Data Privacy

Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V
This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc. Present like a pro with Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc.
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
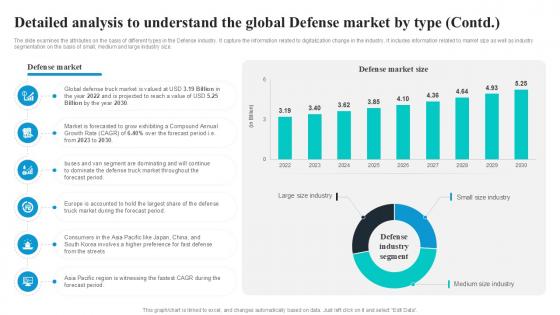
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.

Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Top Rated Outdoor Security Lights that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation
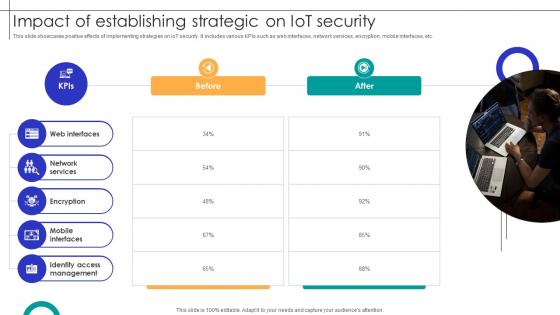
This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc. Retrieve professionally designed Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc.
Research Objectives To Understand Global Security Industry PPT Template IR SS V
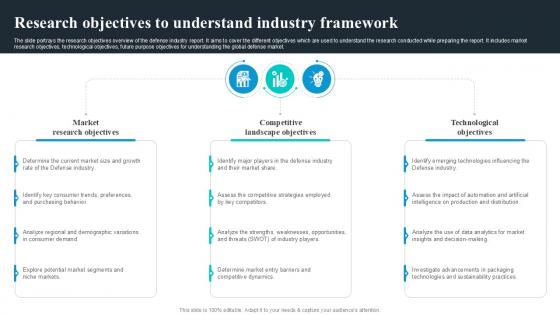
The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats. The slide portrays the research objectives overview of the defense industry report. It aims to cover the different objectives which are used to understand the research conducted while preparing the report. It includes market research objectives, technological objectives, future purpose objectives for understanding the global defense market. Are you searching for a Research Objectives To Understand Global Security Industry PPT Template IR SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Research Objectives To Understand Global Security Industry PPT Template IR SS V from Slidegeeks today. The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats.

5G Technology Development For Digital Transformation Determine Fixed Wireless Access FWA Offerings For Operators Structure PDF
This slide provides details regarding fixed wireless access FWA offerings for operators. Explore a selection of the finest 5G Technology Development For Digital Transformation Determine Fixed Wireless Access FWA Offerings For Operators Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our 5G Technology Development For Digital Transformation Determine Fixed Wireless Access FWA Offerings For Operators Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
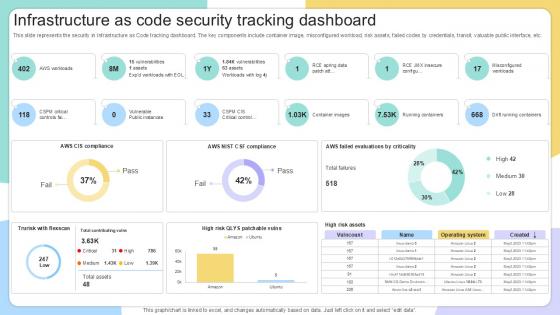
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.

Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Welcome to our selection of the Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc.

Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc.
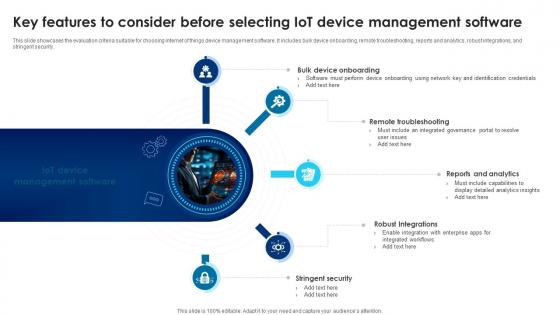
Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.

Stock Photo Unlocked Money With Key For Security Concept PowerPoint Slide
This image slide displays unlocked money security concept with key. This image slide has been designed with dollar bundle locked with padlock and key. This image slide may be used in your presentations to express views on finance, savings, protection and accounting business finance. Create professional presentations using this image slide.

Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs. Explore a selection of the finest Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs.
Security Playbook Example In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Playbook Example In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Playbook Example that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Playbook Example In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Smartphones Mobile Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Smartphones Mobile Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Smartphones Mobile Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Smartphones Mobile Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
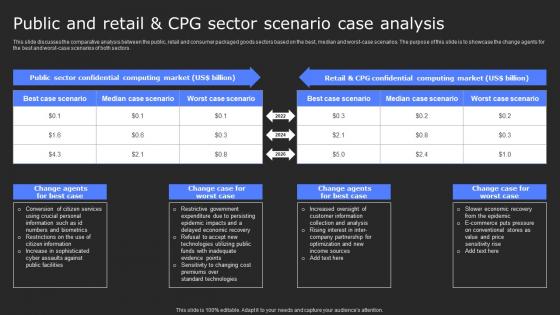
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
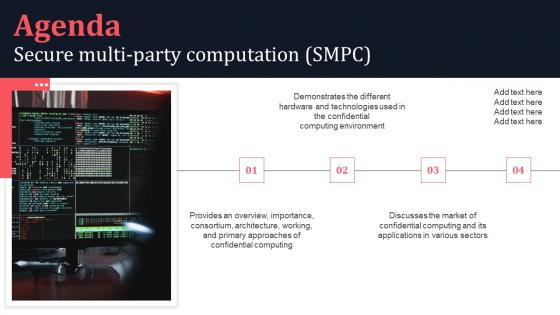
Agenda Secure Multi Party Computation SMPC Professional Pdf
Take your projects to the next level with our ultimate collection of Agenda Secure Multi Party Computation SMPC Professional Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. Our Agenda Secure Multi Party Computation SMPC Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
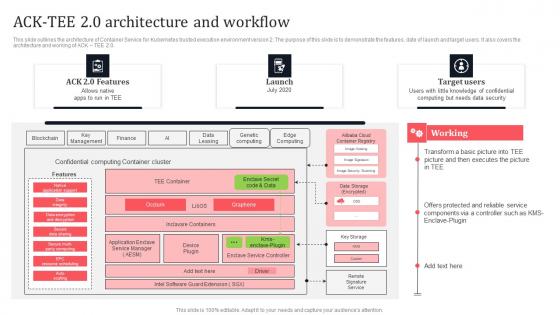
Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
Business Process Flowchart Examples 4 Stages Spoke Design Center Lock PowerPoint Slides

Locked Money Bank For Retirement PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Locked Money Bank For Retirement PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our People PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.Use these PowerPoint slides for presentations relating to Man drawing an organization chart, people, business, marketing, success, shapes. The prominent colors used in the PowerPoint template are Red, Gray, White. Fashionable is what fashionable does. With our Locked Money Bank For Retirement PowerPoint Templates Ppt Backgrounds For Slides 0313 you will fit the bill.

Business Finance Security PowerPoint Templates And PowerPoint Themes 1112
We present our Business Finance Security PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,Explain the process by which you intend to right it. Use our Chains PowerPoint Templates because, Enlighten them with your brilliant understanding of mental health. Use our Money PowerPoint Templates because, Business Process Design:- The template offers an excellent background to build up the various stages of your business process. Use our Finance PowerPoint Templates because, They are logical, accurate and to the point. Use our Business PowerPoint Templates because, Brilliant ideas popping up all over the place.Use these PowerPoint slides for presentations relating to Dollars chained and locked, money, finance, business, security, chains . The prominent colors used in the PowerPoint template are Yellow, Black, White Make your brainstorming effective with our Business Finance Security PowerPoint Templates And PowerPoint Themes 1112. Churn out ideas to act upon.
Business Life Cycle Diagram 4 Stages Spoke Design Center Lock Ppt PowerPoint Slides
We present our business life cycle diagram 4 stages spoke design center lock ppt PowerPoint Slides.Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Present our Arrows PowerPoint Templates because It can Bubble and burst with your ideas. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need. Present our Flow Charts PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience.Use these PowerPoint slides for presentations relating to Act, arrow, blue, business, chart, check, circle, control, creative, cycle, development, diagram, flow, graphic, green, idea, life, lifecycle, management, marketing, model, plan, process, research, software, spiral, step, strategy, success, system, technology, vector, white, work. The prominent colors used in the PowerPoint template are Black, Gray, White. Our Business Life Cycle Diagram 4 Stages Spoke Design Center Lock Ppt PowerPoint Slides are clearly eye catching. One look and you will not want to even blink.
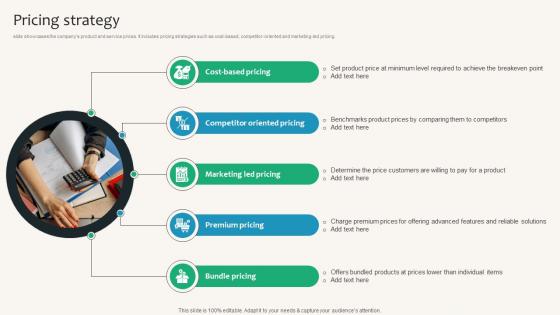
Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing.
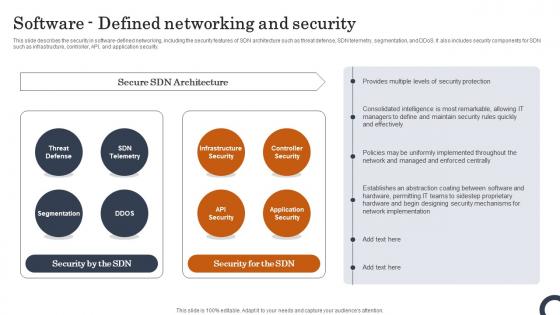
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation. The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry.

Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V
The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry. This Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry..
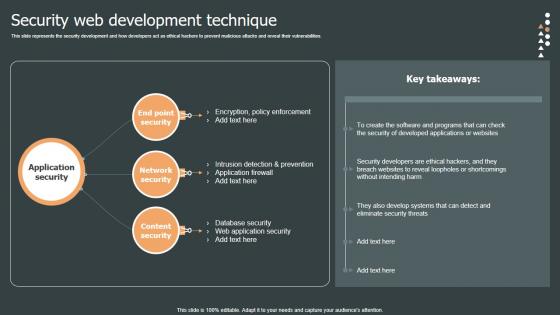
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
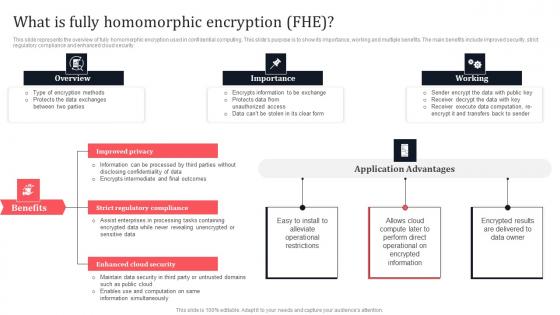
What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Make sure to capture your audiences attention in your business displays with our gratis customizable What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
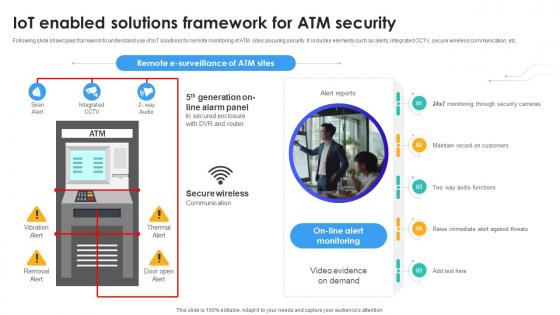
IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V
Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc.

IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide
This slide showcases the security of Infrastructure as Code for protecting cloud infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc. Retrieve professionally designed IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the security of Infrastructure as Code for protecting cloud infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc.
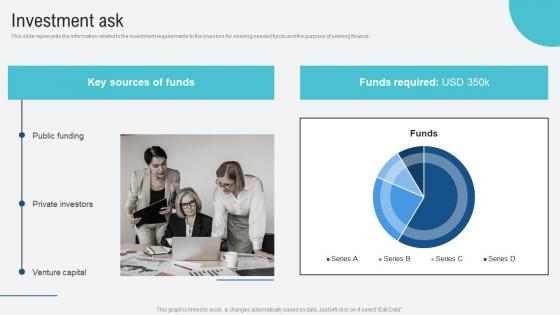
Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Are you searching for a Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf from Slidegeeks today. This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance.
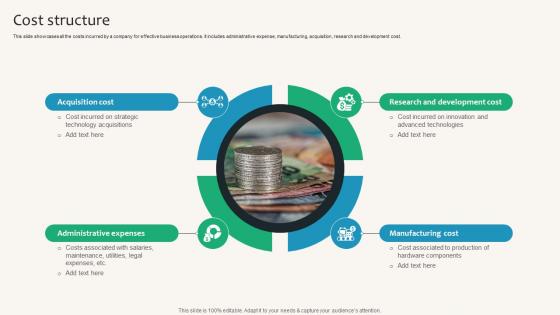
Cost Structure Security Service Provider Business Model BMC SS V
This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cost Structure Security Service Provider Business Model BMC SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost.
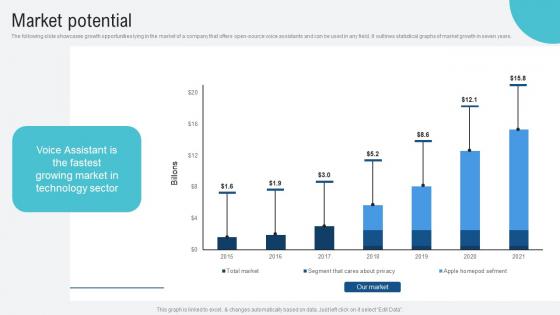
Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf
The following slide showcases growth opportunities lying in the market of a company that offers open source voice assistants and can be used in any field. It outlines statistical graphs of market growth in seven years. Presenting this PowerPoint presentation, titled Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases growth opportunities lying in the market of a company that offers open source voice assistants and can be used in any field. It outlines statistical graphs of market growth in seven years.
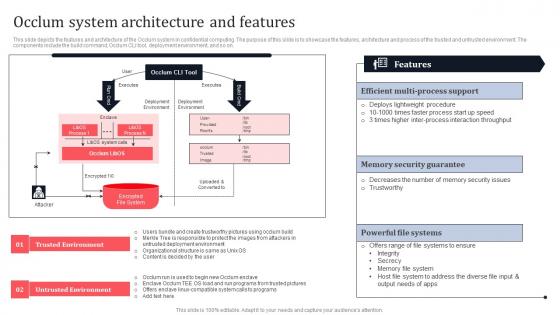
Occlum System Architecture And Features Secure Multi Party Slides Pdf
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Want to ace your presentation in front of a live audience Our Occlum System Architecture And Features Secure Multi Party Slides Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on.
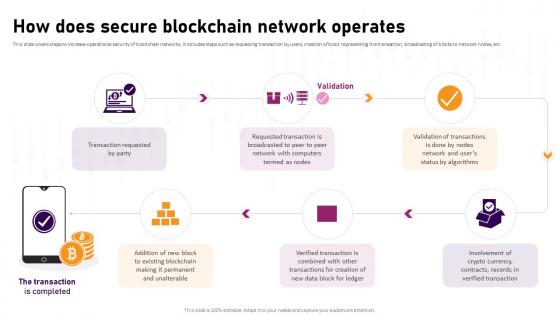
How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V
This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Retrieve professionally designed How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc.
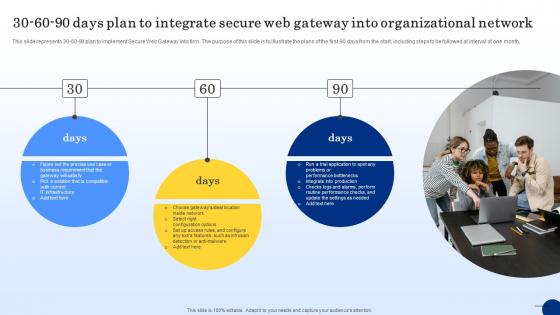
30 60 90 Days Plan To Integrate Secure Web Threat Protection System
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Integrate Secure Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.

Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Slidegeeks is here to make your presentations a breeze with Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.

Connectivity And Security Global PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with globe with wire around it conveying worldwide online security They consider you their father figure. Deliver on their expectations with our Connectivity And Security Global PowerPoint Backgrounds And Templates 1210.

Padlock And Coins Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our finance PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Download our Money PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Use our Future PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow.Use these PowerPoint slides for presentations relating to Financial security with lock and coins, security, business, finance, money, future. The prominent colors used in the PowerPoint template are Yellow, Brown, Black. People tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. People tell us our business PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. PowerPoint presentation experts tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our lock PowerPoint templates and PPT Slides have awesome images to get your point across. Presenters tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our finance PowerPoint templates and PPT Slides are visually appealing. Influence teams with our Padlock And Coins Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Explore a selection of the finest Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents Cybersecurity Risk Assessment Program Dashboard to effectively track cyber security risk levels. This will provide a structured approach for organizations to review and mitigate cyber threats. It includes multiple threat agents, attack methods, and preventive controls implemented with detailed insights, and it shows critical metrics including risk scores, the number of infected systems, and detected vulnerabilities.
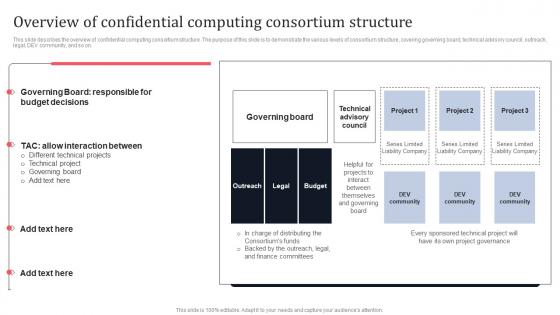
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
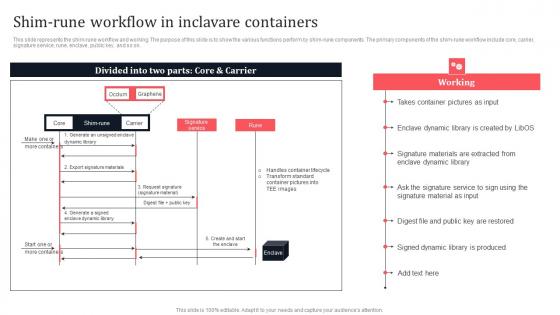
Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
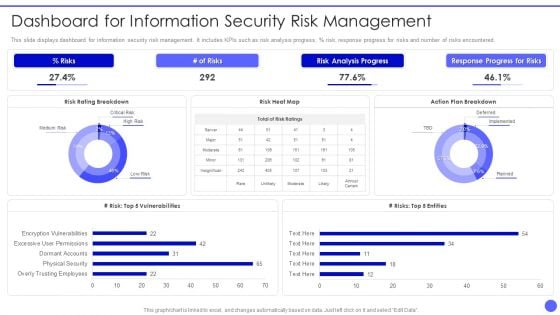
Info Safety And ISO 27001 Dashboard For Information Security Risk Management Information PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Dashboard For Information Security Risk Management Information PDF. Use them to share invaluable insights on Risks, Risk Analysis Progress, Response Progress for Risks, Risk Rating Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
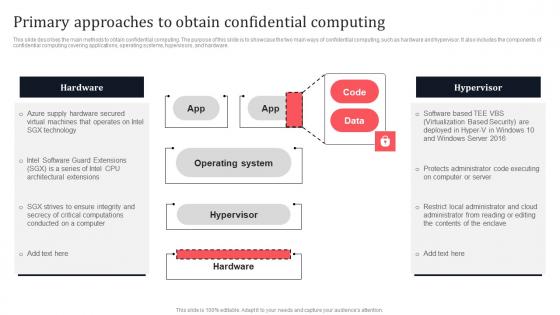
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
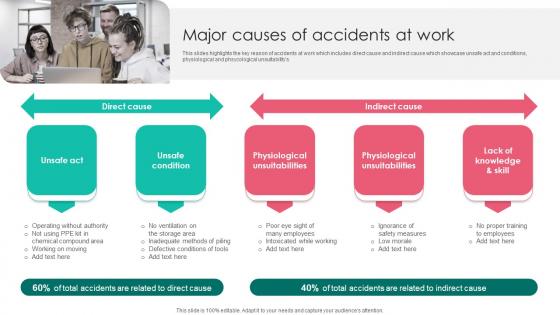
Major Causes Of Accidents Workplace Safety Protocol And Security Practices Portrait Pdf
This slides highlights the key reason of accidents at work which includes direct cause and indirect cause which showcase unsafe act and conditions, physiological and phsycological unsuitabilitys. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Causes Of Accidents Workplace Safety Protocol And Security Practices Portrait Pdf from Slidegeeks and deliver a wonderful presentation. This slides highlights the key reason of accidents at work which includes direct cause and indirect cause which showcase unsafe act and conditions, physiological and phsycological unsuitabilitys.

Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V
The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players.
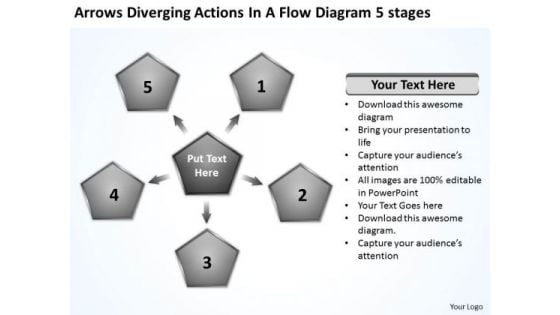
Actions In Flow Diagram 5 Stages Circular Layout Network PowerPoint Templates
We present our actions in flow diagram 5 stages Circular Layout Network PowerPoint templates.Use our Business PowerPoint Templates because spell out your advertising plans to increase market share. The feedback has been positive and productive. Download our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download our Future PowerPoint Templates because analyse your plans with equal sincerity. Download and present our Process and Flows PowerPoint Templates because it helps to churn the mixture to the right degree and pound home your views and expectations in a spectacularly grand and virtuoso fluid performance. Download our Marketing PowerPoint Templates because our PowerPoint templates designed for your ideas to sell.Use these PowerPoint slides for presentations relating to Action, adding, arrow, business, chart,circulation, communication, connection,conservation, cycle, data, design,direction, element, flow, flowchart, graph,graphic, group, icon, illustration, isolated,label, loop, management, network,orientation, planning, process, project,recycling, repeat, repetition, return,reuse, rotation, sign, sticker, strategy,symbol. The prominent colors used in the PowerPoint template are Gray, White, Black. You can be sure our actions in flow diagram 5 stages Circular Layout Network PowerPoint templates are Versatile. Professionals tell us our connection PowerPoint templates and PPT Slides are Ritzy. PowerPoint presentation experts tell us our actions in flow diagram 5 stages Circular Layout Network PowerPoint templates are the best it can get when it comes to presenting. You can be sure our business PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. You can be sure our actions in flow diagram 5 stages Circular Layout Network PowerPoint templates are Spiffy. The feedback we get is that our business PowerPoint templates and PPT Slides are Classic. Your thoughts will leave an everlasting image. Etch them in the memory with our Actions In Flow Diagram 5 Stages Circular Layout Network PowerPoint Templates.
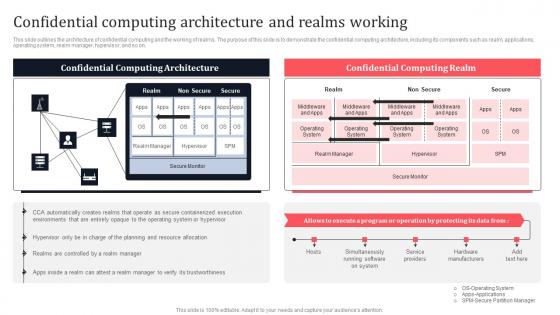
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
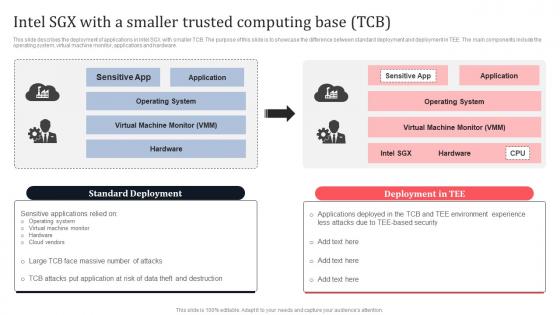
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
Icon For Information And Cyber Security Risk Management Themes PDF
Presenting icon for information and cyber security risk management themes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for information and cyber security risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
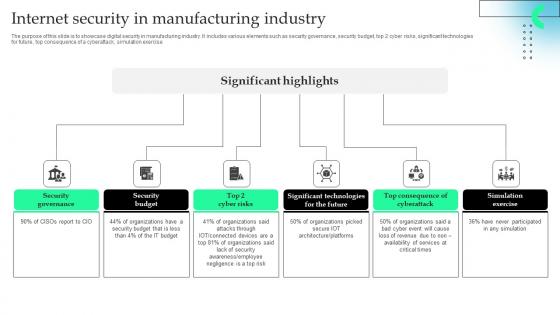
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
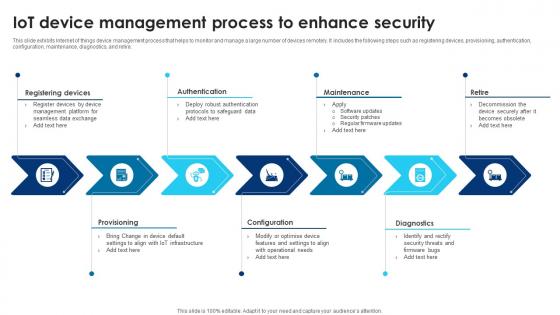
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.
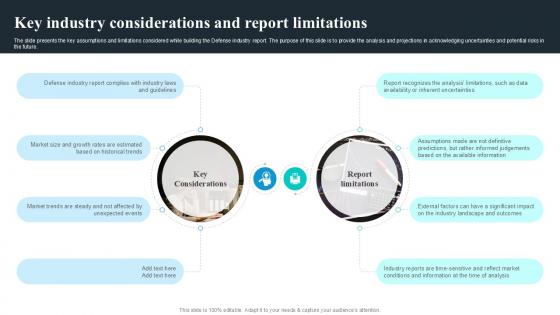
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.
Tablet With Login Username And Password Powerpoint Template
This power point template contains graphics of tablet with login page. Download this diagram slide to display internet and security concepts. Make outstanding presentation by using this creative diagram.


 Continue with Email
Continue with Email

 Home
Home


































