Safety Summary
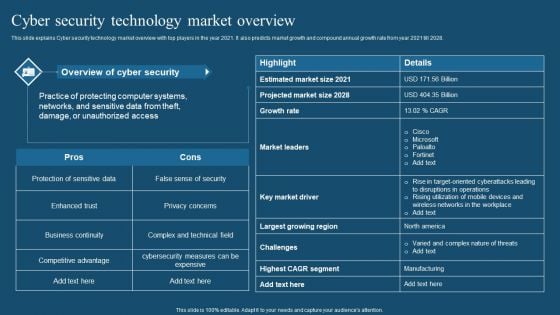
Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF
This slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Presenting this PowerPoint presentation, titled Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.

Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key And Lock Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our Technology PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download our Shapes PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Present our Business PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime.Use these PowerPoint slides for presentations relating to Protect your computer, Security, Technology, Business, Shapes, Computer. The prominent colors used in the PowerPoint template are Yellow, Gray, Blue. Get fascinated by our Laptop With Key And Lock Security PowerPoint Templates Ppt Backgrounds For Slides 0213. They will keep attracting your attention.
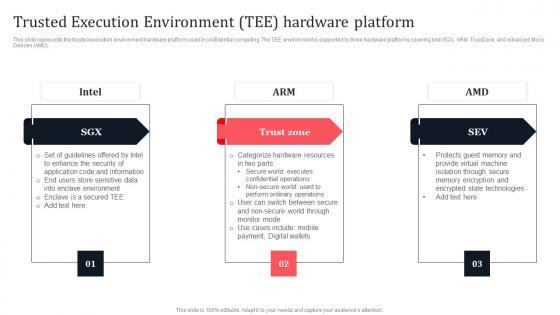
Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.

Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V
This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Secure Digital Wallet Payments In Depth Guide To Digital Wallets Fin SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc.

Lockable Notebook Security Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Lockable Notebook Security Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Computer PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Use our Internet PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Present our Security PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Use our Success PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to Notebook lockable pattern, security, internet, computer, technology, success. The prominent colors used in the PowerPoint template are Brown, Black, Yellow. The audience will always evince interest. Our Lockable Notebook Security Technology PowerPoint Templates Ppt Backgrounds For Slides 0213 will make them apply their minds.
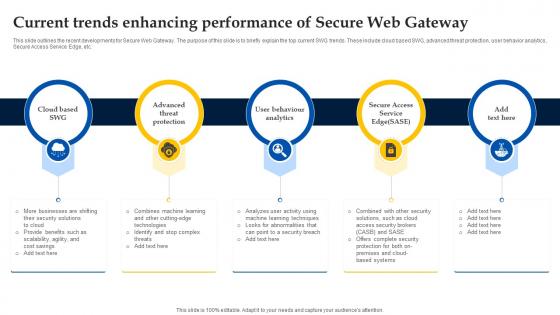
Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Web Access Control Solution Current Trends Enhancing Performance Of Secure Web Gateway that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.
Security Of Cloud Computing Ppt PowerPoint Presentation Inspiration Microsoft
This is a security of cloud computing ppt powerpoint presentation inspiration microsoft. This is a four stage process. The stages in this process are computer software, operating system, open source.
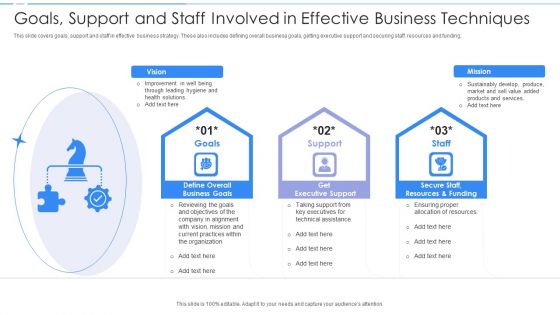
Goals Support And Staff Involved In Effective Business Techniques Ppt PowerPoint Presentation Outline Example PDF
This slide covers goals, support and staff in effective business strategy. These also includes defining overall business goals, getting executive support and securing staff, resources and funding.Showcasing this set of slides titled Goals Support And Staff Involved In Effective Business Techniques Ppt PowerPoint Presentation Outline Example PDF. The topics addressed in these templates are Leading Hygiene, Health Solutions, Improvement Well. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Piggy Bank Locked Secure Money Future PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind.Use these PowerPoint slides for presentations relating to Financial insurance, Security, Business, Shapes, Finance, Technology. The prominent colors used in the PowerPoint template are Gray, Red, Black. PowerPoint presentation experts tell us our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use our Technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. The feedback we get is that our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. The feedback we get is that our Security PowerPoint templates and PPT Slides will help them to explain complicated concepts. People tell us our Piggy Bank Locked Secure Money Future PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Professionals tell us our Technology PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Transition to a better presentation with our Piggy Bank Locked Secure Money Future PowerPoint Templates Ppt Backgrounds For Slides 0113. Download without worries with our money back guaranteee.
Innovation Tech Insights Security Operations Ppt PowerPoint Presentation Model Slideshow Cpb
Presenting this set of slides with name innovation tech insights security operations ppt powerpoint presentation model slideshow cpb. This is an editable Powerpoint four stages graphic that deals with topics like innovation tech insights security operations to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secured Public Cloud Network On Premises Vector Icon Ppt PowerPoint Presentation Gallery Slideshow PDF
Persuade your audience using this secured public cloud network on premises vector icon ppt powerpoint presentation gallery slideshow pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including secured public cloud network on premises vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V
This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc. Find highly impressive Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc.

Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V
The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges. Create an editable Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges.
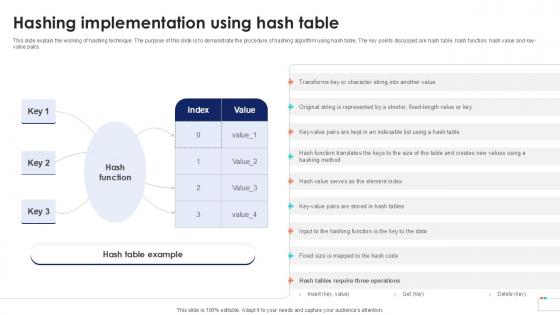
Hashing Implementation Using Data Security In Cloud Computing Ppt Powerpoint
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key-value pairs. Retrieve professionally designed Hashing Implementation Using Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key-value pairs.
Essential Principles For Business Process Improvement Ppt PowerPoint Presentation Outline Format Ideas PDF
Presenting this set of slides with name essential principles for business process improvement ppt powerpoint presentation outline format ideas pdf. This is a four stage process. The stages in this process are teamwork, direction, efficiency, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
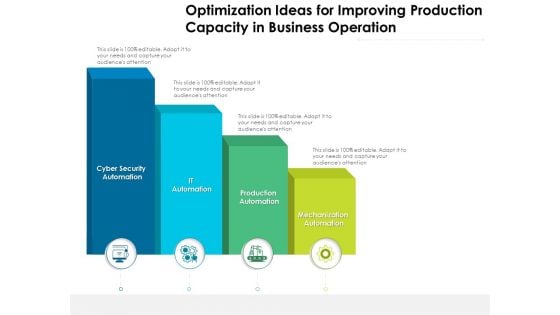
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
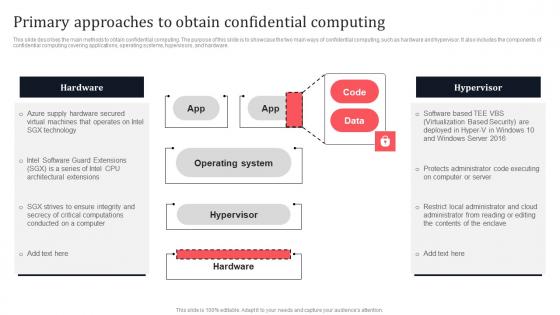
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
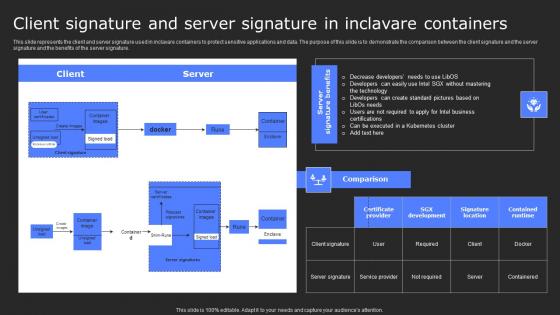
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
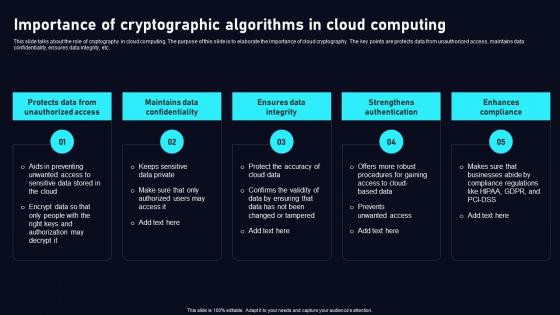
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
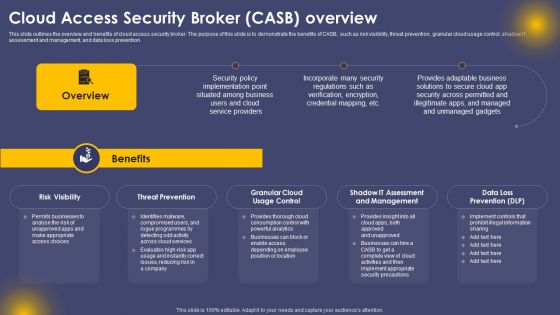
Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.

Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112
Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-Use this awesome PowerPoint template for property and ownership concept. This template features golden key with welcome home text. It portrays the concept of home, happiness, investment, mortgage, ownership, property, residence, security etc. This image has been conceived to enable you to emphatically communicate your ideas in your Real Estate PPT presentations. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand.-Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Gold Key With Welcome Home, Security, Business, Technology, Design, Metaphor Flood your audience with great slides with our Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112. Try us out and see what a difference our templates make.
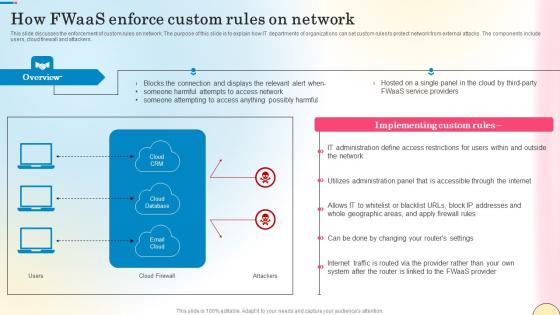
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.

Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V
The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. This Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects.
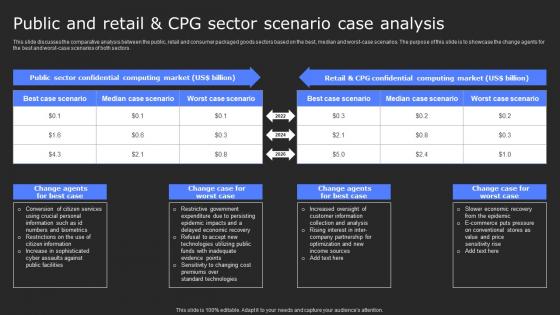
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
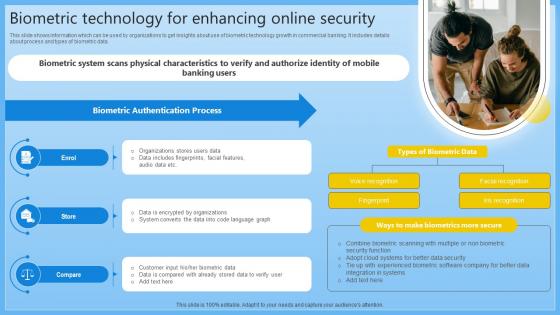
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
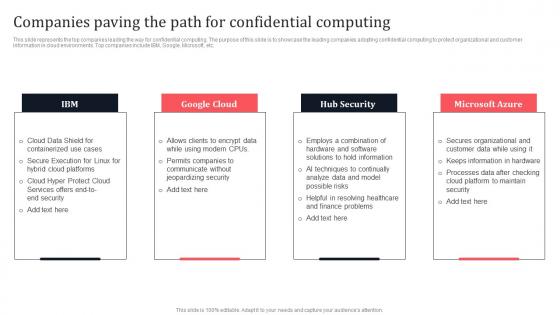
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
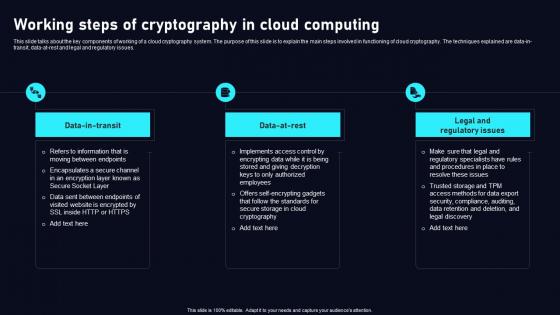
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.

Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V
The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions. There are so many reasons you need a Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions.
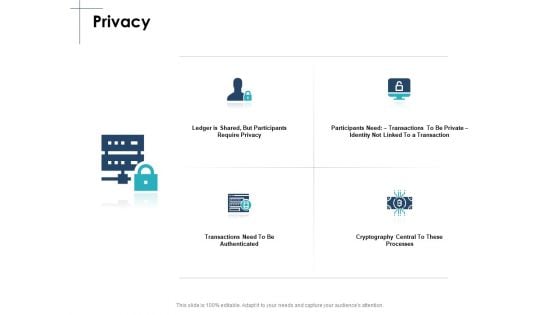
Privacy Security Ppt PowerPoint Presentation File Background Image
Presenting this set of slides with name privacy security ppt powerpoint presentation file background image. This is a four stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V
The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency.
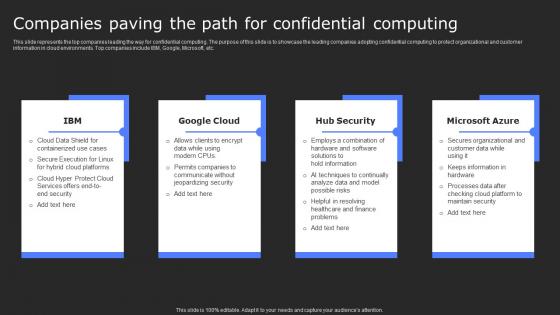
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.

Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V
The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. The Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as.
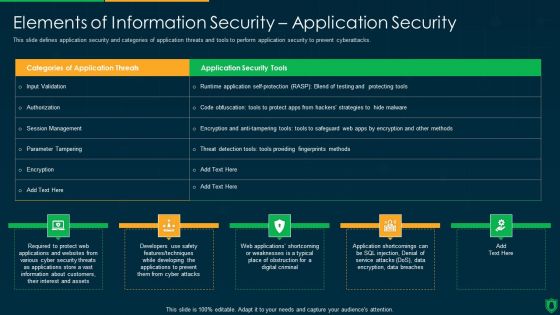
Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
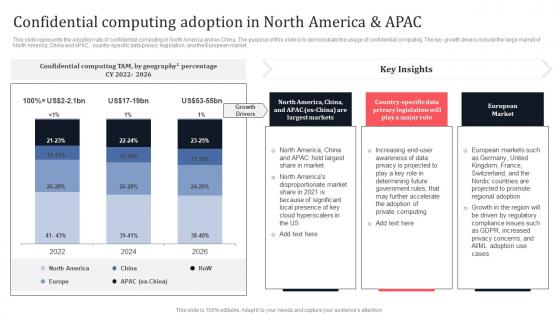
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.

Organizational Assets Security Management Strategy Ppt PowerPoint Presentation Complete Deck With Slides
In business, sometimes the end result can be completely different from what stakeholders visualized. This Organizational Assets Security Management Strategy Ppt PowerPoint Presentation Complete Deck With Slides details the study of enterprise and problem solving as a fundamental area of getting the desired outcomes. Stakeholders need to be convinced of how to proceed and change through this wonderful PPT presentation. The idea guiding this complete deck of twenty two presentation slides is to ensure that dealing with change and unexpected results becomes easy. The area of focus for this change can be customized with the 100 percent editable and customizable nature of each of the slides in our presentation. Download now.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
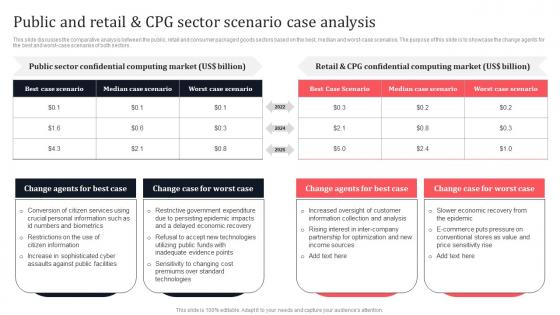
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
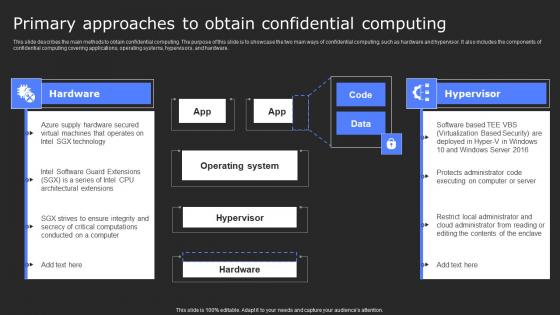
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
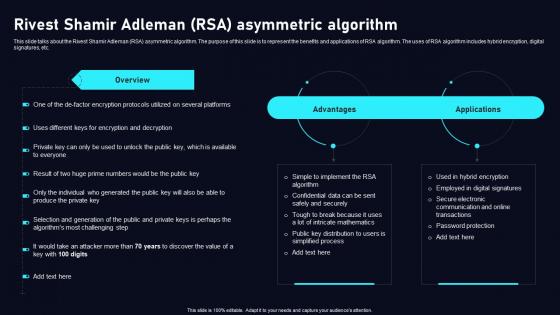
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.

Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain
This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.Presenting this PowerPoint presentation, titled Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.

Key To Success PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Key To Success PowerPoint Templates PPT Backgrounds For Slides 1112.Present our Security PowerPoint Templates because excite your audience with the brilliance of your thoughts. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Present our Business PowerPoint Templates because you have had your share of being a goldfishin a small bowl.you are ready to launch out and spread your wings. Present our Shapes PowerPoint Templates because this template helps you to illustrate your method, piece by piece, and interlock the whole process in the minds of your audience. Download our Future PowerPoint Templates because they have fired the dreams of many fertile minds.Use these PowerPoint slides for presentations relating to Key to success, business, security, success, shapes, future. The prominent colors used in the PowerPoint template are Green, Green dark, White. People tell us our Key To Success PowerPoint Templates PPT Backgrounds For Slides 1112 are visually appealing. Presenters tell us our shapes PowerPoint templates and PPT Slides are Excellent. Presenters tell us our Key To Success PowerPoint Templates PPT Backgrounds For Slides 1112 are designed by professionals Use our security PowerPoint templates and PPT Slides are Graceful. We assure you our Key To Success PowerPoint Templates PPT Backgrounds For Slides 1112 are visually appealing. The feedback we get is that our success PowerPoint templates and PPT Slides are Festive. Interpret plans with our Key To Success PowerPoint Templates Ppt Backgrounds For Slides 1112. Download without worries with our money back guaranteee.

Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Our Services Ppt PowerPoint Presentation Gallery Model
This is a our services ppt powerpoint presentation gallery model. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.
Our Services Ppt PowerPoint Presentation Model Grid
This is a our services ppt powerpoint presentation model grid. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics , security maintenance.

Our Services Ppt PowerPoint Presentation Professional Ideas
This is a our services ppt powerpoint presentation professional ideas. This is a four stage process. The stages in this process are marketing and analytics, digital advertising, security maintenance, digital care package.
Our Services Ppt PowerPoint Presentation Inspiration Brochure
This is a our services ppt powerpoint presentation inspiration brochure. This is a four stage process. The stages in this process are digital advertising, marketing and analytics, digital care package, security and maintenance.

Notebook Lifesaver Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Notebook Lifesaver Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Present our Technology PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Download and present our Shapes PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Present our Business PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust.Use these PowerPoint slides for presentations relating to Notebook lifesaver technology, computer, technology, security, shapes, business. The prominent colors used in the PowerPoint template are Red, Gray, White. Bring the advantages to the fore with our Notebook Lifesaver Technology PowerPoint Templates Ppt Backgrounds For Slides 0213. Your audience will get off the fence.

Staff Recruitment Strategy At Workplace Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Staff Recruitment Strategy At Workplace Ppt PowerPoint Presentation Complete With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty three slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Challenges For New Entrants In Global Security Industry PPT Example IR SS V
The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently. Want to ace your presentation in front of a live audience Our Challenges For New Entrants In Global Security Industry PPT Example IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently.

Best Practices For Secure Web Gateway Implementation Web Threat Protection System
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. There are so many reasons you need a Best Practices For Secure Web Gateway Implementation Web Threat Protection System. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.
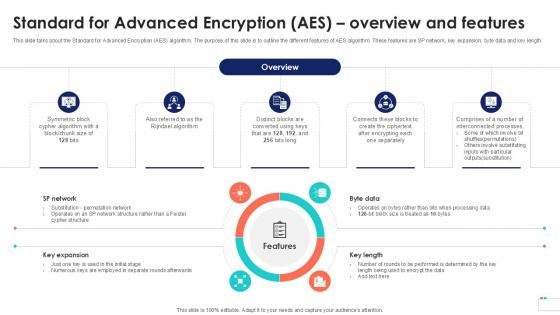
Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
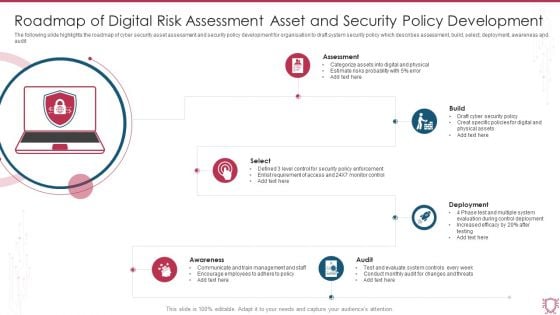
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Tools For Vulnerability Scanning In Security Testing Application Security Testing
This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Retrieve professionally designed Tools For Vulnerability Scanning In Security Testing Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.
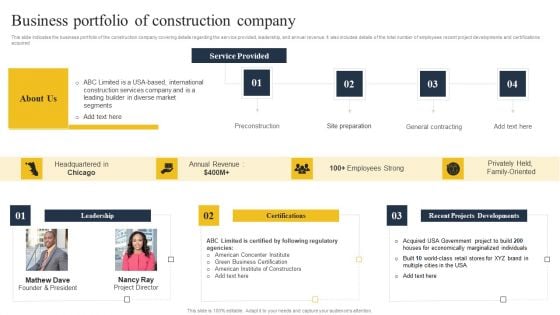
Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
This slide indicates the business portfolio of the construction company covering details regarding the service provided, leadership, and annual revenue. It also includes details of the total number of employees recent project developments and certifications acquired. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF


 Continue with Email
Continue with Email

 Home
Home


































