Safety Summary
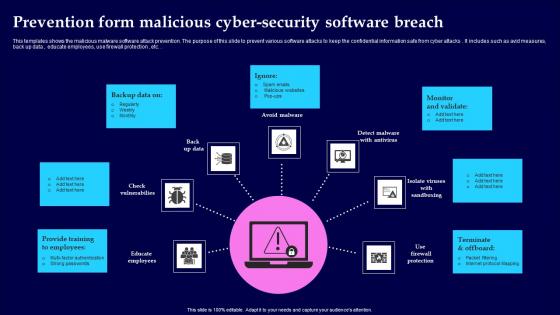
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.
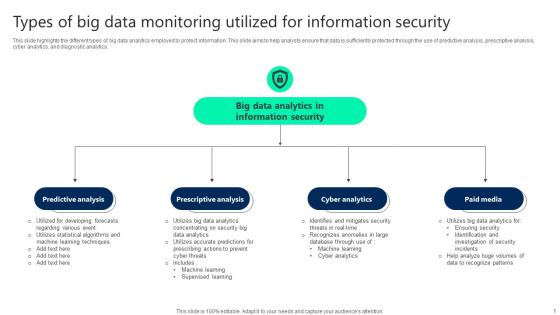
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics.

Process Phases Of Penetration Testing In Application Security Testing
This slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc. Presenting this PowerPoint presentation, titled Process Phases Of Penetration Testing In Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Process Phases Of Penetration Testing In Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Process Phases Of Penetration Testing In Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc.
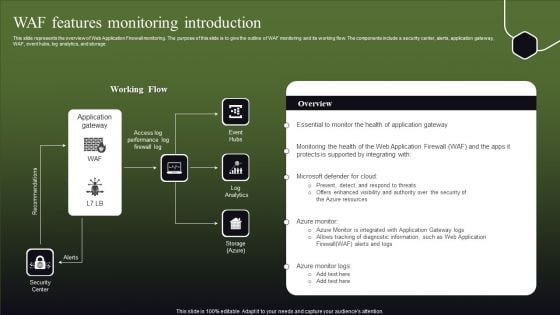
WAF Features Monitoring Introduction Ppt Outline Example Topics PDF
This slide represents the overview of Web Application Firewall monitoring. The purpose of this slide is to give the outline of WAF monitoring and its working flow. The components include a security center, alerts, application gateway, WAF, event hubs, log analytics, and storage. Presenting this PowerPoint presentation, titled WAF Features Monitoring Introduction Ppt Outline Example Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this WAF Features Monitoring Introduction Ppt Outline Example Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable WAF Features Monitoring Introduction Ppt Outline Example Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

International Organization Standardization 270001 Current Security Management Capabilities Overview Pictures PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 current security management capabilities overview pictures pdf. Use them to share invaluable insights on current security management capabilities overview and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
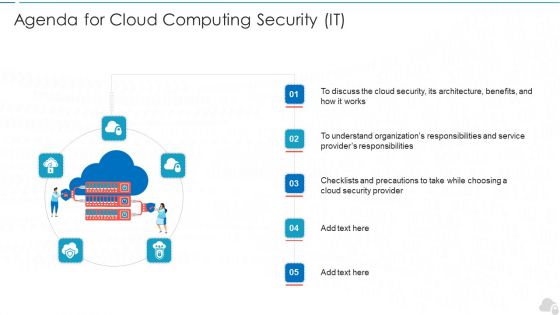
Agenda For Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
Presenting agenda for cloud computing security it ppt infographic template inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cloud security, service, architecture, organizations, responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Big Data Security Market Overview Ppt PowerPoint Presentation Model Sample Cpb
Presenting this set of slides with name big data security market overview ppt powerpoint presentation model sample cpb. This is an editable Powerpoint five stages graphic that deals with topics like big data security market overview to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
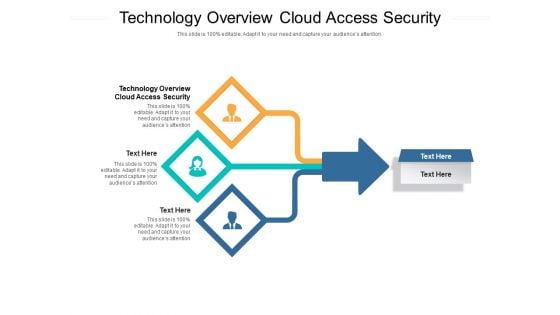
Technology Overview Cloud Access Security Ppt PowerPoint Presentation Model Ideas Cpb Pdf
Presenting this set of slides with name technology overview cloud access security ppt powerpoint presentation model ideas cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like technology overview cloud access security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates
We present our systematic concentric process diagram business plan outline PowerPoint templates.Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Shapes PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download and present our Business PowerPoint Templates because It can Bubble and burst with your ideas. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity.Use these PowerPoint slides for presentations relating to Login, cyber, radar, protocol, elimination, secure, corporate, future, concept, lan, infrastructure, data, process, scan, viral, technology, security, wan, abstract,creative, illustration, system, up, focus, terrorism, futuristic, recognition, precaution, check, processing, zoom, information, background, virus, conceptual,precautionary, pattern, systematic, measure. The prominent colors used in the PowerPoint template are Blue, Blue light, White. Force out your enemies with our Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates. Just download, type and present.
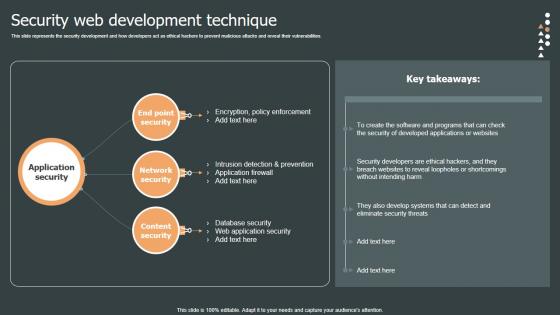
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.

Compound Annual Growth Rate CAGR Of Application Security Testing
This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Compound Annual Growth Rate CAGR Of Application Security Testing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Compound Annual Growth Rate CAGR Of Application Security Testing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc.

Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc. There are so many reasons you need a Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.

Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112
We present our Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112.Use our Technology PowerPoint Templates because, Activities which in themselves have many inherent business oppurtunities. Use our Computer PowerPoint Templates because,And watch them strenthen your companys sinews. Use our Business PowerPoint Templates because, Emphasise on any critical or key factors within them. Use our Internet PowerPoint Templates because,Now use this slide to bullet point your views. Use our Security PowerPoint Templates because,Demonstrate how you think out of the box.Use these PowerPoint slides for presentations relating to Computer under protection of umbrella, internet, security, business, technology, computer. The prominent colors used in the PowerPoint template are Green, Black, Blue Cross the chasm with our Laptop Under Protection Security PowerPoint Templates And PowerPoint Themes 1112. You will come out on top.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V
This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage. This Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage.
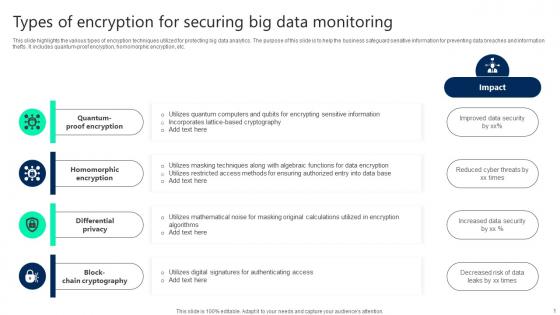
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
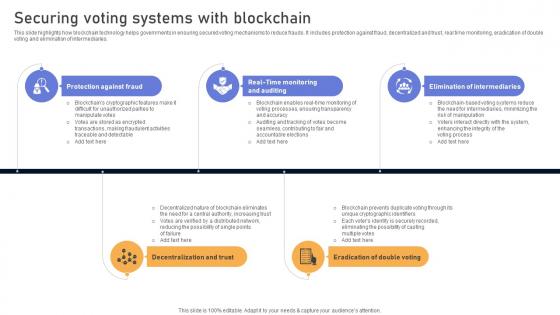
Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. Get a simple yet stunning designed Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.
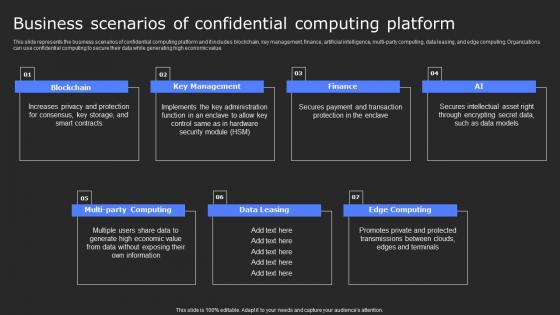
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
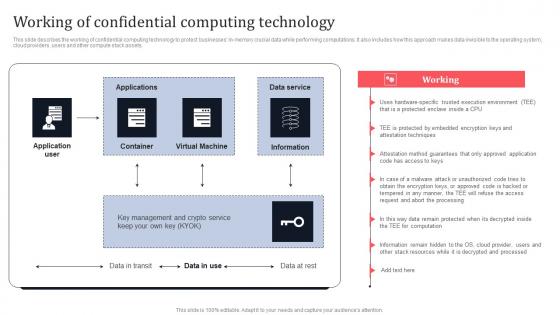
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
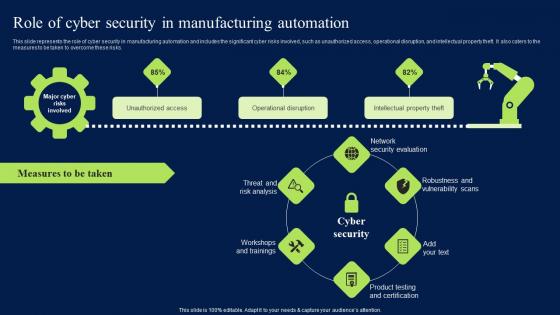
Role Of Cyber Security In Manufacturing Automation Clipart PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.

Four Chains Tied Together Security Teamwork PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Four Chains Tied Together Security Teamwork PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Leadership PowerPoint Templates because it Saves your time as a prized possession, an ideal aid to give an ideal presentation. Present our Teamwork PowerPoint Templates because Our Template designs are State of the Art. Download and present our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Security PowerPoint Templates because your team and you always raise a toast. Download and present our Chains PowerPoint Templates because you can Raise your Company stocks at the Opening Bell.Use these PowerPoint slides for presentations relating to Chains tied together security teamwork, success, security, chains, leadership, teamwork. The prominent colors used in the PowerPoint template are Red, Gray, Black. People tell us our Four Chains Tied Together Security Teamwork PowerPoint Templates PPT Backgrounds For Slides 1112 will make you look like a winner. Presenters tell us our security PowerPoint templates and PPT Slides are Fantastic. PowerPoint presentation experts tell us our Four Chains Tied Together Security Teamwork PowerPoint Templates PPT Backgrounds For Slides 1112 will make the presenter look like a pro even if they are not computer savvy. Customers tell us our together PowerPoint templates and PPT Slides are Cheerful. Customers tell us our Four Chains Tied Together Security Teamwork PowerPoint Templates PPT Backgrounds For Slides 1112 are Elevated. Customers tell us our success PowerPoint templates and PPT Slides are Fashionable. You possess enterprising ideas. Display them with courage on our Four Chains Tied Together Security Teamwork PowerPoint Templates Ppt Backgrounds For Slides 1112.
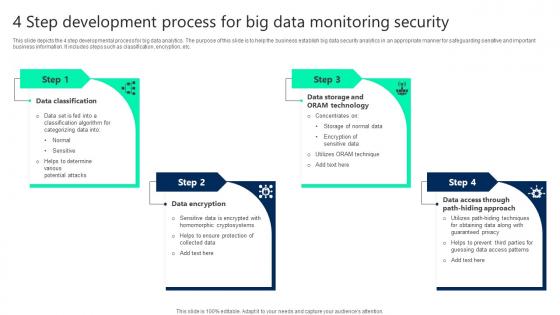
4 Step Development Process For Big Data Monitoring Security Demonstration pdf
This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Showcasing this set of slides titled 4 Step Development Process For Big Data Monitoring Security Demonstration pdf. The topics addressed in these templates are Data Classification, Data Access, Data Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc.

Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112
We present our Keys Tied To Chain Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Success PowerPoint Templates because,This Slide offers an excellent background to build up the various stages of your business process. Use our Chains PowerPoint Templates because,Our PowerPoint templates designed for your ideas to sell. Use our Finance PowerPoint Templates because,Let this slide illustrates others piggyback on you to see well over the horizon Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Keys tied to chain, business, success, chains, finance, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, White Pioneer changes with our Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.

House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112
We present our House And Alarm clock Security PowerPoint Templates PPT Background For Slides 1112.Use our Real estate PowerPoint Templates because,Stable ideas are the building blocks of a sucessful structure. Use our Business PowerPoint Templates because,This template can project the path to sucess that you have charted. Use our Money PowerPoint Templates because,You can Enlighten them with your brilliant understanding of mental health. Use our Finance PowerPoint Templates because, You can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process. Use our Clocks PowerPoint Templates because, This is Aesthetically designed to make a great first impression this template highlights .Use these PowerPoint slides for presentations relating to House and alarm clock, real estate, business, money, finance, clocks. The prominent colors used in the PowerPoint template are Green, White, Blue Get your fill of applause with our House And Alarm Clock Security PowerPoint Templates Ppt Background For Slides 1112. The claps will just continue to come.
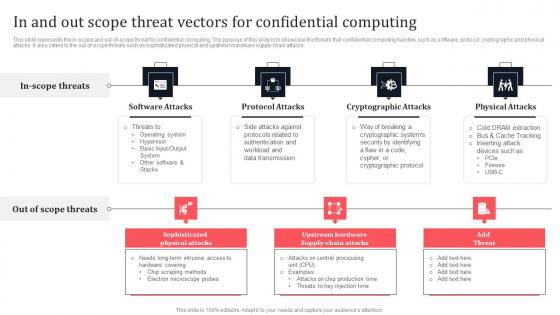
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Features Of Next Generation Secure Web Gateway Web Threat Protection System
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Find highly impressive Features Of Next Generation Secure Web Gateway Web Threat Protection System on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Next Generation Secure Web Gateway Web Threat Protection System for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.

Save Money Business PowerPoint Templates And PowerPoint Themes 1112
We present our Save Money Business PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,To strive to give true form to your great dream. Use our Success PowerPoint Templates because, Our Template designs are State of the Art. Use our Business PowerPoint Templates because, Core Diagram:- Explore the various hues and layers existing in your in your plans and processes. Use our Money PowerPoint Templates because, Outline your targets to your team. Use our Finance PowerPoint Templates because, Support groups are an essential element of the ongoing struggle against cancer.Use these PowerPoint slides for presentations relating to Save money, security, success, business, money, finace. The prominent colors used in the PowerPoint template are Blue, Yellow, Black Performance evaluation is easier with our Save Money Business PowerPoint Templates And PowerPoint Themes 1112. They help you assess results accurately.
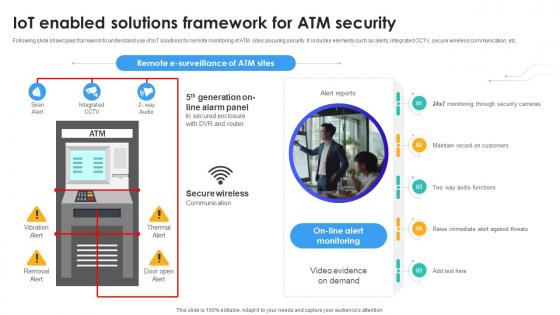
IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V
Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc.
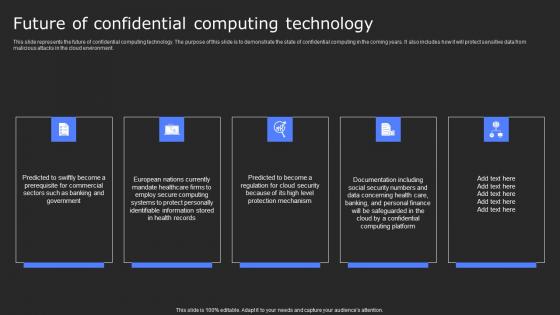
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
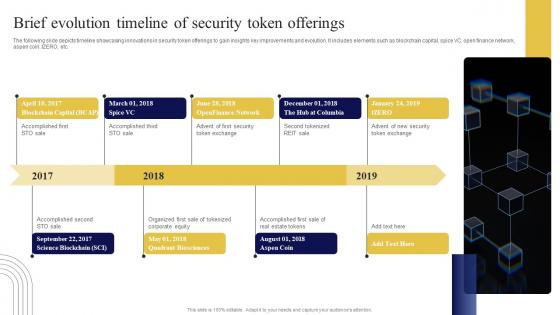
Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf
The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Brief Evolution Timeline Of Security Exploring Investment Opportunities Portrait Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
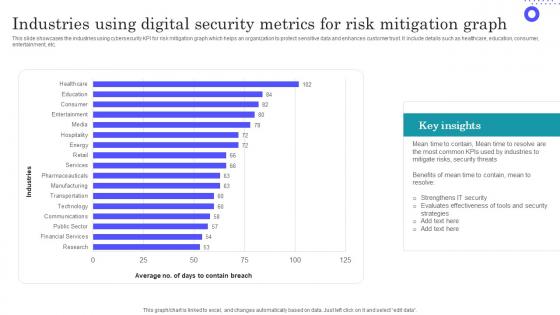
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
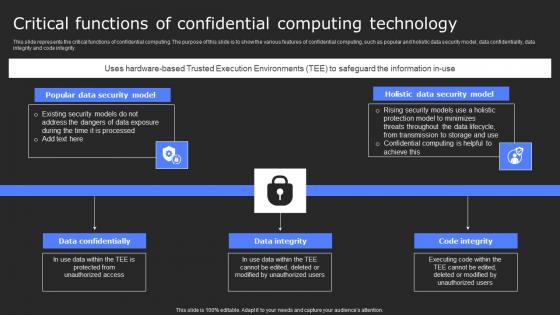
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
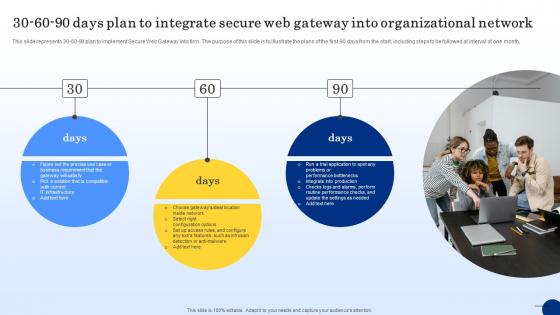
30 60 90 Days Plan To Integrate Secure Web Threat Protection System
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Integrate Secure Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
VPN For Secure Network Vector Icon Ppt PowerPoint Presentation Pictures Example File PDF
Presenting vpn for secure network vector icon ppt powerpoint presentation pictures example file pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn for secure network vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
VPN Privacy And Security Vector Icon Ppt PowerPoint Presentation Model Slides PDF
Presenting vpn privacy and security vector icon ppt powerpoint presentation model slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn privacy and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Common Network Security Threats Vector Icon Ppt PowerPoint Presentation Ideas Elements PDF
Presenting common network security threats vector icon ppt powerpoint presentation ideas elements pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including common network security threats vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Emerging Threats In Cyber Security Ppt PowerPoint Presentation Model Images PDF
Presenting emerging threats in cyber security ppt powerpoint presentation model images pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including emerging threats in cyber security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Security Shield Vector Icon Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud security shield vector icon ppt powerpoint presentation icon background images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud security shield vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Symbol For Data Risk Vector Icon Ppt PowerPoint Presentation Pictures Guide PDF
Presenting security symbol for data risk vector icon ppt powerpoint presentation pictures guide pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security symbol for data risk vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Malware For IT Security Vector Icon Ppt PowerPoint Presentation File Mockup PDF
Presenting malware for it security vector icon ppt powerpoint presentation file mockup pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware for it security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Internet Security Vector Icon Ppt PowerPoint Presentation File Graphics PDF
Presenting smart phone internet security vector icon ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone internet security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Database Inventory Security Vector Icon Ppt PowerPoint Presentation File Graphic Images PDF
Presenting business database inventory security vector icon ppt powerpoint presentation file graphic images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business database inventory security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Security And Privacy With Biometric Ppt PowerPoint Presentation Gallery Slides PDF
Presenting data security and privacy with biometric ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data security and privacy with biometric. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Protecting PC Security From Hacker Vector Icon Ppt PowerPoint Presentation File Infographics PDF
Presenting protecting pc security from hacker vector icon ppt powerpoint presentation file infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protecting pc security from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Biometric Device For Security Access System Icon Ppt PowerPoint Presentation Ideas Picture PDF
Presenting biometric device for security access system icon ppt powerpoint presentation ideas picture pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including biometric device for security access system icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Parked Vehicles With Barrier Security Access Ppt PowerPoint Presentation Gallery Portfolio PDF
Presenting parked vehicles with barrier security access ppt powerpoint presentation gallery portfolio pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including parked vehicles with barrier security access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Access To Protect Cyber Threat System Ppt PowerPoint Presentation Visual Aids Diagrams PDF
Presenting security access to protect cyber threat system ppt powerpoint presentation visual aids diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security access to protect cyber threat system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0.

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing.
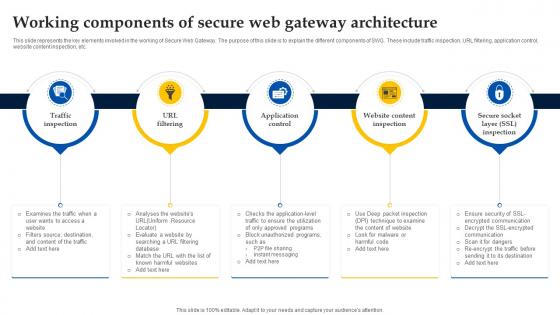
Web Access Control Solution Working Components Of Secure Web Gateway Architecture
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Working Components Of Secure Web Gateway Architecture and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc.
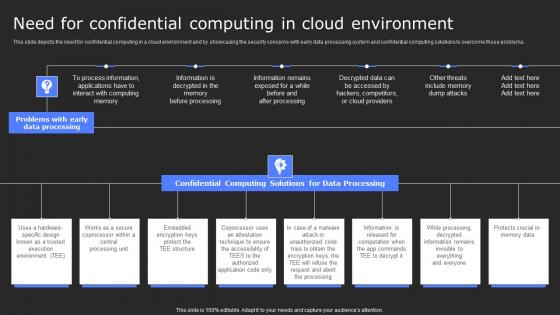
Need For Confidential Computing In Cloud Secure Computing Framework Brochure Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. There are so many reasons you need a Need For Confidential Computing In Cloud Secure Computing Framework Brochure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.

Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Welcome to our selection of the Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.

Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find a pre-designed and impeccable Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf
Find highly impressive Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. Our Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Web Gateway Set Up Configuration And Implementation Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. There are so many reasons you need a Secure Web Gateway Set Up Configuration And Implementation Web Threat Protection System. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc.


 Continue with Email
Continue with Email

 Home
Home


































