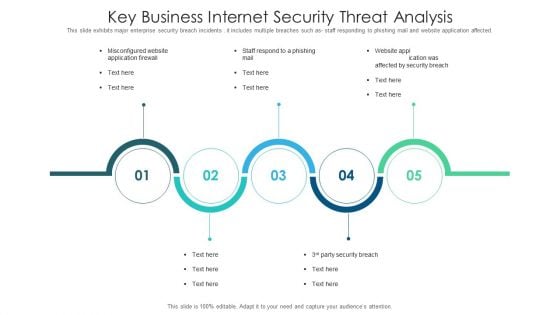
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
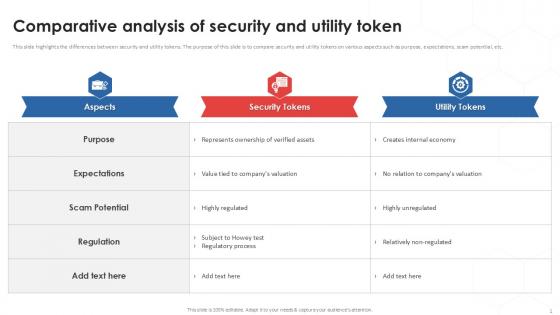
Comparative Analysis Of Tokenization Strategies For Data Security PPT Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Find a pre-designed and impeccable Comparative Analysis Of Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc.
Companys Data Safety Recognition Security Awareness Tracking Kpis Ideas PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
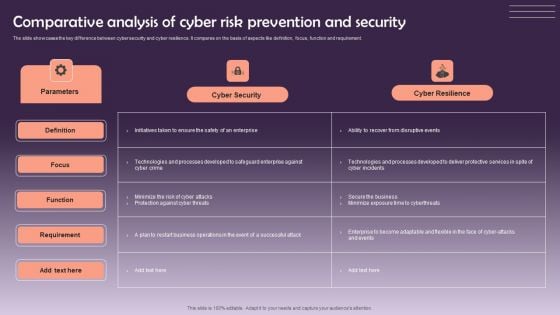
Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF
The slide showcases the key difference between cyber security and cyber resilience. It compares on the basis of aspects like definition, focus, function and requirement. Showcasing this set of slides titled Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF. The topics addressed in these templates are Cyber Security, Cyber Resilience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
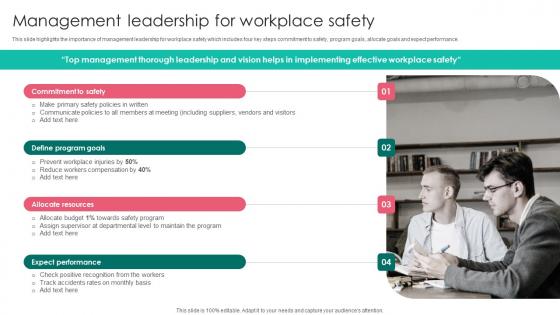
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
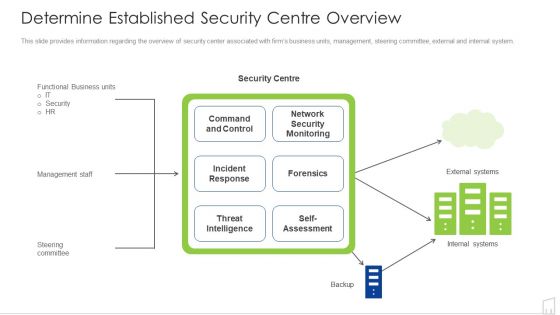
Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
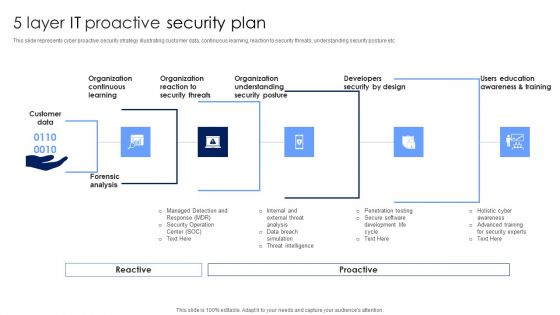
5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Guide To Designing A Staff Handbook Information Pdf

Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
Business Data IT Security Analysis Icon With Shield Download PDF
Presenting Business Data IT Security Analysis Icon With Shield Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Data IT Security, Analysis Icon With Shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
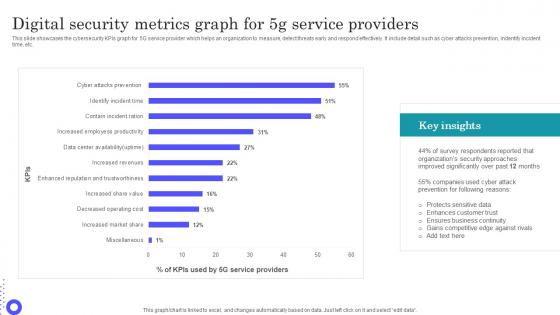
Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf
Showcasing this set of slides titled Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf The topics addressed in these templates are Protects Sensitive, Enhances Customer, Ensures Business Continuity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs graph for 5G service provider which helps an organization to measure, detect threats early and respond effectively. It include detail such as cyber attacks prevention, indentify incident time, etc.
Thank You It Security Ppt PowerPoint Presentation Outline Infographics
This is a thank you it security ppt powerpoint presentation outline infographics. This is a one stage process. The stages in this process are thank you.
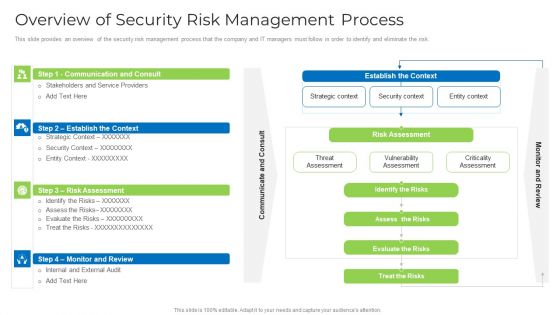
Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
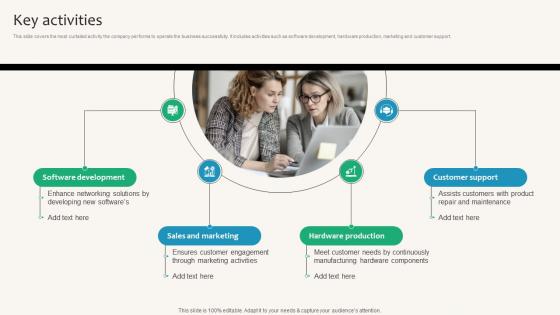
Key Activities Security Service Provider Business Model BMC SS V
This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Security Service Provider Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support.
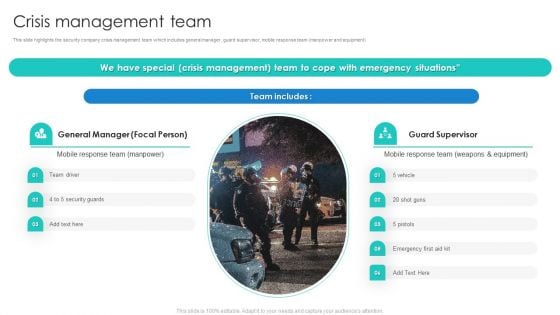
Manpower Corporate Security Business Profile Crisis Management Team Rules PDF
This slide highlights the security company crisis management team which includes general manager, guard supervisor, mobile response team manpower and equipment Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Crisis Management Team Rules PDF bundle. Topics like Team Driver, Security Guards, Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
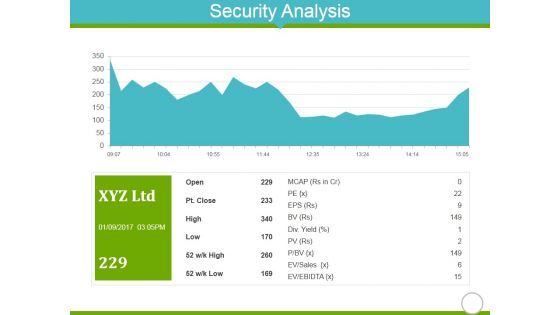
Security Analysis Ppt PowerPoint Presentation Infographic Template Shapes
This is a security analysis ppt powerpoint presentation infographic template shapes. This is a one stage process. The stages in this process are open, high, low, sales, ebidta.

Private Security Service Provider Company Summary Report Clipart PDF
This slide provide information of firm providing security services to safeguards life of human beings who are facing threats. It includes elements such as about, category, services, company stats, packages, our service benefits. Pitch your topic with ease and precision using this Private Security Service Provider Company Summary Report Clipart PDF. This layout presents information on Provide World, Security Guard, Security Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
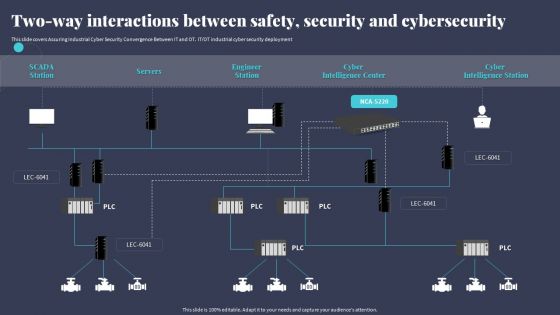
Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Suggested Coverage For Security Management Plan Graphics PDF
This slide provides information about the areas that are covered under the security management plan. This is a suggested coverage for security management plan graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, risk, security, information, system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
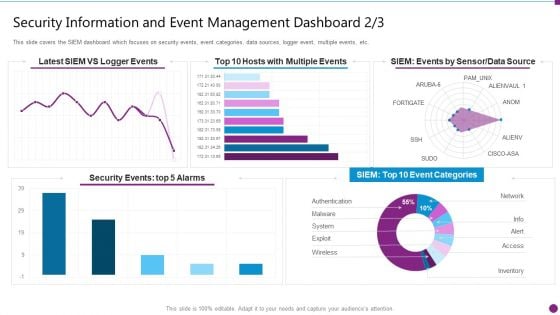
Security Information And Event Management Dashboard Events Ideas PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative security information and event management dashboard events ideas pdf bundle. Topics like security events, data source, event categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
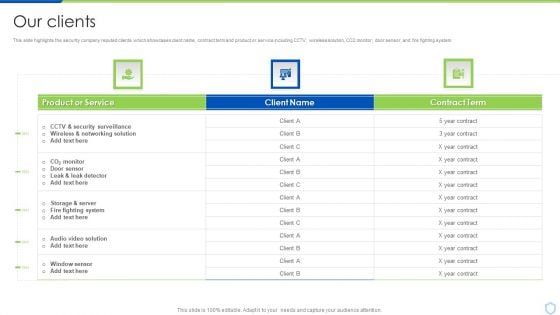
Our Clients Security And Surveillance Company Profile Graphics PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver an awe inspiring pitch with this creative Our Clients Security And Surveillance Company Profile Graphics PDF bundle. Topics like Fighting System, Security Surveillance, Wireless Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
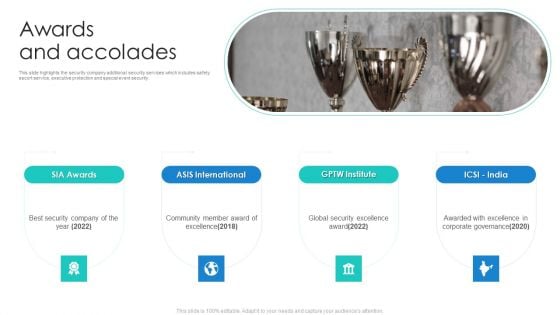
Manpower Corporate Security Business Profile Awards And Accolades Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Manpower Corporate Security Business Profile Awards And Accolades Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Asis International, Gptw Institute, Sia Awards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
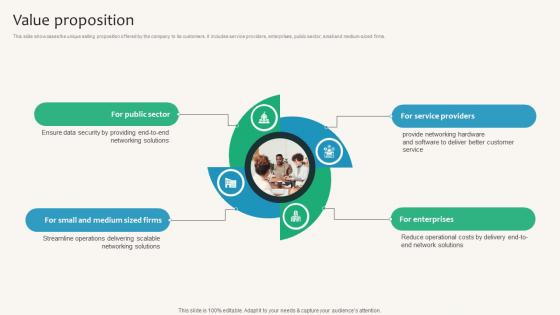
Value Proposition Security Service Provider Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition Security Service Provider Business Model BMC SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms.
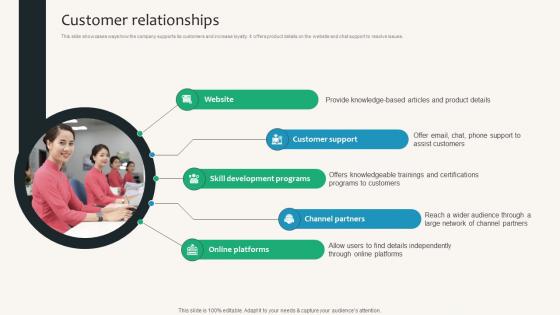
Customer Relationships Security Service Provider Business Model BMC SS V
This slide showcases ways how the company supports its customers and increase loyalty. It offers product details on the website and chat support to resolve issues. Want to ace your presentation in front of a live audience Our Customer Relationships Security Service Provider Business Model BMC SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases ways how the company supports its customers and increase loyalty. It offers product details on the website and chat support to resolve issues.
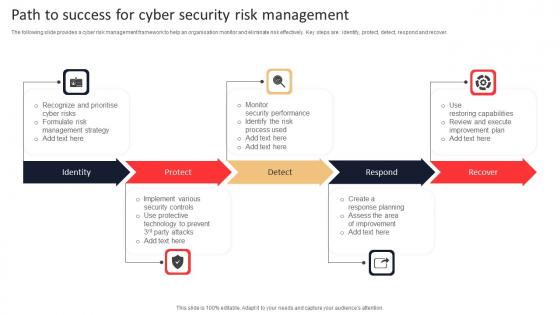
Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.
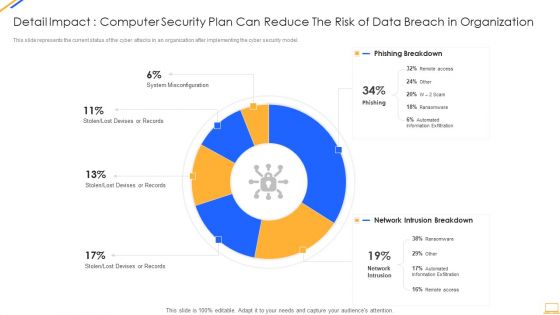
Desktop Security Management Detail Impact Computer Designs PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this desktop security management detail impact computer designs pdf. Use them to share invaluable insights on detail impact computer security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
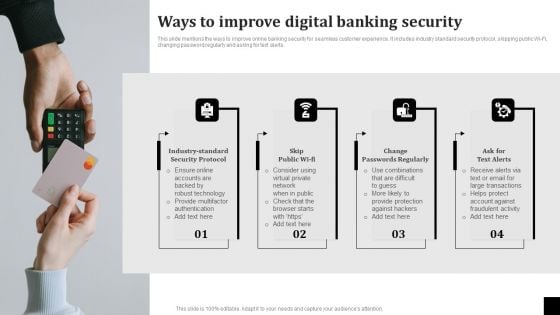
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
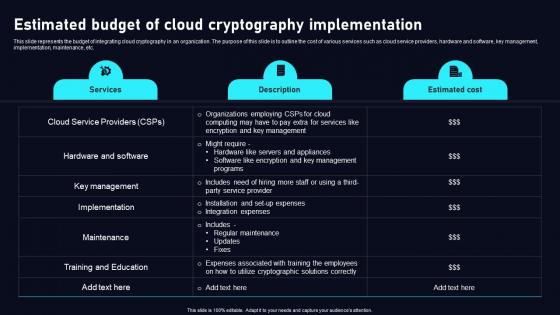
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
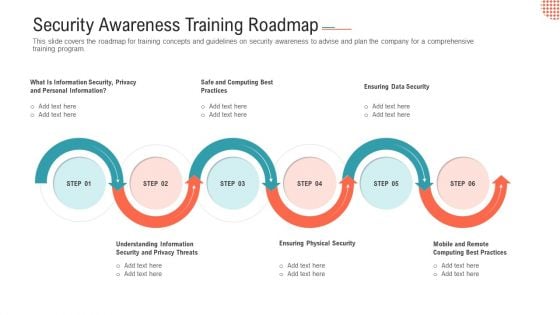
Security Awareness Training Roadmap Ppt Layouts Layouts PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program.Presenting security awareness training roadmap ppt layouts layouts pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like safe and computing best practices, ensuring data security, ensuring physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
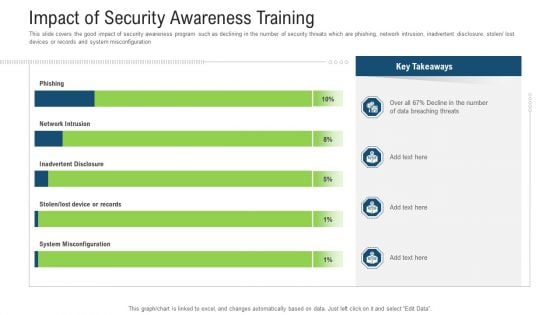
Impact Of Security Awareness Training Ppt Inspiration Design Templates PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt inspiration design templates pdf. Use them to share invaluable insights on impact of security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf
This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation. Showcasing this set of slides titled Steps For Internet Security Risk Assessment And Evaluation Microsoft Pdf The topics addressed in these templates are Risk Identification, Risk Assessment, Risk Evaluation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber risk assessment with standard risk identification to align organizational objective . It includes context establishment, risk identification, risk assessment and risk evaluation.
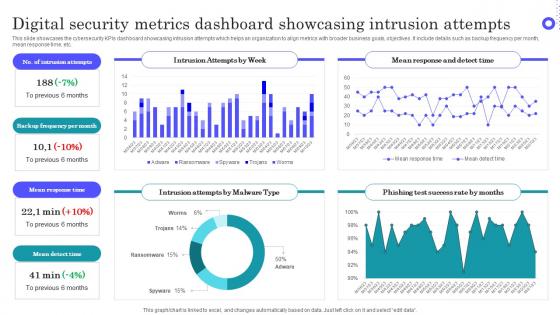
Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf This layout presents information on Intrusion Attempts, Frequency Per Month, Mean Response Time It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cybersecurity KPIs dashboard showcasing intrusion attempts which helps an organization to align metrics with broader business goals, objectives. It include details such as backup frequency per month, mean response time, etc.
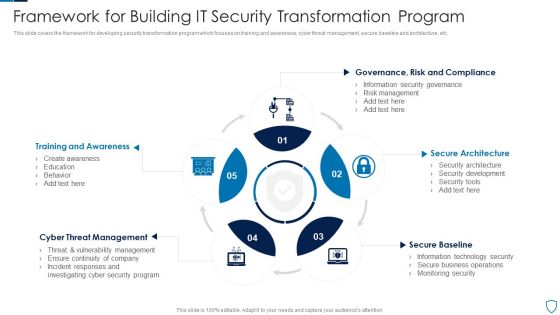
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Estimated Security Management Plan Critical Success Factors Guidelines PDF
This is a estimated security management plan critical success factors guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security incidents level, intrusion attempts, security implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
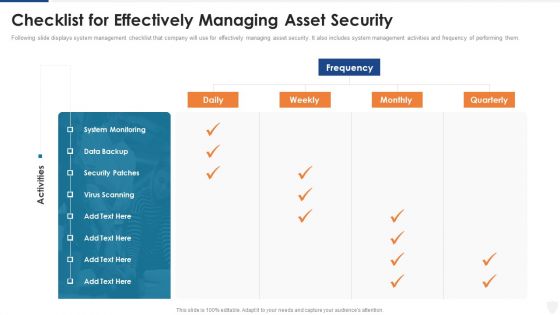
Checklist For Effectively Managing Asset Security Ppt Layouts Introduction PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this checklist for effectively managing asset security ppt layouts introduction pdf. Use them to share invaluable insights on checklist for effectively managing asset security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
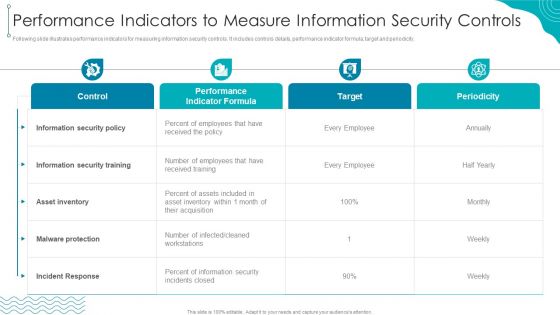
Performance Indicators To Measure Information Security Controls Designs PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Designs PDF bundle. Topics like Information security, received training, Incident Response can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
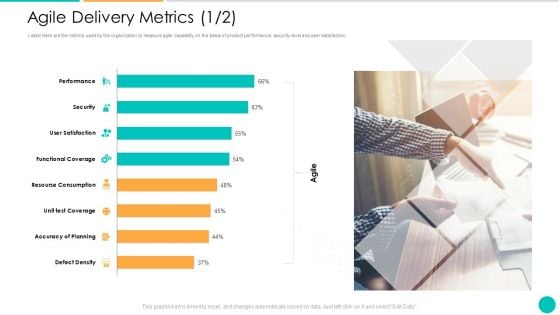
DAD Framework Agile Delivery Metrics Security Ppt Ideas Skills PDF
Listed Here are the metrics used by the organization to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver and pitch your topic in the best possible manner with this DAD framework agile delivery metrics security ppt ideas skills pdf. Use them to share invaluable insights on security, accuracy of planning, functional coverage, performance, resourse consumption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Awareness Tracking Kpis Ppt Layouts Graphics Template PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction.Deliver an awe-inspiring pitch with this creative security awareness tracking kpis ppt layouts graphics template pdf. bundle. Topics like phishing informants, social engineering, refresher training scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































