Data Privacy
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
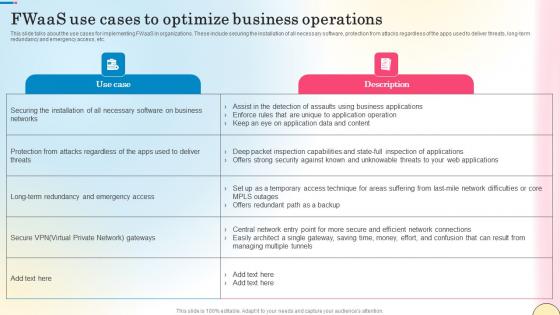
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
Use Case 2 AIOT Smart Home Applications In Home Security AIOT Applications For Various Industries IoT SS V
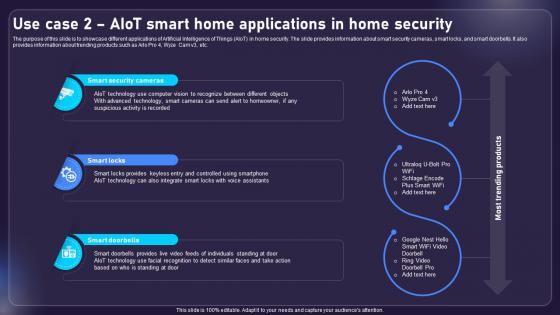
The purpose of this slide is to showcase different applications of Artificial Intelligence of Things AIoT in home security. The slide provides information about smart security cameras, smart locks, and smart doorbells. It also provides information about trending products such as Arlo Pro 4, Wyze Cam v3, etc. Slidegeeks has constructed Use Case 2 AIOT Smart Home Applications In Home Security AIOT Applications For Various Industries IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The purpose of this slide is to showcase different applications of Artificial Intelligence of Things AIoT in home security. The slide provides information about smart security cameras, smart locks, and smart doorbells. It also provides information about trending products such as Arlo Pro 4, Wyze Cam v3, etc.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
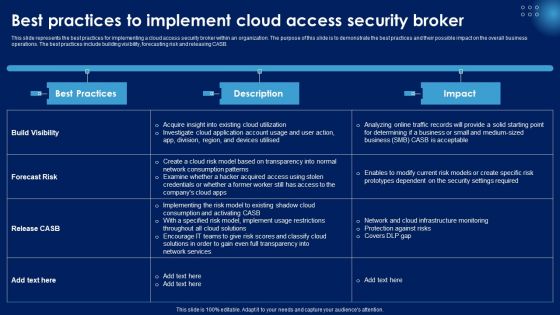
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Protection Icon Security Icon Wall Security Security Shield Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name protection icon security icon wall security security shield ppt powerpoint presentation complete deck. The topics discussed in these slides are security icon, wall security, security shield, security lock, money shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Protection Of Electronic Information PowerPoint Templates Ppt Backgrounds For Slides 0413
Discover decisive moments with our Protection Of Electronic Information PowerPoint Templates PPT Backgrounds For Slides 0413. They help make that crucial difference. Our Locked Mail Protection Of Electronic Information PowerPoint Templates PPT Backgrounds For Slides 0413 will help make your dreams come true. Your thoughts will weave the magic for you. Filter out ideas with our Protection Of Electronic Information PowerPoint Templates Ppt Backgrounds For Slides 0413. They get actionable ones to emerge.
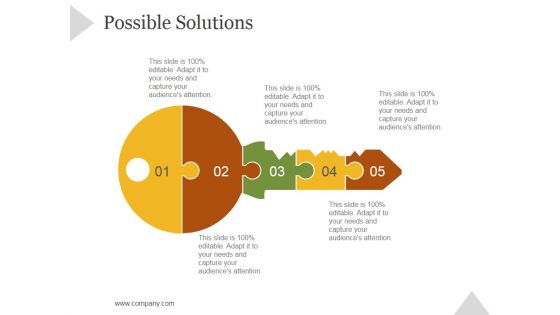
Possible Solutions Ppt PowerPoint Presentation Portfolio
This is a possible solutions ppt powerpoint presentation portfolio. This is a five stage process. The stages in this process are business, strategy, marketing, success, puzzle, key lock.
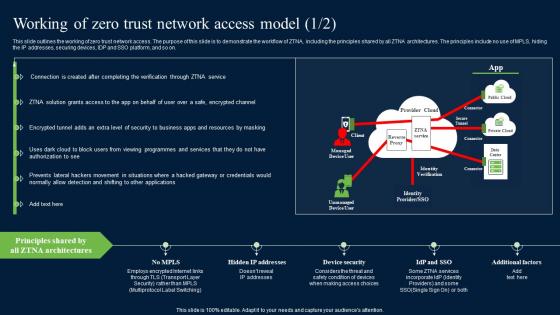
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
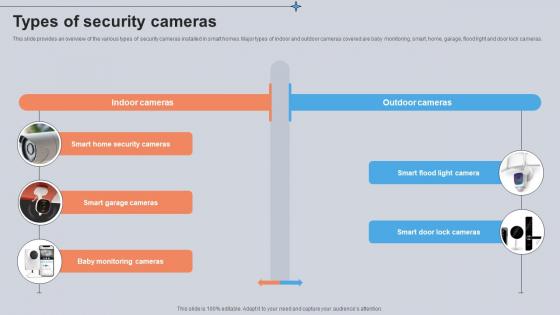
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras.
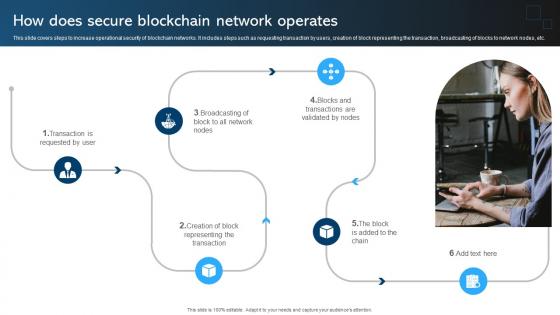
Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V
This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Create an editable Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Comprehensive Manual For How Does Secure Blockchain Network Operates BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.

Settings Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with simple of a lock placed in front of an open file folder Our Settings Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211 are held in high esteem. Many a career has been built on their strength.
Secure Digital Mail Internet PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Our Secure Digital Mail Internet PowerPoint Presentation Slides C need no exaggeration. They are an advertisement for themselves.

Secure Digital Mail Internet PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface No matter how far you have to go. Our Secure Digital Mail Internet PowerPoint Presentation Slides Cc have the drive to get you there.

Secure Digital Mail Internet PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Delight your audience with our Secure Digital Mail Internet PowerPoint Presentation Slides F. You will come out on top.

Secure Digital Mail Internet PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Our Secure Digital Mail Internet PowerPoint Presentation Slides R will be your lucky charm. They will deliver for you on your fateful day.

Secure Digital Mail Internet PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface With our Secure Digital Mail Internet PowerPoint Presentation Slides S you will get far ahead. Let your competitors play catch up.
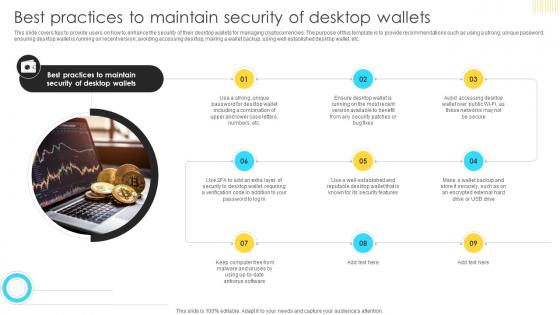
Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V
This slide covers tips to provide users on how to enhance the security of their desktop wallets for managing cryptocurrencies. The purpose of this template is to provide recommendations such as using a strong, unique password, ensuring desktop wallet is running on recent version, avoiding accessing desktop, making a wallet backup, using well established desktop wallet, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mastering Blockchain Wallets Best Practices To Maintain Security Of Desktop BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers tips to provide users on how to enhance the security of their desktop wallets for managing cryptocurrencies. The purpose of this template is to provide recommendations such as using a strong, unique password, ensuring desktop wallet is running on recent version, avoiding accessing desktop, making a wallet backup, using well established desktop wallet, etc.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name.

Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS.

Laptop Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with rendered illustration of a laptop with chains and lock around screen Challenge old thoughts with our Laptop Security PowerPoint Backgrounds And Templates 1210. You will come out on top.
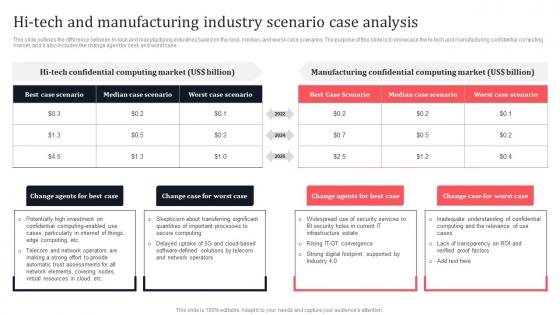
Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Presenting this PowerPoint presentation, titled Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
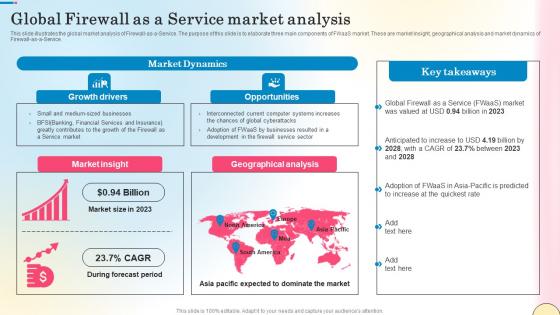
Global Firewall As A Service Market Analysis Network Security Pictures Pdf
This slide illustrates the global market analysis of Firewall-as-a-Service. The purpose of this slide is to elaborate three main components of FWaaS market. These are market insight, geographical analysis and market dynamics of Firewall-as-a-Service. This modern and well-arranged Global Firewall As A Service Market Analysis Network Security Pictures Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide illustrates the global market analysis of Firewall-as-a-Service. The purpose of this slide is to elaborate three main components of FWaaS market. These are market insight, geographical analysis and market dynamics of Firewall-as-a-Service.
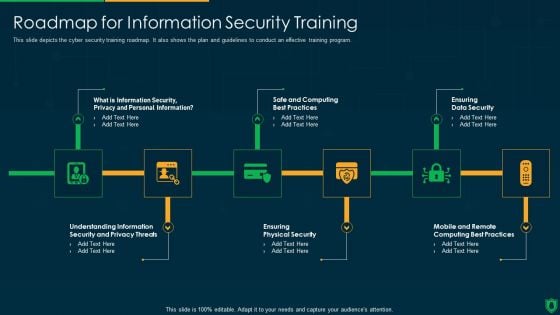
Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
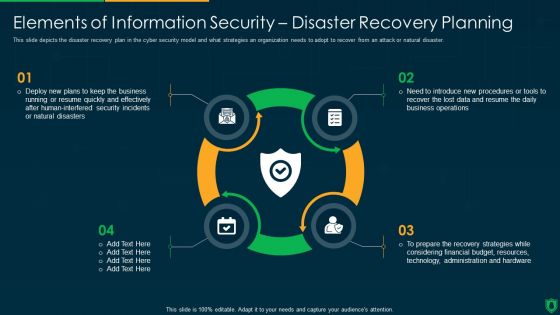
Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf from Slidegeeks and deliver a wonderful presentation. Our Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
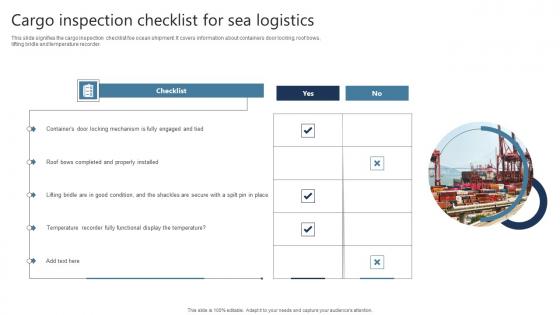
Cargo Inspection Checklist For Sea Logistics Information Pdf
This slide signifies the cargo inspection checklist foe ocean shipment. It covers information about containers door locking, roof bows, lifting bridle and temperature recorder. Showcasing this set of slides titled Cargo Inspection Checklist For Sea Logistics Information Pdf The topics addressed in these templates are Properly Installed, Temperature Recorder, Display The Temperature All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide signifies the cargo inspection checklist foe ocean shipment. It covers information about containers door locking, roof bows, lifting bridle and temperature recorder.
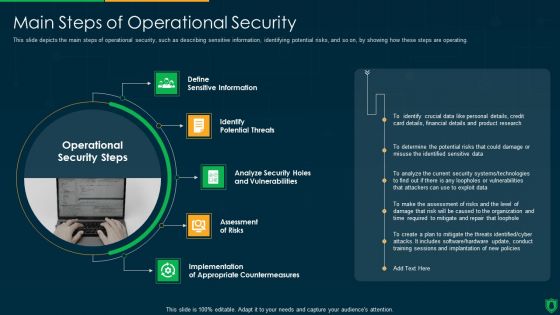
Info Security Main Steps Of Operational Security Ppt PowerPoint Presentation File Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a info security main steps of operational security ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like define sensitive information, identify potential threats, assessment risks, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
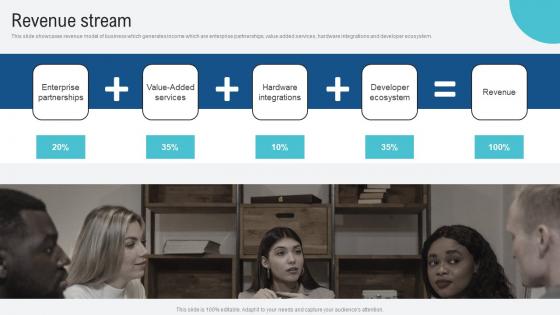
Revenue Stream Voice Assistance Security Platform Investor Funding Presentation Information Pdf
This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem. Find a pre designed and impeccable Revenue Stream Voice Assistance Security Platform Investor Funding Presentation Information Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today. This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc.
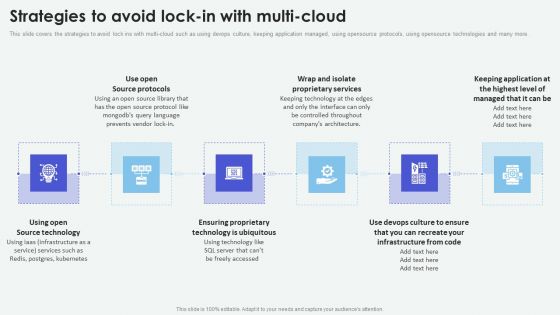
Cloud Based Computing Analysis Strategies To Avoid Lock In With Multi Cloud Slides PDF
This slide covers the strategies to avoid lock ins with multi-cloud such as using devops culture, keeping application managed, using opensource protocols, using opensource technologies and many more. Find a pre-designed and impeccable Cloud Based Computing Analysis Strategies To Avoid Lock In With Multi Cloud Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Stock Photo 3d Dollars Stack Unlocked Security Concept PowerPoint Slide
Graphic of dollar bundle is inside the lock is used in this power point image template. We have displayed concept of financial security in this image. Use this image for security or finance related topics.

Quarterly Information Technology Security Analytics Improvement Roadmap Template
Presenting our innovatively structured quarterly information technology security analytics improvement roadmap template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
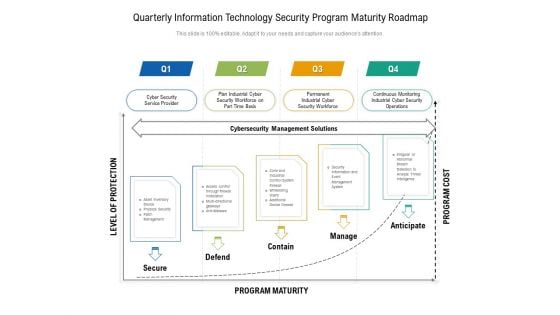
Quarterly Information Technology Security Program Maturity Roadmap Ideas
Introducing our quarterly information technology security program maturity roadmap ideas. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today. This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
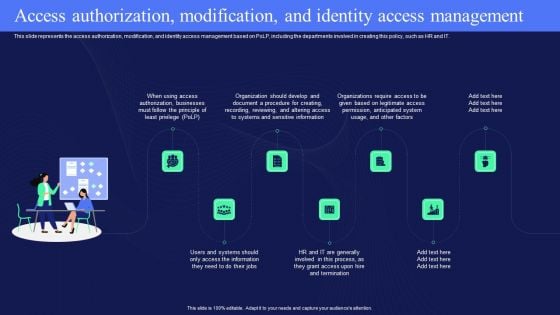
IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF
This slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative IT Policies And Procedures Access Authorization Modification And Identity Access Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
Laptop With Lock Password Authentication Vector Icon Ppt Powerpoint Presentation Icon Summary
This is a laptop with lock password authentication vector icon ppt powerpoint presentation icon summary. This is a one stage process. The stages in this process are password, access approval, authentication icon.
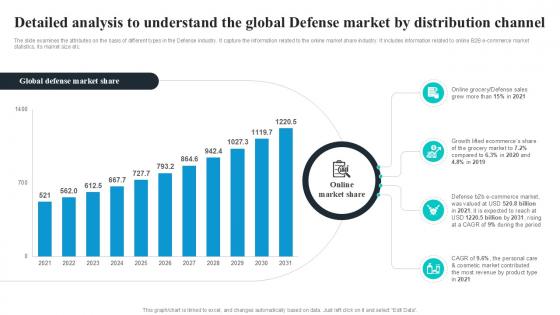
Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Detailed Analysis To Understand The Global Security Industry PPT Slide IR SS V today and make your presentation stand out from the rest The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to the online market share industry. It includes information related to online B2B e-commerce market statistics, its market size etc.
Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf
Showcasing this set of slides titled Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf. The topics addressed in these templates are Cloud Readiness, Assessment Checklist, Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Readiness Assessment Checklist Icon Ppt Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.
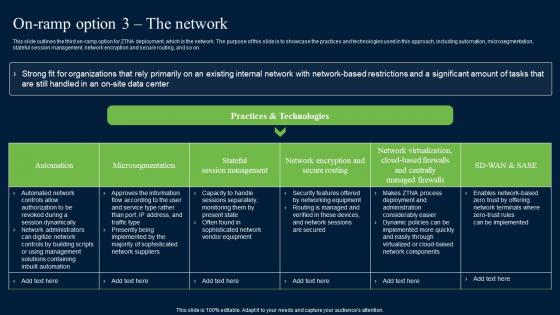
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
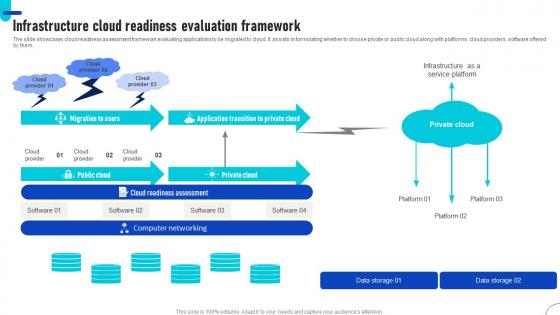
Infrastructure Cloud Readiness Evaluation Framework Ppt File Skills Pdf
The slide showcases cloud readiness assessment framework evaluating applications to be migrated to cloud. It assists in formulating whether to choose private or public cloud along with platforms, cloud providers, software offered by them. Showcasing this set of slides titled Infrastructure Cloud Readiness Evaluation Framework Ppt File Skills Pdf. The topics addressed in these templates are Cloud Provider, Public Cloud, Private Cloud. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases cloud readiness assessment framework evaluating applications to be migrated to cloud. It assists in formulating whether to choose private or public cloud along with platforms, cloud providers, software offered by them.
Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf
Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf. This layout presents information on Cloud Based Robotic, Process Automation Architecture. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Based Robotic Process Automation Architecture Icon For Business Automation Process Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf
Pitch your topic with ease and precision using this Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf. This layout presents information on Cloud Computing Service, Level Agreement Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Computing Service Level Agreement Model Management And Monitoring Framework Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf
Pitch your topic with ease and precision using this Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf. This layout presents information on Showcasing Cloud Computing, Service Level Agreement, Model Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Icon Showcasing Cloud Computing Service Level Agreement Model Management Framework Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf
Pitch your topic with ease and precision using this Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf. This layout presents information on Cloud Migration, Readiness Assessment, Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cloud Migration Readiness Assessment Icon Ppt Layouts Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf
Pitch your topic with ease and precision using this Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf. This layout presents information on Enterprise Cloud, Readiness Assessment, Management Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Enterprise Cloud Readiness Assessment And Management Icon Ppt Professional Example Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf
Slidegeeks is here to make your presentations a breeze with Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Web Access Control Solution Integration Of Swg Inside Sase Architecture
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. The Web Access Control Solution Integration Of Swg Inside Sase Architecture is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
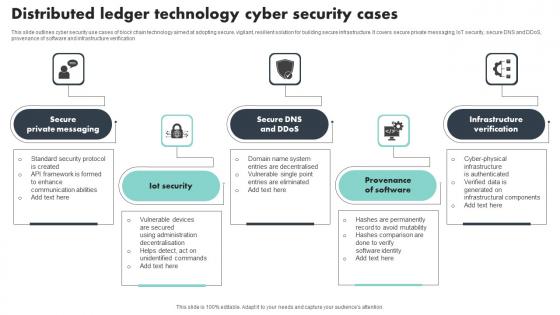
Distributed Ledger Technology Cyber Security Cases Brochure Pdf
This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification Showcasing this set of slides titled Distributed Ledger Technology Cyber Security Cases Brochure Pdf The topics addressed in these templates are Private Messaging, Provenance Of Software, Infrastructure Verification All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification
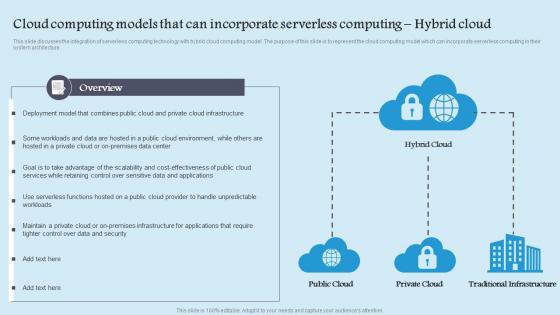
Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf
This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture. This Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Models That Can Incorporate Serverless Computing Hybrid Cloud Background Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the integration of serverless computing technology with hybrid cloud computing model. The purpose of this slide is to represent the cloud computing model which can incorporate serverless computing in their system architecture.
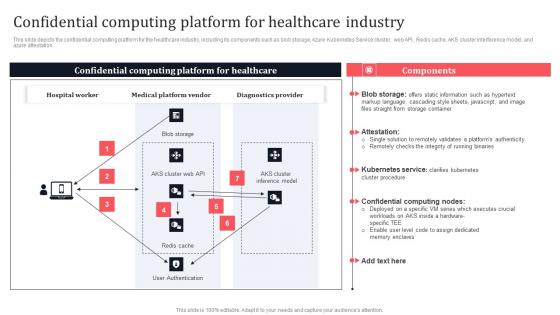
Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. This modern and well-arranged Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
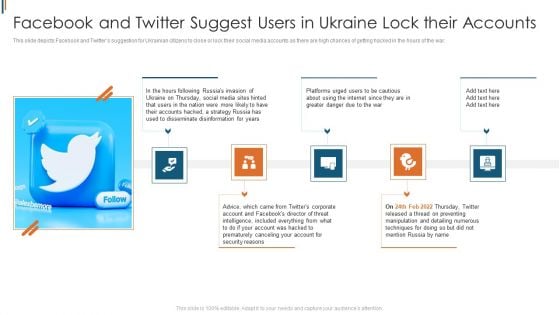
Ukraine Cyberwarfare Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Information Pdf
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Presenting ukraine cyberwarfare facebook and twitter suggest users in ukraine lock their accounts information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like platforms urged users to be cautious about using the internet since they are in greater danger due to the war, in the hours following russias invasion of ukraine on thursday, social media sites hinted that users in the nation were more likely to have their accounts hacked. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.


 Continue with Email
Continue with Email

 Home
Home


































