hacking
Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
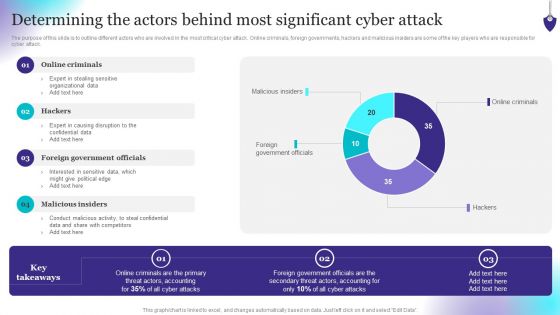
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
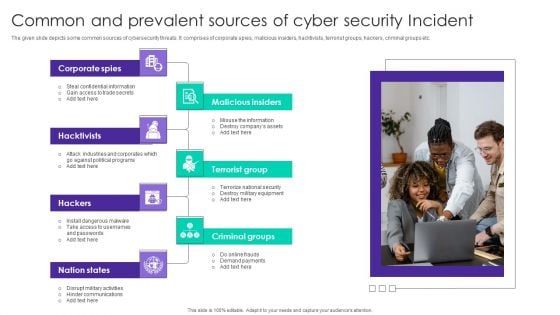
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Certification Information Technology Professionals Top Hiring Industries For IT Certification Icons PDF
This template covers top hiring industries for certification courses such as ITIL foundation certification, project management professional certification and many others This is a certification information technology professionals salary in different countries icons pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project management, ethical hacker, architect certification, developer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certification Information Technology Professionals What Are Certification Infographics PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description This is a certification information technology professionals what are certification infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like certification, preparation, fundamentals, practitioners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
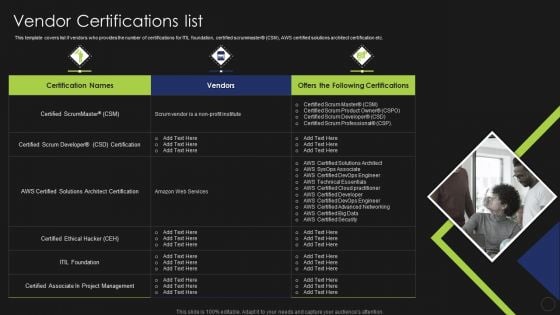
Information Technology Certifications Advantages Vendor Certifications List Graphics PDF
This template covers list if vendors who provides the number of certifications for ITIL foundation, certified scrummaster CSM, AWS certified solutions architect certification etc. This is a Information Technology Certifications Advantages Vendor Certifications List Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Certifications Advantages Who Should Take Which Cert Ideas PDF
This template covers details on who should take certified solutions and certification course for certified associate in project management, certified scrum developer CSD certification etc. Presenting Information Technology Certifications Advantages Who Should Take Which Cert Ideas PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified ScrumMaster, Certified Scrum Deve, Certified Ethical Hacker. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Certifications Advantages Why Companies Hire Professionals Sample PDF
This template covers reasons why company wants to hire certified professionals for ITIL Foundation certified scrummaster CSM,AWS Certififed solutions architect certification etc. This is a Information Technology Certifications Advantages Why Companies Hire Professionals Sample PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides
We present our block to multiple values lin centre and on arms ppt business plan template PowerPoint Slides.Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download our Puzzles or Jigsaws PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Process and Flows PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to abstract, binary, business, code, commerce, communication, computer, concept, connect, connection, corporate, cyberspace, data, digital, download, ecommerce, electronic, futuristic, global, hacker, information, internet, multiple, network, networking, online, program, programming, security, software, tech, technology, values. The prominent colors used in the PowerPoint template are Blue, Gray, White. Get classy with our Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides. They ensure A-list clients.
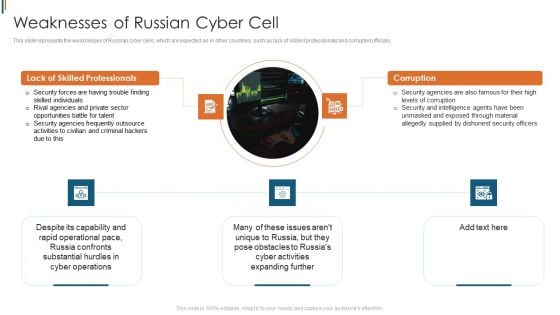
Ukraine Cyberwarfare Weaknesses Of Russian Cyber Cell Brochure Pdf
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Presenting ukraine cyberwarfare weaknesses of russian cyber cell brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security forces are having trouble finding skilled individuals, rival agencies and private sector opportunities battle for talent, security agencies frequently outsource activities to civilian and criminal hackers due to this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
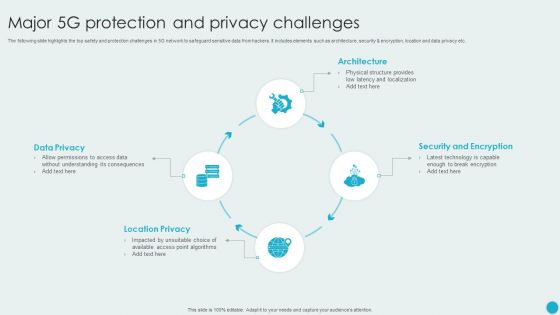
Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
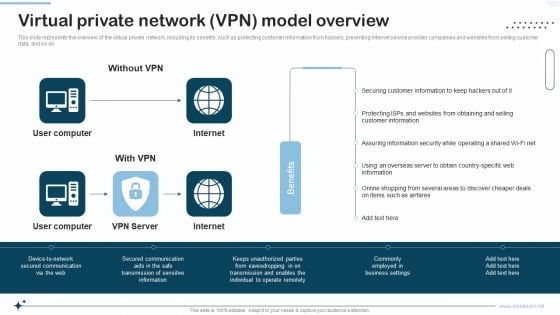
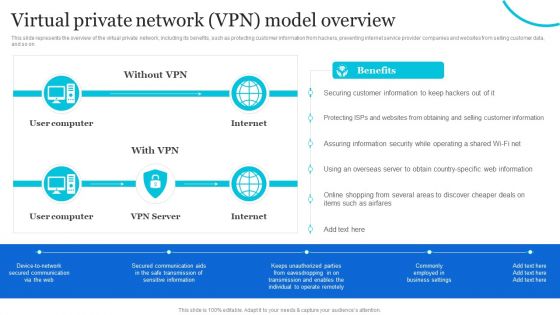
Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF bundle. Topics like Secured Communication, Business, Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
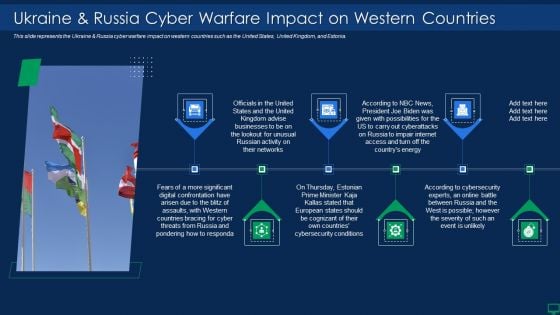
Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Impact Information PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare impact information pdf bundle. Topics like ukraine and russia cyber warfare russian vigilante hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
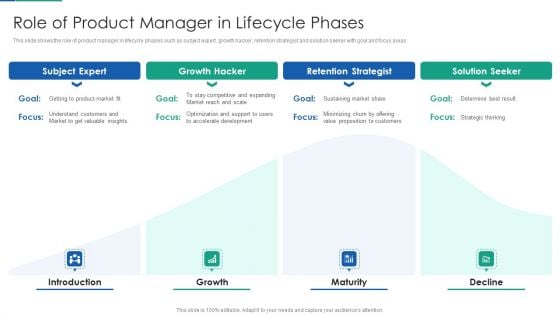
Agile Product Life Process Management Role Of Product Manager In Lifecycle Phases Clipart PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a agile product life process management role of product manager in lifecycle phases clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like retention strategist, growth hacker, subject expert, solution seeker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
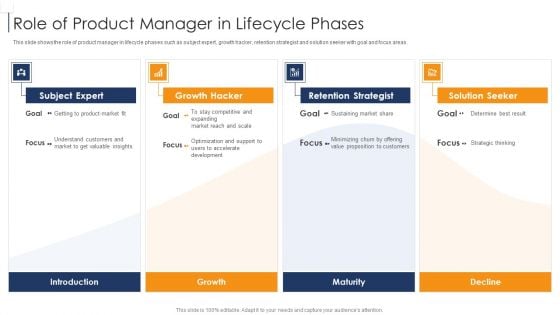
Product Lifecycle Management IT Role Of Product Manager In Lifecycle Phases Themes PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a product lifecycle management it role of product manager in lifecycle phases themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like subject expert, growth hacker, retention strategist, solution seeker . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
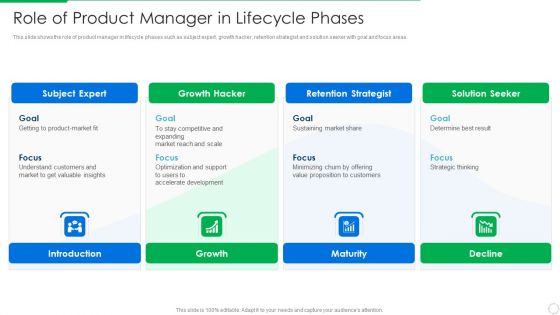
PLM Execution In Company Role Of Product Manager In Lifecycle Phases Sample PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a plm execution in company role of product manager in lifecycle phases sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like subject expert, growth hacker, retention strategist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
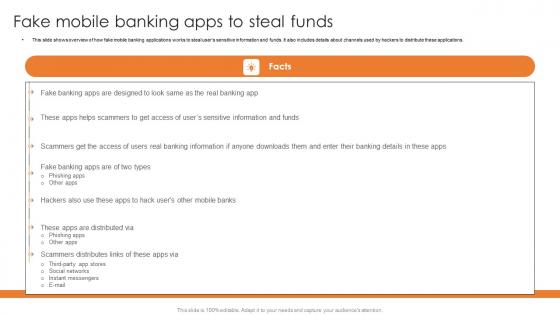
Fake Mobile Banking Apps To Steal Funds Comprehensive Smartphone Banking Ideas Pdf
This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications. Make sure to capture your audiences attention in your business displays with our gratis customizable Fake Mobile Banking Apps To Steal Funds Comprehensive Smartphone Banking Ideas Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications.
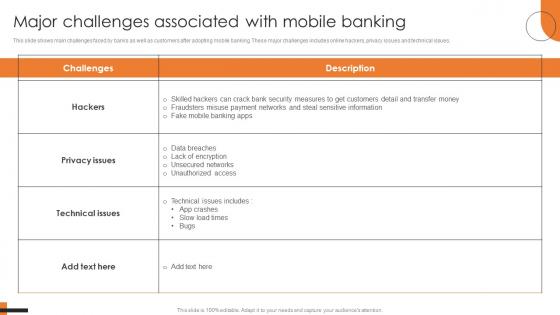
Major Challenges Associated With Mobile Banking Comprehensive Smartphone Banking Graphics Pdf
This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues. Do you know about Slidesgeeks Major Challenges Associated With Mobile Banking Comprehensive Smartphone Banking Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues.
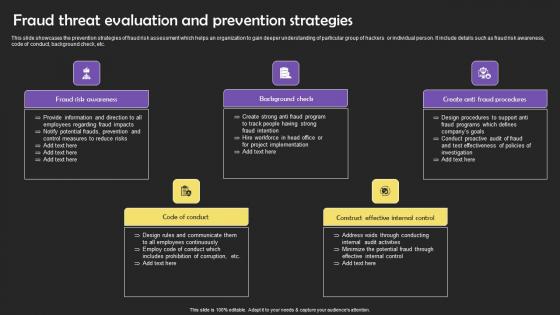
Fraud Threat Evaluation And Prevention Strategies Clipart Pdf
This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc. Showcasing this set of slides titled Fraud Threat Evaluation And Prevention Strategies Clipart Pdf The topics addressed in these templates are Fraud Risk Awareness, Background Check, Code Of Conduct All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc.

Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf
This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer. Showcasing this set of slides titled Most Impactful Data Breaches In Cybersecurity In Medical Industry Inspiration Pdf. The topics addressed in these templates are Data Breaches, Respondents, Mitigation Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents most impactful data breaches in healthcare cybersecurity along with solutions to prevent them helpful for organizations to mitigate risks of losing data or system. It includes internal attack, hacker attack, accidently published information, configuration error, lost stolen media and computer.
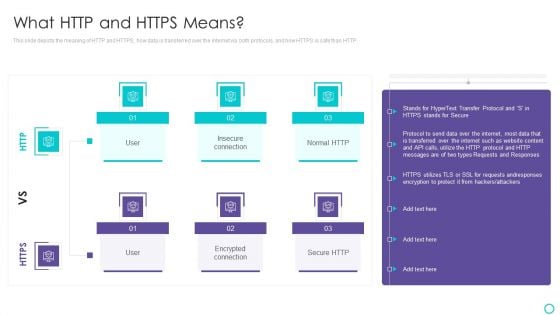
Website Designing And Development Service What HTTP And HTTPS Means Information PDF
This slide depicts the meaning of HTTP and HTTPS, how data is transferred over the internet via both protocols, and how HTTPS is safe than HTTP.Deliver an awe inspiring pitch with this creative Website Designing And Development Service What HTTP And HTTPS Means Information PDF bundle. Topics like Encrypted Connection, Transferred Over The Internet, Hackers Or Attackers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Information Technology Risks Form Human Threat Source Ideas PDF bundle. Topics like Computer Criminal, Industrial Espionage, System Intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
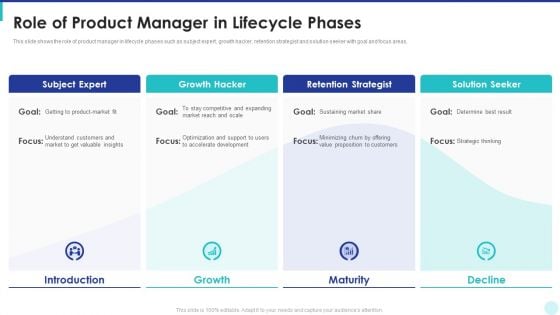
Optimization Of Product Development Life Cycle Role Of Product Manager In Lifecycle Phases Demonstration PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. Presenting optimization of product development life cycle role of product manager in lifecycle phases demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like introduction, growth, maturity, decline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
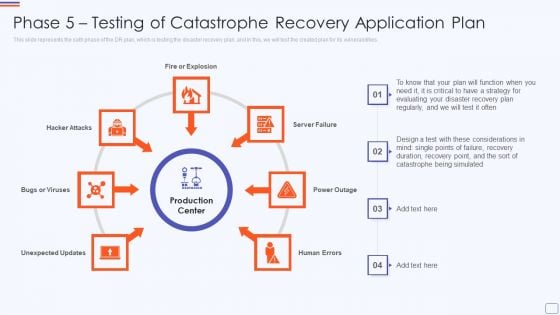
Phase 5 Testing Of Catastrophe Recovery Application Plan Mockup PDF
This slide represents the sixth phase of the DR plan, which is testing the disaster recovery plan, and in this, we will test the created plan for its vulnerabilities. Presenting phase 5 testing of catastrophe recovery application plan mockup pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like fire or explosion, hacker attacks, server failure, power outage, human errors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
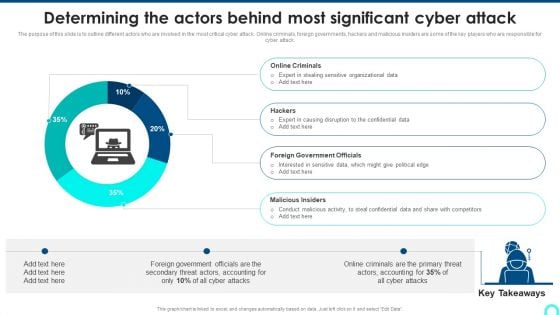
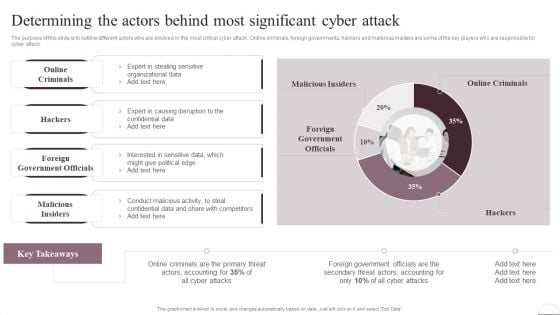
Determining The Actors Behind Most Significant Cyber Attack Download PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver and pitch your topic in the best possible manner with this Determining The Actors Behind Most Significant Cyber Attack Download PDF. Use them to share invaluable insights on Online Criminals, Causing Disruption, Government Officials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
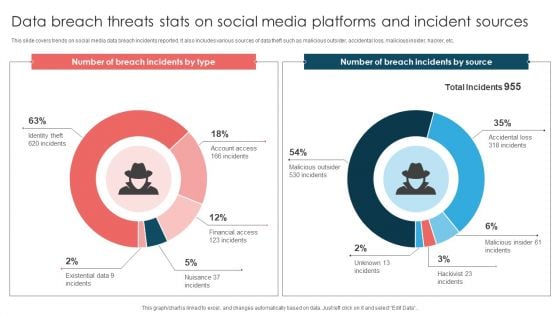
Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF
This slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Pitch your topic with ease and precision using this Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF. This layout presents information on Number Breach, Total Incidents, Malicious Insider. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
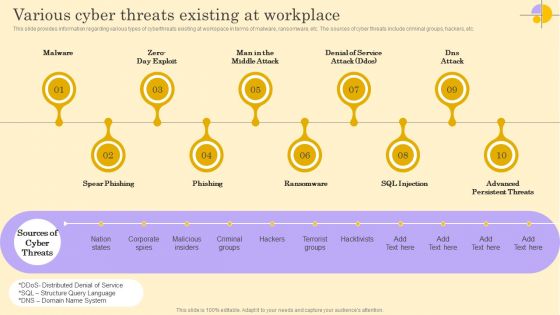
Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF
This slide provides information regarding various types of cyberthreats existing at workspace in terms of malware, ransomware, etc. The sources of cyber threats include criminal groups, hackers, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
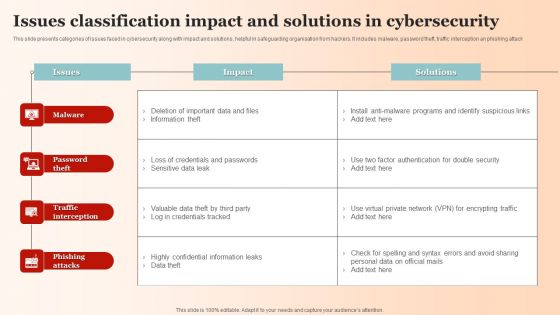
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
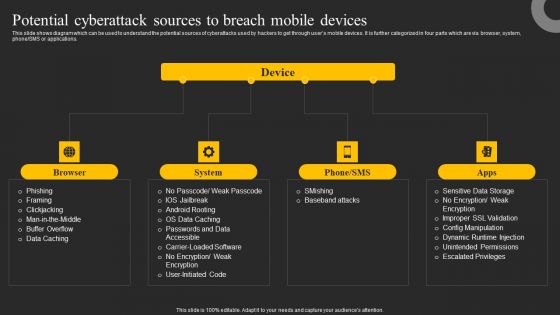
Potential Cyberattack Sources To Breach Mobile Devices Ppt Infographics Graphics Template PDF
This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Make sure to capture your audiences attention in your business displays with our gratis customizable Potential Cyberattack Sources To Breach Mobile Devices Ppt Infographics Graphics Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
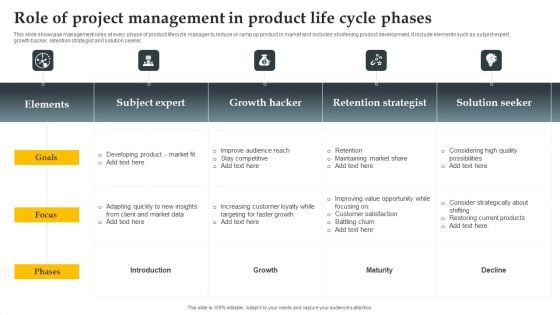
Role Of Project Management In Product Life Cycle Phases Infographics PDF
This slide showcase management roles at every phase of product lifecycle manager to reduce or ramp up product in market and includes shortening product development. It include elements such as subject expert, growth hacker, retention strategist and solution seeker. Pitch your topic with ease and precision using this Role Of Project Management In Product Life Cycle Phases Infographics PDF. This layout presents information on Goals, Developing Product, Faster Growth. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
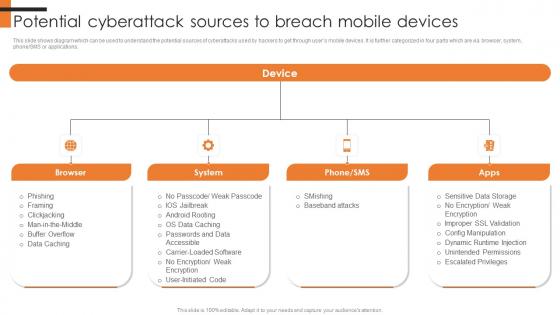
Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf
This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phoneorSMS or applications.If you are looking for a format to display your unique thoughts, then the professionally designed Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Potential Cyberattack Sources To Breach Mobile Comprehensive Smartphone Banking Microsoft Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phoneorSMS or applications.

IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using IT System Risk Management Guide Information Technology Risks Form Human Threat Source Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
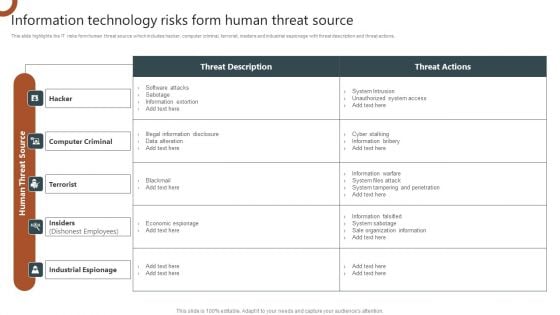
Information Technology Risks Form Human Threat Source Summary PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. If you are looking for a format to display your unique thoughts, then the professionally designed Information Technology Risks Form Human Threat Source Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Technology Risks Form Human Threat Source Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

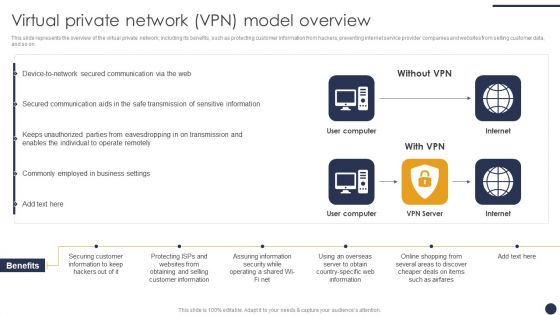
Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Are you searching for a Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF from Slidegeeks today.
Integrating Naas Service Model Virtual Private Network Vpn Model Overview Ppt Summary Visuals PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest. Look no further than Integrating Naas Service Model Virtual Private Network Vpn Model Overview Ppt Summary Visuals PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Integrating Naas Service Model Virtual Private Network Vpn Model Overview Ppt Summary Visuals PDF today and make your presentation stand out from the rest.
Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Naas Architectural Framework Virtual Private Network VPN Model Overview Portrait PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Naas Architectural Framework Virtual Private Network VPN Model Overview Portrait PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
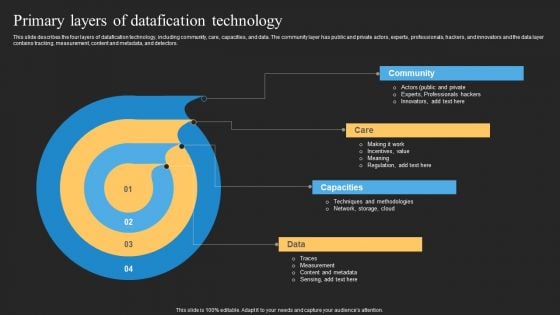
Datafy Primary Layers Of Datafication Technology Structure PDF
This slide describes the four layers of datafication technology, including community, care, capacities, and data. The community layer has public and private actors, experts, professionals, hackers, and innovators and the data layer contains tracking, measurement, content and metadata, and detectors. Retrieve professionally designed Datafy Primary Layers Of Datafication Technology Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
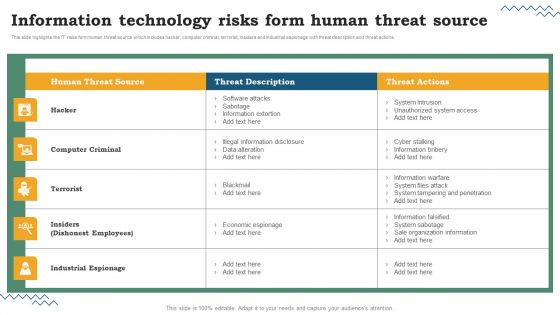
Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF
This slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Evaluation Of Information Technology Systems Information Technology Risks Form Human Threat Source Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
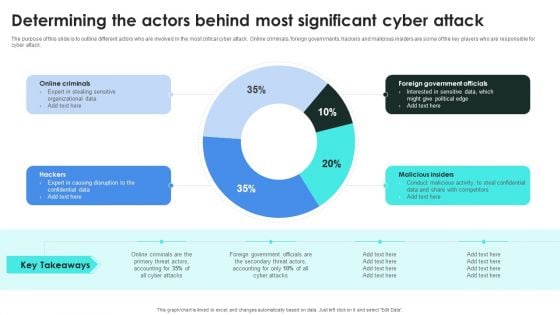
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
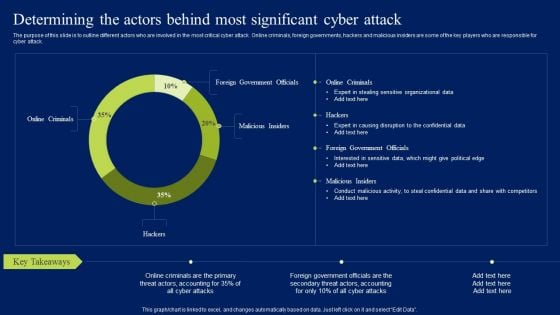
Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Want to ace your presentation in front of a live audience Our Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF
This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Major Challenges Associated With Mobile Banking Ppt Show Maker PDF
This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues. Find highly impressive Major Challenges Associated With Mobile Banking Ppt Show Maker PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Major Challenges Associated With Mobile Banking Ppt Show Maker PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

 Home
Home