Safety Summary

Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. There are so many reasons you need a Secure Web Gateway Set Up Ongoing Maintenance Web Access Control Solution. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.
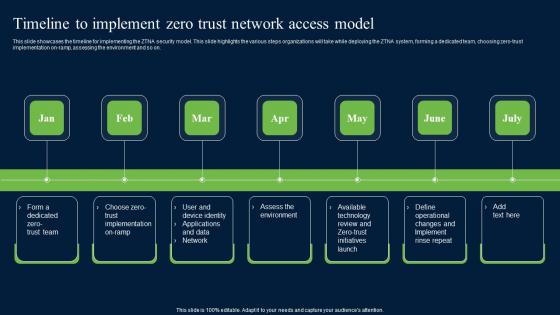
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
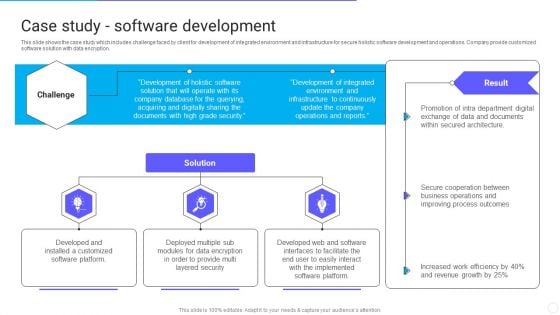
IT Application Services Company Outline Case Study Software Development Infographics PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting IT Application Services Company Outline Case Study Software Development Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Layered Security, Implemented, Developed Web. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
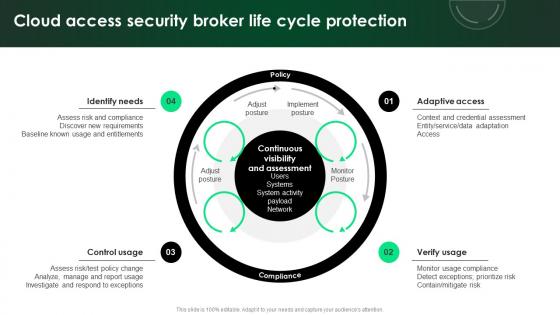
CASB 2 0 IT Cloud Access Security Broker Life Cycle Protection
Explore a selection of the finest CASB 2 0 IT Cloud Access Security Broker Life Cycle Protection here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CASB 2 0 IT Cloud Access Security Broker Life Cycle Protection to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Our CASB 2 0 IT Cloud Access Security Broker Life Cycle Protection are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

How To Strengthen Relationships With Clients And Partners 4 Finalize The Partners Ppt Layouts Outline PDF
Presenting this set of slides with name how to strengthen relationships with clients and partners 4 finalize the partners ppt layouts outline pdf. The topics discussed in these slides are business requirements, necessity, vendor, secure web access, activity planning and tracking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Get a simple yet stunning designed Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today. This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc.

Analyzing Multiple Sales Tactics For Securing Strategic Sales Plan To Enhance Introduction Pdf
This slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc. Want to ace your presentation in front of a live audience Our Analyzing Multiple Sales Tactics For Securing Strategic Sales Plan To Enhance Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc.
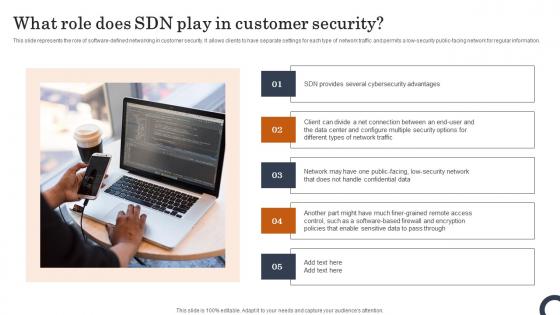
What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.

Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Internet PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download and present our Computer PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Computer security concept, computer, internet, success, technology, security. The prominent colors used in the PowerPoint template are Brown, Black, Gray. People tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our security PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. PowerPoint presentation experts tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Presenters tell us our Laptop With Lock And Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. The feedback we get is that our technology PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Examine the causes with our Laptop With Lock And Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Let everyone know what's behind it all.
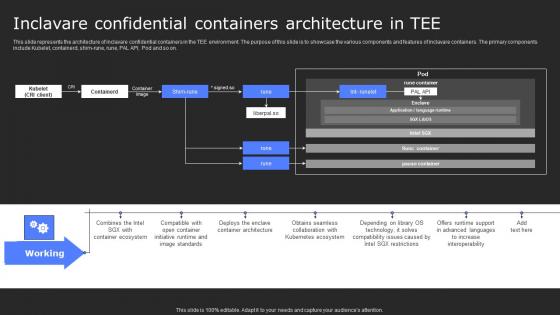
Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Do you know about Slidesgeeks Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
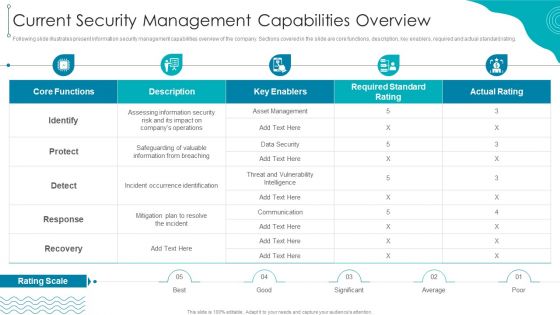
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.
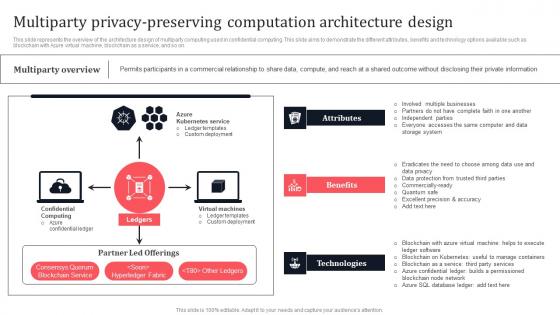
Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Create an editable Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
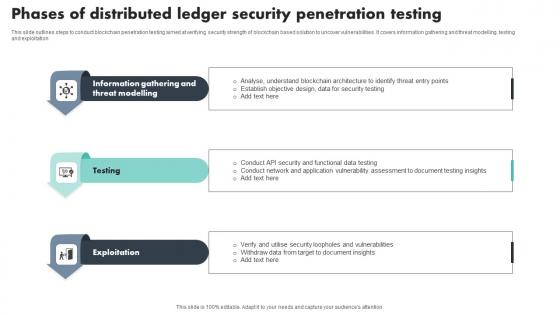
Phases Of Distributed Ledger Security Penetration Testing Download Pdf
This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation Showcasing this set of slides titled Phases Of Distributed Ledger Security Penetration Testing Download Pdf The topics addressed in these templates are Information Gathering, Threat Modelling, Exploitation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation
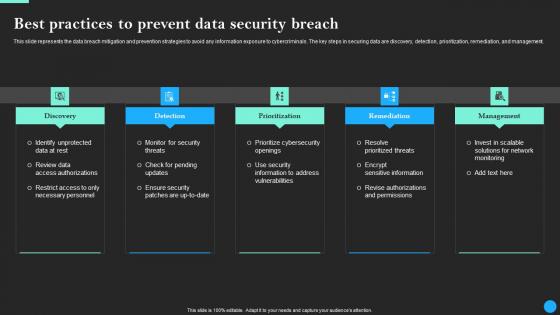
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
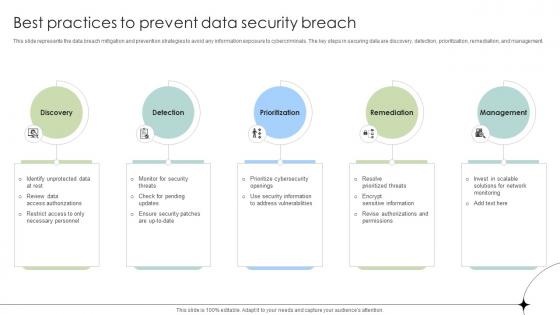
Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
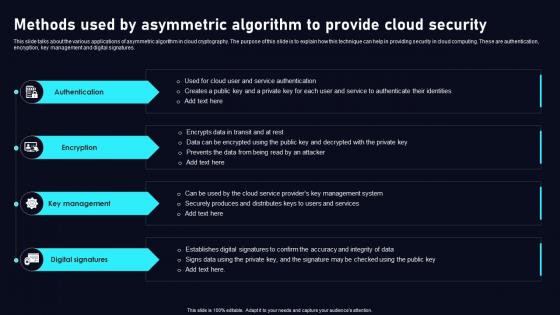
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication.
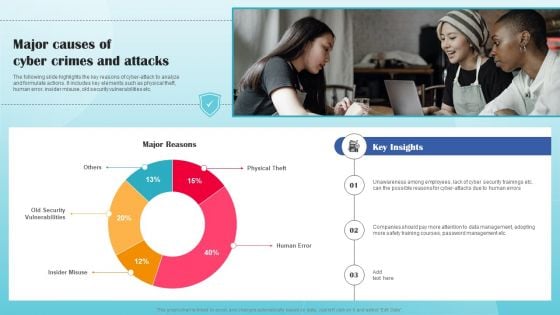
Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Find a pre designed and impeccable Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.
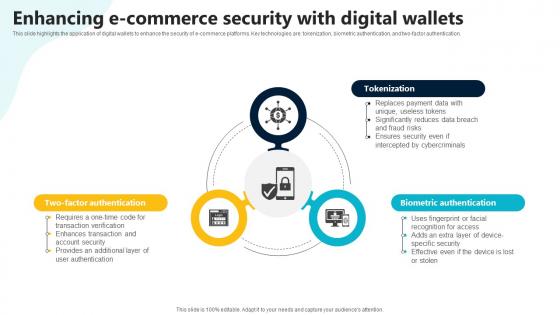
Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the application of digital wallets to enhance the security of e-commerce platforms. Key technologies are tokenization, biometric authentication, and two-factor authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the application of digital wallets to enhance the security of e-commerce platforms. Key technologies are tokenization, biometric authentication, and two-factor authentication.
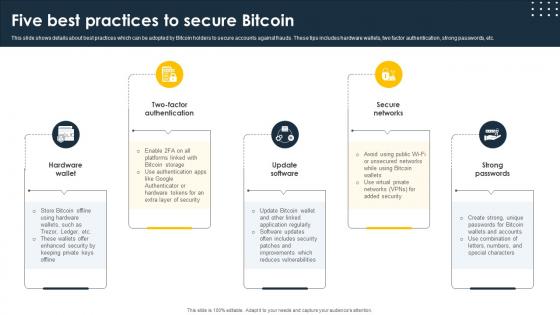
Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.

3d Dollars Under Lifesaver Tube Security PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our 3D Dollars Under Lifesaver Tube Security PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Security PowerPoint Templates because you have the process in your head, our template design showing will illuminate your thoughts. Download and present our Money PowerPoint Templates because you will be able to Highlight these individual targets and the paths to their achievement. Present our Finance PowerPoint Templates because you envisage some areas of difficulty in the near future. The overall financial situation could be a source of worry. Use our Business PowerPoint Templates because your thoughts are pointed and sharp as arrows. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb.Use these PowerPoint slides for presentations relating to Dollar under lifesaver, security, money, finance, business, success. The prominent colors used in the PowerPoint template are Red, Black, White. People tell us our 3D Dollars Under Lifesaver Tube Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Excellent. Presenters tell us our finance PowerPoint templates and PPT Slides are Ultra. PowerPoint presentation experts tell us our 3D Dollars Under Lifesaver Tube Security PowerPoint Templates PPT Backgrounds For Slides 1112 will save the presenter time. Customers tell us our lifesaver PowerPoint templates and PPT Slides are Stunning. Customers tell us our 3D Dollars Under Lifesaver Tube Security PowerPoint Templates PPT Backgrounds For Slides 1112 are Sparkling. Customers tell us our security PowerPoint templates and PPT Slides are Festive. Capture success with our 3d Dollars Under Lifesaver Tube Security PowerPoint Templates Ppt Backgrounds For Slides 1112. You will come out on top.
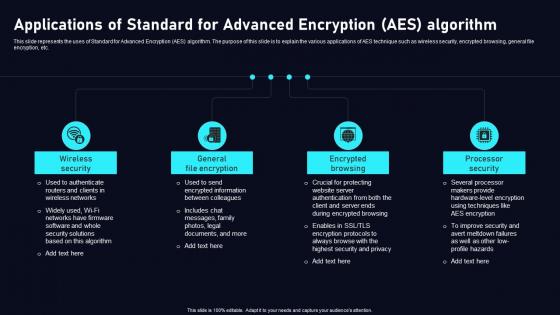
Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.
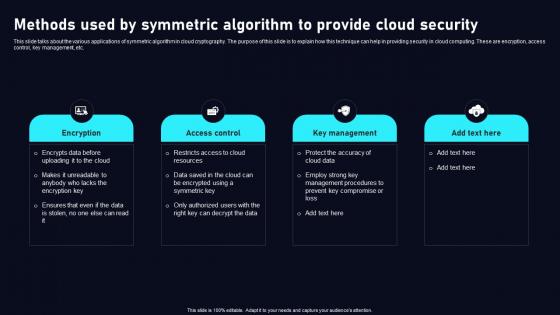
Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
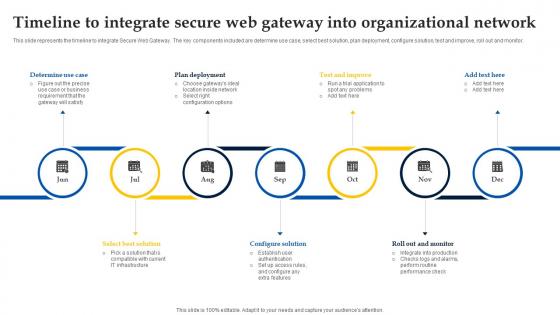
Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network
This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Timeline To Integrate Secure Web Gateway Into Organizational Network and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.
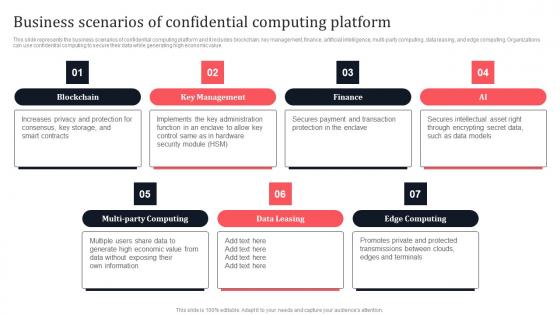
Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Boost your pitch with our creative Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
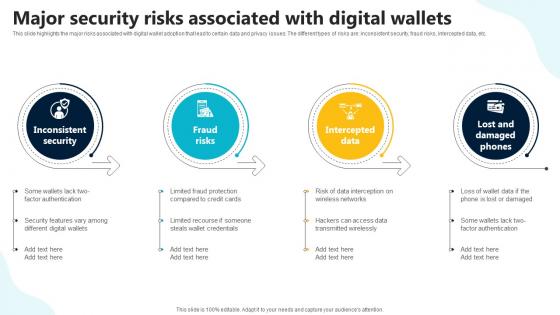
Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Boost your pitch with our creative Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc.

Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF
The following slide showcases comparison of email security gateways along with features rating and price. Main gateways included are mimecast, ironscales, avanan and trustifi. Showcasing this set of slides titled Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF. The topics addressed in these templates are Gateway Device Establishment, Establish Strong, Identity For Gateway. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
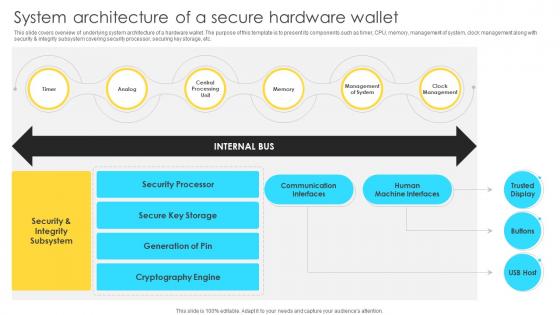
Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V
This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc. Welcome to our selection of the Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc.
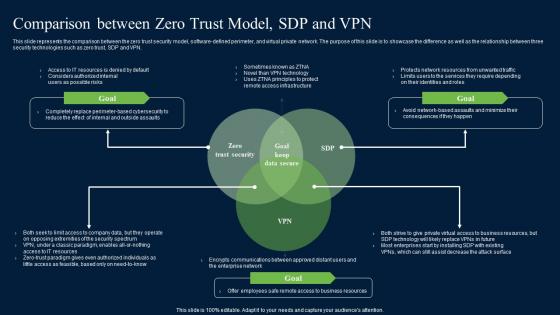
Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
Shield With Lock Sigh For Data Security Vector Icon Ppt PowerPoint Presentation File Samples PDF
Presenting shield with lock sigh for data security vector icon ppt powerpoint presentation file samples pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including shield with lock sigh for data security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Man Opening Door With Security System On Smart Phone Ppt PowerPoint Presentation Model Grid PDF
Presenting man opening door with security system on smart phone ppt powerpoint presentation model grid pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including man opening door with security system on smart phone. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Person Opening Office Door With Security Access Control System Ppt PowerPoint Presentation Styles Rules PDF
Presenting person opening office door with security access control system ppt powerpoint presentation styles rules pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including person opening office door with security access control system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Our Keys To Success Template 1 Ppt PowerPoint Presentation Professional Elements
This is a our keys to success template 1 ppt powerpoint presentation professional elements. This is a four stage process. The stages in this process are our keys to success.

For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf
Are you searching for a For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf from Slidegeeks today. Our For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Concept Of Secured Money America PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Security PowerPoint Templates because it Educates your team with your thoughts and logic. Download and present our Finance PowerPoint Templates because it shows to your group how they mesh together to drive the whole. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Money PowerPoint Templates because this is a wonderful graphics to see the smiles of happiness spread as your audience realizes the value of your words.Use these PowerPoint slides for presentations relating to Lock up & protect us dollar, money, finance, security, success, business. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Customers tell us our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are visually appealing. Presenters tell us our security PowerPoint templates and PPT Slides are Wonderful. Use our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. PowerPoint presentation experts tell us our us PowerPoint templates and PPT Slides are Nifty. Customers tell us our Concept Of Secured Money America PowerPoint Templates PPT Backgrounds For Slides 1212 are Classic. Presenters tell us our protect PowerPoint templates and PPT Slides are Magical. Keep them driven with our Concept Of Secured Money America PowerPoint Templates Ppt Backgrounds For Slides 1212. You will come out on top.
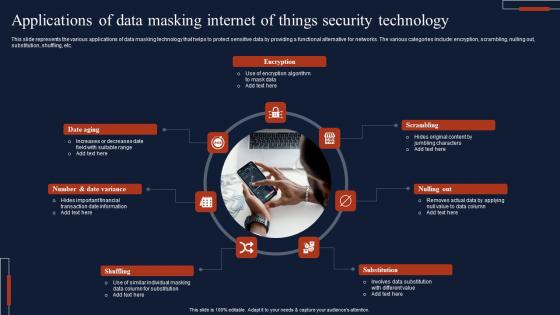
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.

Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. There are so many reasons you need a Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.
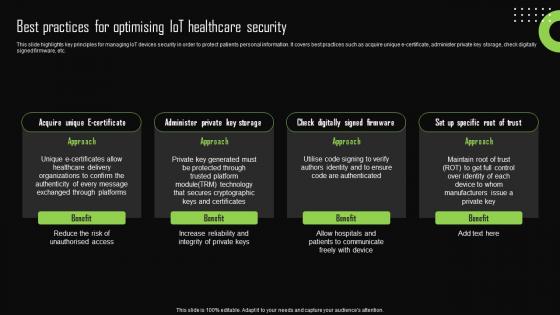
Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. There are so many reasons you need a Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
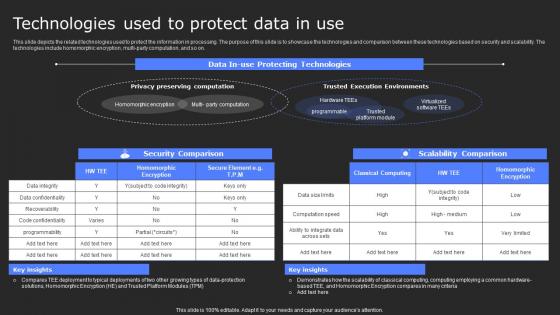
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers.
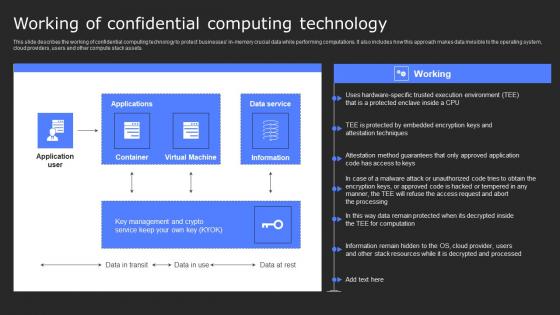
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
Email Security Vector Icon Ppt PowerPoint Presentation Model Example Topics
Presenting this set of slides with name email security vector icon ppt powerpoint presentation model example topics. This is a four stage process. The stages in this process are email security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Recent Global Security Market Trends Behavior Marketing Ppt PowerPoint Presentation Model Slideshow
This is a recent global security market trends behavior marketing ppt powerpoint presentation model slideshow. This is a six stage process. The stages in this process are business, management, marketing.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Computer PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Download our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, security, network diagrams, communication. The prominent colors used in the PowerPoint template are Gray, Blue, Yellow. Corporate battles can be fierce. Be appropriately armed with our Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0213.
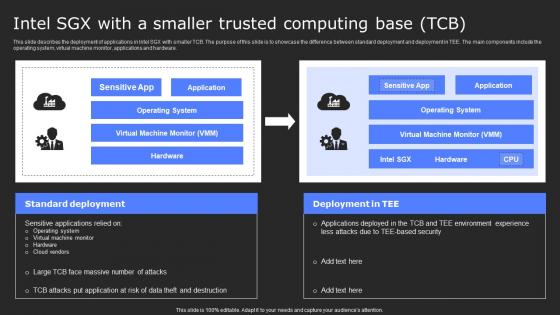
Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Find a pre-designed and impeccable Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.

Firewall Network Security Communication PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Firewall Network Security Communication PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download and present our Business PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Present our Signs PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to firewall, security, business, signs, communication, technology. The prominent colors used in the PowerPoint template are Green, Red, White. Our Firewall Network Security Communication PowerPoint Templates Ppt Backgrounds For Slides 0313 ensure the audience is never fed up. They will continue asking for more.
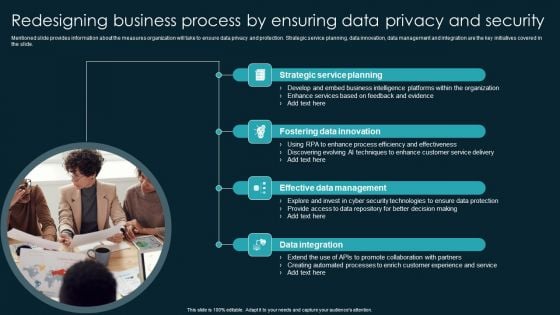
Redesigning Business Process By Ensuring Data Privacy And Security Infographics PDF

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc.

Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V
The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts. Get a simple yet stunning designed Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts.

Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
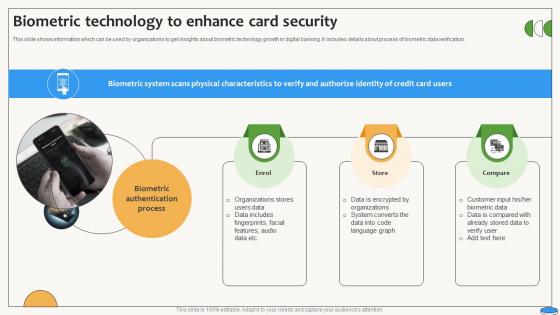
Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V
This slide shows information which can be used by organizations to get insights about biometric technology growth in digital banking. It includes details about process of biometric data verification. There are so many reasons you need a Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows information which can be used by organizations to get insights about biometric technology growth in digital banking. It includes details about process of biometric data verification.
Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF
This slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Presenting Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Essential Features Provided By Saas Program Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the essential features provided by saas platform illustrating key headings which includes cost efficiency, scalability, reliability and security. Persuade your audience using this essential features provided by saas program ppt powerpoint presentation file outline pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cost efficiency, scalability, reliability, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Secure Web Gateway Implementation Methodology Inline Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Boost your pitch with our creative Secure Web Gateway Implementation Methodology Inline Web Threat Protection System. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.


 Continue with Email
Continue with Email

 Home
Home


































