Data Privacy
Network Security Vulnerabilities Analysis Approach Sample Pdf
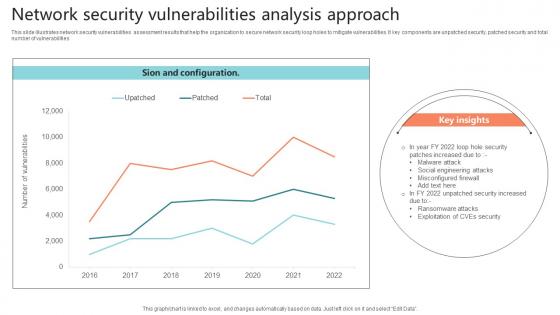
This slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities.Showcasing this set of slides titled Network Security Vulnerabilities Analysis Approach Sample Pdf The topics addressed in these templates are Misconfigured Firewall, Malware Attack, Social Engineering Attacks All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities
Business Diagram Pie Chart In Shape Of Lock For Trading Costs Presentation Template
This slide has been designed with pie chart in shape of lock. This diagram contains the concept of trading costs, finance and marketing. Use this slide for your business related presentations.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
Budget Security Robot Technology In Powerpoint And Google Slides Cpb
Introducing our well-designed Budget Security Robot Technology In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Budget Security Robot Technology. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Budget Security Robot Technology In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf
Showcasing this set of slides titled Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf The topics addressed in these templates are Blockchain Internet, Things Security, Technology For Business All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Of Things Security Technology Image For Mobile Application Download Pdf
Showcasing this set of slides titled Internet Of Things Security Technology Image For Mobile Application Download Pdf The topics addressed in these templates are Internet Of Things, Security Technology, Image For Mobile Application All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Technology Image For Mobile Application Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Smart Phone With Finger Lock Vector Illustration Ppt PowerPoint Presentation Professional Brochure PDF
Persuade your audience using this smart phone with finger lock vector illustration ppt powerpoint presentation professional brochure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone with finger lock vector illustration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
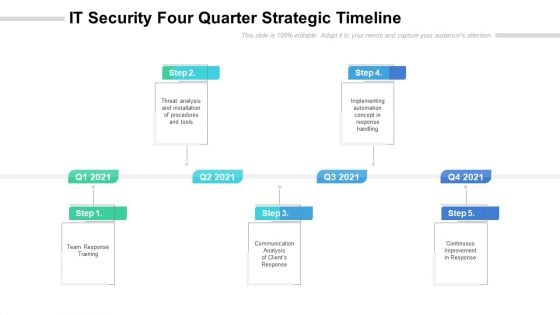
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
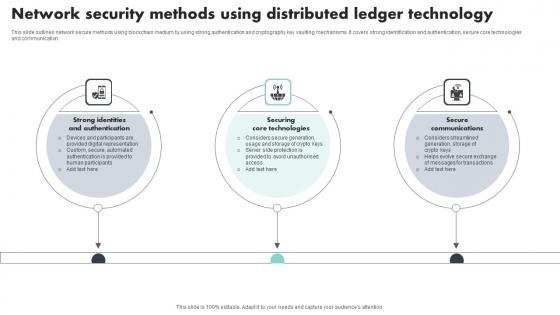
Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication
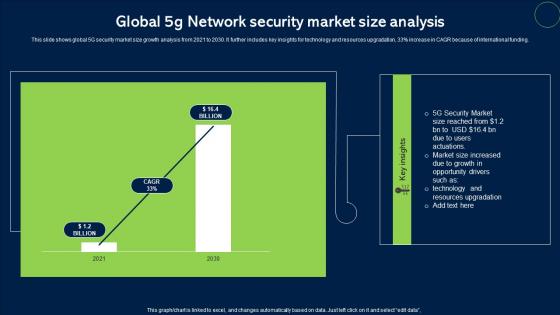
Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding.
Image For Multiple Internet Of Things Security Device Technology Slides Pdf
Pitch your topic with ease and precision using this Image For Multiple Internet Of Things Security Device Technology Slides Pdf This layout presents information on Multiple Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Image For Multiple Internet Of Things Security Device Technology Slides Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
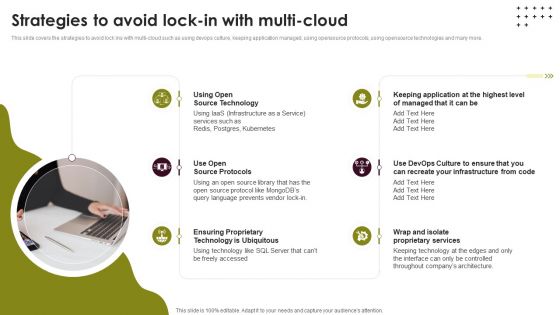
Cloud Computing Scalability Strategies To Avoid Lock In With Multi Cloud Pictures PDF
This slide covers the strategies to avoid lock ins with multi-cloud such as using devops culture, keeping application managed, using opensource protocols, using opensource technologies and many more. Find a pre-designed and impeccable Cloud Computing Scalability Strategies To Avoid Lock In With Multi Cloud Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
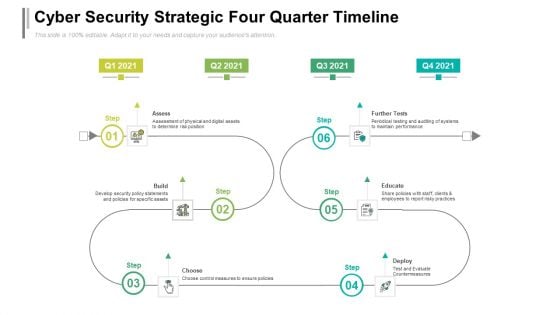
Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Hotel Card Door Lock Access Control Vector Icon Ppt PowerPoint Presentation File Icon PDF
Presenting hotel card door lock access control vector icon ppt powerpoint presentation file icon pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hotel card door lock access control vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Always Lock Your Important Documents PowerPoint Templates Ppt Backgrounds For Slides 0513
Document the process on our Always Lock Your Important Documents PowerPoint Templates PPT Backgrounds For Slides. Make a record of every detail. Satiate desires with our Technology PowerPoint Templates. Give them all they want and more. Be the doer with our Business PowerPoint Templates. Put your thoughts into practice. Enthuse your audience with your ideas. Our Always Lock Your Important Documents PowerPoint Templates Ppt Backgrounds For Slides 0513 will generate keenness.
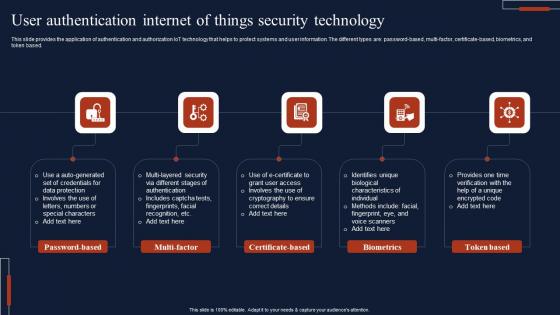
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based.
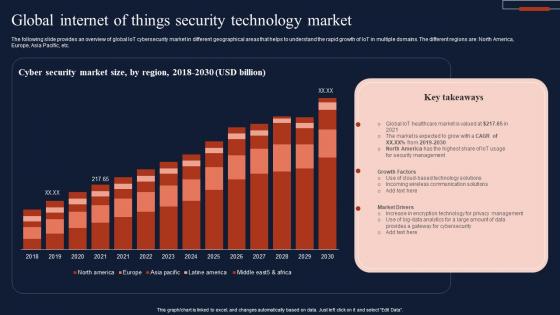
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
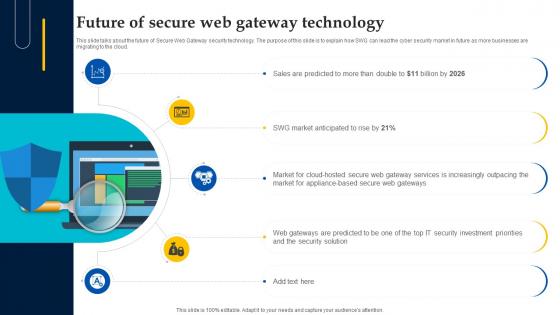
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V
The slide highlights the PESTEL analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external factors on defense market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects. Explore a selection of the finest PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide highlights the PESTEL analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external factors on defense market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects.

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same.
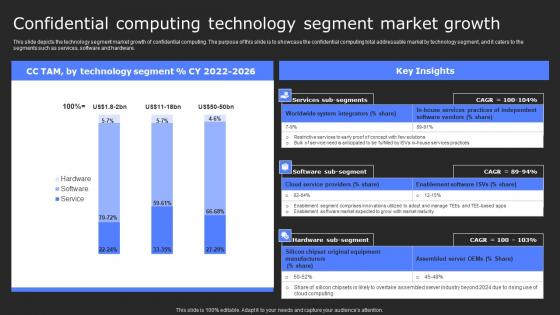
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
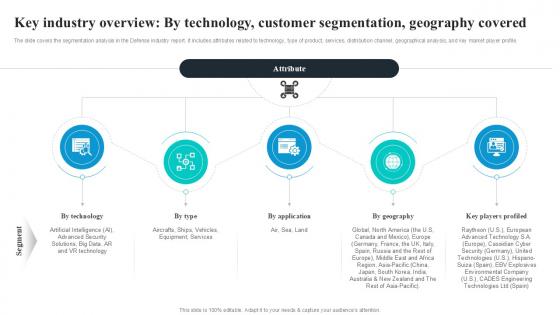
Key Industry Overview By Technology Global Security Industry PPT Template IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Key Industry Overview By Technology Global Security Industry PPT Template IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Key Industry Overview By Technology Global Security Industry PPT Template IR SS V The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.
Business Architecture Diagrams Component Ppt PowerPoint Templates Backgrounds For Slides
We present our business architecture diagrams component ppt PowerPoint templates backgrounds for slides.Download our Architecture PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Present our Layers PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Download and present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds.Use these PowerPoint slides for presentations relating to content, data, icon, information, schema, import, model, base, organization, business, diagram, chart, select, entry, column, symbol, relational, management, connection, collection, dataflow, architecture, maintenance, edition, access, background, database, modification, storage. The prominent colors used in the PowerPoint template are Purple, Gray, White. The adaptability of our Business Architecture Diagrams Component Ppt PowerPoint Templates Backgrounds For Slides is a fact. They will align with your bidding.
Virtual Private Network Tunnel Icon With Globe And Lock Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting virtual private network tunnel icon with globe and lock ppt powerpoint presentation gallery ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virtual private network tunnel icon with globe and lock. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc.

Artificial Intelligence Key Statistics Ppt PowerPoint Presentation Professional Example Introduction
Presenting this set of slides with name artificial intelligence key statistics ppt powerpoint presentation professional example introduction. This is a three stage process. The stages in this process are security, skills, management, marketing, planning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Bright Bulb Lock With Key Vector Icon Ppt PowerPoint Presentation Infographic Template Brochure PDF
Presenting this set of slides with name bright bulb lock with key vector icon ppt powerpoint presentation infographic template brochure pdf. This is a three stage process. The stages in this process are bright bulb lock with key vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparison Between Secure Web Gateway And Firewalls Web Access Control Solution
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
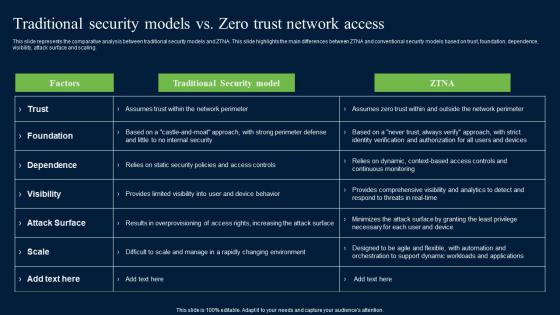
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
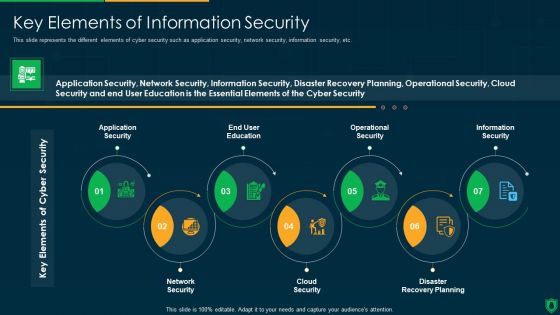
Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protection Of Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Protection Of Information Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team.Use these PowerPoint slides for presentations relating to Laptop with lock and key. Computer security, computer, technology, security, business, services. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Enthral your listeners with your suggestions. Keep them clued in with our Protection Of Information Technology PowerPoint Templates Ppt Backgrounds For Slides 0213.
Rescue Icon Statistics Finance PowerPoint Templates And PowerPoint Themes 1012
Deliver amazing Presentations with our above template containing an image of lifesaver and pie chart. This image represents the concept of statistics. It is a useful captivating tool concieved to enable you to define your message in your Business and Financial PPT presentations. Deliver amazing presentations to mesmerize your audience. Bid farewell to all your doubts. Attain assuredness with our Rescue Icon Statistics Finance PowerPoint Templates And PowerPoint Themes 1012.

Zero Trust Model Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Traditional Security Models Vs Zero Trust Network Access and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.
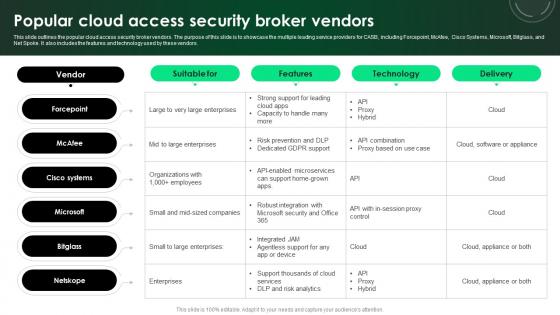
CASB 2 0 IT Popular Cloud Access Security Broker Vendors
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors.

Business Diagram Colored Keys Around The Lock Hole For Process Flow Representation Presentation Temp
This business diagram slide has been designed with graphic of five keys around lock. This PowerPoint template helps to display safety options in your presentations. Use this to make impressive presentations.
Open Access Key Lock Icon Ppt PowerPoint Presentation Portfolio Designs Download
This is a open access key lock icon ppt powerpoint presentation portfolio designs download. This is a three stage process. The stages in this process are computer software, operating system, open source.
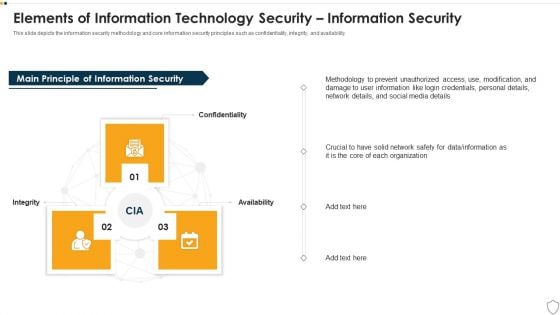
IT Security Elements Of Information Technology Security Information Security Ppt Gallery Grid PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a it security elements of information technology security information security ppt gallery grid pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity, confidentiality, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Locked Email Symbol Computer Internet PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Locked Email Symbol Computer Internet PowerPoint Templates PPT Backgrounds For Slides 0413.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Download our Technology PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download and present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use these PowerPoint slides for presentations relating to Protected email symbol, computer, technology, business, success, future. The prominent colors used in the PowerPoint template are Blue, Black, Gray. Give a colorful facing to your thoughts with our Locked Email Symbol Computer Internet PowerPoint Templates Ppt Backgrounds For Slides 0413. Make it more alluring for your listeners.
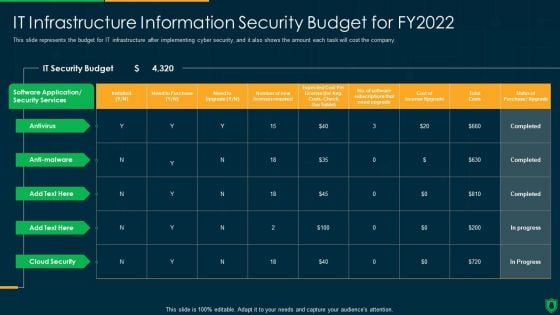
Info Security IT Infrastructure Information Security Budget For FY2022 Ppt PowerPoint Presentation File Pictures PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative info security it infrastructure information security budget for fy2022 ppt powerpoint presentation file pictures pdf bundle. Topics like it security budget, security services, cost license upgrade can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
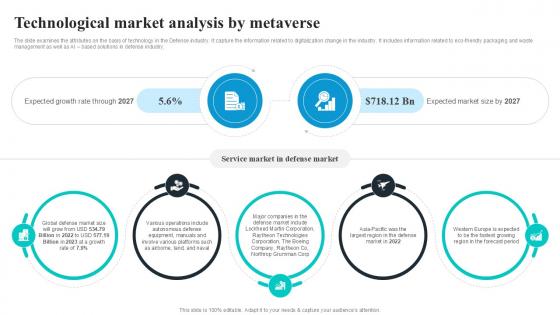
Technological Market Analysis Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management as well as AI based solutions in defense industry. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Technological Market Analysis Global Security Industry PPT PowerPoint IR SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Technological Market Analysis Global Security Industry PPT PowerPoint IR SS V. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management as well as AI based solutions in defense industry.
Computer Keyboard With Word Lock PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Computer Keyboard With Word Lock PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because You can safely bank on our PowerPoint Templates and Slides. They will provide a growth factor to your valuable thoughts. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Present our Services PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Future PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to Deal with matters in an equitable way. Reach a settlement with the help of our Computer Keyboard With Word Lock PowerPoint Templates Ppt Backgrounds For Slides 0113.

Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc.

Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample
This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Find a pre-designed and impeccable Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc.
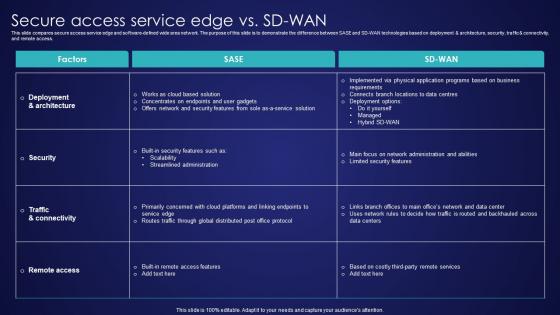
Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Take your projects to the next level with our ultimate collection of Secure Access Service Edge Vs SD Wan Wide Area Network Services Structure Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access.
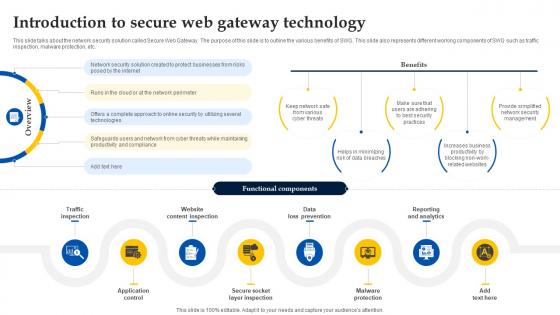
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
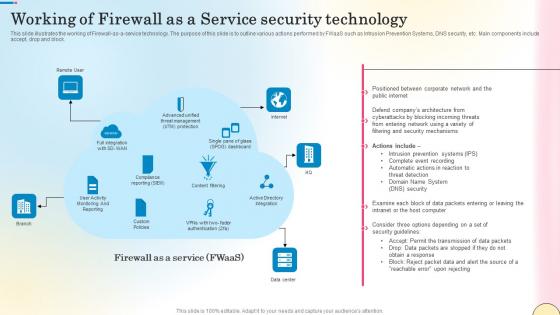
Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf
This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Find highly impressive Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
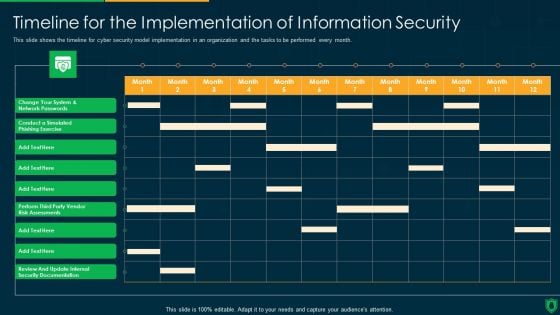
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Development Team Case Study 2 Internet Security Organization SA SS V
This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Development Team Case Study 2 Internet Security Organization SA SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue.
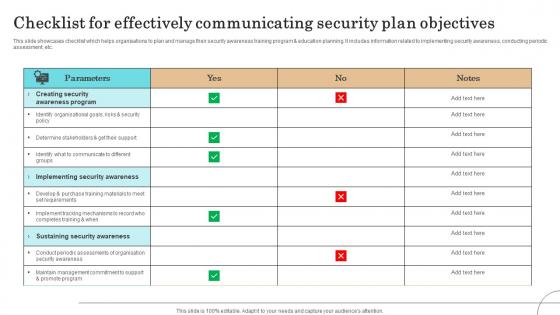
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.

Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates
We present our systematic concentric process diagram business plan outline PowerPoint templates.Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Shapes PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download and present our Business PowerPoint Templates because It can Bubble and burst with your ideas. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity.Use these PowerPoint slides for presentations relating to Login, cyber, radar, protocol, elimination, secure, corporate, future, concept, lan, infrastructure, data, process, scan, viral, technology, security, wan, abstract,creative, illustration, system, up, focus, terrorism, futuristic, recognition, precaution, check, processing, zoom, information, background, virus, conceptual,precautionary, pattern, systematic, measure. The prominent colors used in the PowerPoint template are Blue, Blue light, White. Force out your enemies with our Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates. Just download, type and present.
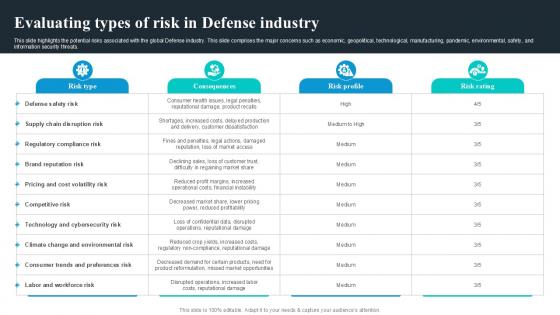
Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V
This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V can be your best option for delivering a presentation. Represent everything in detail using Evaluating Types Of Risk In Defense Industry Global Security Industry PPT Example IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the potential risks associated with the global Defense industry. This slide comprises the major concerns such as economic, geopolitical, technological, manufacturing, pandemic, environmental, safety, and information security threats.
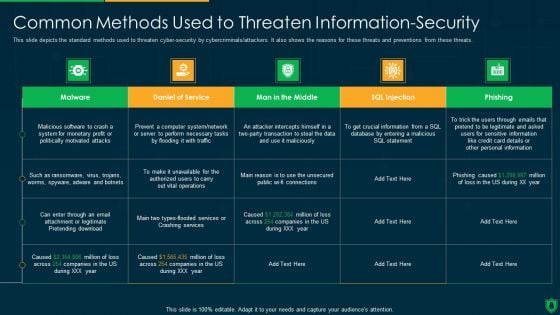
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
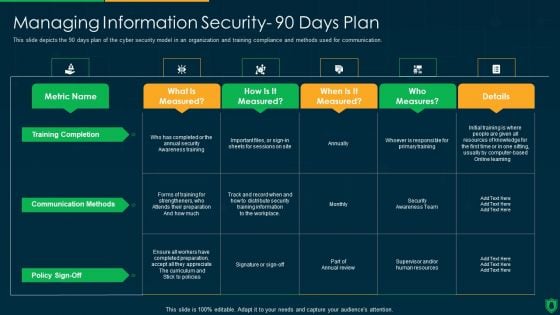
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































