Data Privacy
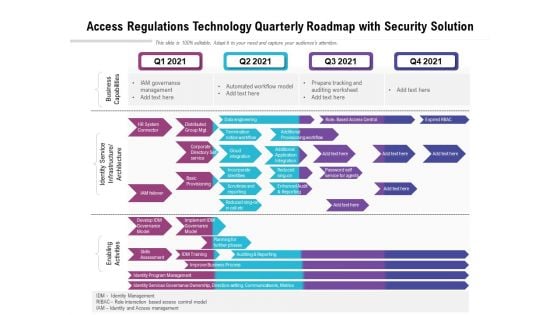
Access Regulations Technology Quarterly Roadmap With Security Solution Graphics
We present our access regulations technology quarterly roadmap with security solution graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched access regulations technology quarterly roadmap with security solution graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
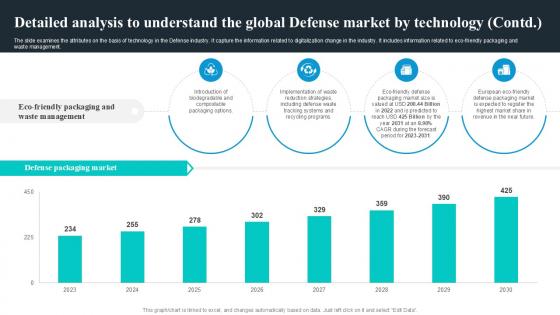
Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management. Present like a pro with Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Welcome to our selection of the Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
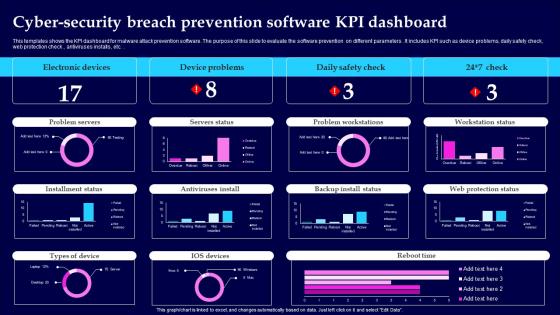
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.

Protection Technology Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Protection Technology Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Technology Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Technology Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Protocol Security PPT Example
Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer. This Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer.

Stock Photo Globe And Chain For Safety Image Graphics For PowerPoint Slide
This image slide has been designed with graphic of blue colored globe locked with chains. This image displays the concept of earth safety and protection. Create eye-catching presentations using this image.
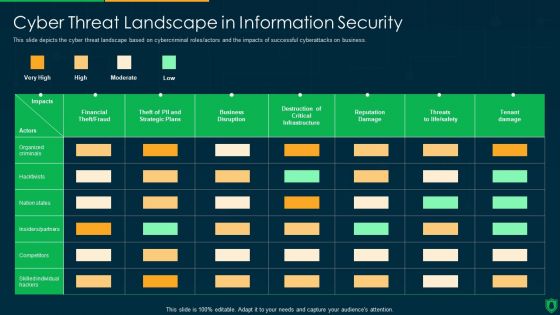
Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
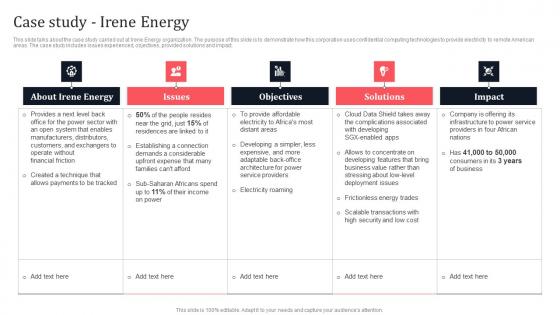
Case Study Irene Energy Secure Multi Party Sample Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Create an editable Case Study Irene Energy Secure Multi Party Sample Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Case Study Irene Energy Secure Multi Party Sample Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
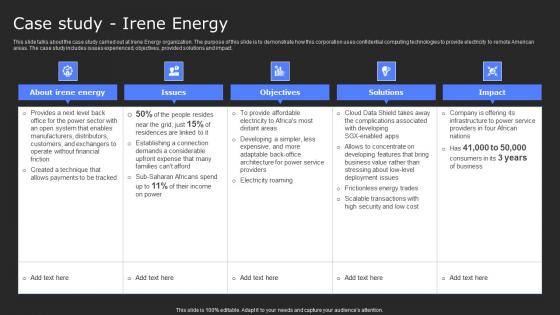
Case Study Irene Energy Secure Computing Framework Ideas Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Secure Computing Framework Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Secure Computing Framework Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
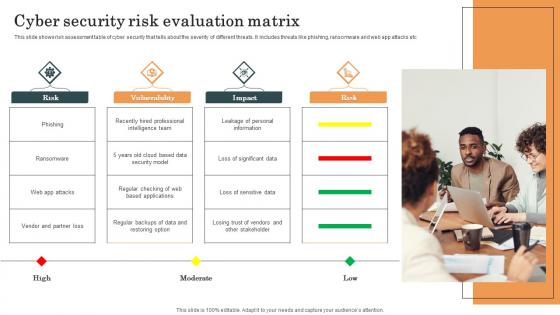
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.

Effective Security Strategic Agenda For Hotels Introduction Pdf
This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel. Showcasing this set of slides titled Effective Security Strategic Agenda For Hotels Introduction Pdf. The topics addressed in these templates are Security, Action Taken, Responsible Authority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel.
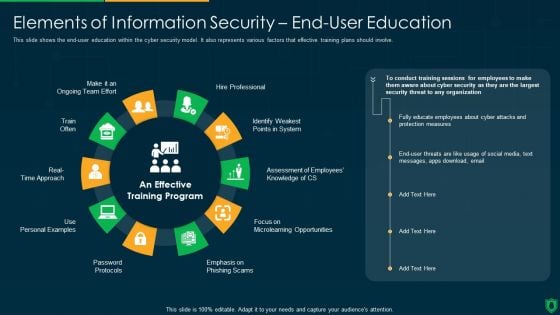
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
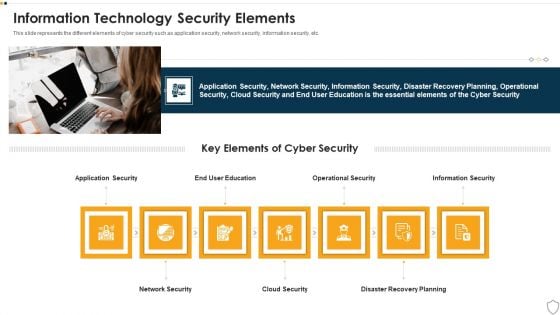
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.

Network Security Model PPT Example

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.

Info Security How Is Automation Used In Information security Ppt PowerPoint Presentation Gallery Samples PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting info security how is automation used in information security ppt powerpoint presentation gallery samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
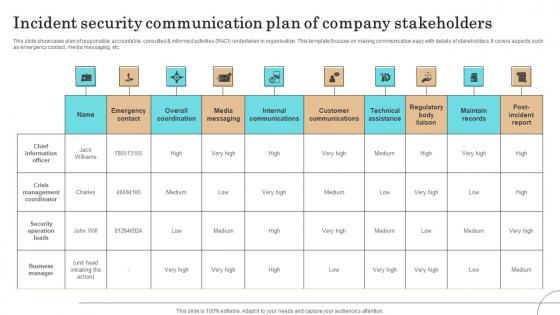
Incident Security Communication Plan Of Company Stakeholders Pictures Pdf
This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.Showcasing this set of slides titled Incident Security Communication Plan Of Company Stakeholders Pictures Pdf The topics addressed in these templates are Crisis Management Coordinator, Security Operation Leads, Business Manager All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases plan of responsible, accountable, consulted informed activities RACI undertaken in organisation. This template focuses on making communication easy with details of stakeholders. It covers aspects such as emergency contact, media messaging, etc.

Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.
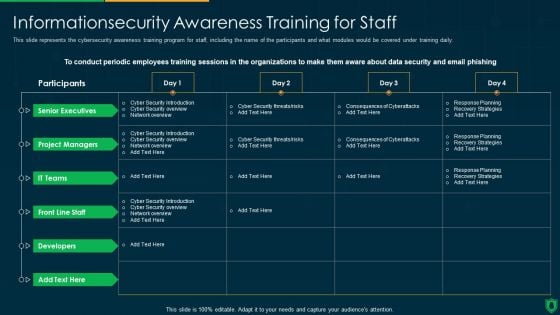
Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
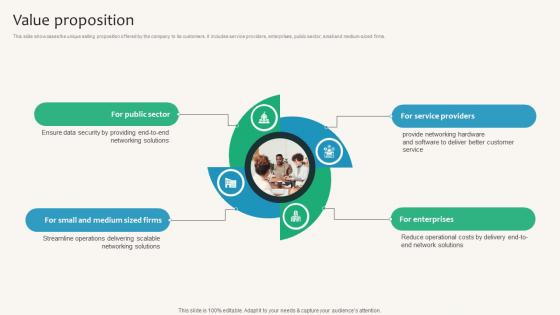
Value Proposition Security Service Provider Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition Security Service Provider Business Model BMC SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the unique selling proposition offered by the company to its customers. It includes service providers, enterprises, public sector, small and medium-sized firms.

Info Security Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Secure Web Gateways Market In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Web Gateways Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Web Gateways Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Web Gateways Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IT Security Roadmap In Powerpoint And Google Slides Cpb
Introducing our well designed IT Security Roadmap In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like IT Security Roadmap. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our IT Security Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Personal Security Apps Android In Powerpoint And Google Slides Cpb
Introducing our well designed Personal Security Apps Android In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Personal Security Apps Android. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Personal Security Apps Android In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Application Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Application Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Application Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Application Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Sdlc Policy Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icon Global Security In Powerpoint And Google Slides Cpb
Introducing our well designed Icon Global Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Icon Global Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Icon Global Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unblocked Online Security Extension In Powerpoint And Google Slides Cpb
Introducing our well-designed Unblocked Online Security Extension In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Unblocked Online Security Extension. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Unblocked Online Security Extension In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Android Security Malware Detection In Powerpoint And Google Slides Cpb
Introducing our well-designed Android Security Malware Detection In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Android Security Malware Detection. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Android Security Malware Detection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Protection Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Communication Encrypted In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Communication Encrypted In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Communication Encrypted. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Communication Encrypted In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Mobile Android Devices Security In Powerpoint And Google Slides Cpb
Introducing our well designed Mobile Android Devices Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Mobile Android Devices Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Mobile Android Devices Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

E Commerce Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed E Commerce Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like E Commerce Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our E Commerce Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Camera System Business In Powerpoint And Google Slides Cpb
Introducing our well-designed Security Camera System Business In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Camera System Business. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Camera System Business In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
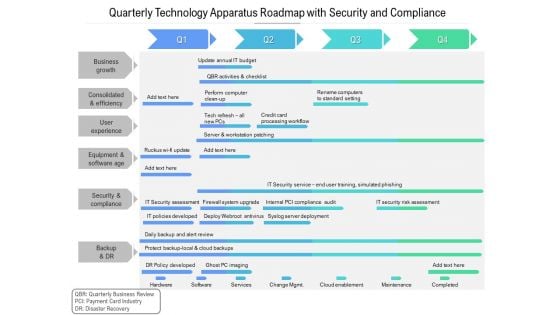
Quarterly Technology Apparatus Roadmap With Security And Compliance Rules
Presenting the quarterly technology apparatus roadmap with security and compliance rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
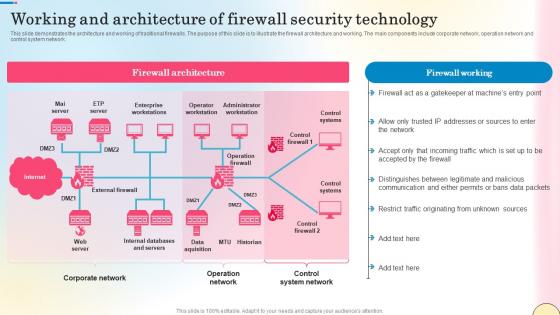
Working And Architecture Of Firewall Security Technology Network Security Summary Pdf
This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Working And Architecture Of Firewall Security Technology Network Security Summary Pdf can be your best option for delivering a presentation. Represent everything in detail using Working And Architecture Of Firewall Security Technology Network Security Summary Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network.

Database Access Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Change Metrics Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of seventeen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf
The following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc.

Iot Smart Home Security Management Technology Demonstration PDF
This slide provides the use of smart security technology to get real time monitoring of home and obtain authenticity. Key features mentioned are smart cameras, biometric locks, smart cameras, connected switches and fire sensor. Persuade your audience using this Iot Smart Home Security Management Technology Demonstration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Smart Cameras, Biometric Locks, Smart Cameras, Connected Switches, Fire Sensor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
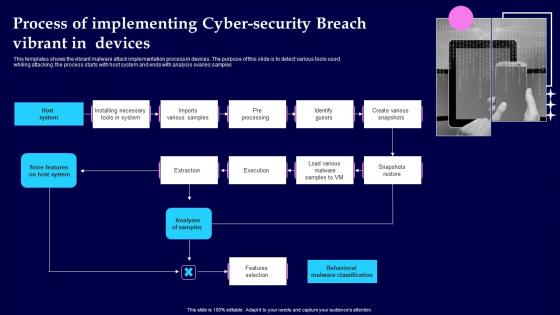
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples
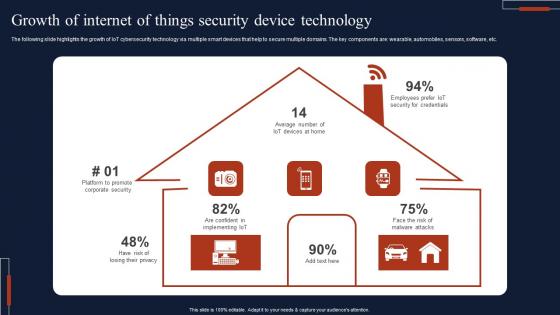
Growth Of Internet Of Things Security Device Technology Professional Pdf
The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc. Pitch your topic with ease and precision using this Growth Of Internet Of Things Security Device Technology Professional Pdf This layout presents information on Growth Of Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc.

5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this 5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set. Our 5G Network Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Mobile Application Security Testing PPT Sample

Cloud Native Application Security PPT Template

Implementing Authentication In Application Security PPT Example

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.
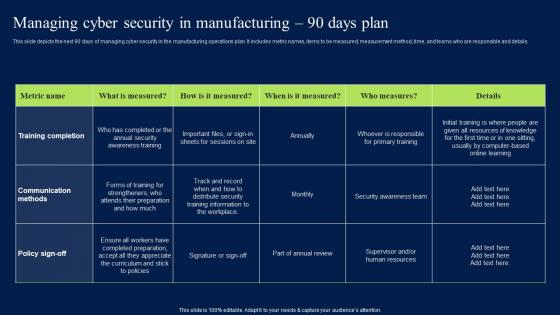
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
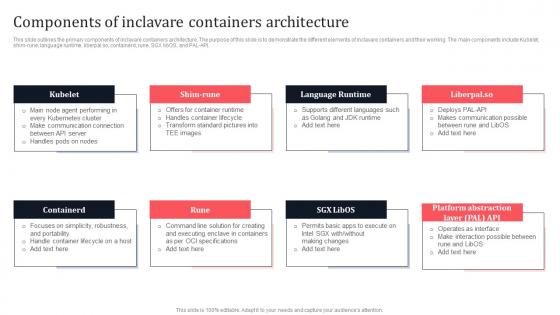
Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
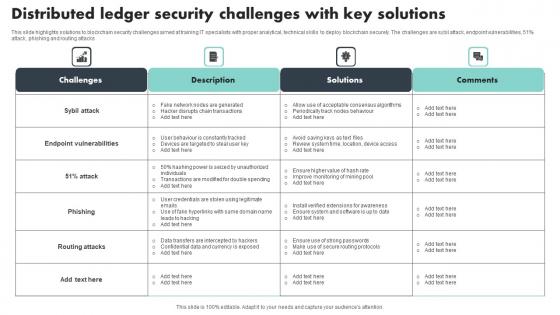
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.
Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf
This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.Pitch your topic with ease and precision using this Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf This layout presents information on Program Participation, Security Breaches, Phishing Rate It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.


 Continue with Email
Continue with Email

 Home
Home


































