Data Privacy

Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. This modern and well arranged Strategies To Avoid Mobile Banking Frauds Ppt Show Layout PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Control Access To Private Content Ppt PowerPoint Presentation Portfolio Outfit
This is a control access to private content ppt powerpoint presentation portfolio outfit. This is a three stage process. The stages in this process are access rights, access management, business.
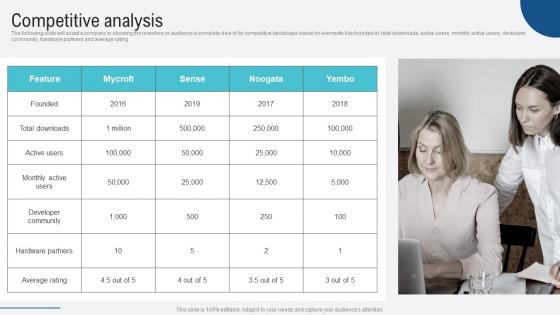
Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating.
Identity Info Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with scaned hand for internet identity and security Our Identity Info Security PowerPoint Templates And PowerPoint Backgrounds 0211 make many a feat feasible. They ease out all difficulties.

Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF
This slide depicts facebook and twitters suggestion for ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Finance Security Money PowerPoint Template 0610
Stack of Money with a Lock and Key - Financial Security Concept Observe growth with our Finance Security Money PowerPoint Template 0610. Download without worries with our money back guaranteee.
Rescue Statistics PowerPoint Icon S
3d illustration of a multi-segment colorful bar chart placed inside of a large red and white lifesaver on a reflective surface Empower yourself with our Rescue Statistics PowerPoint Icon S. Put extra force behind your thoughts.
Rescue Statistics PowerPoint Icon C
3d illustration of a multi-segment colorful bar chart placed inside of a large red and white lifesaver on a reflective surface Be the early bird with our Rescue Statistics PowerPoint Icon C. Be the first on the block with your thoughts.
Rescue Statistics PowerPoint Icon Cc
3d illustration of a multi-segment colorful bar chart placed inside of a large red and white lifesaver on a reflective surface Get the nod for your plans with our Rescue Statistics PowerPoint Icon Cc. You will be at the top of your game.

Secure Files Business PowerPoint Template 1110
Simple 3d illustration of a lock placed in front of an open file folder Count on our Secure Files Business PowerPoint Template 1110 to carry the can. They will never belie your faith.

Unlock Your Potential Security PowerPoint Template 1110
A safe lock dial with the words Unlock Your Potential on it Our Unlock Your Potential Security PowerPoint Template 1110 ensure your credentials are established. Your abilities will be acknowledged by all.
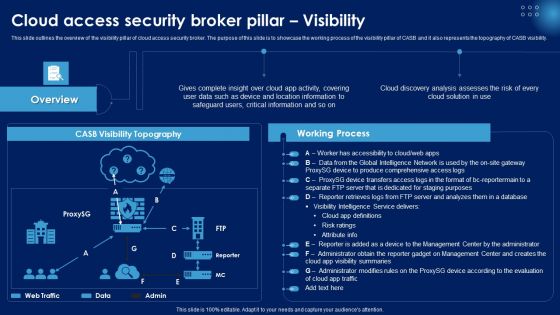
Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Control Laptop Access Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security control laptop access ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the eleven slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 0912
Security Real Estate Finance PowerPoint Templates And PowerPoint Themes Presentations-Microsoft Powerpoint Templates and Background with us money locked in a padlock with keys-Security Real Estate Finance PowerPoint Templates And PowerPoint Themes PresentationsThis PPT can be used for presentations relating to-Us money locked in a padlock with keys, security, money, finance, business, real estate Put your ideas out to flower. Our Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 0912 will get them to bloom.

Confidential Files Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Locked file holder (3D rendered illustration over white background) Chase dreams with our Confidential Files Security PowerPoint Backgrounds And Templates 1210. You will come out on top.

Passport Security Americana PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with American passport with lock chain and flag Facilitate your entry into that exclusive group. Establish your claim with our Passport Security Americana PowerPoint Backgrounds And Templates 1210.

Music Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with musical note sitting inside of a locked glass Ecology is a common concern. Express your beliefs with our Music Security PowerPoint Templates And PowerPoint Backgrounds 0711.

Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it List your core competencies with our Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811. They will make you look good.

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it Our Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811 have amazing characteristics. They educate and entertain on your command.

Music Security PowerPoint Themes And PowerPoint Slides 0711
Microsoft PowerPoint Theme and Slide with musical note sitting inside of a locked glass Make a great career call with our Music Security PowerPoint Themes And PowerPoint Slides 0711. Put your ideas across emphatically.
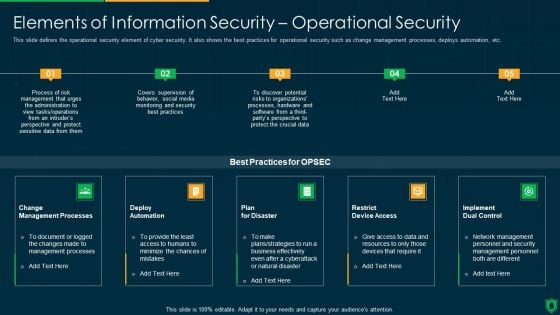
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Time Text With Lock For Time Management PowerPoint Slide
Concept of time management can be well explained with this unique image slide. This slide contains the graphic of time text with lock. Use this professional image to mesmerize your viewers.

Stock Photo Dollar Bundles Safe With Lock And Chain Image Graphics For PowerPoint Slide
This image slide displays dollar bundle locked with chain. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.
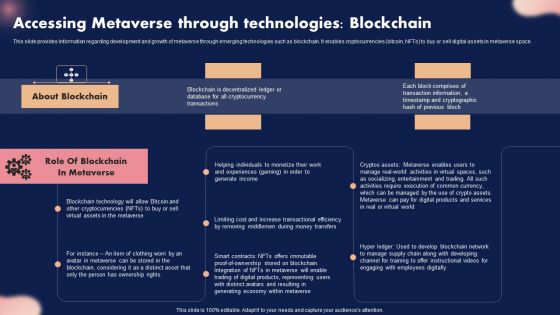
Accessing Metaverse Through Technologies Blockchain Ppt Inspiration Graphics Tutorials PDF
This slide provides information regarding development and growth of metaverse through emerging technologies such as blockchain. It enables cryptocurrencies bitcoin, NFTs to buy or sell digital assets in metaverse space. Boost your pitch with our creative Accessing Metaverse Through Technologies Blockchain Ppt Inspiration Graphics Tutorials PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
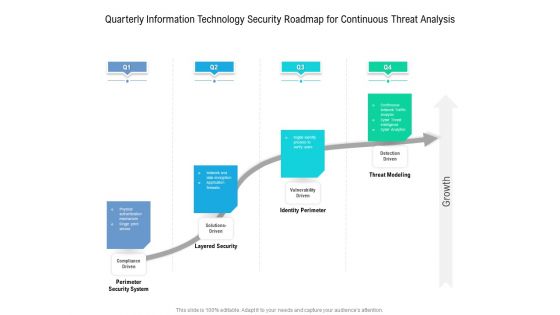
Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Business Diagram Lock With Missing Puzzle Piece Presentation Template

Accessing Metaverse Through Technologies Artificial Intelligence AI Microsoft PDF
This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Boost your pitch with our creative Accessing Metaverse Through Technologies Artificial Intelligence AI Microsoft PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
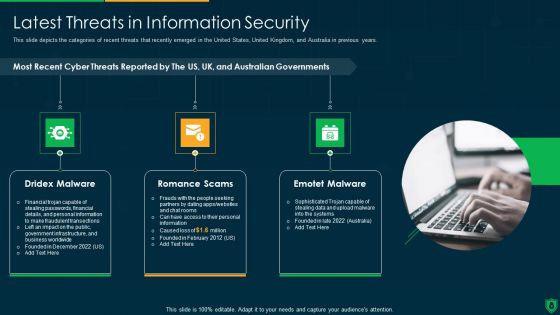
Info Security Latest Threats In Information Security Ppt PowerPoint Presentation Gallery Shapes PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a info security latest threats in information security ppt powerpoint presentation gallery shapes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like most recent, cyber threats reported, dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
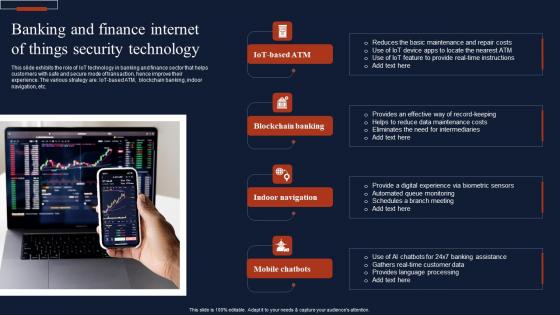
Banking And Finance Internet Of Things Security Technology Information Pdf
This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc. Pitch your topic with ease and precision using this Banking And Finance Internet Of Things Security Technology Information Pdf This layout presents information on Blockchain Banking, Ndoor Navigation, Mobile Chatbots It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc.

Rescue Statistics Business PowerPoint Templates And PowerPoint Themes 1112
Rescue Statistics Business PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint Template contains an image of lifesaver and multicolored bar graphs which depict the concept of rescue statistics. Use our Success PowerPoint Templates because; amplify your thoughts via our appropriate templates. Use our Business PowerPoint Templates because, Business Template: - There is a vision, a need you can meet. Present your views using our innovative slides and be assured of leaving a lasting impression.-Rescue Statistics Business PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Rescue Statistics, Business, Security, Marketing, Finance, Abstract Make sure your audience learns with our Rescue Statistics Business PowerPoint Templates And PowerPoint Themes 1112. Make sure your presentation gets the attention it deserves.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks.
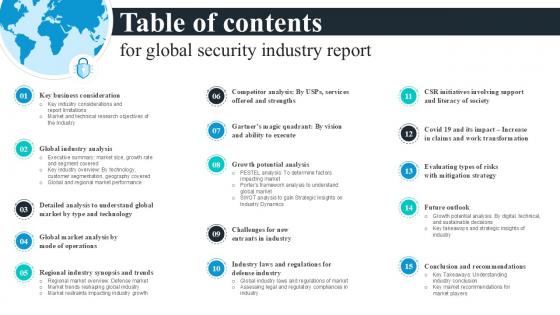
Table Of Contents For Global Security Industry Report PPT Template IR SS V
Slidegeeks has constructed Table Of Contents For Global Security Industry Report PPT Template IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents For Global Security Industry Report PPT Template IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
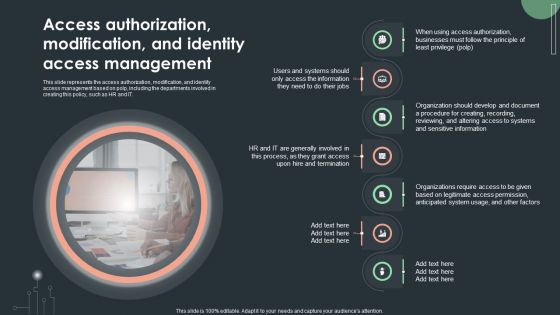
Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF
This slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Pie Chart Statistics Success PowerPoint Templates And PowerPoint Themes 0512
Pie Chart Statistics Success PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with key in shape of pie chart Banish the blues with our Pie Chart Statistics Success PowerPoint Templates And PowerPoint Themes 0512. Your thoughts will bring in the cheer.
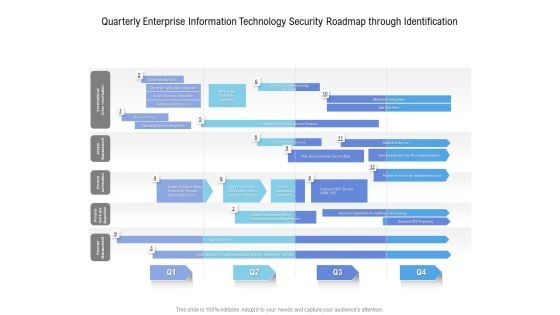
Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Protect Us Dollar Money PowerPoint Templates And PowerPoint Themes 0912
Protect Us Dollar Money PowerPoint Templates And PowerPoint Themes Presentations-Microsoft Powerpoint Templates and Background with us money locked in a padlock-Protect Us Dollar Money PowerPoint Templates And PowerPoint Themes PresentationsThis PPT can be used for presentations relating to-Us money locked in a padlock, security, money, finance, business, future Achieve high-performance with our Protect Us Dollar Money PowerPoint Templates And PowerPoint Themes 0912. They will make you look good.
7 Stages Of Functional Information Security Business Plan PowerPoint Slides
We present our 7 stages of functional information security business plan PowerPoint Slides .Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Flow Charts PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to Abstract, arrows, balance, business, chart, company, concept, data, diagram, document, finance, financial, report, graph, market, marketing, price, profit, report, statistics, stock, success, trade, work. The prominent colors used in the PowerPoint template are Purple, White, Gray. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by professionals Customers tell us our business PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our 7 stages of functional information security business plan PowerPoint Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our concept PowerPoint templates and PPT Slides will impress their bosses and teams. Presenters tell us our 7 stages of functional information security business plan PowerPoint Slides are designed by a team of presentation professionals. People tell us our balance PowerPoint templates and PPT Slides will save the presenter time. Ask any favour of our 7 Stages Of Functional Information Security Business Plan PowerPoint Slides. You will find them truly accomodating.
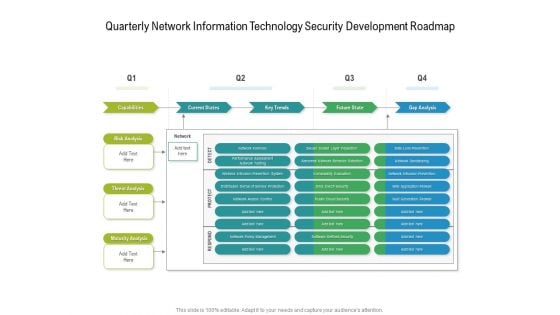
Quarterly Network Information Technology Security Development Roadmap Diagrams
Presenting our jaw dropping quarterly network information technology security development roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Male And Female Symbol PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Male And Female Symbols on a lock on a white background Display world class organization with our Male And Female Symbol PowerPoint Backgrounds And Templates 1210. They will make you look good.
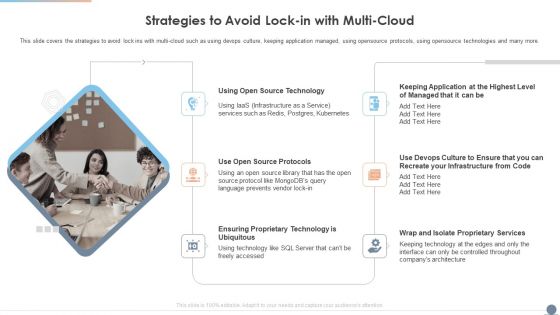
Multi Cloud Complexity Management Strategies To Avoid Lock In With Multi Cloud Elements PDF
This slide covers the strategies to avoid lock ins with multi cloud such as using devops culture, keeping application managed, using opensource protocols, using opensource technologies and many more. This is a Multi Cloud Complexity Management Strategies To Avoid Lock In With Multi Cloud Elements PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Source Technology, Source Protocols, Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Network Safety Problems With Lock Icon Ppt PowerPoint Presentation Gallery Samples PDF
Presenting cloud network safety problems with lock icon ppt powerpoint presentation gallery samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, environments, vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
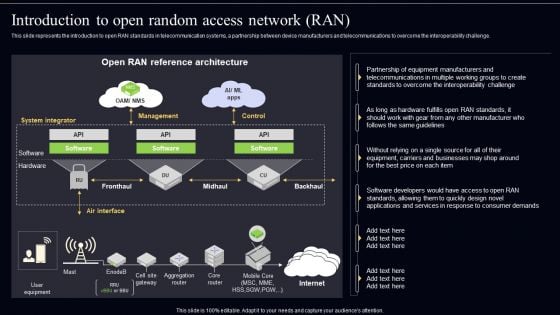
Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF
This slide represents the introduction to open RAN standards in telecommunication systems, a partnership between device manufacturers and telecommunications to overcome the interoperability challenge. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Open Radio Access Network IT Introduction To Open Random Access Network RAN Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Comparative Analysis Of Vulnerability Scanning Application Security Testing
This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparative Analysis Of Vulnerability Scanning Application Security Testing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
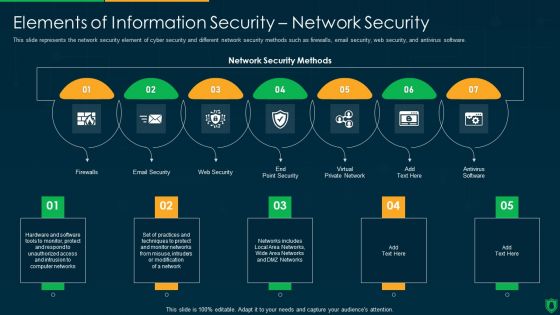
Info Security Elements Of Information Security Network Security Ppt PowerPoint Presentation File Vector PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting info security elements of information security network security ppt powerpoint presentation file vector pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like email security, web security, virtual private network, firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
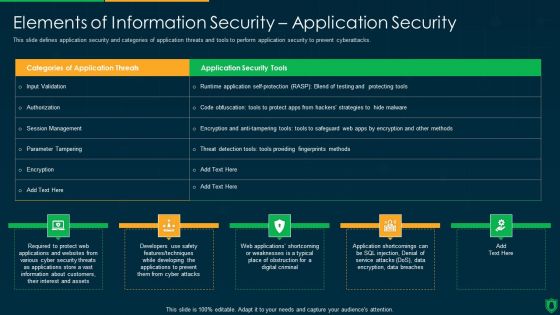
Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Analytics Use Cases In Powerpoint And Google Slides Cpb
Introducing our well designed Security Analytics Use Cases In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Analytics Use Cases. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Analytics Use Cases In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Figures Icon Infographics For Security Best Practices Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this figures icon infographics for security best practices ppt powerpoint presentation file graphics example pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including figures icon infographics for security best practices. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
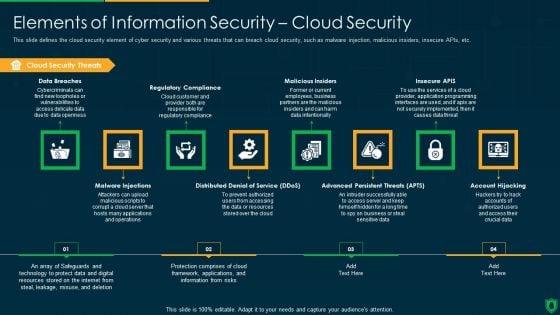
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Network Safety Shield With Lock Symbol Vector Ppt PowerPoint Presentation File Maker PDF
This is a cloud network safety shield with lock symbol vector ppt powerpoint presentation file maker pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud network safety shield with lock symbol vector. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Multiple Device Based Internet Of Things Security Icon Formats Pdf
Showcasing this set of slides titled Multiple Device Based Internet Of Things Security Icon Formats Pdf The topics addressed in these templates are Multiple Device Based, Internet Of Things, Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Multiple Device Based Internet Of Things Security Icon Formats Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf
Showcasing this set of slides titled Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf. The topics addressed in these templates are Unauthorized Computer, Access, Causing Virtual Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Unauthorized Computer Access Icon Causing Virtual Security Hazards Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
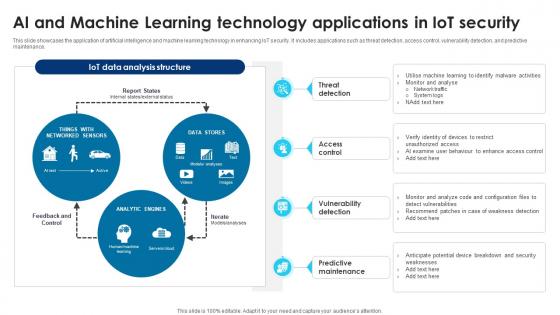
Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V
This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance. Boost your pitch with our creative Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance.
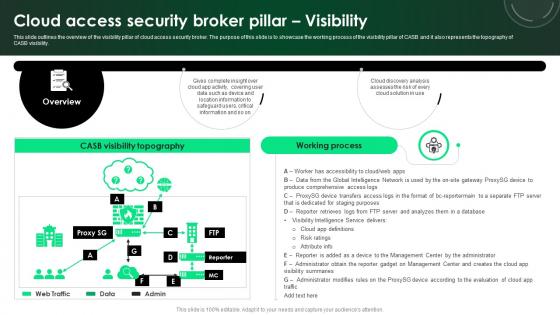
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.
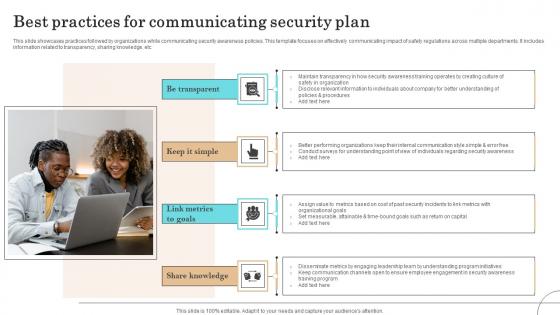
Best Practices For Communicating Security Plan Infographics Pdf
This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc Pitch your topic with ease and precision using this Best Practices For Communicating Security Plan Infographics Pdf This layout presents information on Measurable Attainable, Keep Communication, Maintain Transparency It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases practices followed by organizations while communicating security awareness policies. This template focuses on effectively communicating impact of safety regulations across multiple departments. It includes information related to transparency, sharing knowledge, etc
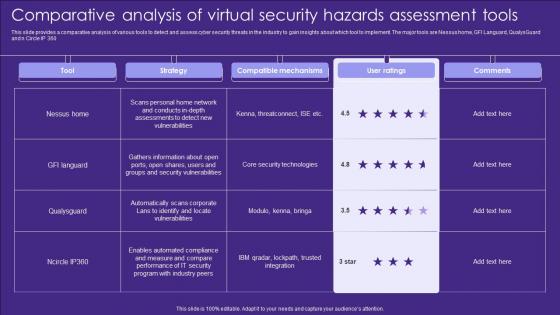
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360
Cyber Security Breach Icon To Prevent Threat Brochure Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon To Prevent Threat Brochure Pdf This layout presents information on Cyber Security Breach, Icon To Prevent Threat It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon To Prevent Threat Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Virtual Security Hazards And Network Hacking Icon Diagrams Pdf
Pitch your topic with ease and precision using this Virtual Security Hazards And Network Hacking Icon Diagrams Pdf. This layout presents information on Virtual Security, Hazards, Network Hacking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Virtual Security Hazards And Network Hacking Icon Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
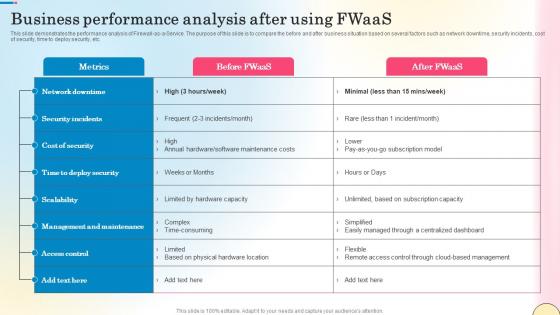
Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc.


 Continue with Email
Continue with Email

 Home
Home


































