Safety Summary

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
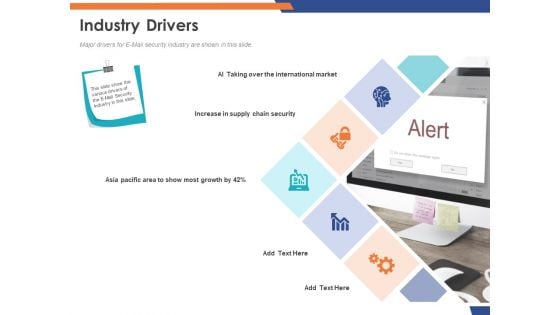
Email Security Market Research Report Industry Drivers Ppt Outline Maker PDF
Presenting this set of slides with name email security market research report industry drivers ppt outline maker pdf. This is a five stage process. The stages in this process are increase in supply chain security, asia pacific area to show most growth, ai taking over the international market. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
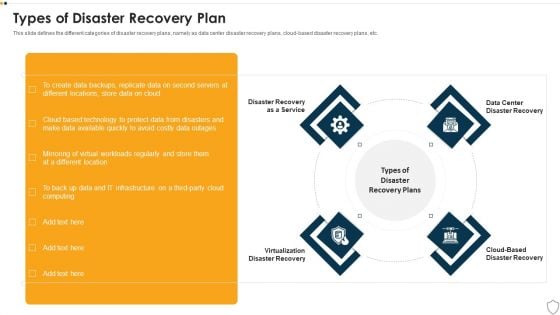
IT Security Types Of Disaster Recovery Plan Ppt Outline Show PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a it security types of disaster recovery plan ppt outline show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery as a service, virtualization disaster recovery, cloud based disaster recovery, data center disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Explore a selection of the finest Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc.
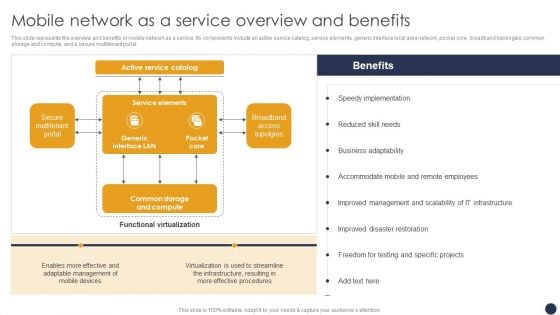
Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. Explore a selection of the finest Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Naas Service Model Mobile Network As A Service Overview And Benefits Ppt Model Examples PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Components To Enhance Processes Ppt PowerPoint Presentation Complete With Slides
This content ready template on Cyber Security Components To Enhance Processes Ppt PowerPoint Presentation Complete With Slides has all the details you need to mention in a presentation. The template also emphasizes critical business service details and charges as a separate package. You can customize each slide of this forteen part complete deck into creative bundles and turn your business visitors into customers. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download with a click below and gain instant access to this handy preset.

Application Security Performance Monitoring Application Security Testing
This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Want to ace your presentation in front of a live audience Our Application Security Performance Monitoring Application Security Testing can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the performance tracking dashboard for application security to analyze and monitor security of application.
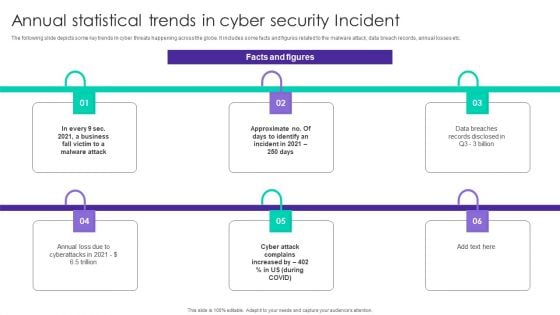
Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
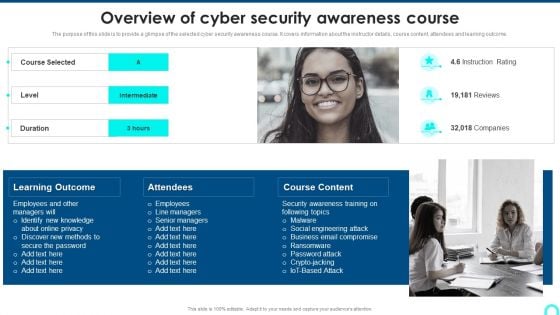
Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
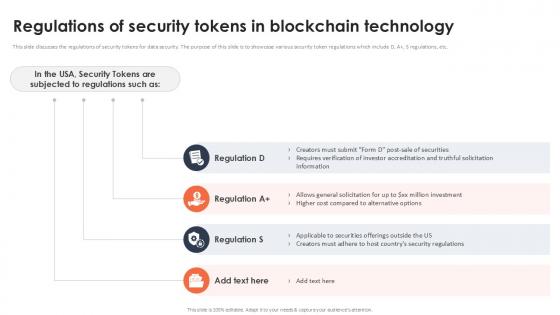
Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc.

National Security America PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Americana PowerPoint Templates because you have the plans ready for them to absorb and understand. Use our Security PowerPoint Templates because you can gain the success to desired levels in one go. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Business PowerPoint Templates because you have churned your mind and come upwith solutions. Present our Stars PowerPoint Templates because the Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant.Use these PowerPoint slides for presentations relating to National security america, business, security, success, americana, stars. The prominent colors used in the PowerPoint template are Red, White, Blue navy. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. Presenters tell us our security PowerPoint templates and PPT Slides are Exuberant. Use our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will get their audience's attention. PowerPoint presentation experts tell us our america PowerPoint templates and PPT Slides are Ultra. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will save the presenter time. Presenters tell us our stars PowerPoint templates and PPT Slides are Perfect. Our National Security America PowerPoint Templates Ppt Backgrounds For Slides 1212 exist in abundance. They believe in giving you ample oppurtunities.

Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation
This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation today and make your presentation stand out from the rest This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes.

Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Boost your pitch with our creative Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
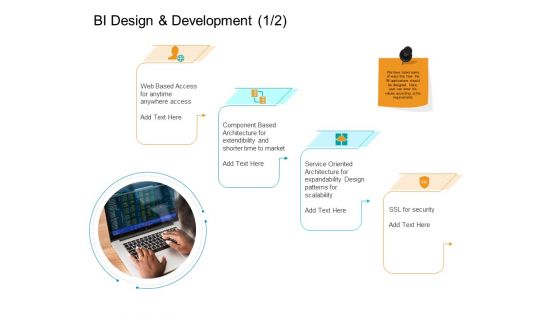
Facts Assessment BI Design And Development Security Ppt PowerPoint Presentation Slides Master Slide PDF
Presenting this set of slides with name facts assessment bi design and development security ppt powerpoint presentation slides master slide pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Personalize Rewards Ppt PowerPoint Presentation Icon Slideshow
This is a personalize rewards ppt powerpoint presentation icon slideshow. This is a six stage process. The stages in this process are promotion, recognition, pay, job security, sense of accomplishment.

Main Data Security Tokenization Techniques Securing Your Data Ppt Sample
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. The Main Data Security Tokenization Techniques Securing Your Data Ppt Sample is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.
Cloud Data Security Vector Icon Ppt PowerPoint Presentation Diagram Templates PDF
Presenting cloud data security vector icon ppt powerpoint presentation diagram templates pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including cloud data security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Construction Worker Security Checklist Icon Portrait Pdf
Pitch your topic with ease and precision using this Construction Worker Security Checklist Icon Portrait Pdf. This layout presents information on Construction Worker, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Construction Worker Security Checklist Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Food Quality Security Checklist Icon Guidelines Pdf
Pitch your topic with ease and precision using this Food Quality Security Checklist Icon Guidelines Pdf. This layout presents information on Food Quality, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Food Quality Security Checklist Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Security Compliance System Icon Clipart Pdf
Pitch your topic with ease and precision using this Data Security Compliance System Icon Clipart Pdf. This layout presents information on Data Security, Compliance System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Compliance System Icon Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
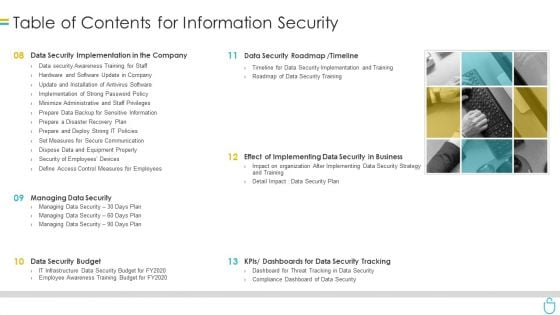
Table Of Contents For Information Security Ppt Styles Outline PDF
Presenting table of contents for information security ppt styles outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security implementation, data security roadmap, data security budget, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Lock Icon On Notepad Ppt PowerPoint Presentation Infographic Template Format
Presenting this set of slides with name lock icon on notepad ppt powerpoint presentation infographic template format. This is a three stage process. The stages in this process are lock icon on notepad. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
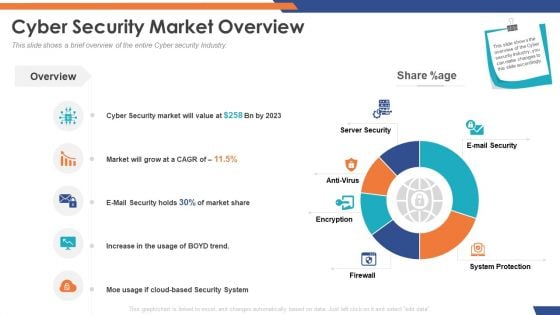
Email Security Market Research Report Cyber Security Market Overview Inspiration PDF
Presenting this set of slides with name email security market research report cyber security market overview inspiration pdf. The topics discussed in these slides are server security, e mail security, system protection, antivirus, firewall, encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
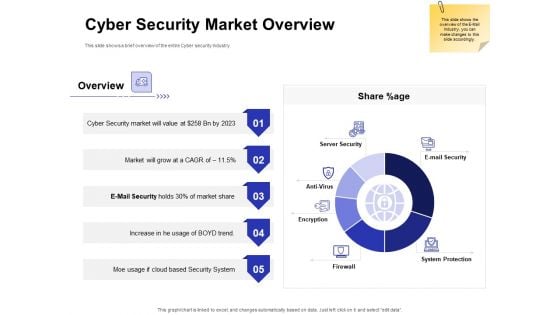
Global Cloud Based Email Security Market Cyber Security Market Overview Designs PDF
Presenting this set of slides with name global cloud based email security market cyber security market overview designs pdf. The topics discussed in these slides are server security, e mail security, system protection, antivirus, firewall, encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V
The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.
Real Estate Template 1 Ppt PowerPoint Presentation Background Images
This is a real estate template 1 ppt powerpoint presentation background images. This is a one stage process. The stages in this process are real estate, planning, management, marketing, strategy.
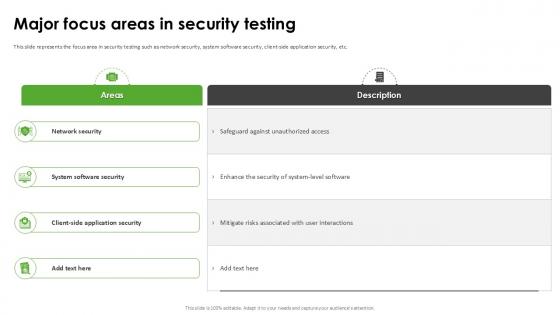
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.
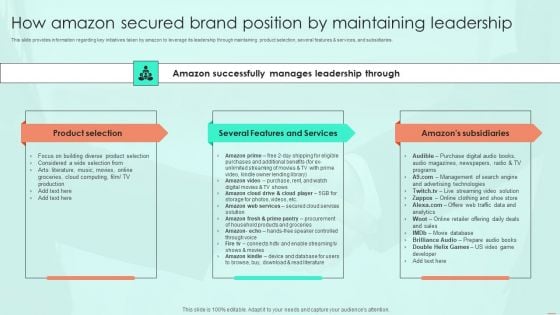
How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF
This slide provides information regarding key initiatives taken by amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF
Cyber Security Threat With Hacker Icon On The Screen Ppt PowerPoint Presentation Infographic Template PDF
Persuade your audience using this cyber security threat with hacker icon on the screen ppt powerpoint presentation infographic template pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security threat with hacker icon on the screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.
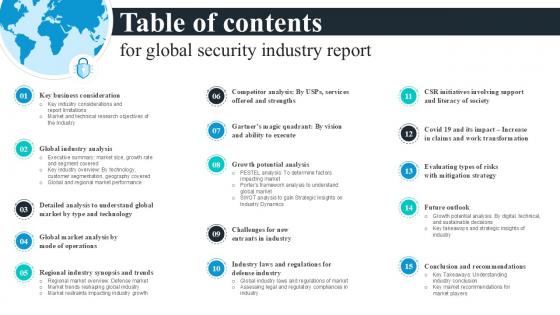
Table Of Contents For Global Security Industry Report PPT Template IR SS V
Slidegeeks has constructed Table Of Contents For Global Security Industry Report PPT Template IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents For Global Security Industry Report PPT Template IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
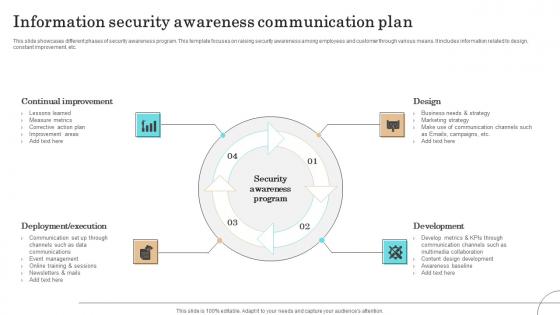
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.
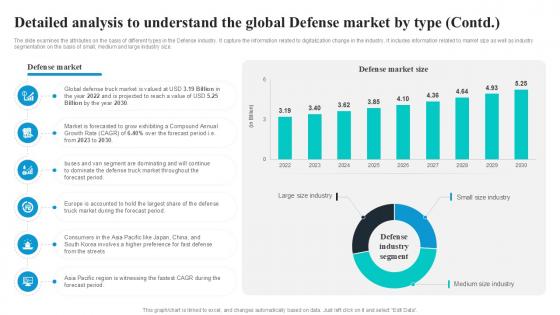
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.
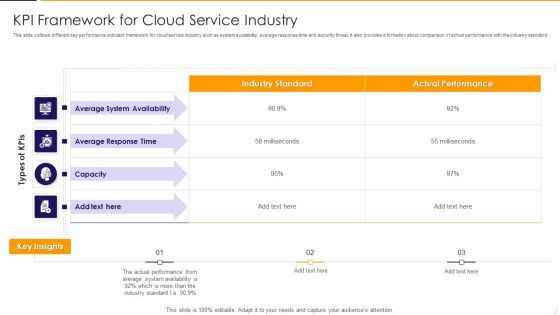
KPI Framework For Cloud Service Industry Ppt PowerPoint Presentation Gallery Styles PDF
This slide outlines different key performance indicator framework for cloud service industry such as system availability, average response time and security threat. It also provides information about comparison of actual performance with the industry standard. Pitch your topic with ease and precision using this kpi framework for cloud service industry ppt powerpoint presentation gallery styles pdf This layout presents information on average, performance, system It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
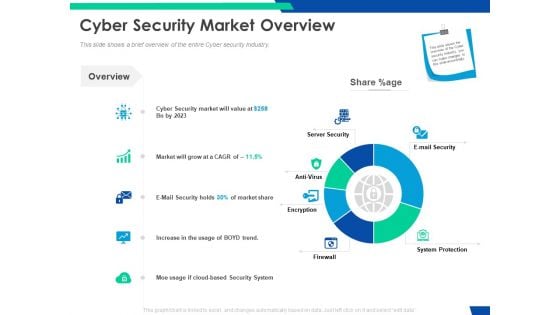
Cloud Based Email Security Market Report Cyber Security Market Overview Ppt Infographics Format PDF
This slide shows a brief overview of the entire Cyber security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report cyber security market overview ppt infographics format pdf bundle. Topics like cyber security market overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Application Security Case Study Kroll Application Security Testing
This slide highlights the overview of the company, problems faced, and their related solutions in the case study. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Application Security Case Study Kroll Application Security Testing for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the overview of the company, problems faced, and their related solutions in the case study.
Cyber Security Ppt PowerPoint Presentation Styles Inspiration
This is a cyber security ppt powerpoint presentation styles inspiration. This is a three stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
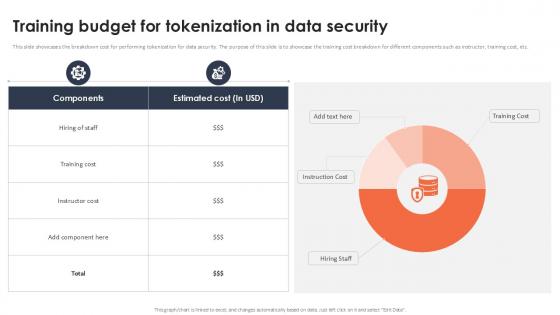
Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
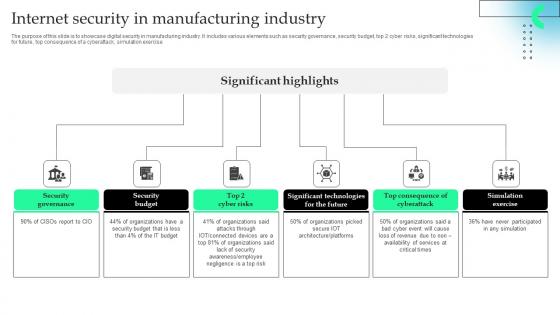
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.
Data Security Strategic Agenda Checklist Icon Mockup Pdf
Pitch your topic with ease and precision using this Data Security Strategic Agenda Checklist Icon Mockup Pdf. This layout presents information on Data Security Strategic, Agenda Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Strategic Agenda Checklist Icon Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
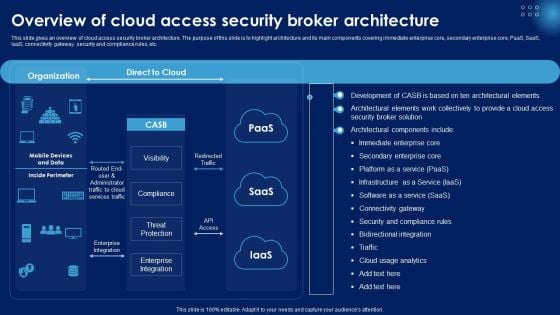
Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Slidegeeks has constructed Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Security Log Management Best Practices Application Security Testing
This slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security Log Management Best Practices Application Security Testing to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security Log Management Best Practices Application Security Testing. This slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc.
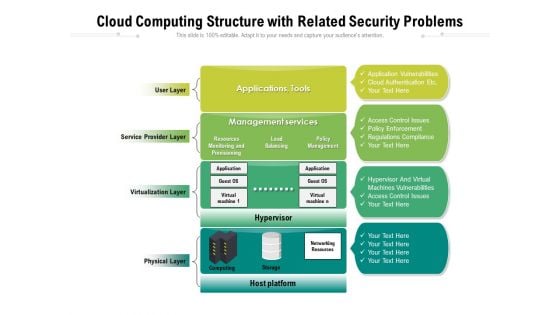
Cloud Computing Structure With Related Security Problems Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting this set of slides with name cloud computing structure with related security problems ppt powerpoint presentation gallery infographics pdf. This is a four stage process. The stages in this process are management, services, virtualization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
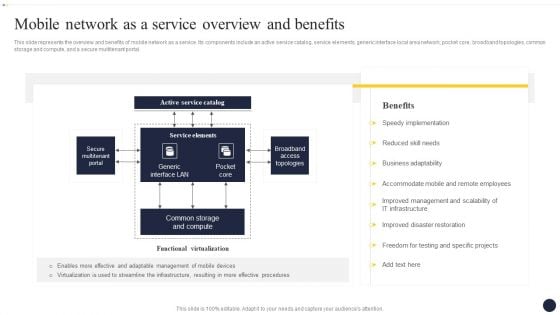
Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF
This slide represents the overview and benefits of mobile network as a service. Its components include an active service catalog, service elements, generic interface local area network, pocket core, broadband topologies, common storage and compute, and a secure multitenant portal. If you are looking for a format to display your unique thoughts, then the professionally designed Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Integrating Naas Service Model To Enhance Mobile Network As A Service Overview Themes PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
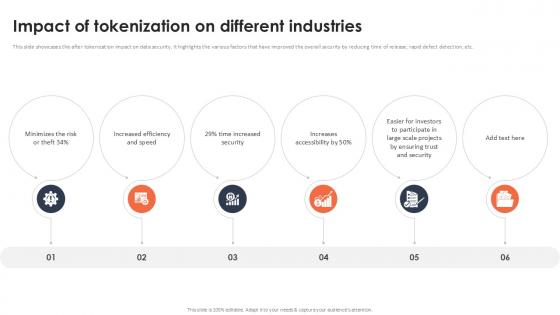
Impact Of Tokenization On Different Industries Securing Your Data Ppt Example
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Welcome to our selection of the Impact Of Tokenization On Different Industries Securing Your Data Ppt Example These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
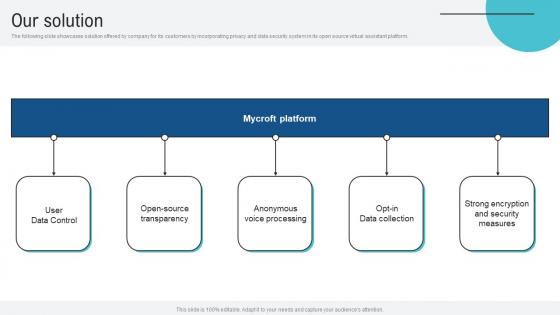
Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. This Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.

Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide
This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on. Want to ace your presentation in front of a live audience Our Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on.
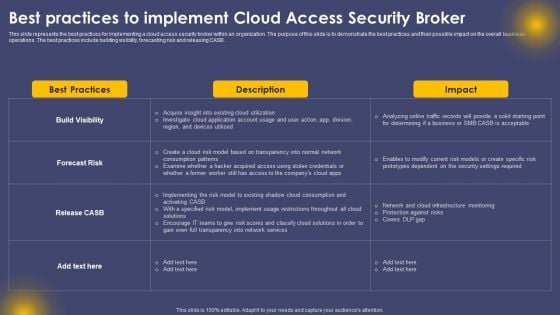
Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. There are so many reasons you need a Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
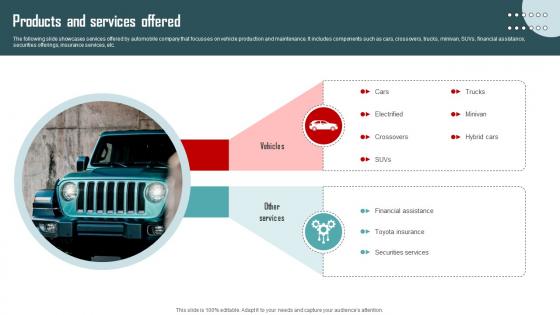
Products And Services Offered Vehicle Company Capital Funding Pitch Deck
The following slide showcases services offered by automobile company that focusses on vehicle production and maintenance. It includes components such as cars, crossovers, trucks, minivan, SUVs, financial assistance, securities offerings, insurance services, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Products And Services Offered Vehicle Company Capital Funding Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Products And Services Offered Vehicle Company Capital Funding Pitch Deck. The following slide showcases services offered by automobile company that focusses on vehicle production and maintenance. It includes components such as cars, crossovers, trucks, minivan, SUVs, financial assistance, securities offerings, insurance services, etc.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Authentication In Application Security For Data Protection Application Security Testing
This slide discusses about the overview of authentication in application security and the various elements of MFA. Present like a pro with Authentication In Application Security For Data Protection Application Security Testing. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses about the overview of authentication in application security and the various elements of MFA.
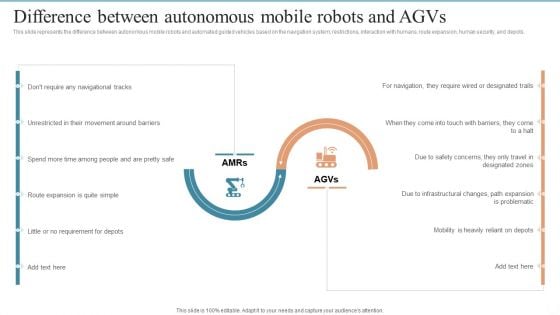
AMR Robot Difference Between Autonomous Mobile Robots And Agvs Ppt PowerPoint Presentation File Outline PDF
This slide represents the difference between autonomous mobile robots and automated guided vehicles based on the navigation system, restrictions, interaction with humans, route expansion, human security, and depots. Want to ace your presentation in front of a live audience Our AMR Robot Difference Between Autonomous Mobile Robots And Agvs Ppt PowerPoint Presentation File Outline PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
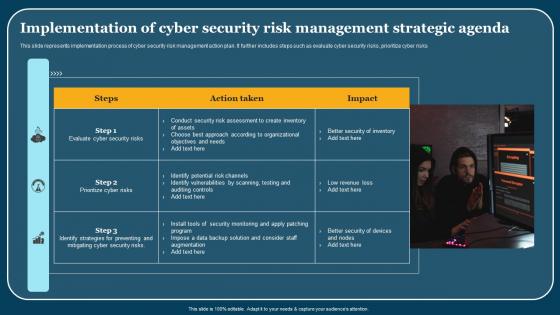
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.

Features Of Marketing Campaigns Presentation Outline
This is a features of marketing campaigns presentation outline. This is a ten stage process. The stages in this process are reporting and analysis, automatic capture, check previous activities, confidential security, classification, blocking, services, progressive profiling, time based degradation, updates lead remarks.

Capturing Security Events For Log Management Application Security Testing
This slide discusses the selection of security events that need to be logged for application security to ensure user accountability. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Capturing Security Events For Log Management Application Security Testing and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the selection of security events that need to be logged for application security to ensure user accountability.


 Continue with Email
Continue with Email

 Home
Home


































