hacking
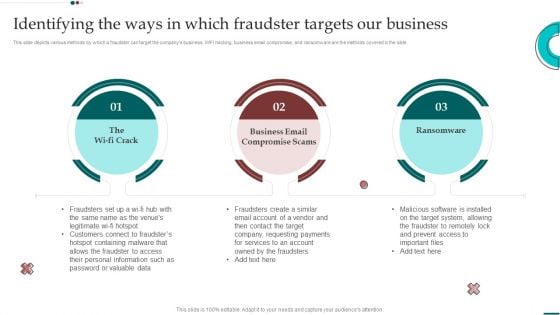
Scam Inquiry And Response Playbook Identifying The Ways In Which Fraudster Targets Our Business Ideas PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide. Welcome to our selection of the Scam Inquiry And Response Playbook Identifying The Ways In Which Fraudster Targets Our Business Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
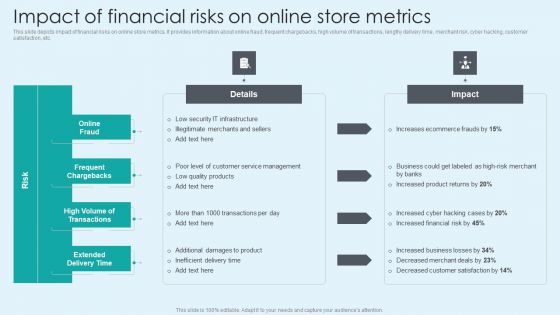
Impact Of Financial Risks On Online Store Metrics Summary PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Impact Of Financial Risks On Online Store Metrics Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Impact Of Financial Risks On Online Store Metrics Summary PDF.
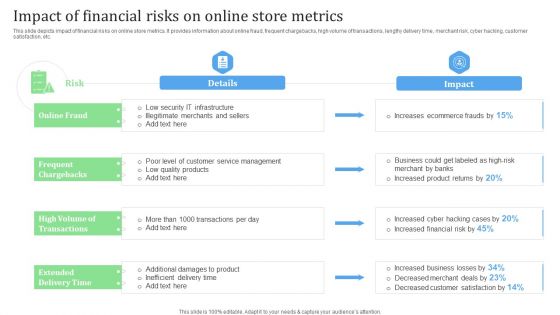
Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Financial Risks On Online Store Metrics Financial Management Strategies Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc. Find highly impressive Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Managing E Commerce Business Accounting Impact Of Financial Risks On Online Store Metrics Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
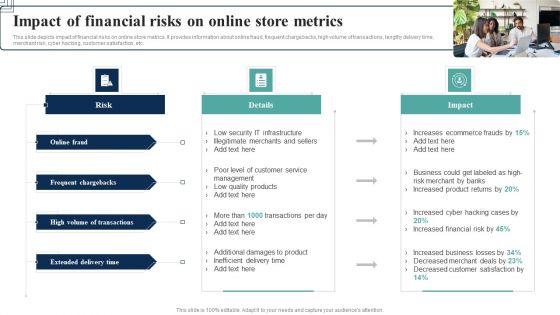
How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF
This slide depicts impact of financial risks on online store metrics. It provides information about online fraud, frequent chargebacks, high volume of transactions, lengthy delivery time, merchant risk, cyber hacking, customer satisfaction, etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable How Electronic Commerce Financial Procedure Can Be Enhanced Impact Of Financial Risks On Online Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF
This slide provides details regarding cybersecurity trends existing across globe in terms of rise in automotive hacking, IoT with 5G, cloud platform as potential vulnerable, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
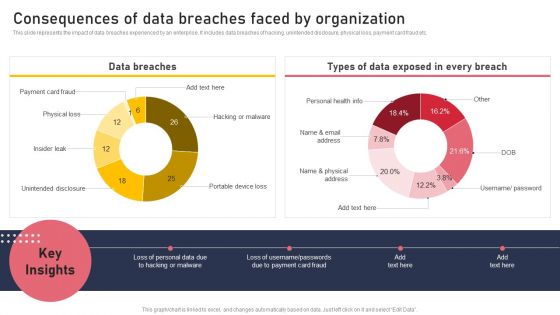
Consequences Of Data Breaches Faced By Organization Ideas PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Consequences Of Data Breaches Faced By Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Consequences Of Data Breaches Faced By Organization Ideas PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
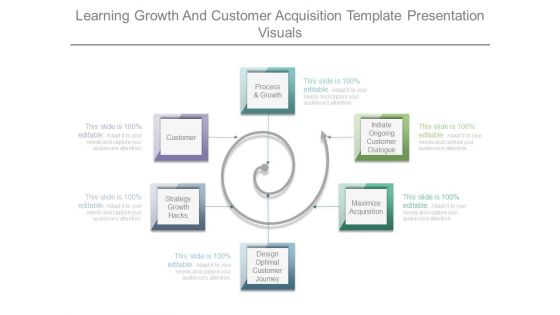
Learning Growth And Customer Acquisition Template Presentation Visuals
This is a learning growth and customer acquisition template presentation visuals. This is a six stage process. The stages in this process are initiate ongoing customer dialogue, maximize acquisition, design optimal customer journey, strategy growth hacks, customer, process and growth.

Manufacturing Capability Building Chart Powerpoint Slide Background Picture
This is a manufacturing capability building chart powerpoint slide background picture. This is a ten stage process. The stages in this process are components, off the shelf hack, design for manufacturing, manufacturing, engineering, engineering validation test, purchasing, paper prototype, invoicing, planning.
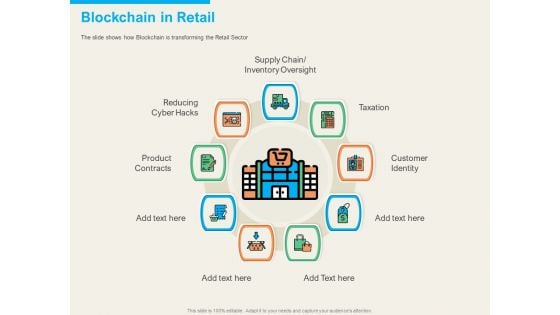
Understanding Blockchain Basics Use Cases Blockchain In Retail Ppt Inspiration Background Designs PDF
Presenting this set of slides with name understanding blockchain basics use cases blockchain in retail ppt inspiration background designs pdf. This is a nine stage process. The stages in this process are taxation, customer identity, product contracts, reducing cyber hacks, supply chain or inventory oversight. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
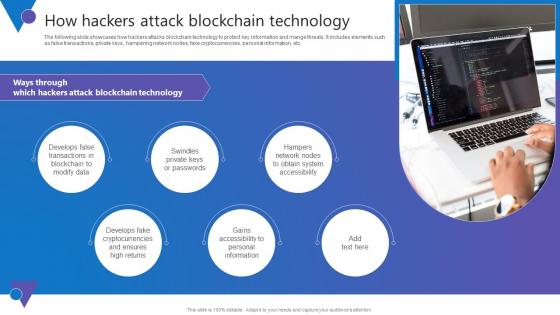
How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc.
Architecture Blockchain System Blockchain In Retail Ppt Icon Objects PDF
The slide shows how Blockchain is transforming the Retail Sector. This is a architecture blockchain system blockchain in retail ppt icon objects pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product contracts, customer identity, taxation, reducing cyber hacks, supply chain. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
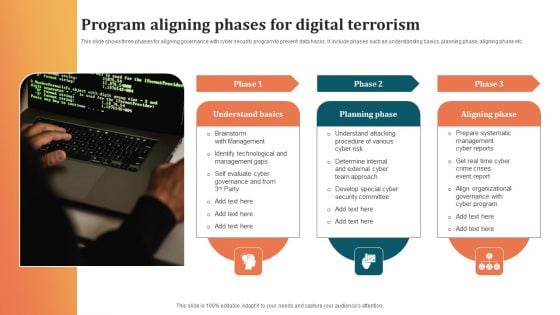
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Revolut Capital Funding How Will We Market Ourselves For Revolut Pitch Deck Ppt Infographics Slide Download PDF
The following slide provides an overview of the marketing strategy of the organization s it displays the total number of early adopters, total number of events, the key partners and hacks. Deliver an awe inspiring pitch with this creative Revolut Capital Funding How Will We Market Ourselves For Revolut Pitch Deck Ppt Infographics Slide Download PDF bundle. Topics like Market Ourselves, Initial Plan, Target can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
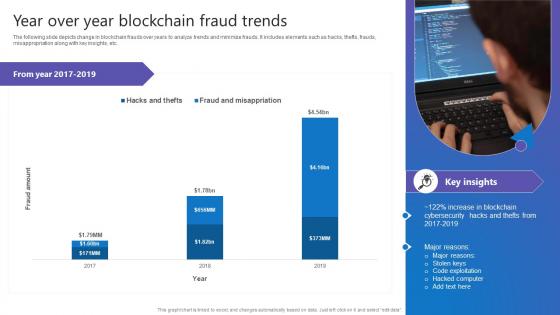
Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf
The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf can be your best option for delivering a presentation. Represent everything in detail using Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc.
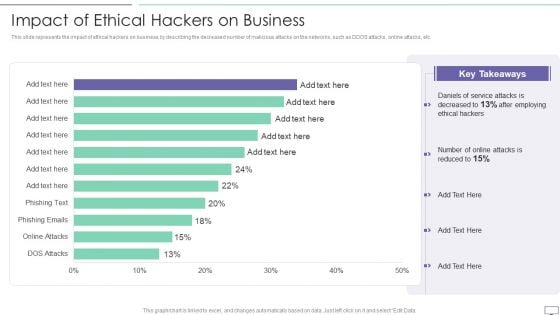
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
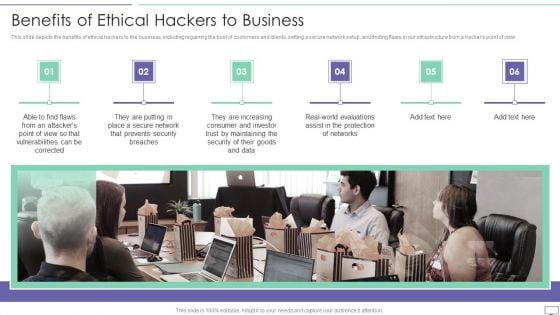
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

White Hat Or Ethical Hackers Ppt Show Diagrams PDF
Deliver an awe inspiring pitch with this creative white hat or ethical hackers ppt show diagrams pdf bundle. Topics like organization, security, system, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Details On Certified Ethical Hacker Ceh Certification Professional PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a details on certified ethical hacker ceh certification professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device, network, analysis, system, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
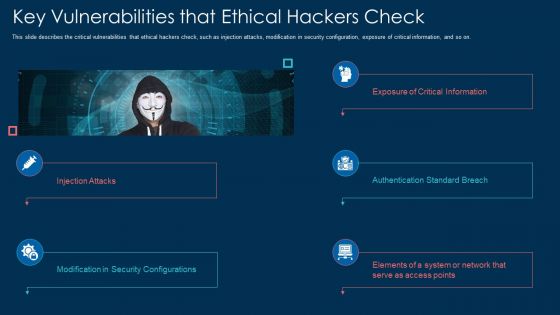
Key Vulnerabilities That Ethical Hackers Check Ppt Layouts Templates PDF
This is a key vulnerabilities that ethical hackers check ppt layouts templates pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, network, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why Organizations Recruit Ethical Hackers Ppt Slides Smartart PDF
This is a why organizations recruit ethical hackers ppt slides smartart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information systems, security, measures, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
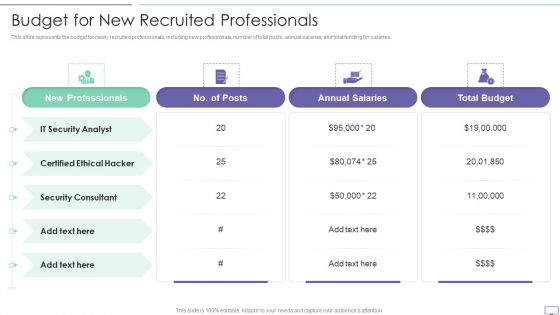
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hacker People PowerPoint Template 0810
A business hacker is breaking into a laptop computer and stealing information isolated against a white background Take the fast train to success. Book a berth with our Hacker People PowerPoint Template 0810.
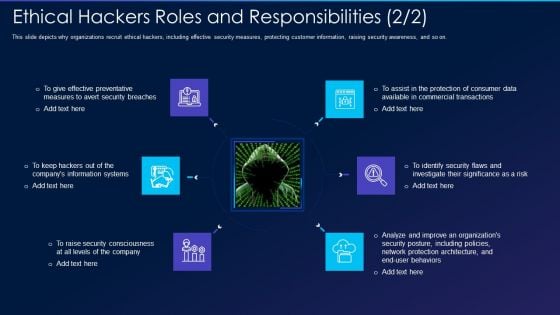
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
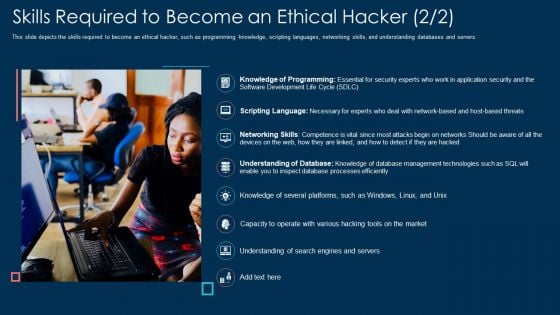
Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
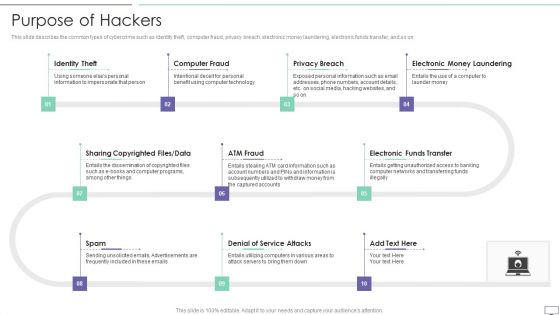
IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
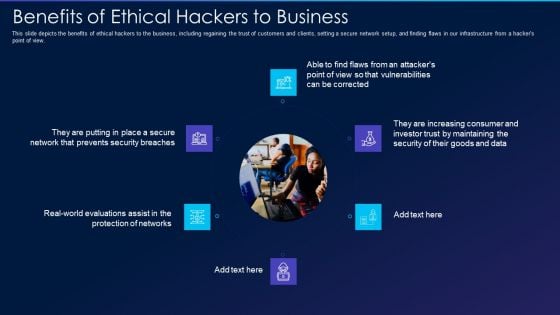
Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Skills And Certifications Required For Ethical Hacker Ppt Gallery Icon PDF
This slide describes the skills and certifications required for ethical hacker, such as computer networking skills, computer skills, Linux skills, and so on. Deliver an awe inspiring pitch with this creative skills and certifications required for ethical hacker ppt gallery icon pdf bundle. Topics like technologies, management, security, requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Ethical Hacker Ceh Job Description Collection Of Information Technology Certifications Themes PDF
This slide covers Certified ethical hacker CEH certifications Training and Exam Cost, Job Description, Roles and responsibilities and average salary package etc. Presenting certified ethical hacker ceh job description collection of information technology certifications themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Networks, Systems, Organization, secure device. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
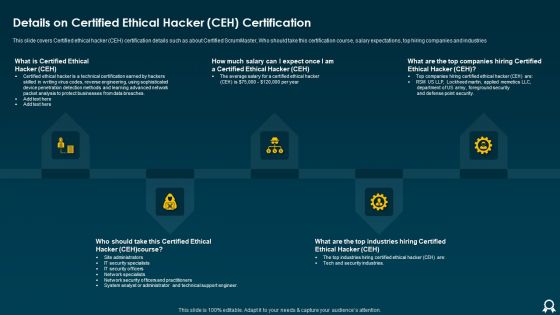
IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Average Salary, Point Security, Methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
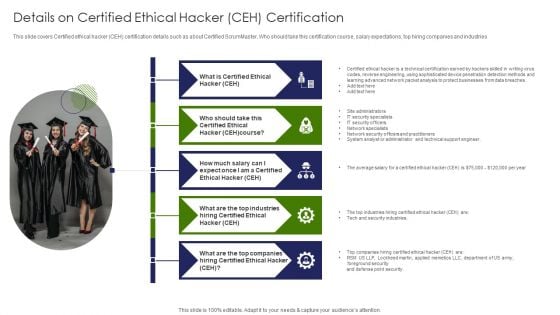
IT Professional Data Certification Program Details On Certified Ethical Hacker CEH Certification Portrait PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. Presenting IT Professional Data Certification Program Details On Certified Ethical Hacker CEH Certification Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Specialists, Network Specialists, Detection Methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
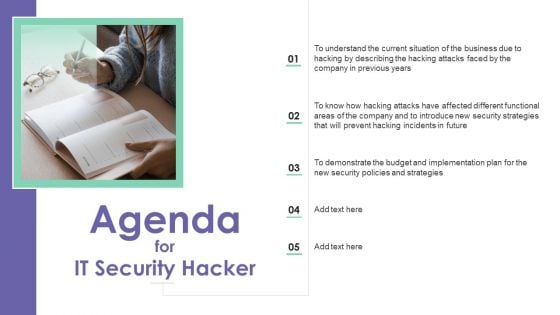
IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Certified Ethical Hacker Collection Of Information Technology Certifications Structure PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting certified ethical hacker collection of information technology certifications structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like technology, demand, management, developments, strategies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
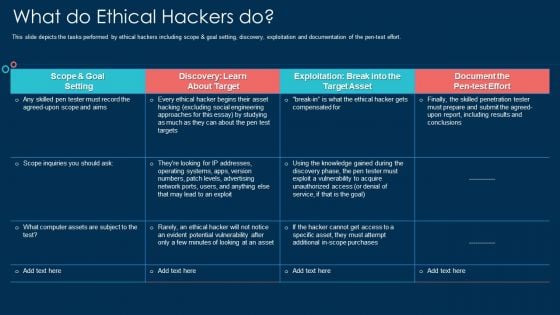
What Do Ethical Hackers Do Ppt Outline Deck PDF
This slide depicts the tasks performed by ethical hackers including scope and goal setting, discovery, exploitation and documentation of the pen test effort. Deliver an awe inspiring pitch with this creative what do ethical hackers do ppt outline deck pdf bundle. Topics like goal, target, systems, document can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
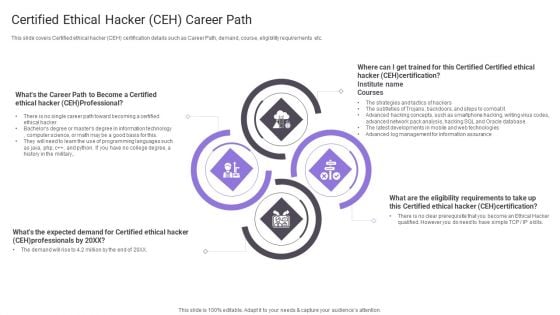
Certified Ethical Hacker CEH Career Path Portrait PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc.Presenting Certified Ethical Hacker CEH Career Path Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Expected Demand, Programming Languages, Eligibility Requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
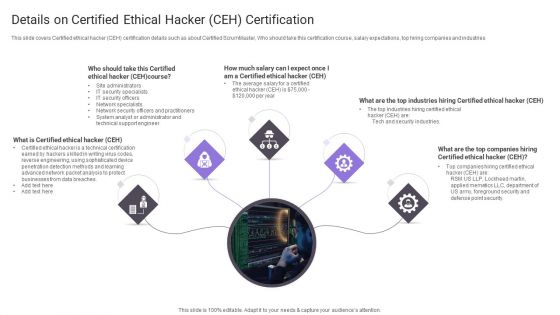
Details On Certified Ethical Hacker CEH Certification Summary PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries.Presenting Details On Certified Ethical Hacker CEH Certification Summary PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Solutions Architect, Certified Solutions, Solutions Architect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
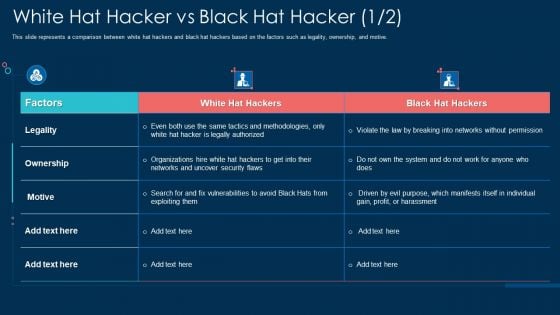
White Hat Hacker Vs Black Hat Hacker Security Ppt File Example PDF
This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver and pitch your topic in the best possible manner with this white hat hacker vs black hat hacker security ppt file example pdf. Use them to share invaluable insights on ownership, networks, organizations, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf
Showcasing this set of slides titled Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf The topics addressed in these templates are Fraud Threat Evaluation, Icon Showcasing Hacker All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Hacker In Powerpoint And Google Slides Cpb
Introducing our well-designed Process Hacker In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Process Hacker. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Process Hacker In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IT Security Hacker Use Of Security Programs Professional PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks.Presenting IT Security Hacker Use Of Security Programs Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Requires, Monthly Membership, Elimination Of Malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
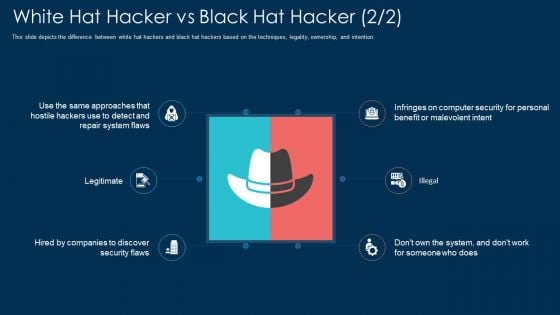
White Hat Hacker Vs Black Hat Hacker Ppt Inspiration Slide Download PDF
This slide depicts the difference between white hat hackers and black hat hackers based on the techniques, legality, ownership, and intention. Presenting white hat hacker vs black hat hacker ppt inspiration slide download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with background concept of computer trojan horse Go far and further with our Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811. Add to the distance your thoughts can cover.
Icons Slide For IT Security Hacker Inspiration PDF
Download our innovative and attention grabbing Icons Slide For IT Security Hacker Inspiration PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
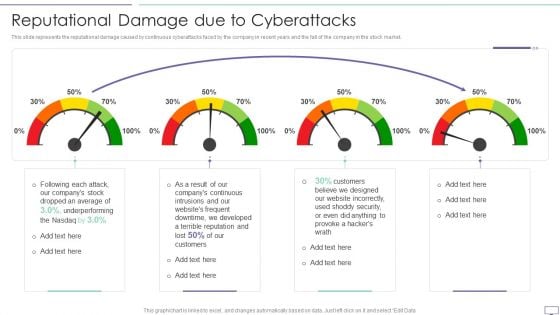
IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF. Use them to share invaluable insights on Website Incorrectly, Underperforming, Dropped An Average and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Regaining Reputation Of Our Company Infographics PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies.This is a IT Security Hacker Regaining Reputation Of Our Company Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers And Clients, Appropriate Service, Database Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Backup Of Sensitive Information Ideas PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization.This is a IT Security Hacker Backup Of Sensitive Information Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Different Service, Emergency Access, Natural Disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fivty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
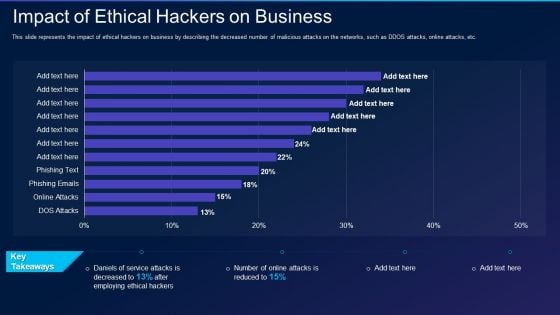
Cyber Exploitation IT Impact Of Ethical Hackers On Business Template PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc. Deliver an awe inspiring pitch with this creative cyber exploitation it impact of ethical hackers on business template pdf bundle. Topics like impact of ethical hackers on business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Roles And Responsibilities Of Ethical Hacker Ppt Infographics Graphics Example PDF
This slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports, repairing the vulnerabilities of the system, etc. This is a roles and responsibilities of ethical hacker ppt infographics graphics example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roles and responsibilities of ethical hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
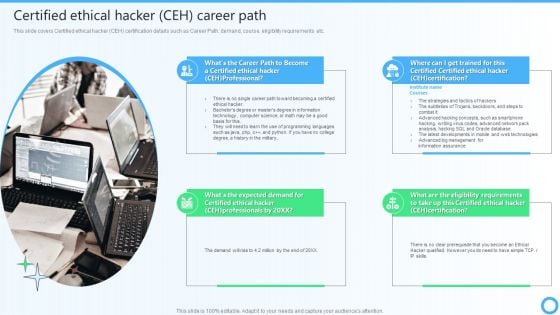
Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc.Get a simple yet stunning designed Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Certified Ethical Hacker CEH Career Path IT Certifications To Enhance Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
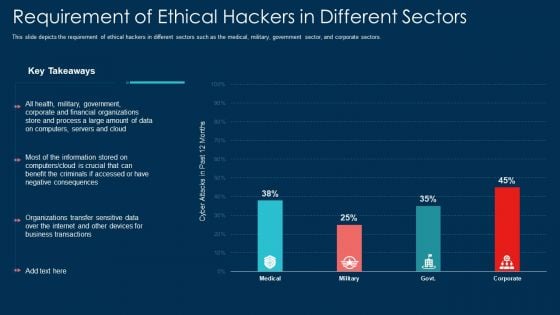
Requirement Of Ethical Hackers In Different Sectors Ppt Model Example File PDF
This slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Deliver and pitch your topic in the best possible manner with this requirement of ethical hackers in different sectors ppt model example file pdf. Use them to share invaluable insights on information, benefit, process, organizations, financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Data Services Certification Programs Certified Ethical Hacker CEH Career Path Graphics PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting IT Data Services Certification Programs Certified Ethical Hacker CEH Career Path Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Information, Management, Requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
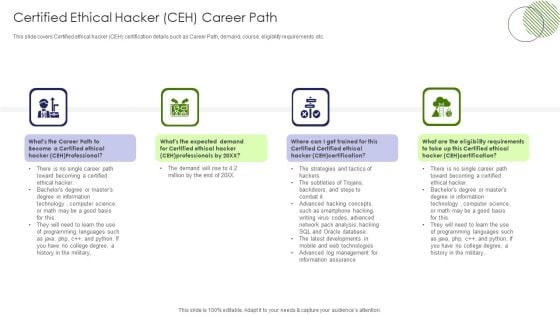
IT Professional Data Certification Program Certified Ethical Hacker CEH Career Path Guidelines PDF
This slide covers Certified ethical hacker CEH certification details such as Career Path, demand, course, eligibility requirements etc. Presenting IT Professional Data Certification Program Certified Ethical Hacker CEH Career Path Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Information, Demand, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home