hacking

Market Segmentation Strategy Solutions PowerPoint Presentation Complete Deck With Slides
This is a market segmentation strategy solutions powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are business, market segmentation, problem, solution, strategy.

Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
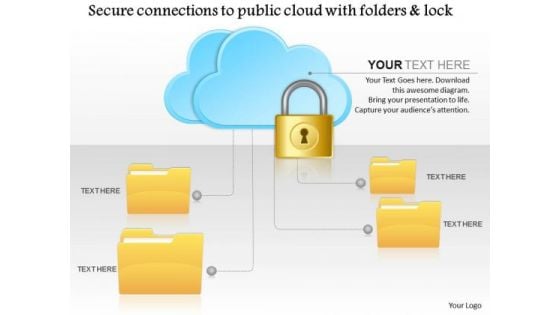
Business Diagram Secure Connections To The Public Cloud With Folders And Lock Ppt Slide
This technical slide has been designed with graphic of folders and cloud with lock. This PPT slide depicts the concept of secure connections. It focuses on the data safety in cloud technology. Use this diagram for data safety related presentations.
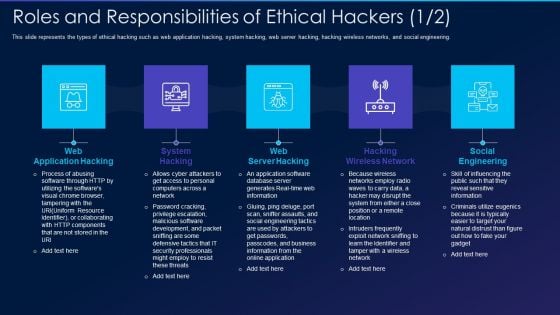
Cyber Exploitation IT Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Presenting cyber exploitation it roles and responsibilities of ethical hackers pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like web application hacking, system hacking, web server hacking, hacking wireless network, social engineering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
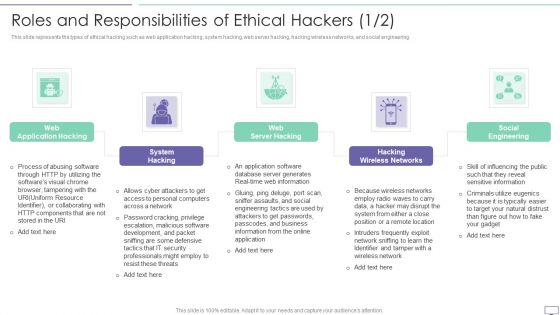
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a conceptual illustration on the subject of computer hacking Our Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211 never fail to amaze. They catch every eye that comes by.

Distributed Ledger Technology Impact On Data Security Infographics Pdf
This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking Pitch your topic with ease and precision using this Distributed Ledger Technology Impact On Data Security Infographics Pdf This layout presents information on Encryption And Validation, Decentralized Data Security, Difficulties In Hacking It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking

How Are Ethical Hackers Different Than Malicious Hackers Ppt File Sample PDF
This slide represents how ethical hackers are different from malicious hackers based on their purpose of hacking for organizational benefit and personal advantage. This is a ethical hacking vs penetration testing ppt tips pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ethical hackers, malicious hackers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
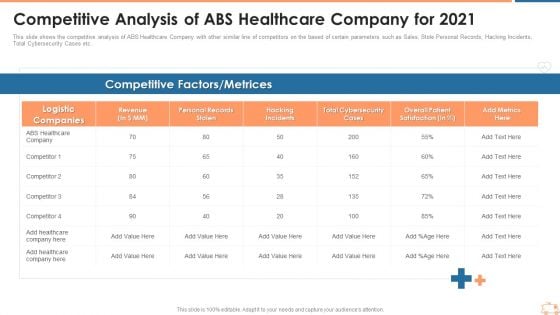
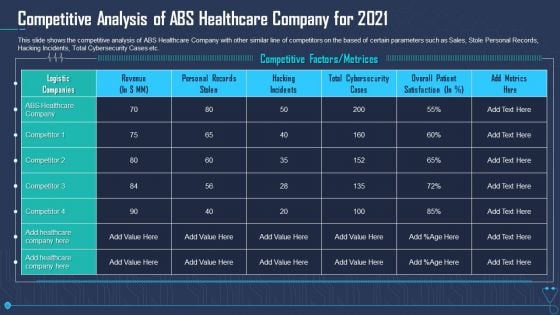
Competitive Analysis Of ABS Healthcare Company For 2021 Designs PDF
This slide shows the competitive analysis of ABS Healthcare Company with other similar line of competitors on the based of certain parameters such as Sales, Stole Personal Records, Hacking Incidents, Total Cybersecurity Cases etc. Deliver an awe inspiring pitch with this creative competitive analysis of abs healthcare company for 2021 designs pdf bundle. Topics like hacking incidents, total cybersecurity cases, personal records stolen can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Competitive Analysis Of ABS Healthcare Company For 2021 Themes PDF
This slide shows the competitive analysis of ABS Healthcare Company with other similar line of competitors on the based of certain parameters such as Sales, Stole Personal Records, Hacking Incidents, Total Cybersecurity Cases etc. Deliver an awe inspiring pitch with this creative competitive analysis of abs healthcare company for 2021 themes pdf bundle. Topics like personal records stolen, hacking incidents, cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Competitive Analysis Of Abs Healthcare Company For 2021 Ppt Portfolio Templates PDF
This slide shows the competitive analysis of ABS Healthcare Company with other similar line of competitors on the based of certain parameters such as Sales, Stole Personal Records, Hacking Incidents, Total Cybersecurity Cases etc. Deliver an awe-inspiring pitch with this creative competitive analysis of abs healthcare company for 2021 ppt portfolio templates pdf. bundle. Topics like logistic companies, revenue, personal records stolen, hacking incidents, total cybersecurity cases, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc.
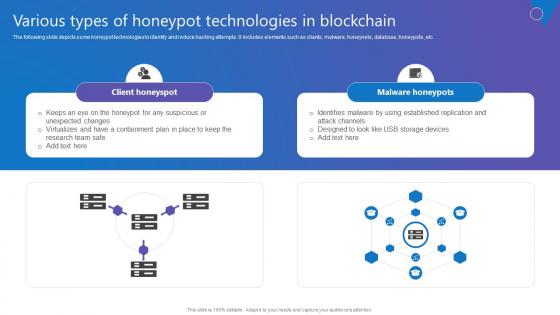
Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc.
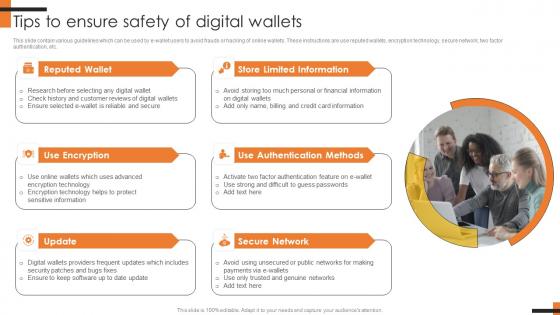
Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100Precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide contain various guidelines which can be used by e wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.
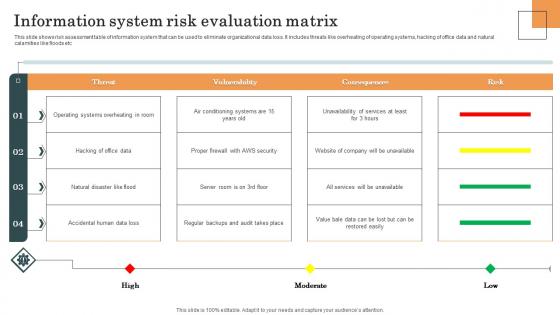
Information System Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of information system that can be used to eliminate organizational data loss. It includes threats like overheating of operating systems, hacking of office data and natural calamities like floods etc. Showcasing this set of slides titled Information System Risk Evaluation Matrix Survey SS. The topics addressed in these templates are Information System, Risk Evaluation Matrix, Operating Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows risk assessment table of information system that can be used to eliminate organizational data loss. It includes threats like overheating of operating systems, hacking of office data and natural calamities like floods etc.

Certified Ethical Hacker CEH Job Description Sample PDF
This slide covers Certified ethical hacker CEH certifications Training Exam Cost, Job Description, Roles and responsibilities and average salary package etc.Deliver an awe inspiring pitch with this creative Certified Ethical Hacker CEH Job Description Sample PDF bundle. Topics like Roles And Responsibilities, Hacking Destruction, Circumvent Detection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
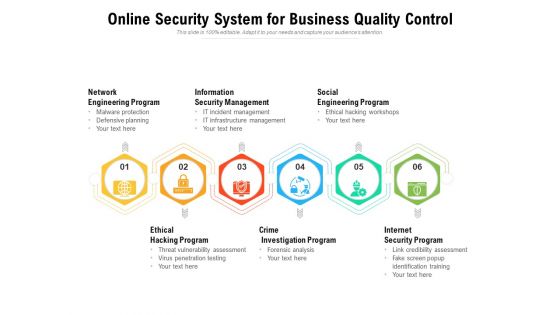
Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
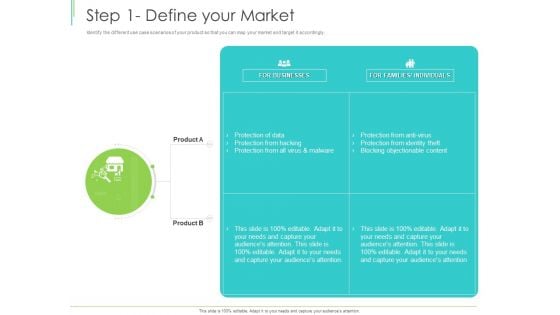
Marketing Plan Implementation Step 1 Define Your Market Ppt Styles Outline PDF
Identify the different use case scenarios of your product so that you can map your market and target it accordingly. Deliver an awe-inspiring pitch with this creative marketing plan implementation step 1 define your market ppt styles outline pdf bundle. Topics like blocking objectionable content, protection of data, protection from hacking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
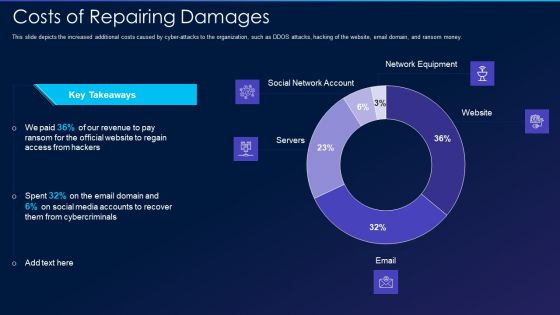
Cyber Exploitation IT Costs Of Repairing Damages Themes PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money. Deliver an awe inspiring pitch with this creative cyber exploitation it costs of repairing damages themes pdf bundle. Topics like social network account, servers, network equipment, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
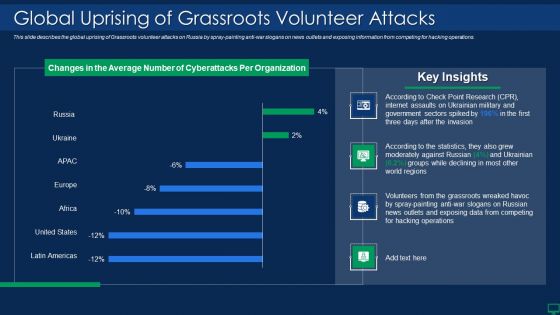
Russian Cyber Attacks On Ukraine IT Global Uprising Of Grassroots Microsoft PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it global uprising of grassroots microsoft pdf bundle. Topics like internet, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
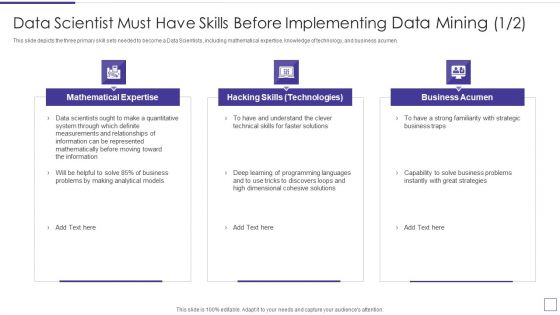
Data Mining Implementation Data Scientist Must Have Skills Before Implementing Data Clipart PDF
This slide depicts the three primary skill sets needed to become a Data Scientists, including mathematical expertise, knowledge of technology, and business acumen.Deliver an awe inspiring pitch with this creative data mining implementation data scientist must have skills before implementing data clipart pdf bundle. Topics like mathematical expertise, hacking skills technologies, business acumen can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
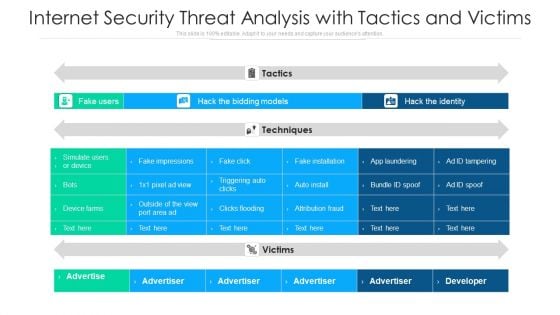
Internet Security Threat Analysis With Tactics And Victims Ppt PowerPoint Presentation Infographic Template Format Ideas PDF
Showcasing this set of slides titled internet security threat analysis with tactics and victims ppt powerpoint presentation infographic template format ideas pdf. The topics addressed in these templates are fake installation, hack the bidding models, hack the identity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program Ppt Layouts Demonstration PDF
This slide depicts the reasons to pursue the certified ethical hacking program, including the number of available jobs, the average salary in US dollars, and so on. Presenting reasons to pursue the certified ethical hacker ceh v11 program ppt layouts demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
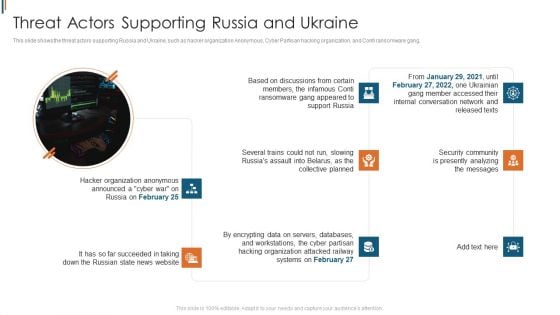
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF
This slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Presenting Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Program, Threats And Risks, Protected Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
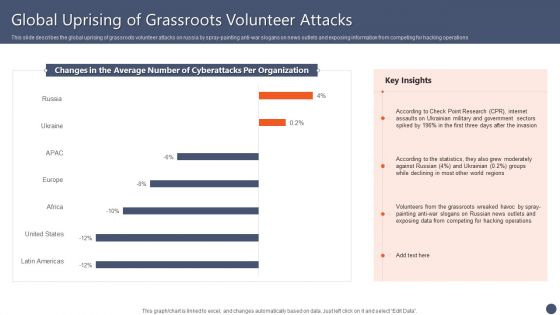
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
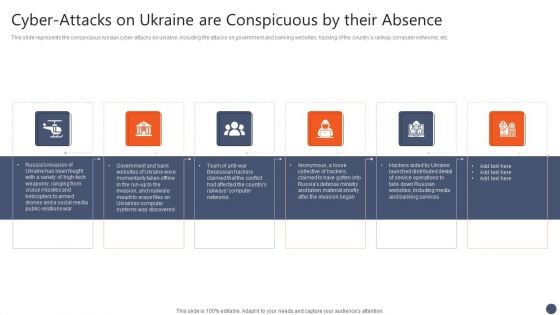
Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
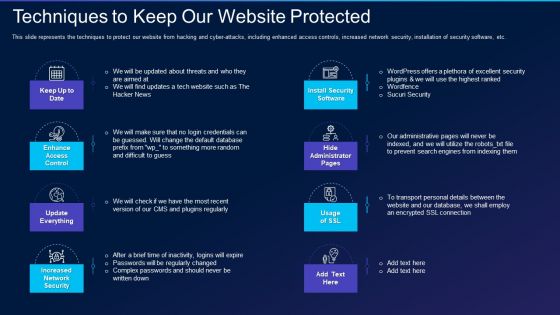
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
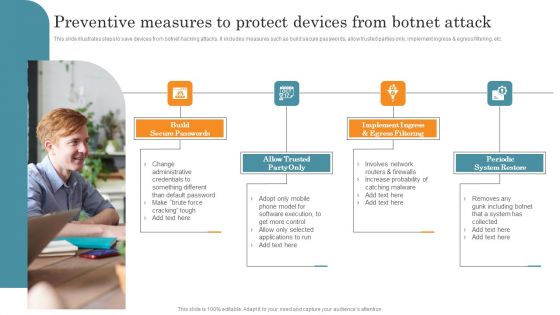
Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
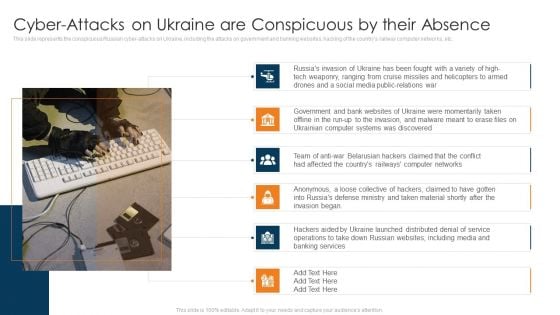
Data Wiper Spyware Attack Cyber Attacks On Ukraine Are Conspicuous Elements PDF
This slide represents the conspicuous Russian cyber-attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc.This is a data wiper spyware attack cyber attacks on ukraine are conspicuous elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine launched distributed, russian websites, belarusian hackers You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Competitive Analysis Of ABS Healthcare Company For 2021 Ppt Pictures Design Ideas PDF
This slide shows the competitive analysis of ABS Healthcare Company with other similar line of competitors on the based of certain parameters such as Sales, Stole Personal Records, Hacking Incidents, Total Cybersecurity Cases etc. Deliver and pitch your topic in the best possible manner with this competitive analysis of ABS healthcare company for 2021 ppt pictures design ideas pdf. Use them to share invaluable insights on revenue, cybersecurity cases, competitor, logistic companies, competitive factors metrices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Dashboard For ABS Healthcare Company Ppt Themes PDF
This slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Presentingcybersecurity dashboard for abs healthcare company ppt themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like phishing attacks 2021, records stolen 2021, malware cases resolved 2021, malware attacks 2021, hacking incidents 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Cyber Attacks On Ukraine Information PDF
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. Presenting russian cyber attacks on ukraine it cyber attacks on ukraine information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like social media, systems, networks, services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
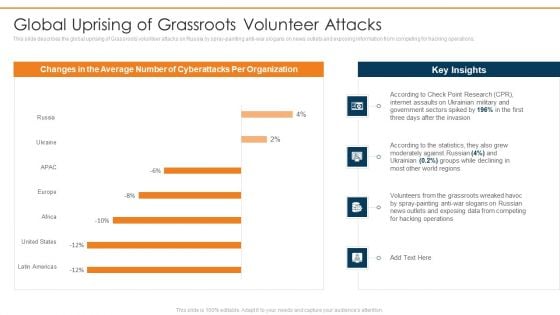
Data Wiper Spyware Attack Global Uprising Of Grassroots Volunteer Attacks Background PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray-painting anti war slogans on news outlets and exposing information from competing for hacking operations.Deliver an awe inspiring pitch with this creative data wiper spyware attack global uprising of grassroots volunteer attacks background pdf bundle. Topics like according to the statistics, moderately against russian, volunteers from the grassroots can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
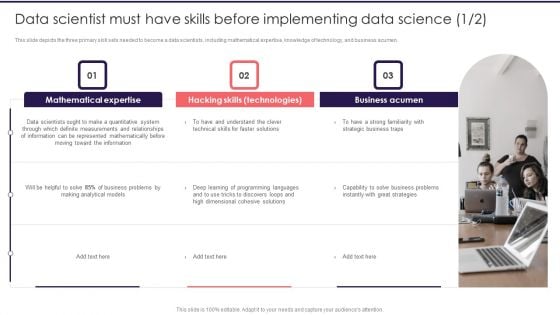
Information Studies Data Scientist Must Have Skills Before Implementing Data Science Slides PDF
This slide depicts the three primary skill sets needed to become a data scientists, including mathematical expertise, knowledge of technology, and business acumen. This is a Information Studies Data Scientist Must Have Skills Before Implementing Data Science Slides PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mathematical Expertise, Business Acumen, Hacking Skills. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
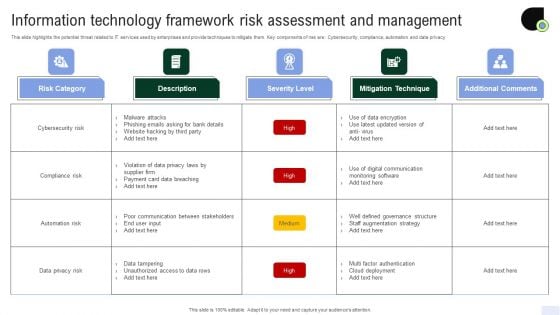
Information Technology Framework Risk Assessment And Management Diagrams PDF
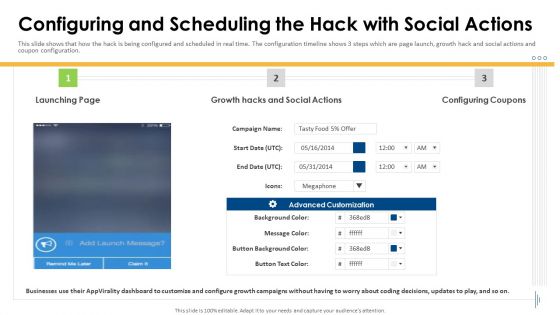
Appvirality Capital Financing Elevator Pitch Deck Configuring And Scheduling Sample PDF
This slide shows that how the hack is being configured and scheduled in real time. The configuration timeline shows 3 steps which are page launch, growth hack and social actions and coupon configuration. Deliver and pitch your topic in the best possible manner with this Appvirality Capital Financing Elevator Pitch Deck Configuring And Scheduling Sample PDF Use them to share invaluable insights on Launching Page, Social Actions, Configuring Coupons and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
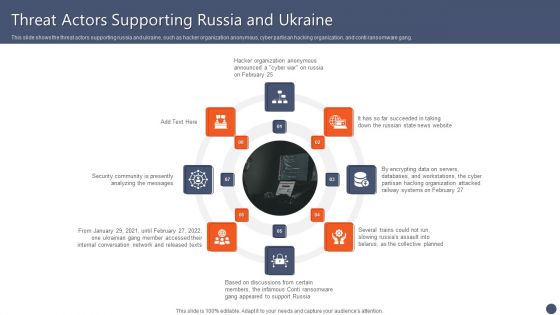
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF
This slide showcases cyber security risk landscape which can benefit various users around the world to be proactive of potential outcomes. It includes information about target, purpose, possible outcome, social media phishing, system viruses, configuration and passcodes, allocated service denial, hacking devices and structured query language. Persuade your audience using this Cyber Security Business Threats Landscape With Potential Outcomes Ppt Outline Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Landscape, Target, Purpose, Possible Outcome. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ukraine Cyberwarfare Cyber Attacks On Ukraine Are Conspicuous By Their Absence Topics Pdf
This slide represents the conspicuous Russian cyber attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. This is a ukraine cyberwarfare cyber attacks on ukraine are conspicuous by their absence topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like government and bank websites of ukraine were momentarily taken offline, team of anti war belarusian hackers claimed that the conflict had affected the countrys railways computer networks, hackers aided by ukraine launched distributed denial of service operations to take down russian websites. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
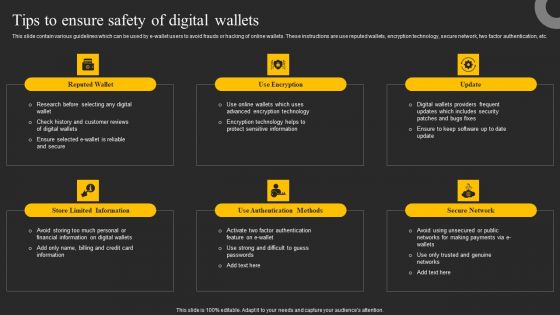
Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc. Welcome to our selection of the Tips To Ensure Safety Of Digital Wallets Ppt Summary Slide Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
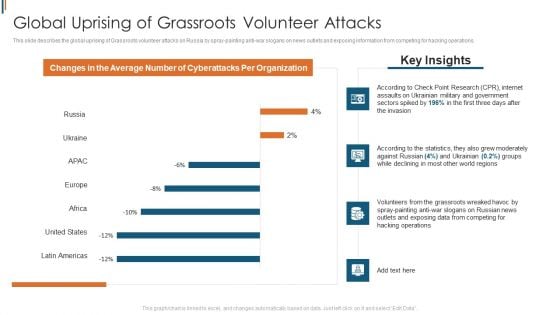
Ukraine Cyberwarfare Global Uprising Of Grassroots Volunteer Attacks Rules Pdf
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative ukraine cyberwarfare global uprising of grassroots volunteer attacks rules pdf bundle. Topics like according to check point research cpr, internet assaults on ukrainian military, government sectors spiked by 196 percentage in the first three days after the invasion, according to the statistics, they also grew moderately against russian 4 percent, ukrainian 0.2 percent groups while declining in most other world regions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
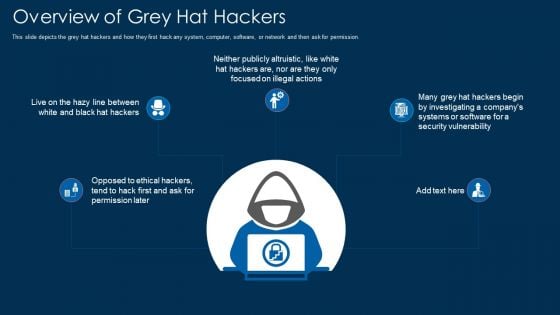
Overview Of Grey Hat Hackers Ppt Infographics Pictures PDF
This slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission. This is a overview of grey hat hackers ppt infographics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
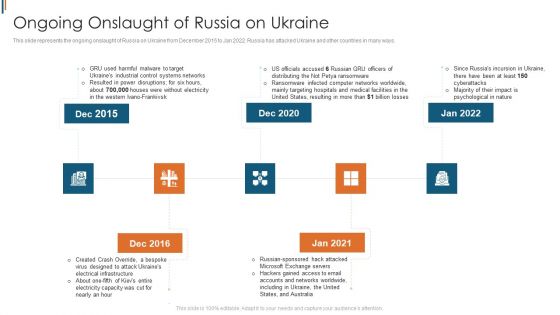
Ukraine Cyberwarfare Ongoing Onslaught Of Russia On Ukraine Brochure Pdf
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. Presenting ukraine cyberwarfare ongoing onslaught of russia on ukraine brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like russian sponsored hack attacked microsoft exchange servers, hackers gained access to email accounts and networks worldwide, including in ukraine, the united states, and australia. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download
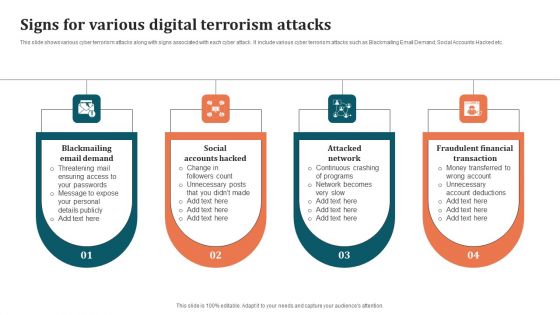
Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
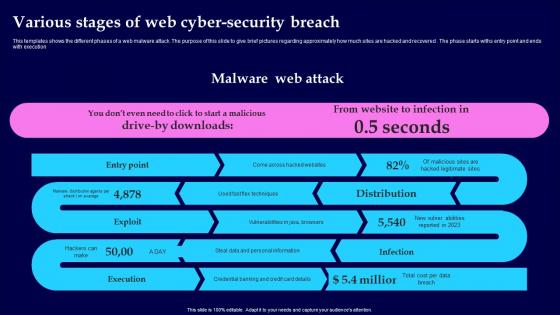
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution
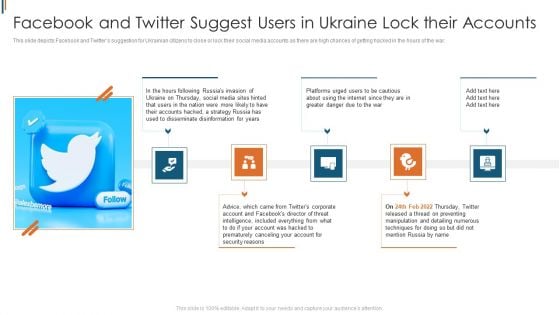
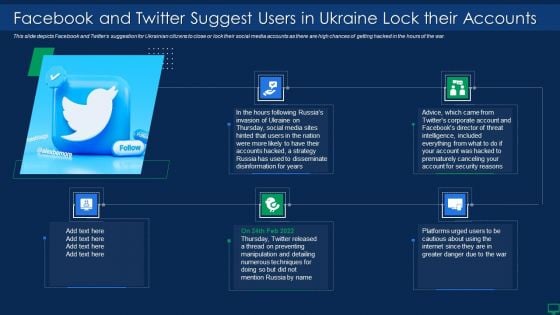
Ukraine Cyberwarfare Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Information Pdf
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Presenting ukraine cyberwarfare facebook and twitter suggest users in ukraine lock their accounts information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like platforms urged users to be cautious about using the internet since they are in greater danger due to the war, in the hours following russias invasion of ukraine on thursday, social media sites hinted that users in the nation were more likely to have their accounts hacked. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
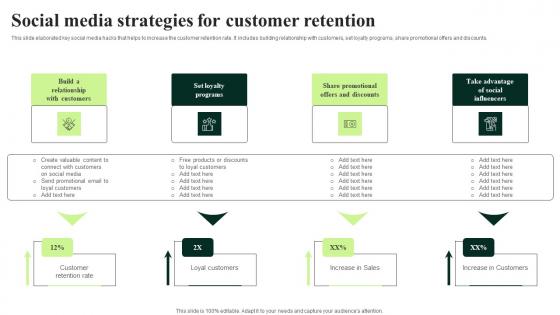
Client Feedback Strategies Social Media Strategies For Customer Retention Infographics Pdf
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. Find a pre designed and impeccable Client Feedback Strategies Social Media Strategies For Customer Retention Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
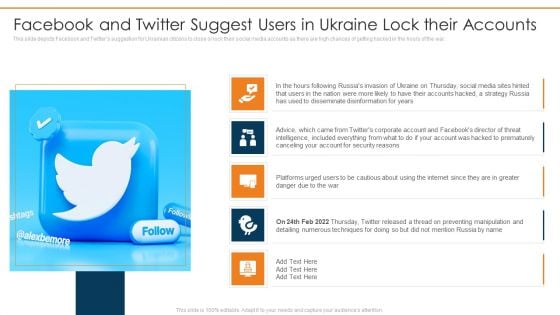
Data Wiper Spyware Attack Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Clipart PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack facebook and twitter suggest users in ukraine lock their accounts clipart pdf Use them to share invaluable insights on disseminate disinformation, included everything, prematurely canceling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
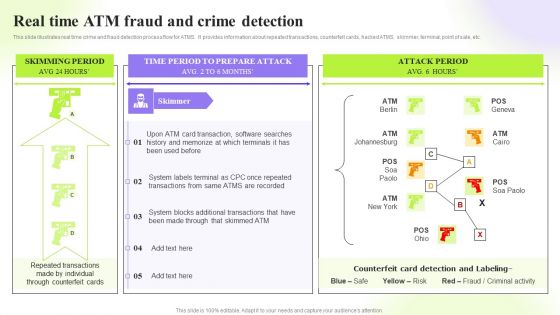
Techniques To Monitor Transactions Real Time Atm Fraud And Crime Detection Slides PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Take your projects to the next level with our ultimate collection of Techniques To Monitor Transactions Real Time Atm Fraud And Crime Detection Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Deploying AML Transaction Monitoring Real Time ATM Fraud And Crime Detection Designs PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Boost your pitch with our creative Deploying AML Transaction Monitoring Real Time ATM Fraud And Crime Detection Designs PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
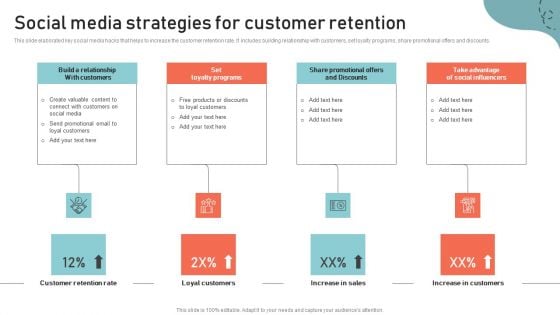
Optimizing Multichannel Strategy To Improve User Experience Social Media Strategies Ideas PDF
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Optimizing Multichannel Strategy To Improve User Experience Social Media Strategies Ideas PDF from Slidegeeks and deliver a wonderful presentation.

 Home
Home