Safety Summary

Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example
This slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on. The Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on.

Transportation And Logistics Services Company Profile Brief Company Overview Mockup PDF
The slide highlights the brief company overview depicting company name, founding year, founder name, employees, established place, head office, website, key subsidiaries, awards and achievements. This is a Transportation And Logistics Services Company Profile Brief Company Overview Mockup PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Key Subsidiaries, Awards And Achievements, Total Warehousing Solutions, Total Security And Monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.

Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide
This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc. Find highly impressive Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc.
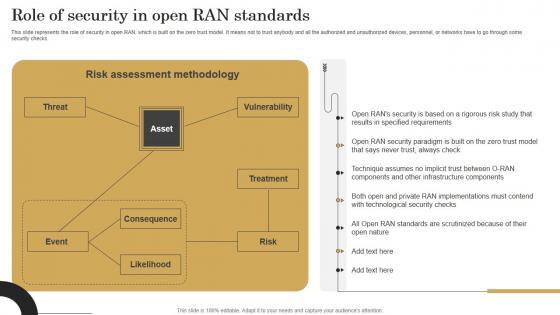
Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF from Slidegeeks and deliver a wonderful presentation. This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks.

Security KPI Dashboard Content Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Security KPI Dashboard Content Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising tweleve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
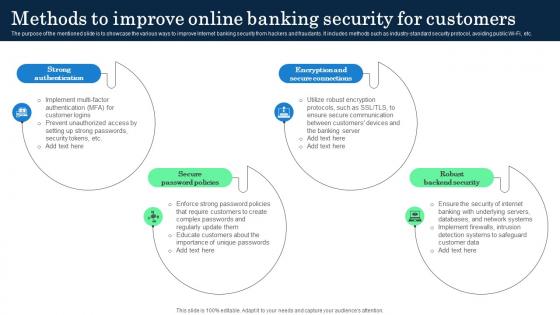
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.
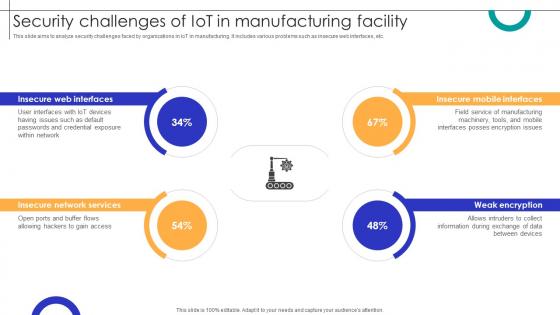
Security Challenges Of IOT In Manufacturing Facility Streamlining Production Ppt Example
This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Boost your pitch with our creative Security Challenges Of IOT In Manufacturing Facility Streamlining Production Ppt Example Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc.
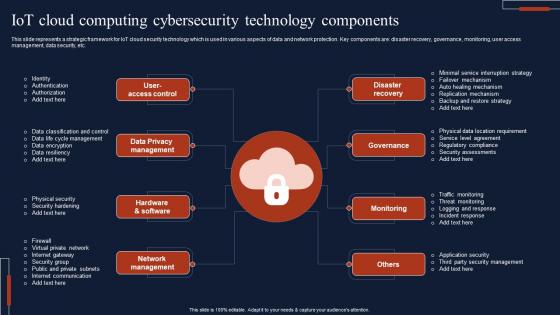
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
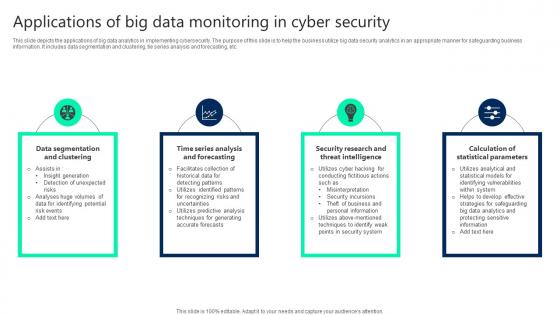
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
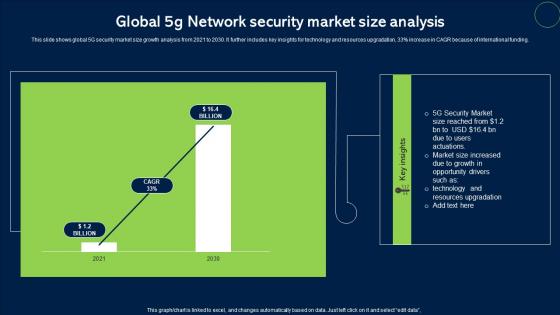
Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding.
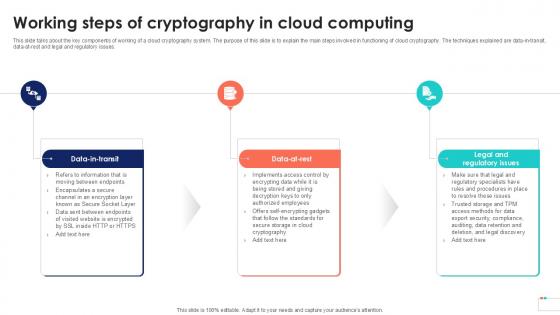
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.

Secure Files Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Do not leave it all up to fate. Fashion your destiny with our Secure Files Security PowerPoint Presentation Slides C.
Secure Files Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Achieve strong & sustainable quality gains with our Secure Files Security PowerPoint Presentation Slides Cc. They will make you look good.

Secure Files Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give your thoughts an exclusive feel. Our Secure Files Security PowerPoint Presentation Slides F will give them a distinctive touch.

Secure Files Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Your ideas will raise the stocks. Gain equity with our Secure Files Security PowerPoint Presentation Slides R.

Secure Files Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give a fillip to your campaign. Give it a fitting finale with our Secure Files Security PowerPoint Presentation Slides S.
Image For Multiple Internet Of Things Security Device Technology Slides Pdf
Pitch your topic with ease and precision using this Image For Multiple Internet Of Things Security Device Technology Slides Pdf This layout presents information on Multiple Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Image For Multiple Internet Of Things Security Device Technology Slides Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf
Pitch your topic with ease and precision using this Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf This layout presents information on Cyber Security Device, Icon To Prevent Form Malicious Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
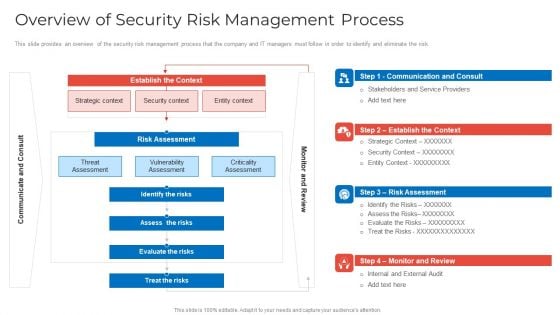
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
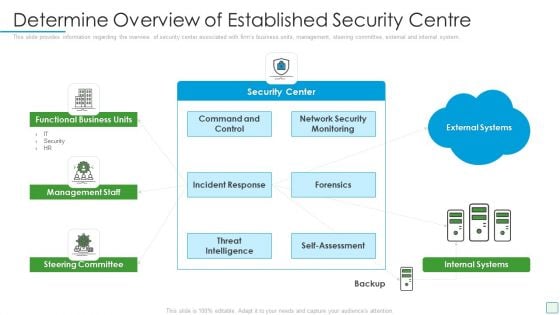
Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
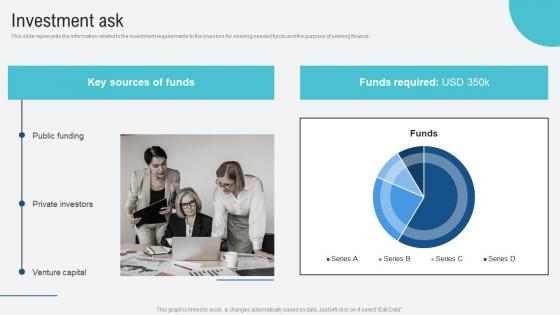
Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Are you searching for a Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf from Slidegeeks today. This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance.
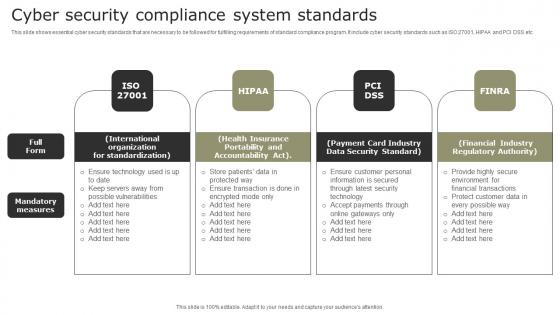
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
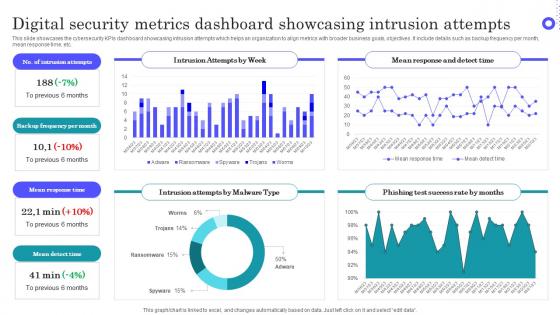
Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Dashboard Showcasing Intrusion Attempts Topics Pdf This layout presents information on Intrusion Attempts, Frequency Per Month, Mean Response Time It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cybersecurity KPIs dashboard showcasing intrusion attempts which helps an organization to align metrics with broader business goals, objectives. It include details such as backup frequency per month, mean response time, etc.
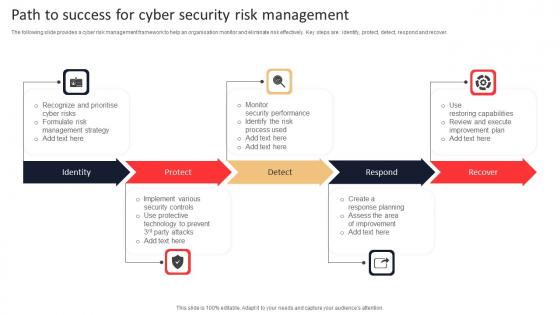
Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.
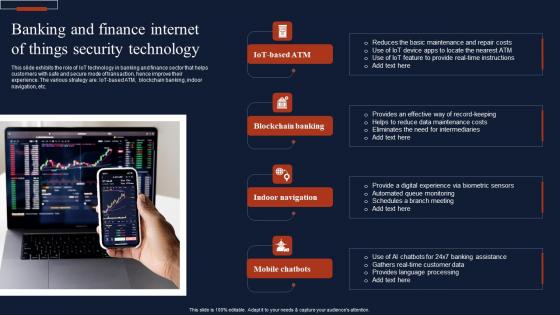
Banking And Finance Internet Of Things Security Technology Information Pdf
This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc. Pitch your topic with ease and precision using this Banking And Finance Internet Of Things Security Technology Information Pdf This layout presents information on Blockchain Banking, Ndoor Navigation, Mobile Chatbots It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide exhibits the role of IoT technology in banking and finance sector that helps customers with safe and secure mode of transaction, hence improve their experience. The various strategy are IoT-based ATM, blockchain banking, indoor navigation, etc.
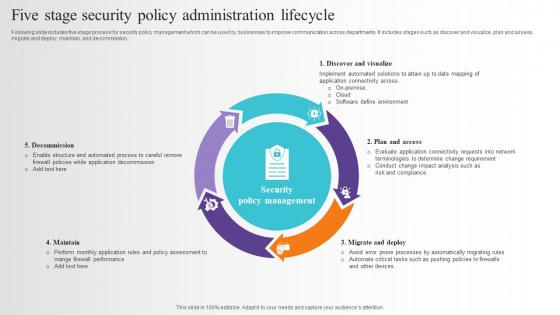
Five Stage Security Policy Administration Lifecycle Pictures Pdf
Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission. Pitch your topic with ease and precision using this Five Stage Security Policy Administration Lifecycle Pictures Pdf. This layout presents information on Plan And Assess, Migrate And Deploy, Maintain, Decommission. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission.
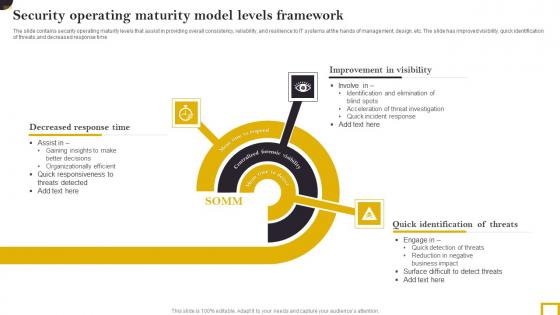
Security Operating Maturity Model Levels Framework Elements Pdf
The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Pitch your topic with ease and precision using this Security Operating Maturity Model Levels Framework Elements Pdf. This layout presents information on Decreased Response Time,Improvement Visibility, Quick Identification Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time.
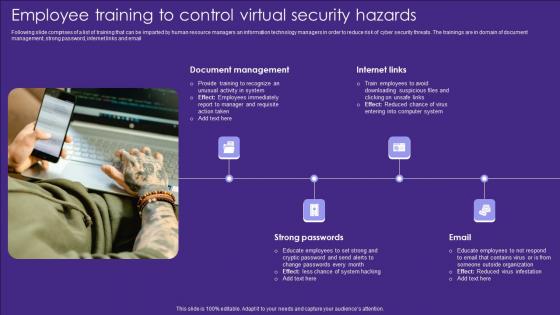
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
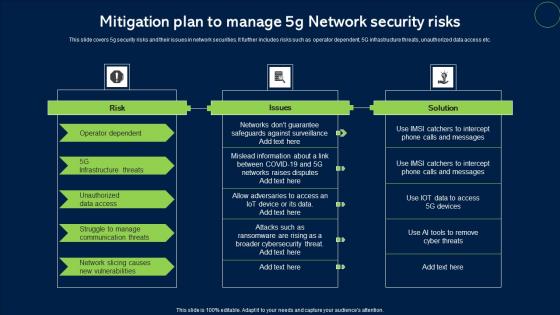
Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf
This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Showcasing this set of slides titled Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf. The topics addressed in these templates are Risk, Issues, Solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc.
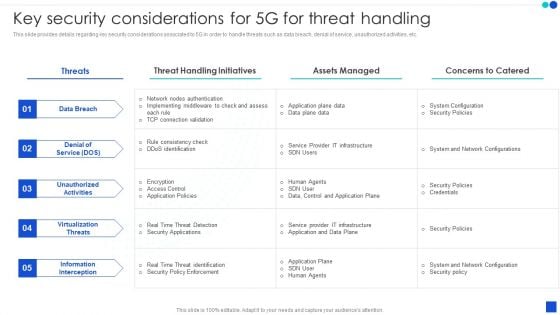
5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.
Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide
This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc. The Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc.
PowerPoint Presentation Designs Marketing Chains Process Ppt Designs
PowerPoint Presentation Designs Marketing chains process PPT Designs-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go. Our PowerPoint Presentation Designs Marketing Chains Process Ppt Designs will blow your ideas. They will fan out across the audience.
PowerPoint Slide Designs Marketing Chains Process Ppt Presentation
PowerPoint Slide Designs Marketing chains process PPT Presentation-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go. The corporate world can be fiercely competitive. Battle it out with our PowerPoint Slide Designs Marketing Chains Process Ppt Presentation.
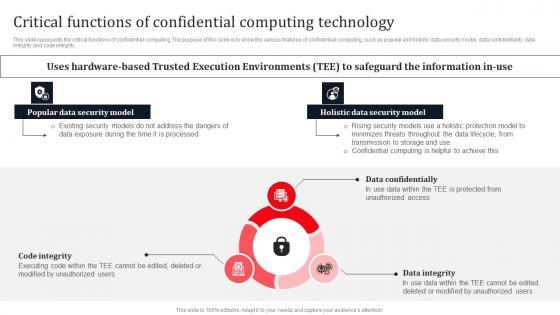
Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
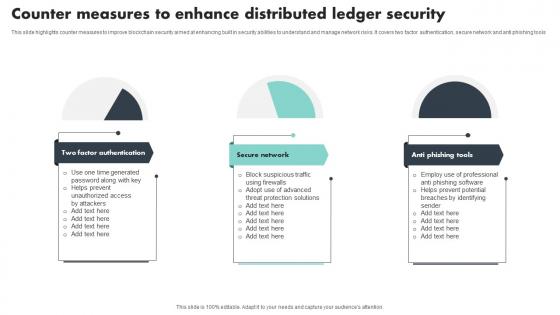
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools
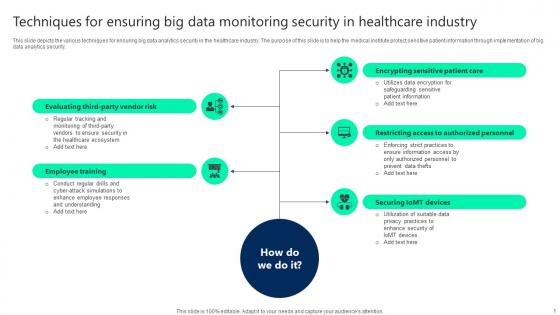
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.
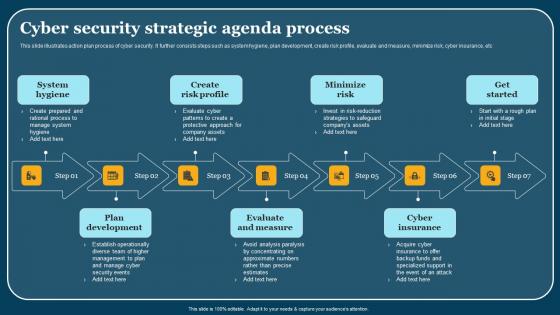
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.
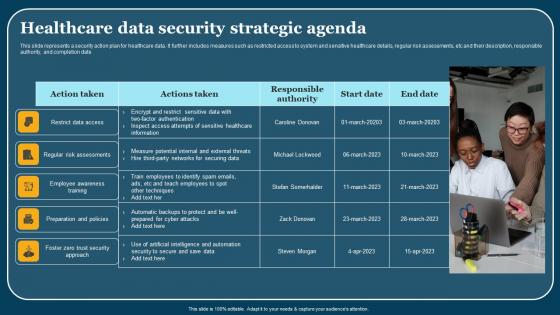
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date.
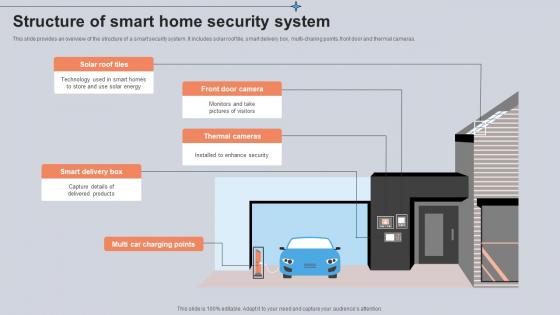
Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V
This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras.
Agenda Secure Multi Party Computation SMPC Professional Pdf
Take your projects to the next level with our ultimate collection of Agenda Secure Multi Party Computation SMPC Professional Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. Our Agenda Secure Multi Party Computation SMPC Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Handbook For Corporate Personnel Information Pdf
Create an editable Security Handbook For Corporate Personnel Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Handbook For Corporate Personnel Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide exhibits impact of effective internal communication on employee based on measurement performance indicators. It include elements such as engagement rate, turnover rate, productivity etc.
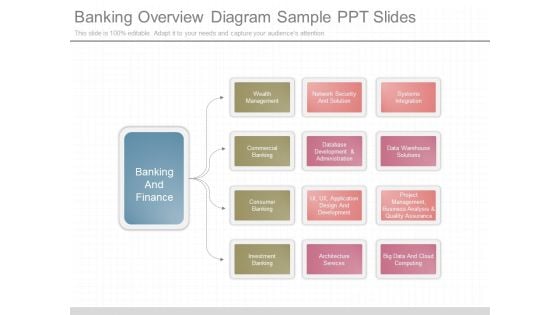
Banking Overview Diagram Sample Ppt Slides
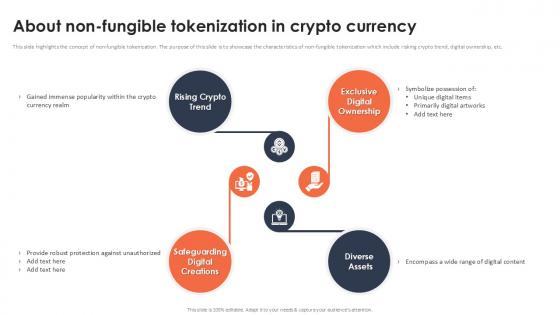
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.

Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc.

Top Rising Virtual Security Hazards In 2023 Elements Pdf
This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks Showcasing this set of slides titled Top Rising Virtual Security Hazards In 2023 Elements Pdf. The topics addressed in these templates are Crypto Jacking, Attacks, Medical Devices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks
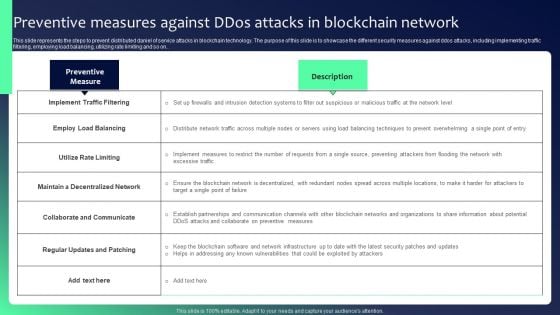
Blockchain Security Solutions Deployment Preventive Measures Against Ddos Attacks Professional PDF
This slide represents the steps to prevent distributed daniel of service attacks in blockchain technology. The purpose of this slide is to showcase the different security measures against ddos attacks, including implementing traffic filtering, employing load balancing, utilizing rate limiting and so on.. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Blockchain Security Solutions Deployment Preventive Measures Against Ddos Attacks Professional PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Secure Web Gateway Performance Tracking Dashboard Web Threat Protection System
Want to ace your presentation in front of a live audience Our Secure Web Gateway Performance Tracking Dashboard Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web
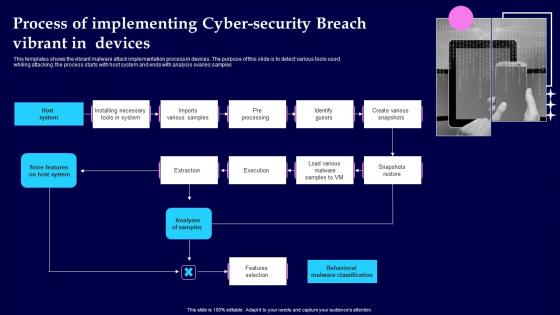
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples
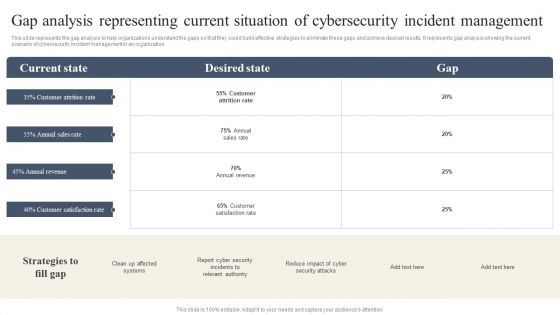
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
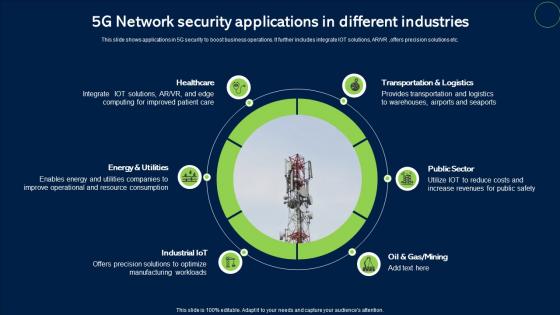
5G Network Security Applications In Different Industries Infographics Pdf
This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc. Showcasing this set of slides titled 5G Network Security Applications In Different Industries Infographics Pdf. The topics addressed in these templates are Healthcare, Public Sector, Transportation And Logistics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc.

Objective For Hard Money Loan Services Proposal Ppt Ideas Background Image PDF
This slide showcases objective for hard money loan services proposal which includes dream home purchase, long term security, good returns, taxes, insurance, general purchase, real estate investment, etc. Unleash your creativity with our Objective For Hard Money Loan Services Proposal Ppt Ideas Background Image PDF single-slide PPT template. Whether youre a seasoned presenter or a newbie, our editable and visually-stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience.
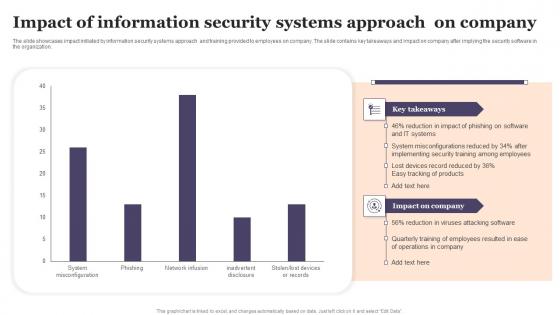
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization.
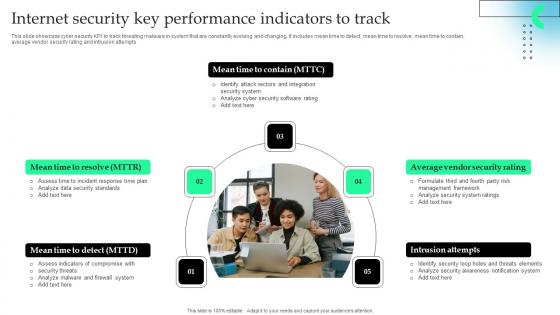
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.

Virtual Security Hazards Detection And Response Topics Pdf
This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Showcasing this set of slides titled Virtual Security Hazards Detection And Response Topics Pdf. The topics addressed in these templates are Security Centre, Access Time, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps


 Continue with Email
Continue with Email

 Home
Home


































